Author: Denis Avetisyan
This review examines the evolution of Quantum Key Distribution, from foundational security proofs to the practical challenges of real-world implementation and error mitigation.

A comprehensive analysis of QKD protocols, attacks, error correction codes, and their role in building secure quantum-augmented networks.
While quantum key distribution (QKD) promises information-theoretic security, translating theoretical proofs into robust, practical systems remains a significant challenge. This review, ‘Quantum Key Distribution: Bridging Theoretical Security Proofs, Practical Attacks, and Error Correction for Quantum-Augmented Networks’, comprehensively analyzes the landscape of QKD, categorizing protocols, detailing contemporary attacks, and evaluating error correction strategies. Our synthesis reveals critical advancements in protocols like Twin-field QKD and Device-Independent QKD, alongside the crucial role of quantum error correction in enhancing channel fidelity. As quantum networks evolve, can these advancements pave the way for truly secure, scalable quantum-augmented communication infrastructures?
The Quantum Promise: Security Rooted in Reality
Quantum Key Distribution (QKD) represents a fundamental departure from classical cryptography by leveraging the laws of quantum physics to guarantee secure communication. Unlike traditional encryption methods, which rely on mathematical complexity that could be broken with sufficient computing power, QKD’s security is rooted in the very nature of reality. It functions by transmitting cryptographic keys encoded onto individual particles of light, or photons. Any attempt to intercept or measure these photons inevitably disturbs their quantum state, alerting the communicating parties to the presence of an eavesdropper. This means that, in theory, a secure key can be established even if an adversary possesses unlimited computational resources. The implications are profound, promising a future where sensitive data – from financial transactions to government secrets – remains truly protected against even the most sophisticated attacks, and ushering in a new era of information security based on the principles of quantum mechanics rather than computational assumptions.
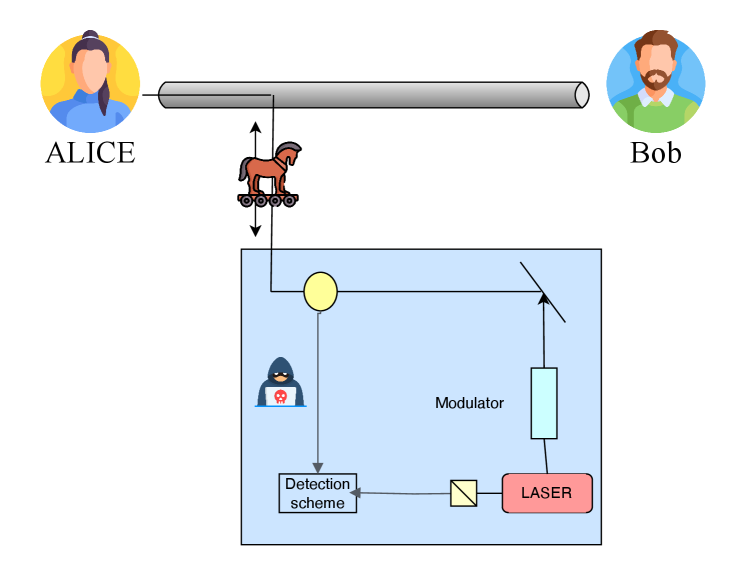
While Quantum Key Distribution (QKD) promises information-theoretic security, its practical implementations are susceptible to a range of attacks that deviate from idealized theoretical models. These vulnerabilities aren’t breaches of the quantum principles themselves, but rather exploits of imperfections in the physical devices used to generate and detect single photons, and the characteristics of the communication channel. For instance, detectors aren’t perfect and introduce noise, while optical fibers exhibit losses and polarization drifts. Attackers can leverage these real-world limitations – manipulating detector efficiencies, controlling channel parameters, or even exploiting side-channel information – to gain information about the key without being detected. Consequently, robust countermeasures, including careful device calibration, channel characterization, and sophisticated data post-processing techniques, are crucial to bridging the gap between theoretical security and practical resilience in QKD systems.
The theoretical invulnerability of Quantum Key Distribution (QKD) faces significant challenges from practical implementation flaws, most notably attacks like the Photon-Number-Splitting (PNS) attack. This attack exploits vulnerabilities in single-photon detectors, allowing an eavesdropper to gain information without introducing detectable disturbances. Countermeasures necessitate a delicate optimization of decoy state intensities – weak laser pulses mixed with signal pulses – to effectively detect any eavesdropping attempts. The effectiveness of these decoy states hinges on precisely calibrating their intensity; too weak, and the eavesdropper remains undetected; too strong, and legitimate signals are mistaken for noise. Current research focuses on advanced statistical analysis and detector characterization to minimize the impact of these attacks and ensure the long-term security of QKD systems, moving beyond purely theoretical guarantees to a robust, practical reality.
![This schematic illustrates a powerful eavesdropper executing a plausible network security (PNS) attack, as detailed in reference [38].](https://arxiv.org/html/2511.20602v1/x1.png)
Quantum Error Correction: Fortifying Fragile Information
Quantum Error Correction (QEC) is essential for maintaining the fidelity of quantum information due to the inherent fragility of quantum states. These states are highly susceptible to both noise – random environmental disturbances – and decoherence, the loss of quantum information through interaction with the environment. Unlike classical bits, which can be duplicated for redundancy, the no-cloning theorem prohibits the creation of identical quantum copies. Therefore, QEC doesn’t directly replicate the quantum state but instead encodes the logical quantum information across multiple physical qubits in a manner that allows detection and correction of errors without directly measuring the encoded quantum state and collapsing its superposition. Error correction relies on identifying error syndromes – patterns indicating the type of error that occurred – and applying corrective operations based on these syndromes to restore the original quantum state. The effectiveness of QEC is quantified by the code’s ability to suppress error rates below a certain threshold, enabling reliable quantum computation and communication.
CSS codes and Surface Codes are prominent Quantum Error Correction (QEC) approaches built upon the foundation of stabilizer formalism. Stabilizer formalism defines error correction based on operators that commute with the encoded quantum state, allowing for the detection and correction of errors without directly measuring the fragile quantum information. CSS codes construct error-correcting codes by combining two classical linear codes – a symmetric code for bit-flip errors and a Hamming code for phase-flip errors – providing protection against both types of errors. Surface codes, a subset of topological codes, utilize a two-dimensional lattice of qubits and stabilizer measurements to encode quantum information in a manner resilient to local noise. Both approaches rely on encoding logical qubits using multiple physical qubits, and the effectiveness of error correction is directly related to the code’s ability to detect and correct errors before they propagate and corrupt the encoded quantum state.
Quantum Key Distribution (QKD) systems utilize error correction to improve key generation rates and secure communication in the presence of practical limitations. Channel impairments, such as fiber attenuation and dark counts in detectors, introduce errors that must be corrected. Furthermore, potential eavesdropping attacks also contribute to error rates. CSS codes and, notably, surface codes, are employed to address these errors; surface codes necessitate a minimum code distance of $d ≥ 3$ to reliably correct errors occurring in realistic fiber optic channels. This threshold ensures that single errors, and even correlated errors within a limited scope, can be detected and corrected without compromising the security or integrity of the generated key. Achieving a code distance of 3 requires encoding each logical qubit into multiple physical qubits, providing redundancy to combat noise and malicious intervention.
Quantum Augmented Networks: Bridging Classical and Quantum Realms
Quantum Augmented Networks (QANs) represent a hybrid communication architecture designed to leverage the benefits of both classical and quantum communication methods. Classical networks provide established infrastructure and high bandwidth for bulk data transfer, while integrated quantum components address limitations in security and potentially enhance efficiency. Specifically, QANs utilize quantum communication protocols-such as Quantum Key Distribution (QKD)-to establish secure communication channels, impervious to many attacks affecting classical cryptography. This is coupled with continued reliance on classical infrastructure for the majority of data transmission, resulting in a system that balances security needs with practical considerations of cost and performance. The resulting network aims for increased resilience against evolving cyber threats and the potential for optimized data transmission through quantum-enhanced protocols where applicable.
Quantum Key Distribution (QKD) and Quantum Error Correction (QEC) are foundational technologies enabling practical Quantum Augmented Networks. QKD protocols, such as BB84, allow two parties to generate a shared, secret key with information-theoretic security, guaranteeing protection against any eavesdropping attempt governed by the laws of physics. However, quantum signals are susceptible to noise and loss during transmission. QEC techniques, leveraging principles of quantum entanglement and redundancy, mitigate these errors, ensuring reliable data transmission. Specifically, QEC encodes logical qubits into multiple physical qubits, allowing the detection and correction of errors without collapsing the quantum state. The combination of secure key establishment via QKD and reliable communication via QEC forms the basis for secure and robust quantum-enhanced network infrastructure.
The Symmetry Check is a validation procedure employed in Quantum Augmented Networks to assess the security of established communication channels. This check relies on formal security proofs demonstrating that a channel’s characteristics – specifically its symmetrizability – guarantee secure key exchange. Symmetrizability, in this context, refers to the channel’s ability to maintain security even when subjected to certain types of attacks or noise. The validation process analyzes channel properties to confirm adherence to the required symmetrizability conditions, thereby providing quantifiable assurance of channel security prior to data transmission and confirming the effectiveness of Quantum Key Distribution (QKD) or other quantum communication protocols employed within the network.
Countering Eavesdropping: The Art of Decoy States and Beyond
The decoy state method addresses photon number splitting (PNS) attacks in Quantum Key Distribution (QKD) systems by randomly encoding signals in weak coherent pulses alongside single-photon pulses. PNS attacks exploit the inability to perfectly distinguish single photons from weak coherent pulses; an eavesdropper can split the quantum signal into multiple photons to gain information without being detected. By analyzing the outcomes of signals sent in different intensity levels – the decoy states – legitimate parties can estimate the probability of a multi-photon pulse being present. This estimation allows for the calculation of the quantum bit error rate (QBER) due to eavesdropping and enables the rejection of potentially compromised key bits, thus mitigating the impact of PNS attacks and ensuring secure key generation. The effectiveness of the method relies on accurately characterizing the single-photon detectors and carefully selecting the intensity levels of the decoy states.
Decoy state methods in Quantum Key Distribution (QKD) rely on modulating signal intensity to detect eavesdropping attempts. Weak pulses, known as decoy states, are transmitted alongside signal states. By analyzing the quantum bit error rate (QBER) of both signal and decoy states, legitimate users can estimate the amount of information potentially gained by an eavesdropper. Specifically, an increased error rate in decoy states, compared to the expected rate for a lossless channel, indicates the presence of an intercept-resend attack. Variable decoy state intensity optimization further refines this process, allowing for a more accurate estimation of eavesdropping rates and improved key generation security by minimizing the impact of detector efficiencies and channel losses on the QBER estimation. The effectiveness of this technique stems from the fact that any attempt to measure the quantum state inevitably introduces disturbances, detectable through increased error rates.
Twin-Field QKD (TF-QKD) and the Three-Stage Protocol represent advancements beyond traditional QKD systems by addressing limitations in key rate and communication distance. TF-QKD utilizes a dual basis approach and composition of weak coherent states to effectively remove the detector dead time, significantly increasing the key rate and achievable transmission distance. The Three-Stage Protocol, building on TF-QKD principles, further optimizes state preparation and measurement, improving the secret key rate and extending the communication range by mitigating effects of channel loss and imperfections. Both protocols employ advanced techniques for parameter estimation and error correction, allowing for secure communication over longer distances than previously achievable with standard QKD implementations, and offer increased resilience against practical attacks.
A Quantum-Resilient Future: Secure Communication Redefined
The convergence of Quantum Key Distribution (QKD), Quantum Error Correction (QEC), and sophisticated network designs promises a transformative leap in secure communication capabilities. QKD establishes cryptographic keys using the principles of quantum mechanics, guaranteeing detection of any eavesdropping attempt, while QEC mitigates the impact of noise and transmission loss inherent in quantum channels. Integrating these technologies with advanced network architectures – including trusted nodes and quantum repeaters – allows for the creation of secure communication networks extending far beyond the limitations of current cryptographic systems. This future network envisions unhackable data transmission for critical infrastructure like power grids and financial institutions, and reinforces national security by protecting sensitive governmental communications, ultimately ushering in an era where data confidentiality is guaranteed by the laws of physics rather than computational complexity.
The advent of quantum-resistant communication promises a transformative effect on sectors demanding unwavering security. Critical infrastructure, encompassing power grids, water treatment facilities, and transportation networks, stands to benefit from communication channels impervious to eavesdropping, safeguarding operational stability and public safety. Financial transactions, currently vulnerable to increasingly sophisticated cyber threats, could achieve unprecedented levels of confidentiality and integrity, fostering trust in digital economies. Perhaps most significantly, national security will be fundamentally altered, with the potential to protect sensitive government communications and intelligence data from both current and future decryption attempts. This shift represents a proactive defense against evolving threats, ensuring continued operational capability and strategic advantage in an increasingly interconnected, and potentially hostile, digital landscape.
Realizing the transformative potential of quantum communication necessitates sustained research efforts focused on mitigating practical challenges, particularly the vulnerability to jamming attacks. These attacks introduce errors into the quantum signal, directly impacting the reliability of secure key distribution. The quantifiable metric for this disruption is the Quantum Bit Error Rate (QBER), and current models demonstrate that jamming’s influence is mathematically represented as $1 – \cos^2(\beta)$, where β represents the angle of polarization disturbance. Reducing this QBER is paramount, and ongoing development centers on advanced error correction protocols, sophisticated detection mechanisms, and novel network architectures designed to proactively counteract jamming attempts. Further exploration into these areas promises not only to enhance the resilience of quantum communication systems but also to pave the way for widespread adoption across critical sectors reliant on uncompromised data security.
The pursuit of absolute security, as examined within the review of Quantum Key Distribution, often reveals itself as a series of increasingly refined approximations. The study meticulously details potential attacks and error correction methods, highlighting a landscape where perfect defense remains elusive. This resonates with a sentiment expressed by John Bell: “No physicist believes that mechanism produces a result.” Bell wasn’t dismissing causality, but rather emphasizing that models, however elegant, are always simplifications of reality. Similarly, QKD protocols, despite their theoretical foundations, are subject to practical limitations and ongoing scrutiny. The constant need for refinement and adaptation, detailed in the analysis of decoy-state QKD and error correction codes, underscores that security isn’t a destination, but a continuous process of challenging and improving existing systems.
What Lies Ahead?
The pursuit of unconditionally secure communication, as exemplified by Quantum Key Distribution, reveals itself less as a solved problem and more as an exquisitely detailed mapping of human fallibility. This review highlights not simply what QKD can do, but the myriad ways in which practical implementations deviate from idealized models – a familiar story in applied physics. The gap between theoretical proofs and demonstrable security remains, stubbornly, the central challenge. Advancements in attack mitigation, and particularly the ongoing race against side-channel vulnerabilities, suggest that security is not a property of the system, but an emergent property of relentless adversarial testing.
Future progress will likely hinge not on inventing wholly new protocols, but on refining existing ones to account for imperfections. Quantum error correction, while promising, demands resources that strain current technological limits. Perhaps a more fruitful avenue lies in embracing a layered approach – combining QKD with classical cryptographic techniques, accepting that absolute security is an asymptote, not a destination. Data isn’t the goal – it’s a mirror of human error.
Moreover, the integration of QKD into larger quantum networks introduces complexities beyond key distribution itself. Managing entanglement across multiple nodes, ensuring synchronization, and building truly scalable infrastructure pose substantial hurdles. Even what we can’t measure still matters – it’s just harder to model. The field needs to resist the temptation to declare victory prematurely, and instead focus on rigorously quantifying the remaining vulnerabilities.
Original article: https://arxiv.org/pdf/2511.20602.pdf
Contact the author: https://www.linkedin.com/in/avetisyan/
See also:
- The Winter Floating Festival Event Puzzles In DDV
- Jujutsu Kaisen: Why Megumi Might Be The Strongest Modern Sorcerer After Gojo
- Best JRPGs With Great Replay Value
- Jujutsu Kaisen: Yuta and Maki’s Ending, Explained
- Sword Slasher Loot Codes for Roblox
- One Piece: Oda Confirms The Next Strongest Pirate In History After Joy Boy And Davy Jones
- Roblox Idle Defense Codes
- All Crusade Map Icons in Cult of the Lamb
- Non-RPG Open-World Games That Feel Like RPGs
- Dungeons and Dragons Level 12 Class Tier List
2025-11-26 07:27