Author: Denis Avetisyan
A new analysis reveals critical vulnerabilities in RFID-based traceability systems and proposes a path-based authentication method to enhance security and protect sensitive data.
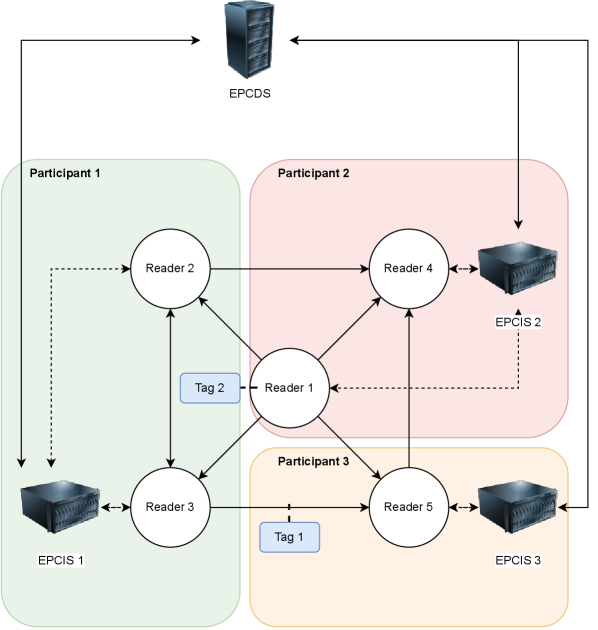
This review presents a systematic framework for evaluating the security of path-based traceability systems in RFID-enabled supply chains, identifying key weaknesses and proposing solutions.
While RFID-enabled traceability systems are increasingly deployed to bolster supply chain security, their inherent vulnerabilities remain largely unaddressed. This paper, ‘A Systematic Security Analysis for Path-based Traceability Systems in RFID-Enabled Supply Chains’, presents a novel security framework for evaluating these systems, revealing critical weaknesses in seventeen existing solutions. Our analysis demonstrates that current traceability approaches often lack robust path authentication, creating opportunities for counterfeiting and circumvention. Can a path-based approach offer a more secure and privacy-preserving foundation for future supply chain traceability systems?
The Unfolding Chain: Navigating Complexity and Vulnerability
Contemporary supply chains, designed for efficiency, have become remarkably intricate networks spanning multiple continents and involving countless intermediaries. This complexity, while enabling global commerce, inherently creates opacity, making it difficult to ascertain the complete journey of a product – from raw material sourcing to the end consumer. This lack of visibility isn’t merely a logistical challenge; it actively fosters vulnerabilities to disruption, whether from natural disasters, geopolitical instability, or deliberate malicious acts. Furthermore, the convoluted nature of these chains provides fertile ground for fraudulent activities, including counterfeiting, the introduction of substandard materials, and unethical labor practices, all concealed within layers of obscured origins and transfers of custody. Consequently, businesses and consumers alike face increasing risks associated with product authenticity, safety, and sustainability, highlighting the urgent need for greater systemic clarity.
Historically, verifying a product’s journey from raw material to consumer has relied on fragmented documentation and manual checks, a system demonstrably susceptible to error and manipulation. These conventional methods often involve numerous intermediaries, each maintaining their own records – creating data silos and hindering a unified view of the supply chain. Consequently, pinpointing the precise origin of components or identifying points of contamination becomes exceptionally difficult, if not impossible. The inherent limitations of paper trails and disparate databases fail to guarantee data integrity, leaving businesses vulnerable to counterfeit goods, ethical sourcing concerns, and significant financial losses. This lack of verifiable data not only impacts brand reputation but also impedes effective recall procedures and proactive risk management strategies within increasingly complex global networks.
The absence of clear information regarding a product’s journey from origin to consumer actively diminishes public confidence in brands and the goods they offer. This opacity isn’t merely a matter of inconvenience; it creates significant challenges for effective risk management within businesses and across entire industries. Without verifiable data tracing materials and processes, identifying the source of defects, unethical labor practices, or counterfeit goods becomes exponentially more difficult, leading to costly recalls, reputational damage, and potential legal liabilities. Consequently, organizations struggle to proactively mitigate disruptions, assess vulnerabilities, and ensure the integrity of their supply chains, ultimately impacting both financial stability and consumer safety.
A truly resilient and accountable supply chain hinges on the implementation of robust traceability systems. These systems move beyond simply tracking a product’s journey; they establish an immutable record of its origin, processing, and custody, utilizing technologies like blockchain and advanced sensor networks. Such detailed provenance data not only mitigates the impact of disruptions – from natural disasters to geopolitical instability – but also actively combats fraud and counterfeiting. By providing verifiable information at every stage, traceability fosters trust among consumers and stakeholders, enabling quicker identification of issues and facilitating targeted interventions. Ultimately, a commitment to traceability transforms the supply chain from a vulnerable network into a source of competitive advantage and sustainable growth, prioritizing ethical sourcing and responsible production practices.
Weaving the Digital Thread: Traceability in Practice
A comprehensive traceability system utilizes Radio Frequency Identification (RFID) technology to uniquely identify items and capture data related to their movement and status throughout the supply chain. This data is then stored and managed within an event data repository, commonly employing the EPCIS (Electronic Product Code Information Services) standard. EPCIS facilitates the standardized capture, storage, and sharing of event-level data – including production, ownership transfers, and location changes – creating a detailed and auditable history for each item. The combination of RFID and EPCIS provides a robust foundation for supply chain security by enabling verification of product authenticity, improved recall management, and enhanced visibility into the origin and chain of custody.
A comprehensive traceability system functions by documenting all pertinent occurrences throughout a product’s entire lifecycle, from raw material sourcing and manufacturing to distribution and end-of-life management. These recorded events include, but are not limited to, production dates, batch numbers, quality control checks, temperature readings during transport, custody transfers between parties, and location data. The resulting dataset forms a chronological and immutable record, enabling verification of a product’s provenance and history. This verifiable history is critical for identifying the source of defects, ensuring regulatory compliance, and combating counterfeiting. The granularity of event capture directly impacts the effectiveness of the system; more detailed records allow for more precise issue resolution and enhanced supply chain visibility.
The Food Trust initiative, a blockchain-based traceability system involving major food producers and retailers, provides a practical demonstration of the benefits of comprehensive supply chain tracking. This implementation leverages data sharing and immutable records to trace food products from farm to store shelf, reducing the time required to identify the source of contamination during recalls from weeks to seconds. Food Trust has successfully tracked products like mangoes and lettuce, demonstrating a reduction in food waste and an increase in consumer trust through improved transparency. The platform currently includes data from over 16 million shipments and involves participants across five continents, showcasing scalability and interoperability in a real-world logistical environment.
An evaluation of 1717 traceability systems was conducted to identify potential vulnerabilities within data management practices. This analysis focused on assessing the susceptibility of these systems to data manipulation, including unauthorized modification or deletion of event data. The scope of the evaluation encompassed a range of architectures and implementation details commonly found in supply chain traceability solutions. Results indicated a significant need for enhanced security protocols to protect the integrity and reliability of traceability data, as compromised data can undermine the entire purpose of establishing a verifiable product history and secure supply chain.
Fortifying the Chain: Cryptographic Bastions
Path Authentication is strengthened through the combined use of Secure Multi-Signature schemes and Homomorphic Encryption. Multi-signature technology requires multiple parties to approve a location record before it is added to the product’s journey, preventing single points of failure or fraudulent entries. Homomorphic Encryption allows computations to be performed on encrypted location data without decryption, ensuring that while the sequence of visits can be verified – confirming product provenance – the specific location details remain confidential. This combination enables validation of the supply chain history without exposing commercially sensitive information about suppliers or distribution routes, protecting both data integrity and privacy.
Hierarchical Identity-Based Encryption (HIBE) and Shamir Secret Sharing (SSS) are employed to ensure data integrity throughout the supply chain. HIBE facilitates the encryption of data using identities as public keys, eliminating the need for traditional Public Key Infrastructure (PKI) and simplifying key management. This allows for granular access control, where different parties are granted decryption keys based on their role. SSS implements a threshold cryptography scheme, dividing critical information into multiple shares and distributing them across different entities. Data can only be reconstructed when a predefined number of these shares are combined, preventing single points of failure and mitigating the risk of data compromise even if some shares are intercepted. The combination of HIBE and SSS provides a robust mechanism for protecting sensitive data while maintaining accessibility for authorized parties and ensuring data integrity verification.
Physically Uncloneable Functions (PUFs) provide a hardware-based security anchor by leveraging inherent manufacturing variations within a chip. These variations, resulting from unpredictable processes during fabrication, create a unique “fingerprint” for each individual integrated circuit. A PUF doesn’t store a secret key; instead, it generates a key in response to a specific challenge, making it extremely difficult to predict or replicate without physical access to the original chip. This characteristic effectively prevents tag cloning and counterfeiting, as a duplicated tag would not generate the same key response as the authentic device, even if the design is known. The security relies on the difficulty of reverse-engineering the physical characteristics that determine the key generation process, offering a robust defense against software-based attacks.
Batch verification is a performance optimization technique used to reduce computational overhead in cryptographic systems. Instead of individually verifying each data element or signature, batch verification allows multiple verifications to be performed simultaneously as a single operation. This is achieved through the aggregation of individual verification processes into a collective proof, significantly reducing the number of modular exponentiations or hash function calls required. The computational savings are particularly pronounced when dealing with a large number of verifications, as the cost of processing scales sublinearly with the batch size. This technique is widely implemented in blockchain technologies, secure multi-party computation, and digital signature schemes to improve throughput and reduce latency.
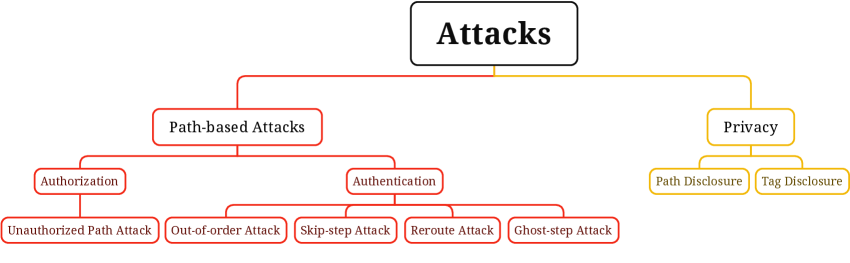
Addressing Vulnerabilities: Mapping the Threat Landscape
Reroute and out-of-order attacks represent significant threats to the reliable tracking of items within a supply chain. These attacks don’t necessarily involve falsifying individual tag reads, but rather manipulate the sequence in which those reads are recorded, effectively rewriting the item’s journey. A malicious actor might insert false location data, or rearrange legitimate data points, creating a misleading path that obscures the true origin or destination of a product. Consequently, systems relying on the integrity of this recorded path – for provenance tracking, authenticity verification, or quality control – become vulnerable to deception. Mitigating these attacks demands the implementation of robust verification protocols, such as cryptographic checksums or digital signatures applied to each recorded location, allowing for the detection of any tampering with the sequence of events and ensuring the trustworthiness of supply chain data.
Linking attacks represent a significant threat to data privacy by exploiting the potential to correlate seemingly innocuous pieces of information, ultimately revealing sensitive details about individuals or processes. These attacks don’t necessarily breach encryption or directly access confidential data; instead, they infer information by combining multiple, individually harmless data points. For instance, tracking the movement of tagged items over time, even without knowing their contents, can reveal patterns indicative of sensitive activities or locations. Consequently, robust data anonymization techniques are essential, alongside secure data sharing practices that minimize the exposure of potentially linkable attributes. Implementing differential privacy, k-anonymity, or other privacy-enhancing technologies can effectively disrupt these correlation attempts, safeguarding individual privacy and maintaining the confidentiality of tracked assets.
The efficacy of Radio Frequency Identification (RFID) security measures is fundamentally linked to the available memory within the tag itself. Sufficient storage capacity isn’t merely about accommodating identification data; it’s essential for embedding critical security metadata, such as cryptographic keys, digital signatures, and access control lists. Without this capacity, tags become vulnerable to cloning, counterfeiting, and unauthorized access. Protecting this tag memory from tampering is equally vital; physical attacks and sophisticated code injection techniques can compromise stored security information. Therefore, a holistic approach to RFID security necessitates not only expanding tag memory capabilities but also implementing robust mechanisms to shield that memory from both physical and digital threats, ensuring the ongoing integrity and trustworthiness of the entire supply chain.
A recent investigation revealed significant vulnerabilities within prominent radio frequency identification (RFID) systems, including ReSC, RF-Chain, and those proposed by Ray et al. and Burbridge et al. This analysis, conducted through a novel security framework, successfully identified weaknesses that could compromise both the integrity of tracked items and the privacy of associated data. The findings underscore a critical need to move beyond fragmented security approaches; a holistic strategy is essential, one that simultaneously safeguards against data manipulation and unauthorized access to sensitive information. The demonstrated effectiveness of this framework highlights its potential as a proactive tool for assessing and fortifying the resilience of supply chain security systems against evolving threats, advocating for a more comprehensive and integrated approach to data protection.
The Future of Trust: A Resilient and Transparent Ecosystem
A fundamental shift in supply chain management is occurring through the implementation of blockchain technology, which provides a shared, immutable record of transactions and asset movements. This decentralized ledger eliminates the need for a central authority, fostering greater trust and reducing the potential for fraud or manipulation. Each event – from raw material sourcing to final delivery – is recorded as a ‘block’ cryptographically linked to the previous one, creating a tamper-proof history. This heightened transparency allows stakeholders – including manufacturers, distributors, retailers, and consumers – to verify the authenticity and provenance of goods, improving accountability at every stage. Consequently, businesses are increasingly adopting blockchain solutions to streamline processes, reduce costs associated with dispute resolution, and build more resilient and trustworthy supply chains.
Zero-Knowledge Proofs represent a pivotal advancement in data verification, allowing parties to confirm the validity of information without disclosing the information itself. This cryptographic technique functions by demonstrating knowledge of a secret – such as a product’s origin or a component’s authenticity – without revealing what that secret actually is. Imagine verifying a supplier’s compliance with ethical sourcing standards without accessing their proprietary cost data; this is the power of Zero-Knowledge Proofs. By isolating the ‘truth’ of a claim from the underlying data, these proofs dramatically enhance privacy within supply chains, mitigating risks associated with data breaches and maintaining competitive advantages. The implications extend beyond simple verification, potentially enabling complex, confidential transactions and fostering trust between entities that might otherwise be hesitant to share sensitive information.
The ongoing evolution of supply chain security demands persistent advancements in cryptography and the foundational hardware upon which it relies. Current encryption methods, while robust, face increasing vulnerability from quantum computing and sophisticated adversarial attacks. Consequently, research focuses on post-quantum cryptography, developing algorithms resistant to decryption by future quantum computers. Simultaneously, hardware security primitives – secure enclaves, physically unclonable functions, and trusted execution environments – are being refined to protect cryptographic keys and sensitive data from physical tampering and side-channel attacks. These innovations aren’t merely about stronger algorithms; they involve designing security directly into the hardware, creating a deeply embedded defense against increasingly resourceful threats and ensuring the long-term integrity of increasingly complex global supply networks.
The convergence of advanced technologies promises a fundamental shift in supply chain management, moving beyond mere logistical efficiency toward genuine trust and openness. A future supply chain, fortified by innovations like blockchain and zero-knowledge proofs, isn’t simply about getting products from origin to consumer; it’s about establishing verifiable provenance and accountability at every stage. This allows stakeholders – from manufacturers and distributors to retailers and end-users – to independently confirm the authenticity, ethical sourcing, and quality of goods. Consequently, a resilient, transparent supply chain minimizes risks associated with counterfeiting, fraud, and disruptions, while simultaneously fostering stronger relationships built on shared confidence and demonstrable integrity. The resulting ecosystem benefits not only businesses through enhanced reputation and reduced costs, but also consumers who gain access to reliably sourced and trustworthy products.
The pursuit of robust traceability systems, as detailed in this analysis of RFID-enabled supply chains, inherently acknowledges the ephemeral nature of information. Systems designed to track goods across complex networks are not static monuments, but rather transient records responding to the arrow of time. As Tim Berners-Lee observed, “The Web is more a social creation than a technical one.” This sentiment resonates deeply; security isn’t merely about cryptographic strength, but also about the social and logistical processes that maintain data integrity over time. Versioning, in this context, becomes a form of memory, allowing the system to recall its past states and authenticate the path of goods, mitigating vulnerabilities identified within the proposed framework.
What Lies Ahead?
The presented framework, while offering a granular examination of RFID-enabled supply chain traceability, inevitably highlights the transient nature of security itself. Any improvement to these systems, any fortification of path authentication, ages faster than expected. The very act of identifying a vulnerability initiates a countdown, a period before adaptation renders the mitigation insufficient. This is not failure, but the expected decay of any complex system striving for permanence in a mutable environment.
Future work will undoubtedly focus on dynamic security models, systems that anticipate, rather than simply react to, evolving threats. However, a critical, often overlooked, aspect remains the cost of rollback. Returning to a previous security state – a journey back along the arrow of time – is rarely seamless. Data integrity, system compatibility, and the inevitable loss of information all contribute to the increasing expense of reverting to earlier configurations. The pursuit of ever-greater security, therefore, risks creating systems too brittle to gracefully accommodate necessary regressions.
Ultimately, the field must confront the inherent paradox of traceability. Perfect security implies perfect surveillance, while perfect privacy renders authentication impossible. The challenge isn’t to solve security, but to establish a sustainable equilibrium between these opposing forces, accepting that any achieved state is merely a temporary reprieve in the inevitable entropic march.
Original article: https://arxiv.org/pdf/2601.09407.pdf
Contact the author: https://www.linkedin.com/in/avetisyan/
See also:
- The Winter Floating Festival Event Puzzles In DDV
- Jujutsu Kaisen Modulo Chapter 18 Preview: Rika And Tsurugi’s Full Power
- Top 8 UFC 5 Perks Every Fighter Should Use
- USD COP PREDICTION
- Best Video Game Masterpieces Of The 2000s
- Upload Labs: Beginner Tips & Tricks
- Roblox 1 Step = $1 Codes
- Jujutsu: Zero Codes (December 2025)
- Jujutsu Kaisen: Why Megumi Might Be The Strongest Modern Sorcerer After Gojo
- How To Load & Use The Prototype In Pathologic 3
2026-01-15 19:38