Author: Denis Avetisyan
A new framework assesses the resilience of common communication protocols – MQTT, HTTP, and HTTPS – against the looming threat of quantum computing.
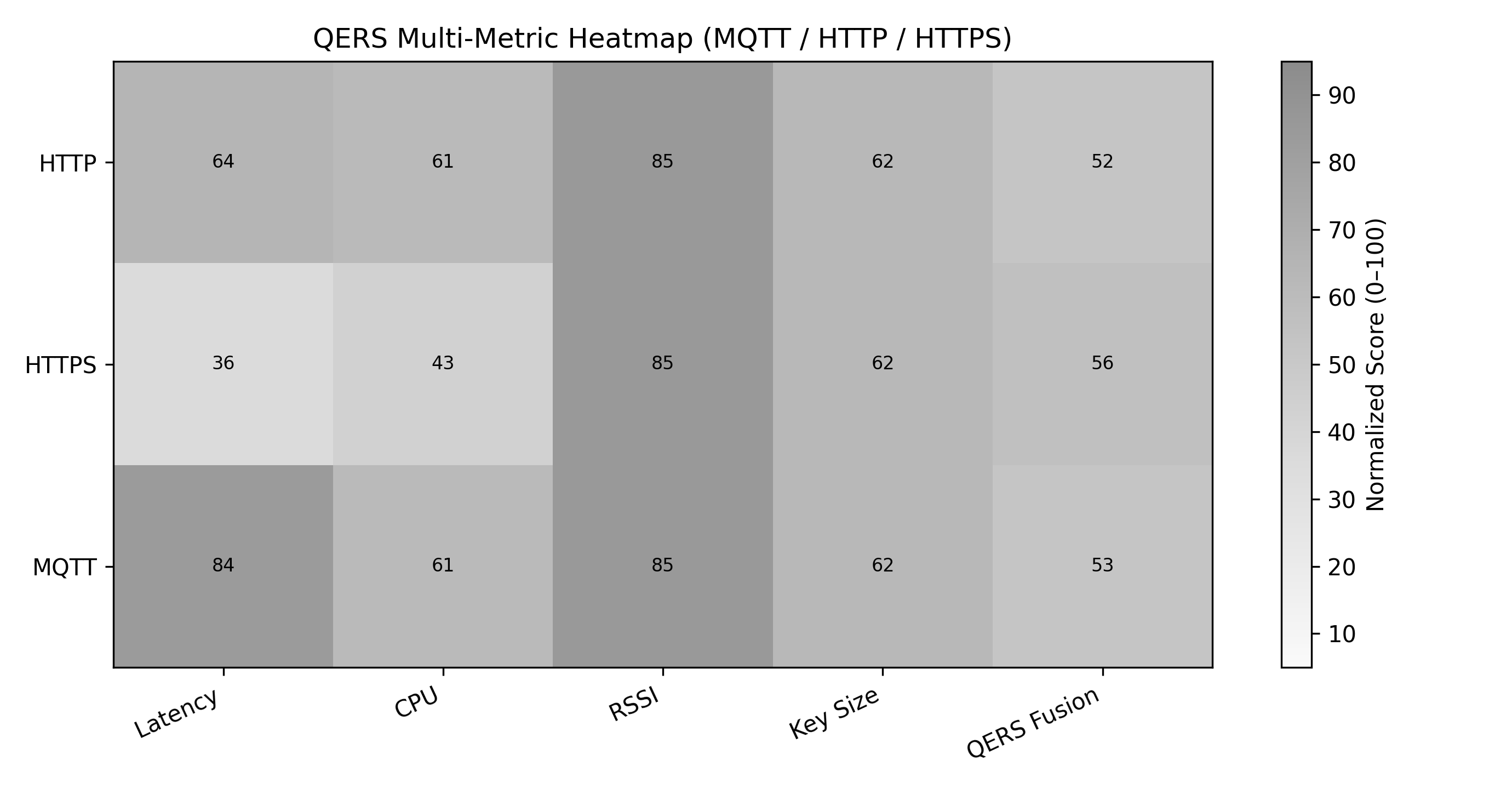
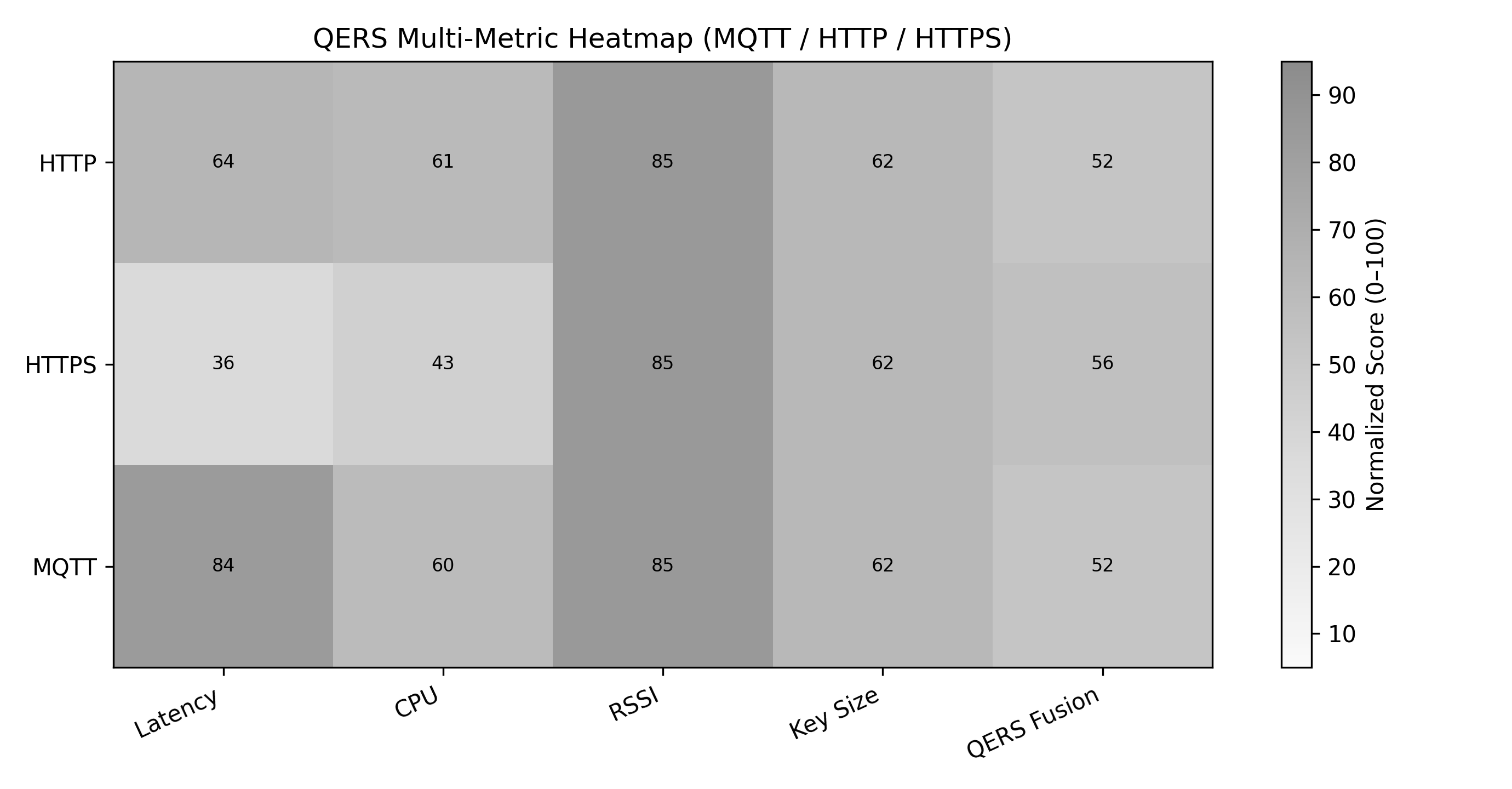
This review introduces the Quantum Encryption Resilience Score (QERS) to evaluate protocol performance and security trade-offs on resource-constrained devices under post-quantum cryptographic workloads.
The increasing threat of quantum computing necessitates a re-evaluation of cryptographic protocols, yet implementing post-quantum cryptography introduces significant overhead for resource-constrained devices. This paper presents an experimental evaluation, detailed in ‘Quantum Encryption Resilience Score (QERS) for MQTT, HTTP, and HTTPS under Post-Quantum Cryptography in Computer, IoT, and IIoT Systems’, of a novel framework-the Quantum Encryption Resilience Score (QERS)-for quantifying the performance and security trade-offs of common communication protocols. Results demonstrate that MQTT offers the most efficient resilience under post-quantum constraints, while HTTPS prioritizes security at the cost of increased latency and resource consumption. How can these findings inform the strategic adoption of post-quantum cryptography in increasingly interconnected IoT and IIoT ecosystems?
The Looming Fracture: Cryptography at the Edge of Quantum Disruption
The foundation of much modern digital security rests upon cryptographic algorithms – notably RSA and ECC – which, while currently robust against conventional attacks, face an existential threat from the advent of quantum computing. These algorithms rely on the mathematical difficulty of factoring large numbers or solving discrete logarithm problems; however, Shor’s algorithm, a quantum algorithm, can efficiently solve these problems, effectively breaking these encryption schemes. This poses a particularly acute risk for the Internet of Things (IoT), where billions of devices – from smart thermostats to medical implants – rely on these vulnerable standards to protect sensitive data and ensure operational integrity. A successful quantum attack could compromise device functionality, expose personal information, and disrupt critical infrastructure, highlighting the urgent need to transition to quantum-resistant cryptographic solutions before sufficiently powerful quantum computers become a reality.
The exponential growth of Internet of Things (IoT) devices – from smart thermostats and wearable health trackers to critical infrastructure components – dramatically escalates the potential impact of cryptographic breaches. Each newly connected device represents another entry point for malicious actors, and the sheer scale of this expanding network creates an unprecedented attack surface. This isn’t simply a matter of individual device compromise; a coordinated attack leveraging vulnerabilities in widely deployed IoT systems could disrupt essential services, compromise sensitive data across millions of users, and even pose physical safety risks. Consequently, reactive security measures are insufficient; the urgency lies in proactively implementing robust, future-proof cryptographic solutions that can withstand both current and emerging threats, including those posed by quantum computers, before widespread exploitation occurs.
The integration of enhanced cryptographic protocols into resource-constrained Internet of Things (IoT) devices presents a considerable challenge due to performance limitations. Existing security fortifications, while effective against conventional attacks, often demand significant computational power and memory – resources that many IoT devices simply lack. Implementing these upgrades can lead to unacceptable latency in data transmission and processing, hindering real-time responsiveness critical for applications like industrial control systems or medical devices. Consequently, a direct application of traditional security measures can effectively neuter the functionality of these devices, creating a trade-off between security and usability. Researchers are actively investigating lightweight cryptographic algorithms and hardware acceleration techniques to mitigate this performance overhead, striving to provide robust security without compromising the operational efficiency of the expanding IoT ecosystem.
QERS: Mapping Resilience in a Post-Quantum World
The Quantum Encryption Resilience Score (QERS) is a proposed metric designed to quantify the effects of implementing post-quantum cryptography within Internet of Things (IoT) protocols. Currently, evaluating the impact of these cryptographic transitions requires analyzing multiple, often disparate, performance indicators. QERS aims to consolidate these analyses into a single, unified score, allowing for a more holistic assessment of resilience against quantum computing threats. The score is intended to facilitate comparative analysis of different post-quantum cryptographic algorithms and their suitability for resource-constrained IoT devices and networks, providing a standardized method for evaluating the trade-offs between security and performance.
The Quantum Encryption Resilience Score (QERS) utilizes Multi-Criteria Decision Analysis (MCDA) to provide a holistic evaluation of IoT protocol resilience against quantum threats. Instead of focusing on a single performance indicator, MCDA within QERS simultaneously assesses three key criteria: latency introduced by post-quantum cryptographic algorithms, the computational overhead imposed on constrained devices, and the quantifiable security gains achieved through the implementation of these algorithms. This simultaneous assessment allows for a trade-off analysis, identifying optimal configurations that balance performance and security, and is facilitated by weighting each criterion based on its relative importance within the specific IoT deployment scenario. The resulting score represents a composite measure of resilience, enabling comparative analysis of different post-quantum cryptographic solutions and their impact on IoT system performance.
The Quantum Encryption Resilience Score (QERS) is specifically engineered for resource-constrained IoT devices. Its calculation incorporates CPU usage as a primary Key Performance Indicator (KPI), directly measuring the computational load imposed by post-quantum cryptographic algorithms. Furthermore, signal strength is included as a KPI to account for the impact of communication overhead on energy expenditure; lower signal strengths necessitate increased transmission power, impacting device battery life. These two KPIs – CPU usage and signal strength – are weighted within the QERS calculation to provide a comprehensive assessment of protocol resilience considering both processing and communication limitations common in IoT deployments.
Layered Resilience: Dissecting Performance Under Quantum Pressure
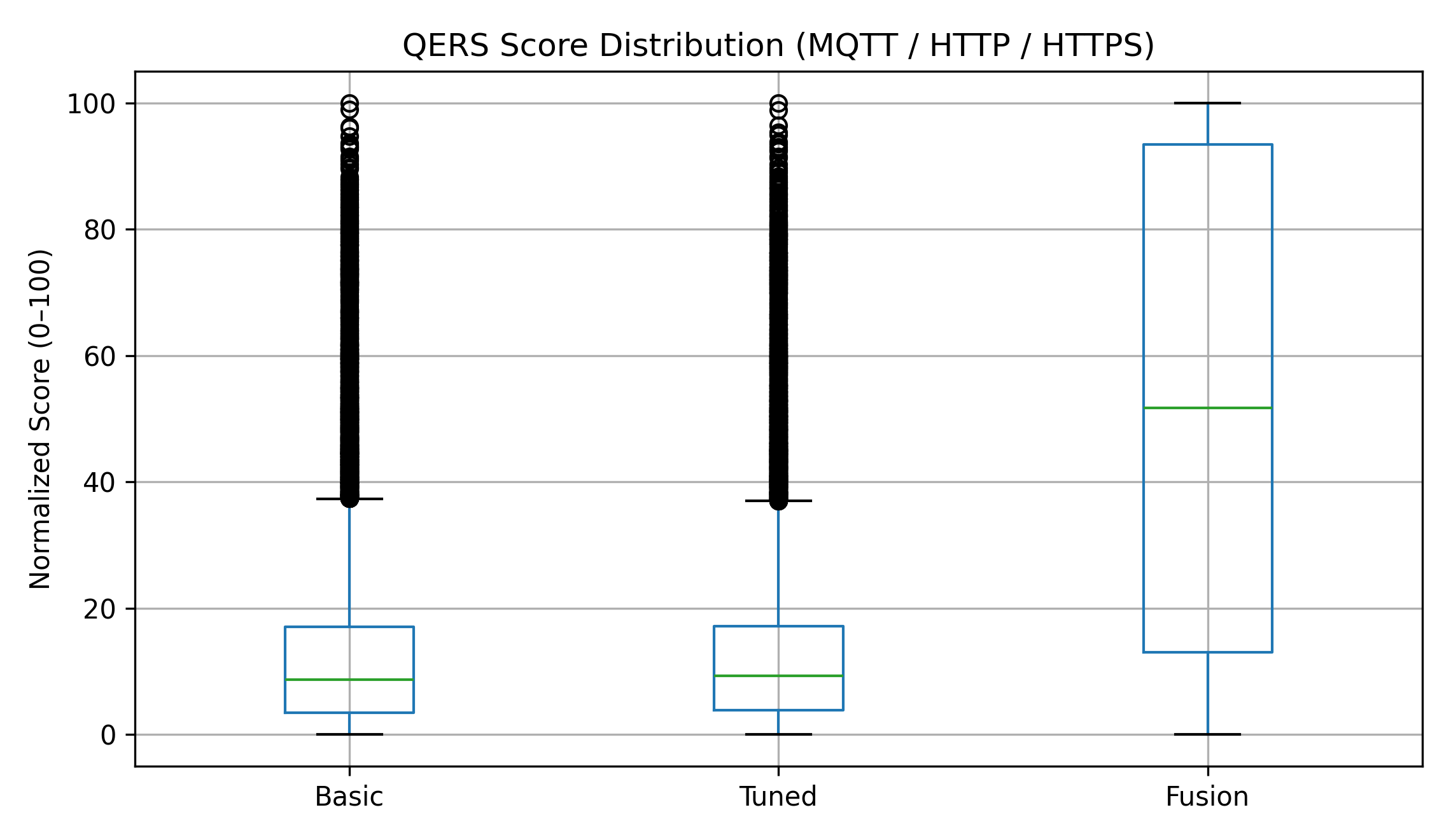
The Basic Quality of Experience Resilience Security (QERS) layer provides an initial assessment of network performance impacting secure communications. This foundational layer quantifies three core metrics: latency, measured as round-trip time; cryptographic overhead, representing the computational cost of encryption and decryption processes; and packet loss, indicating the percentage of data packets failing to reach their destination. Evaluation of these factors establishes a baseline for determining the inherent performance penalties associated with implementing security measures and identifies potential bottlenecks before considering more complex system-level interactions. Data gathered at this stage is crucial for understanding the fundamental trade-offs between security and performance in a given network environment.
The Tuned Quality of Experience Resilience System (QERS) layer builds upon the foundational assessment of the Basic layer by integrating system-specific and environmental variables into its evaluation. These factors include CPU load, memory utilization, network bandwidth availability, and prevailing network conditions such as jitter and packet loss rates. By analyzing these dynamic elements alongside core latency and cryptographic overhead, the Tuned layer provides a more granular and context-aware resilience profile. This nuanced assessment allows for a more accurate prediction of performance impacts under varying operational circumstances, facilitating targeted optimization strategies beyond those achievable with static baseline measurements.
The Fusion Quality of Experience Resilience System (QERS) layer analyzes the trade-offs between security implementations and resulting performance impacts. This layer moves beyond aggregate metrics by disaggregating performance penalties – such as increased latency or reduced throughput – directly attributable to specific security features. By isolating these penalties, the Fusion layer provides granular data enabling targeted optimization; administrators can identify security features with minimal performance overhead or pinpoint areas where alternative configurations or technologies can mitigate performance degradation without compromising security posture. This detailed analysis supports informed decision-making regarding security deployments and resource allocation, ultimately maximizing both security and user experience.
Validation Through Experiment: Protocols and the Limits of Resilience
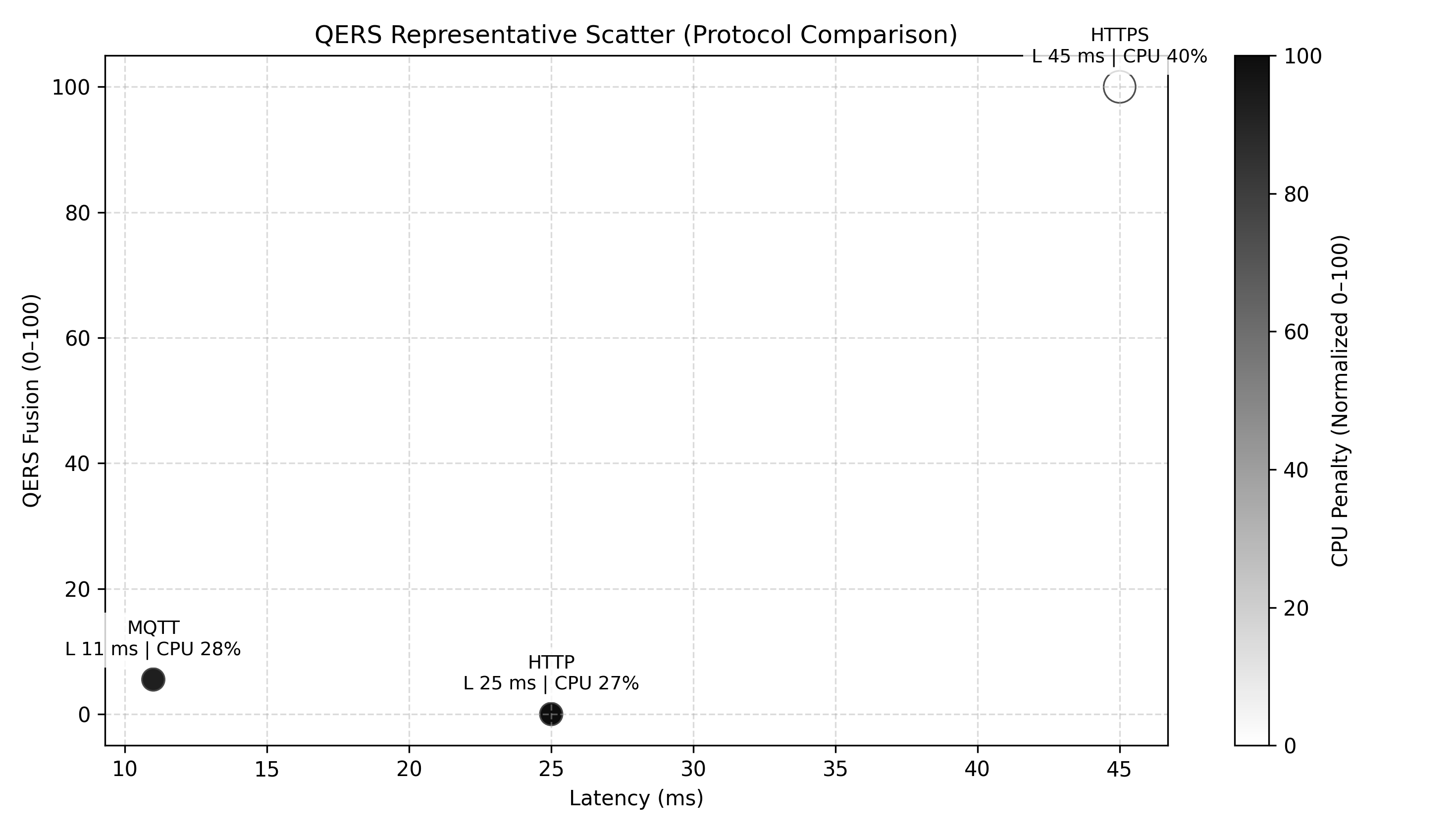
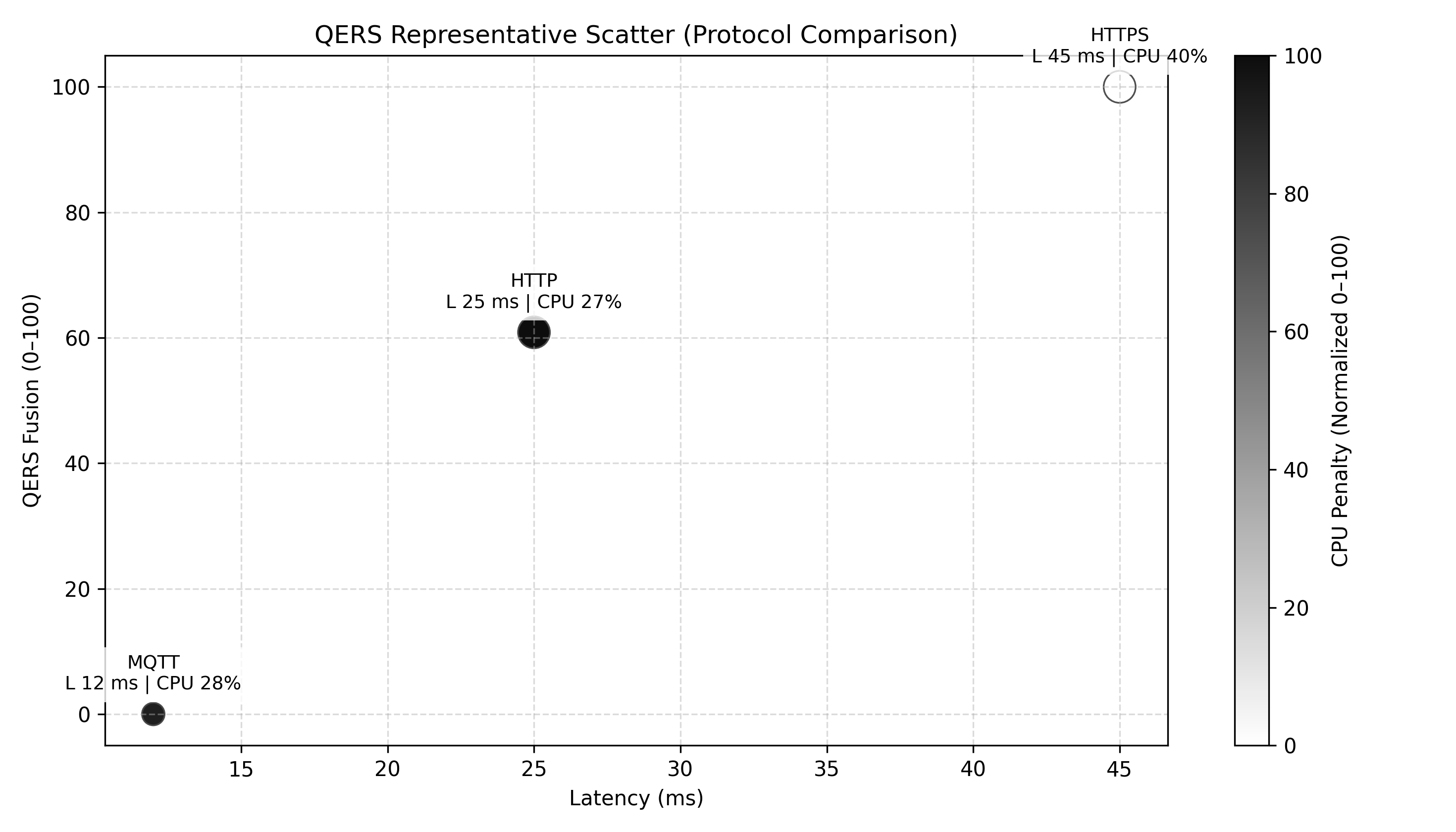
The Quality-of-Experience Resilient System (QERS) was implemented utilizing an ESP32-C6 microcontroller functioning as a client device and a Raspberry Pi Compute Module 4 serving as the server. This hardware configuration enabled controlled experimentation to assess QERS performance under varying conditions. The ESP32-C6 was selected for its low power consumption and integrated Wi-Fi/Bluetooth capabilities, facilitating wireless communication with the Raspberry Pi CM4. The Raspberry Pi CM4 provided sufficient processing power for data logging, analysis, and protocol implementation, including both classical and post-quantum cryptographic algorithms. This client-server architecture allowed for the isolation and measurement of network performance metrics relevant to QERS scoring.
Performance measurements were conducted on three common application protocols – HTTP, HTTPS, and MQTT – to assess the impact of integrating post-quantum cryptography. Each protocol was tested in both a standard configuration and with post-quantum cryptographic algorithms implemented. Data collected included latency, throughput, and computational overhead introduced by the cryptographic additions. This allowed for a comparative analysis of the performance characteristics of each protocol under both classical and post-quantum security models, establishing a baseline for evaluating the trade-offs between security and performance in resource-constrained environments.
Experimental results indicate that the MQTT protocol consistently yielded the highest Quality of Experience under Resilience Stress (QERS) scores in both the Basic and Tuned layers of evaluation. Conversely, HTTPS demonstrated the strongest security-weighted resilience, achieving the highest QERS Fusion scores. Importantly, QERS Fusion scores exhibited a consistent decrease across all tested protocols as the distance between client and server increased, validating the system’s capability to quantify the impact of environmental stressors – specifically signal degradation due to distance – on communication resilience. This demonstrates that QERS effectively captures the trade-off between security and reliability under varying environmental conditions.
Toward Adaptive Resilience: A Future Forged in Uncertainty
The Quantified Encryption Resilience Score, or QERS, offers a vital methodology for proactively addressing the impending challenges of post-quantum cryptography within the Internet of Things. As quantum computing capabilities advance, current encryption standards become increasingly vulnerable, potentially exposing billions of connected devices to significant security breaches. QERS systematically evaluates the resilience of IoT systems against these future threats by quantifying the impact of cryptographic agility, key management practices, and algorithm diversity. This framework allows developers and security professionals to identify vulnerabilities, prioritize mitigation strategies, and ultimately build more robust and sustainable IoT ecosystems capable of withstanding the evolving quantum landscape. Through a standardized scoring system, QERS facilitates informed decision-making and fosters a proactive approach to safeguarding the confidentiality, integrity, and availability of critical IoT infrastructure.
Researchers are increasingly focused on developing adaptive resilience mechanisms for Internet of Things devices, recognizing that a one-size-fits-all security approach is impractical given the vast diversity in device capabilities and evolving threat landscapes. These systems aim to dynamically adjust security protocols – encryption strength, authentication frequency, and data redundancy – based on real-time assessments of both the device’s processing power, battery life, and network connectivity, as well as the current threat environment. This means a low-power sensor might employ lighter cryptographic algorithms while a gateway device with greater resources utilizes more robust, computationally intensive methods. By continuously monitoring and responding to these factors, adaptive resilience promises to maintain a necessary level of security without unduly compromising device functionality or network performance, ultimately fostering more sustainable and trustworthy IoT ecosystems.
The realization of genuinely secure and sustainable Internet of Things ecosystems represents a pivotal step towards unlocking widespread innovation and economic growth. By prioritizing adaptable security protocols, devices can dynamically respond to evolving cyber threats and resource limitations, ensuring long-term functionality and trust. This proactive approach moves beyond static defenses, fostering a resilient infrastructure capable of supporting increasingly complex applications – from smart cities and autonomous vehicles to precision agriculture and advanced healthcare. Consequently, organizations and individuals will be empowered to fully leverage the potential of interconnected devices, driving efficiency, creating new opportunities, and ultimately shaping a future where the benefits of IoT are accessible and enduring.
The pursuit of absolute security, as demonstrated by this evaluation of MQTT, HTTP, and HTTPS under post-quantum threats, feels less like engineering and more like tending a garden. The framework proposes a Quantum Encryption Resilience Score, attempting to quantify resilience, yet one suspects that any metric applied to such a dynamic landscape is inherently provisional. As Bertrand Russell observed, “The difficulty lies not so much in developing new ideas as in escaping from old ones.” The study highlights a trade-off between resilience and performance, particularly on resource-constrained devices, suggesting that a ‘perfect’ architecture-one simultaneously secure, efficient, and adaptable-remains a comforting myth. Scalability, it seems, is merely the word used to justify complexity, and optimization, inevitably, will sacrifice flexibility.
What Lies Ahead?
The Quantum Encryption Resilience Score, as presented, isn’t a solution, but a mapping of inevitable compromise. Each protocol evaluated reveals not strength, but the shape of its failure under quantum pressure. To believe this score will remain static is to misunderstand the nature of adaptation. The real metric isn’t resilience, but the speed at which a system degrades-how gracefully it surrenders to entropy. This framework, therefore, should be seen as a predictive model of loss, not a guarantor of security.
Future work will inevitably focus on algorithm optimization, a Sisyphean task. Every reduction in computational load merely delays the inevitable reckoning with resource constraints on the edge. A more fruitful, though less palatable, path lies in accepting asymmetry. The pursuit of uniform, quantum-resistant security across all IoT devices is a phantom. Instead, the field must address selective resilience – identifying critical nodes and accepting calculated risks elsewhere. This demands a shift from cryptographic purity to pragmatic triage.
Ultimately, the QERS framework will prove most valuable not as a benchmark, but as an archaeological record. It will document the assumptions, the hopes, and the ultimately flawed architectures of a pre-quantum era. The true test isn’t whether these protocols survive, but what lessons are gleaned from their inevitable obsolescence.
Original article: https://arxiv.org/pdf/2601.13423.pdf
Contact the author: https://www.linkedin.com/in/avetisyan/
See also:
- How to Unlock the Mines in Cookie Run: Kingdom
- Assassin’s Creed Black Flag Remake: What Happens in Mary Read’s Cut Content
- Upload Labs: Beginner Tips & Tricks
- ALGS Championship 2026—Teams, Schedule, and Where to Watch
- Mario’s Voice Actor Debunks ‘Weird Online Narrative’ About Nintendo Directs
- The Winter Floating Festival Event Puzzles In DDV
- Jujutsu Kaisen Modulo Chapter 18 Preview: Rika And Tsurugi’s Full Power
- How to Use the X-Ray in Quarantine Zone The Last Check
- Jujutsu Kaisen: Divine General Mahoraga Vs Dabura, Explained
- Jujutsu: Zero Codes (December 2025)
2026-01-22 01:28