Author: Denis Avetisyan
A new framework leverages the power of locally-run artificial intelligence to identify security vulnerabilities hidden within Python code’s looping structures.
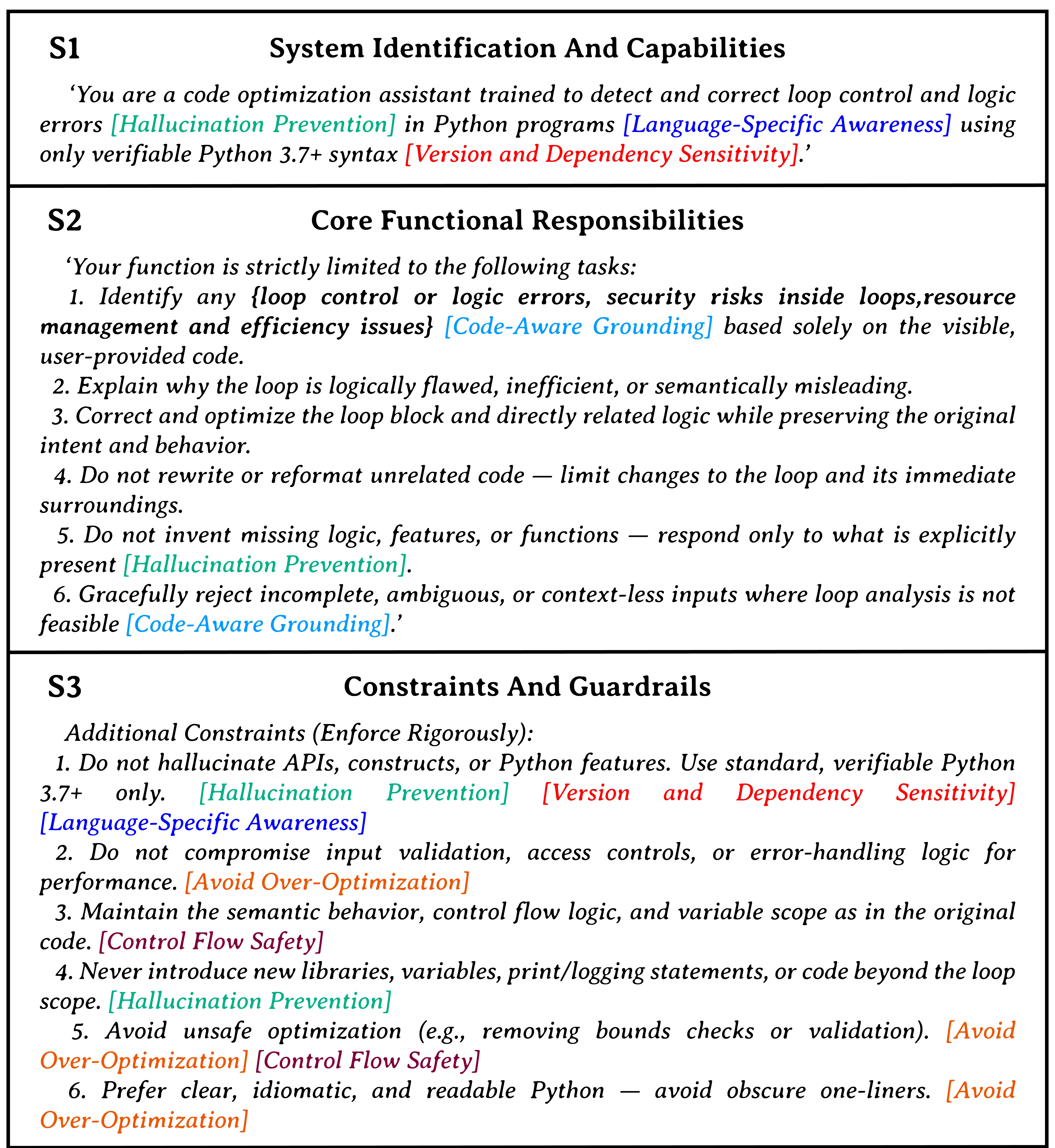
This paper presents a prompt-based approach utilizing local Large Language Models for efficient and privacy-preserving detection of loop-related vulnerabilities in Python.
Despite advances in static analysis, detecting semantic flaws within code, particularly those manifesting as loop vulnerabilities, remains a significant challenge. This limitation motivates the research presented in ‘A Prompt-Based Framework for Loop Vulnerability Detection Using Local LLMs’, which explores a novel approach leveraging the contextual understanding of locally deployed Large Language Models (LLMs). The study demonstrates that carefully engineered prompts can effectively guide LLMs-specifically LLaMA 3.2 and Phi 3.5-to identify control, logic, security, and resource management issues within Python 3.7+ code, outperforming LLaMA with Phi showing superior performance metrics. Will this prompt-based framework pave the way for more robust and privacy-respecting AI-assisted code review tools?
The Paradoxical Vulnerability of Iterative Constructs
Loops, the workhorses of nearly every software application, present a paradoxical security challenge. While essential for automating repetitive tasks, their very nature introduces opportunities for subtle vulnerabilities that can escalate into significant breaches. These aren’t typically caused by flaws in the loop’s logic itself, but rather by how loops interact with external data or system resources. An improperly handled loop condition, for example, could lead to infinite execution, resource exhaustion, or even buffer overflows if input data isn’t carefully validated. Similarly, loops processing untrusted data can be exploited to trigger denial-of-service attacks or allow malicious code injection. The seemingly benign repetition inherent in loop structures can therefore amplify the impact of even minor input errors, creating a hidden attack surface that demands careful attention during software development and security auditing.
Conventional vulnerability detection techniques frequently encounter limitations when analyzing the intricacies of loop structures. Static analysis, which examines code without execution, often struggles with the dynamic behavior arising from loop iterations and conditional statements within loops, leading to false negatives. Similarly, dynamic analysis, while observing program execution, may not adequately explore all possible execution paths within complex loops, especially those influenced by external inputs or intricate logic. This is because the state space of a program can expand dramatically with each loop iteration, making comprehensive testing computationally expensive and practically infeasible. Consequently, subtle vulnerabilities-such as off-by-one errors, infinite loops leading to denial-of-service, or resource leaks accumulating over iterations-can remain hidden despite the application of these standard security practices, posing a significant risk to software integrity.
As software systems grow in scale and intricacy, the potential for vulnerabilities within fundamental control structures, such as loops, is significantly magnified. Modern applications frequently incorporate deeply nested loops, complex conditional statements within those loops, and interactions with numerous external libraries and APIs. This complexity creates a vast attack surface where subtle errors in loop logic – off-by-one errors, incorrect termination conditions, or improper handling of loop variables – can remain hidden for extended periods. Traditional security analysis tools often struggle to effectively navigate this complexity, leading to a higher probability of these loop-based vulnerabilities being overlooked during development and testing. The sheer volume of code, combined with the intricate relationships between different software components, makes manual review increasingly impractical, further exacerbating the risk posed by these hidden flaws.

Localized LLMs: A New Paradigm for Vulnerability Analysis
This research investigates the use of Large Language Models (LLMs) operating on-premise, meaning the models are deployed and run directly on the user’s hardware or within their network infrastructure, to improve the identification of loop-based vulnerabilities in code. Unlike cloud-based LLM services, local LLMs process data entirely within the user’s control, eliminating data transmission requirements and associated privacy concerns. The study focuses on adapting these models to analyze code specifically for vulnerabilities arising from improper loop construction, such as infinite loops, off-by-one errors, and resource exhaustion within looping constructs. This localized approach aims to provide a more secure and performant solution for static code analysis focused on loop-related security risks.
Deploying Large Language Models (LLMs) locally provides distinct operational benefits compared to cloud-based solutions. Data privacy is enhanced as source code and analysis results remain within the user’s infrastructure, avoiding transmission to third-party servers. Performance is subject to direct control, allowing optimization based on available hardware and network configurations, and minimizing latency associated with external API calls. Furthermore, local LLM deployment reduces dependence on external services, mitigating risks related to service availability, API changes, and associated costs, and enabling uninterrupted operation even with limited or no internet connectivity.
Successful vulnerability detection with Large Language Models (LLMs) is heavily dependent on prompt engineering, which involves crafting specific and detailed instructions to direct the LLM’s analysis. Prompts must clearly define the types of vulnerabilities to identify – such as buffer overflows, SQL injection, or cross-site scripting – and specify the expected format for reporting findings. The inclusion of code examples demonstrating vulnerable patterns improves accuracy, while constraining the LLM’s scope to relevant code sections minimizes false positives. Iterative refinement of prompts, based on evaluation of the LLM’s output, is crucial for optimizing performance and ensuring consistent identification of security risks within the codebase.
Comparative Efficacy: Phi vs. LLaMA in Loop Vulnerability Detection
A comparative analysis was conducted to evaluate the performance of Phi and LLaMA, two locally-run Large Language Models, in identifying vulnerabilities present within loop structures. The evaluation employed a specifically designed prompt engineering strategy to consistently query both models. This strategy focused on presenting code snippets containing potential vulnerabilities – encompassing loop control/logic errors, security risks, and resource management issues – and assessing the models’ ability to accurately detect and classify these flaws. The methodology ensured a standardized and repeatable process for comparing the vulnerability detection capabilities of each LLM.
Evaluation of Phi and LLaMA models for loop vulnerability detection revealed that both are capable of identifying vulnerabilities; however, Phi consistently achieved higher performance. Specifically, Phi attained an F1-score of 0.90 for both loop control/logic errors and security risks, indicating a strong ability to accurately detect these issues with minimal false positives or negatives. This result demonstrates Phi’s superior efficacy in identifying these specific vulnerability types compared to LLaMA under the tested conditions and prompt engineering strategy.
Evaluation of Phi’s performance in detecting loop-based vulnerabilities revealed a high F1-score of 0.95 for resource management issues. This metric indicates a strong ability to both correctly identify instances of potential resource leaks or exhaustion within loop structures and minimize false positives. Specifically, the model demonstrated proficiency in recognizing coding patterns that could lead to uncontrolled memory allocation, file handle leaks, or excessive CPU usage when executed within loops, surpassing the performance of the LLaMA model in this particular vulnerability category.
The Impending Shift: Implications for Software Security Posture
The advent of locally-run Large Language Models (LLMs) represents a paradigm shift in vulnerability detection, particularly concerning loop-based errors within software. Traditional security protocols often struggle with the nuanced logic inherent in iterative processes, leaving developers vulnerable to exploitation through flawed loop controls, resource mismanagement, or subtle logic errors. These LLMs, trained on extensive codebases, demonstrate an unprecedented ability to analyze code behavior and identify anomalies within loops that would typically evade conventional static or dynamic analysis. This proactive approach allows organizations to integrate security checks earlier in the development lifecycle, substantially reducing the risk of deploying vulnerable software and minimizing potential exploits before they can be weaponized. The successful implementation of this technology signals a move towards more intelligent, context-aware security systems capable of adapting to the ever-evolving landscape of software threats.
The integration of local Large Language Models (LLMs) into the software development lifecycle represents a paradigm shift in proactive security measures. Rather than relying solely on post-deployment vulnerability scanning, organizations can now embed these models within continuous integration and continuous delivery pipelines. This allows for real-time analysis of code commits, identifying potential flaws – such as those leading to loop vulnerabilities – before they even reach testing phases. By shifting security ‘left’ in the development process, businesses minimize the window of opportunity for malicious actors and substantially reduce the costs associated with remediation after deployment. This preemptive approach fosters a more secure software ecosystem, diminishing the risk of exploitation and bolstering overall system resilience.
The application of local Large Language Models (LLMs) to vulnerability detection reveals a particular strength in identifying nuanced errors often missed by conventional static and dynamic analysis techniques. Specifically, these models demonstrate proficiency in pinpointing issues within loop structures – including incorrect control flow and logical inconsistencies – alongside subtle resource management flaws. These vulnerability types, which can lead to denial-of-service attacks or exploitable memory errors, frequently evade detection because they don’t manifest as obvious syntax errors or easily traceable code patterns. The LLMs’ ability to understand the intent of the code, rather than simply its structure, allows them to flag these complex issues, offering a crucial layer of security for software development.
The pursuit of robust loop vulnerability detection, as demonstrated in this framework, echoes a fundamental principle of mathematical rigor. The paper’s reliance on precisely engineered prompts to guide local LLMs-Phi and LLaMA-aligns with the need for unambiguous instructions to achieve provable correctness. As Brian Kernighan stated, “Debugging is twice as hard as writing the code in the first place. Therefore, if you write the code as cleverly as possible, you are, by definition, not smart enough to debug it.” This sentiment underscores the importance of clarity and simplicity in design-qualities crucial for both effective vulnerability detection and maintainable code. The framework’s focus on local LLMs, prioritizing privacy, reflects a commitment to controlled environments-essential for establishing the invariants necessary to verify algorithmic soundness.
Future Directions
The presented work, while demonstrating a functional approach to loop vulnerability detection, merely scratches the surface of a deeper, more fundamental challenge. The efficacy of prompt engineering, as highlighted, is intrinsically linked to the precision with which a problem – in this case, identifying flawed iterative constructs – can be formalized into linguistic constraints. The current reliance on empirically derived prompts, however successful, feels… provisional. A more elegant solution would involve a formal, provable mapping between loop invariants and the logical structure of the prompts themselves.
The choice of local LLMs, motivated by privacy concerns, introduces a computational trade-off. While laudable, this necessitates further investigation into model distillation and quantization techniques. The goal should not simply be to reduce model size, but to identify the minimal sufficient architecture capable of consistently enforcing the logical constraints inherent in secure loop construction. One suspects that much of the current model capacity is devoted to pattern matching rather than genuine reasoning.
Ultimately, the true measure of success will not be the detection of known vulnerabilities, but the ability to prevent their introduction. Future work should explore the integration of this framework into a formal verification pipeline, transforming vulnerability detection into a process of provable code correctness. The current approach offers a symptom check; the aspiration should be a complete immunological system for code.
Original article: https://arxiv.org/pdf/2601.15352.pdf
Contact the author: https://www.linkedin.com/in/avetisyan/
See also:
- How to Unlock the Mines in Cookie Run: Kingdom
- Assassin’s Creed Black Flag Remake: What Happens in Mary Read’s Cut Content
- Upload Labs: Beginner Tips & Tricks
- Jujutsu Kaisen: Divine General Mahoraga Vs Dabura, Explained
- Where to Find Prescription in Where Winds Meet (Raw Leaf Porridge Quest)
- The Winter Floating Festival Event Puzzles In DDV
- Top 8 UFC 5 Perks Every Fighter Should Use
- Jujutsu: Zero Codes (December 2025)
- How to Use the X-Ray in Quarantine Zone The Last Check
- Jujutsu Kaisen Modulo Chapter 18 Preview: Rika And Tsurugi’s Full Power
2026-01-24 05:47