Author: Denis Avetisyan
New research reveals a successful wireless Man-in-the-Middle attack against CCS EV charging stations, highlighting critical vulnerabilities in current security protocols.
The study demonstrates a real-world exploit leveraging the HomePlug Green PHY communication standard within the ISO 15118 protocol, potentially allowing manipulation of power delivery to electric vehicles.
Despite the rapid adoption of Electric Vehicles, the security of their charging infrastructure remains surprisingly vulnerable. This paper, ‘DCeption: Real-world Wireless Man-in-the-Middle Attacks Against CCS EV Charging’, details the first successful real-time Software-Defined Radio implementation of attacks against the Combined Charging System (CCS), exploiting wireless leakage in the HomePlug Green PHY communication protocol. We demonstrate that a malicious actor can not only hijack communication with a charging vehicle, but also manipulate power delivery information-causing a vehicle to falsely display excessive charging power or even remotely overcharge-with limited detection. Given these demonstrated vulnerabilities, how can the CCS protocol be effectively secured against increasingly sophisticated wireless attacks and ensure the safety of EV charging?
The Expanding Attack Surface of EV Charging
The rapid proliferation of electric vehicles, while promising a sustainable future, simultaneously expands the potential surface area for cyberattacks. As reliance on EV charging infrastructure grows, so too does the opportunity for malicious actors to exploit vulnerabilities within these systems. Unlike traditional fueling stations, EV charging relies heavily on digital communication between the vehicle, the charging station, and often, a central network. This interconnectedness introduces new attack vectors – ranging from compromising user credentials to manipulating the charging process itself. Consequently, charging infrastructure is becoming an increasingly attractive target, not only for data breaches – potentially exposing personal and financial information – but also for acts of sabotage that could disrupt power grids or even cause physical harm to vehicle owners, demanding a proactive and layered security approach.
The widespread deployment of Electric Vehicle (EV) charging infrastructure, particularly systems utilizing the Combined Charging System (CCS), introduces inherent security challenges due to the communication protocols employed. These protocols, designed primarily for functionality rather than robust security, are susceptible to interception and manipulation by malicious actors. Data transmitted during the charging process – including authentication credentials and energy usage information – can be compromised if not adequately protected. More concerningly, vulnerabilities within the communication framework could enable attackers to exert control over the power delivery to a vehicle, potentially causing damage to the EV, the charging station, or even posing a safety risk to users. The reliance on protocols that weren’t initially conceived with cybersecurity as a primary concern necessitates a critical re-evaluation of charging station security and the implementation of enhanced protection mechanisms.
The vulnerabilities within EV charging communication protocols extend beyond simple data compromise; malicious actors gaining control of the charging process present a tangible physical risk. An attacker intercepting or manipulating communications could potentially overload the vehicle’s battery, causing damage or even creating a fire hazard. Furthermore, compromised systems could be leveraged to disrupt the power grid by rapidly cycling power demands or initiating widespread charging surges. Beyond the immediate danger to individual vehicles, this control over power delivery opens the door to ransomware attacks targeting charging networks, demanding payment to restore functionality and prevent infrastructure damage – a scenario that highlights the critical need for robust security measures beyond simple data encryption.
While EV charging infrastructure often implements security protocols like Transport Layer Security (TLS) to encrypt communication and ensure data integrity, these defenses are proving insufficient against sophisticated attacks. Research demonstrates vulnerabilities in how TLS is implemented within charging stations and management systems, allowing malicious actors to perform downgrade attacks – forcing the connection to use weaker, less secure encryption standards. This circumvention of robust security leaves sensitive user data, such as payment information and charging history, exposed to interception. Furthermore, attackers can exploit these downgraded connections to manipulate charging parameters, potentially causing damage to the vehicle, the charging station, or even disrupting the power grid, highlighting a critical need for more resilient security architectures beyond standard TLS implementation.
CCS Communication: A Deep Dive into HomePlug Green PHY
The Combined Charging System (CCS) employs HomePlug Green PHY as its physical layer technology, defining the electrical and data transmission characteristics for communication between the electric vehicle (EV) and the charging station. This standardized approach facilitates data exchange necessary for charge negotiation, authentication, and real-time monitoring of the charging process. Specifically, HomePlug Green PHY operates in the 4.6 to 8.8 MHz frequency band, utilizing Frequency Shift Keying (FSK) modulation to transmit digital information over existing power line infrastructure. This choice allows for cost-effective communication without requiring dedicated data lines, leveraging the existing power cables for both energy transfer and control signaling. The protocol’s design prioritizes low data rates and robustness against noise inherent in power line environments, suitable for the relatively limited bandwidth requirements of EV charging communication.
Signal Level Attenuation Characterization (SLAC) is a critical initial phase in establishing communication via HomePlug Green PHY, wherein the Electric Vehicle (EV) and the charger negotiate signal strength to ensure reliable data transmission. This process involves the exchange of specific signaling packets that reveal information about the communication channel. Analysis indicates that vulnerabilities exist within the SLAC handshake, allowing a malicious actor to inject or modify these packets. Successful manipulation of the SLAC exchange can disrupt the connection process, potentially allowing unauthorized access or control over communication parameters, and enabling further exploitation of the communication channel.
The Service Discovery Protocol (SDP) is a foundational element in establishing communication between an Electric Vehicle (EV) and its charging station, facilitating the exchange of information necessary to define the communication channel parameters. Specifically, SDP negotiations determine the supported services and associated attributes, including data transfer rates and security configurations. Vulnerabilities within the SDP implementation allow for manipulation of these parameters, potentially enabling an attacker to downgrade security protocols, inject malicious data, or disrupt the communication link. Successful exploitation of SDP weaknesses can occur during the initial handshake phase, before secure communication is established, making it a critical attack vector for compromising the CCS communication channel.
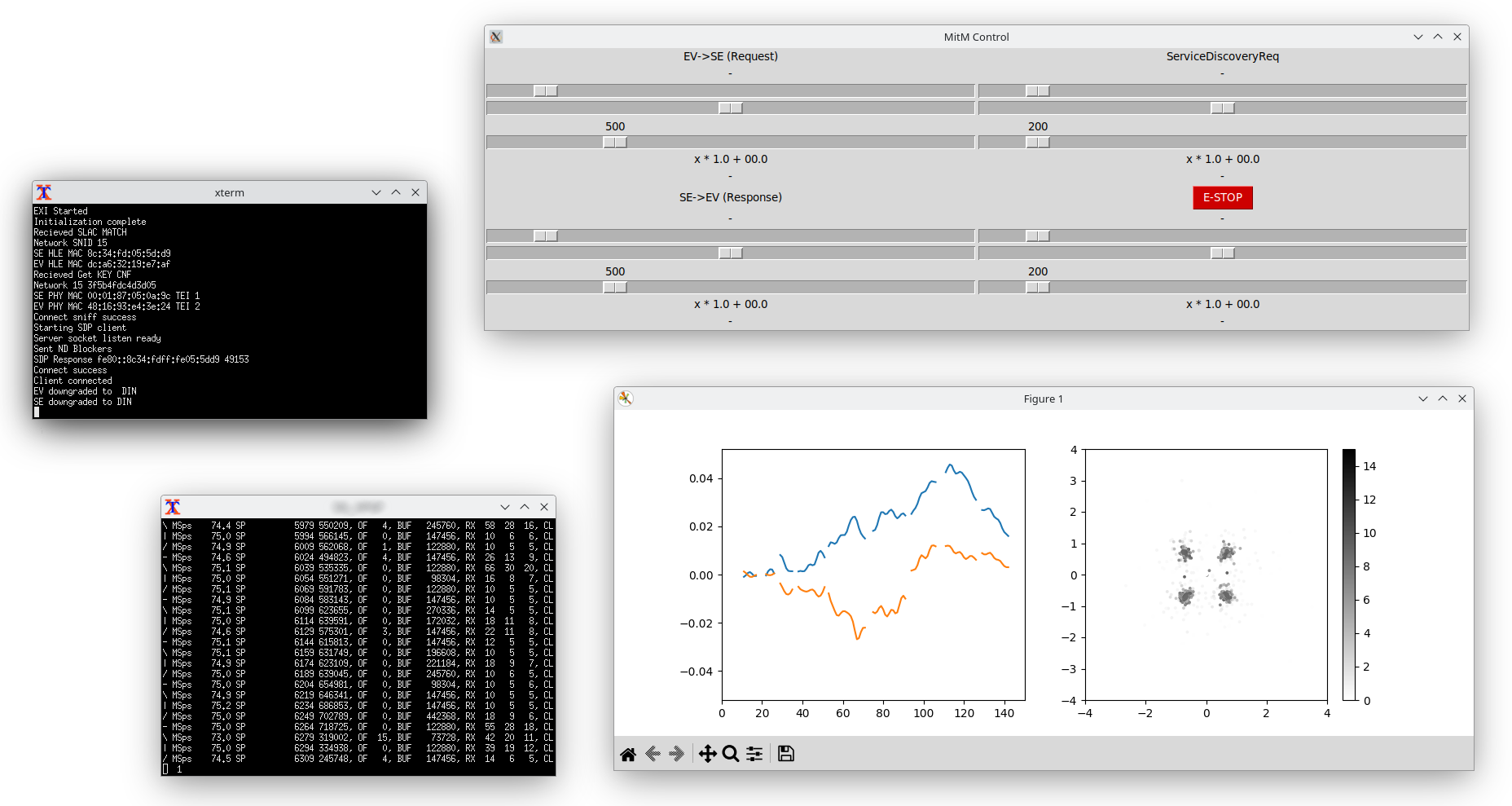
A Software-Defined Radio (SDR) implementation was utilized to gain complete bidirectional access to the physical layer of HomePlug Green PHY communication. This access facilitated a detailed analysis of the protocol, revealing specific vulnerabilities within the packet structure and control mechanisms. Consequently, real-time control over communication packets became possible, allowing for manipulation of data transmitted between the Electric Vehicle (EV) and the charging station. The SDR setup enabled both transmission and reception of modified packets, confirming the ability to actively interfere with the standard communication process and potentially exploit identified weaknesses.
Demonstrating the Threat: MitM Attacks and Protocol Exploitation
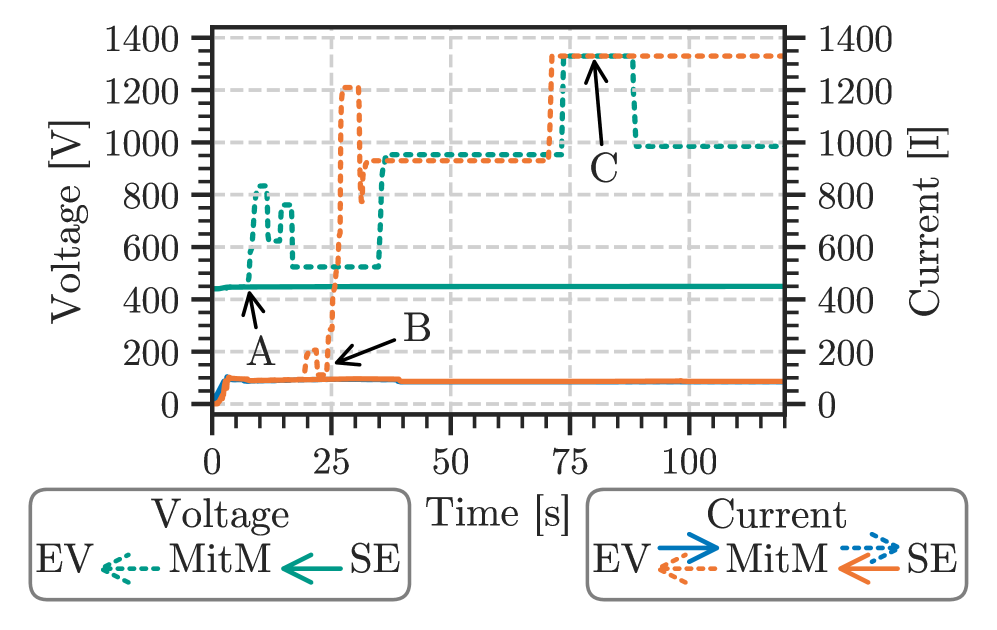
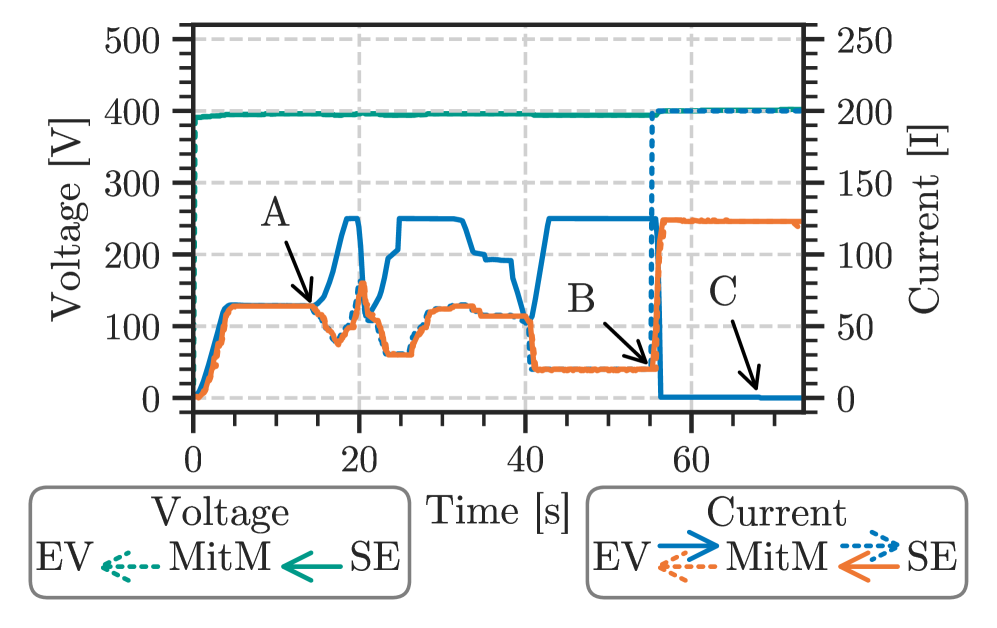
A successful wireless Man-in-the-Middle (MitM) attack was demonstrated against the Combined Charging System (CCS). This attack intercepted communication between an electric vehicle (EV) and a charging station, allowing for modification of data in transit. The demonstrated attack proves the feasibility of an external actor disrupting the charging process and potentially gaining unauthorized control or access to vehicle systems through manipulation of communication protocols. Successful interception and modification confirm a vulnerability in the wireless communication link between the EV and charger, highlighting the need for robust security measures.
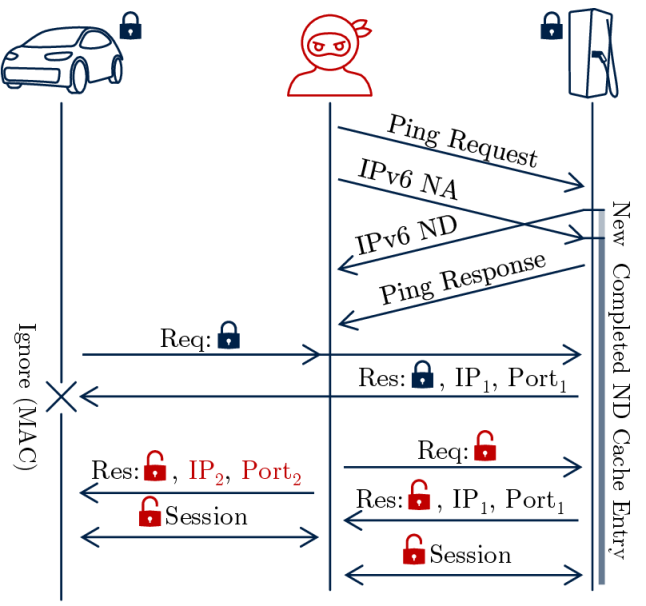
Neighbor Advertisement (NA) spoofing functions as a critical component in establishing a Man-in-the-Middle (MitM) attack against Charge Communication Systems (CCS). This technique involves the attacker broadcasting wireless messages that falsely advertise their presence as a legitimate charging station. By manipulating the signal strength and timing of these NA messages, the attacker redirects communication traffic intended for the actual charging station to their own system. Successful redirection allows the attacker to intercept, and subsequently modify, Secure Device Pairing (SDP) requests and responses, effectively hijacking the pairing process and positioning themselves as the trusted intermediary between the Electric Vehicle (EV) and the charger. This compromised position enables further exploitation of communication parameters and potential malicious actions.
Successful exploitation of the Security Data Parameter (SDP) protocol enables manipulation of critical communication parameters between the Electric Vehicle (EV) and the charging station. Specifically, an attacker can alter settings governing authentication, authorization, and data exchange rates. This capability allows for the potential bypass of security measures, granting unauthorized access to vehicle systems or the charging infrastructure. Furthermore, manipulated parameters can facilitate the injection of malicious data into the communication stream, potentially leading to compromised vehicle functionality, fraudulent charging sessions, or disruption of grid services. The attacker’s control over these parameters is not limited to simple modification; complete substitution of valid parameters with attacker-defined values is also possible.
The Software Defined Radio (SDR) implementation utilized in the attack consistently transmitted packets with lower latency than both the Electric Vehicle (EV) and the Charging Station. This prioritized transmission enabled a faster attack setup by allowing the attacker to establish a connection and begin spoofing legitimate communications before the expected response from authorized devices. Specifically, the SDR’s ability to preemptively send Neighbor Advertisement (NA) spoofing packets facilitated successful redirection of communication traffic. This timing advantage demonstrates a critical vulnerability in the system, as it reduces the window for detection and allows the attacker to effectively hijack the Secure Device Provisioning (SDP) process before legitimate devices can assert control of the communication channel.
Strengthening EV Charging: A New Approach to Security
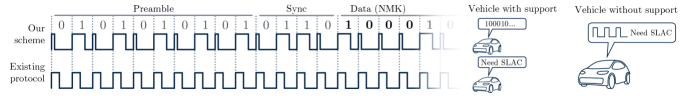
Electric vehicle charging relies on a communication protocol where the Control Pilot signal dictates whether charging can commence, but a novel application of this established channel offers a pathway to enhanced security. Researchers propose repurposing the Control Pilot signal not merely for charge control, but as a supplementary data stream for authentication and integrity verification. This innovative approach encodes security credentials directly within the existing signal, creating a secondary communication path that is inherently resistant to many common attack vectors. By cleverly utilizing pre-existing infrastructure, this method avoids the substantial costs and logistical hurdles associated with deploying entirely new security systems, offering a pragmatic and effective solution to fortify the growing EV charging network against malicious interference and ensure a safer user experience.
The vulnerability of electric vehicle (EV) charging to Man-in-the-Middle (MitM) attacks stems from the potential for malicious actors to intercept and manipulate communication between the vehicle and the charging station. To address this, researchers propose a novel security enhancement that repurposes the Control Pilot (CP) signal-traditionally used to regulate charging current-as a dedicated channel for authentication and integrity verification. By embedding cryptographic checks within the CP signal’s waveform, the system establishes a secure handshake, confirming the legitimacy of both the charging station and the vehicle before any power transfer occurs. This effectively creates a secondary, hardware-based security layer that is exceedingly difficult for attackers to spoof or bypass, even if the primary communication channels are compromised, bolstering the overall resilience of the EV charging infrastructure.
A significant advantage of this security enhancement lies in its compatibility with currently deployed electric vehicle charging infrastructure. Rather than demanding costly and disruptive overhauls of existing stations, the proposed system ingeniously repurposes the Control Pilot signal – already a standard component of the charging process – to transmit authentication and integrity data. This strategic utilization minimizes implementation barriers and associated expenses, allowing for a relatively seamless integration of improved security measures. Consequently, widespread adoption becomes far more feasible, protecting a larger number of charging points and electric vehicles without imposing substantial financial burdens or operational disruptions on charging network providers.
The integration of a bolstered security protocol into electric vehicle (EV) charging infrastructure promises a significantly safer and more dependable experience for users. Current systems, while functional, present vulnerabilities to malicious interference, potentially compromising both vehicle and grid stability. This new approach actively mitigates these risks by layering authentication and integrity checks directly into the established communication pathways between the vehicle and charging station. Consequently, the likelihood of successful “man-in-the-middle” attacks is dramatically reduced, fostering greater trust in public charging networks and paving the way for wider EV adoption. This proactive defense not only safeguards sensitive data but also ensures the consistent and reliable delivery of power, ultimately contributing to a more robust and secure energy ecosystem.
The pursuit of seamless EV charging, as detailed in this dissection of CCS vulnerabilities, feels remarkably like building a more elaborate Rube Goldberg machine. Each layer of communication, each attempt at standardization, introduces another point of failure. It’s almost comforting, really. Grace Hopper observed, “It’s easier to ask forgiveness than it is to get permission.” This rings true; the industry rushes toward ‘innovation’ – complex protocols like ISO 15118 – before adequately securing the basics. The researchers demonstrate a wireless MitM attack via HomePlug Green PHY; a predictable outcome, honestly. They didn’t break the idea of fast charging, just the illusion of security around it. One suspects future archaeologists will find this paper alongside diagrams of perfectly predictable exploits, wondering what we were thinking. It’s not a bug; it’s a feature, ensuring job security for security researchers for decades to come.
What’s Next?
The demonstrated susceptibility of CCS charging infrastructure to wireless Man-in-the-Middle attacks, while concerning, feels less like a revelation and more like a predictable outcome. Every abstraction dies in production, and the convenient complexity of power delivery – the blending of communication protocols, physical layer quirks of HomePlug Green PHY, and the imperative of rapid charging – was always going to present an attractive target. The work highlights not a failure of security design per se, but the inevitable friction between theoretical robustness and the realities of deployed systems.
Future efforts will undoubtedly focus on hardening the ISO 15118 protocol and implementing more aggressive cryptographic measures. Yet, the fundamental problem remains: a compromised physical layer bypasses much of that application-level security. The next iteration of attacks won’t necessarily target the protocol itself, but the signal. Expect research to explore jamming resistance, side-channel analysis of the HomePlug Green PHY, and the feasibility of active deception – creating phantom charging stations to lure vulnerable vehicles.
Ultimately, this research serves as a reminder that security is not a destination, but a perpetual state of structured panic. The elegance of a secure system is only ever temporary. Everything deployable will eventually crash, and in this case, that crash could involve manipulated power delivery and compromised vehicle systems. The question isn’t whether these attacks will be exploited, but when, and how creatively.
Original article: https://arxiv.org/pdf/2601.15515.pdf
Contact the author: https://www.linkedin.com/in/avetisyan/
See also:
- How to Unlock the Mines in Cookie Run: Kingdom
- Assassin’s Creed Black Flag Remake: What Happens in Mary Read’s Cut Content
- Jujutsu Kaisen: Divine General Mahoraga Vs Dabura, Explained
- The Winter Floating Festival Event Puzzles In DDV
- Upload Labs: Beginner Tips & Tricks
- Top 8 UFC 5 Perks Every Fighter Should Use
- Jujutsu: Zero Codes (December 2025)
- Xbox Game Pass Officially Adds Its 6th and 7th Titles of January 2026
- Where to Find Prescription in Where Winds Meet (Raw Leaf Porridge Quest)
- MIO: Memories In Orbit Interactive Map
2026-01-24 22:24