Author: Denis Avetisyan
A new FPGA implementation dramatically accelerates the FrodoKEM post-quantum cryptographic algorithm, offering a practical path towards quantum-resistant security.
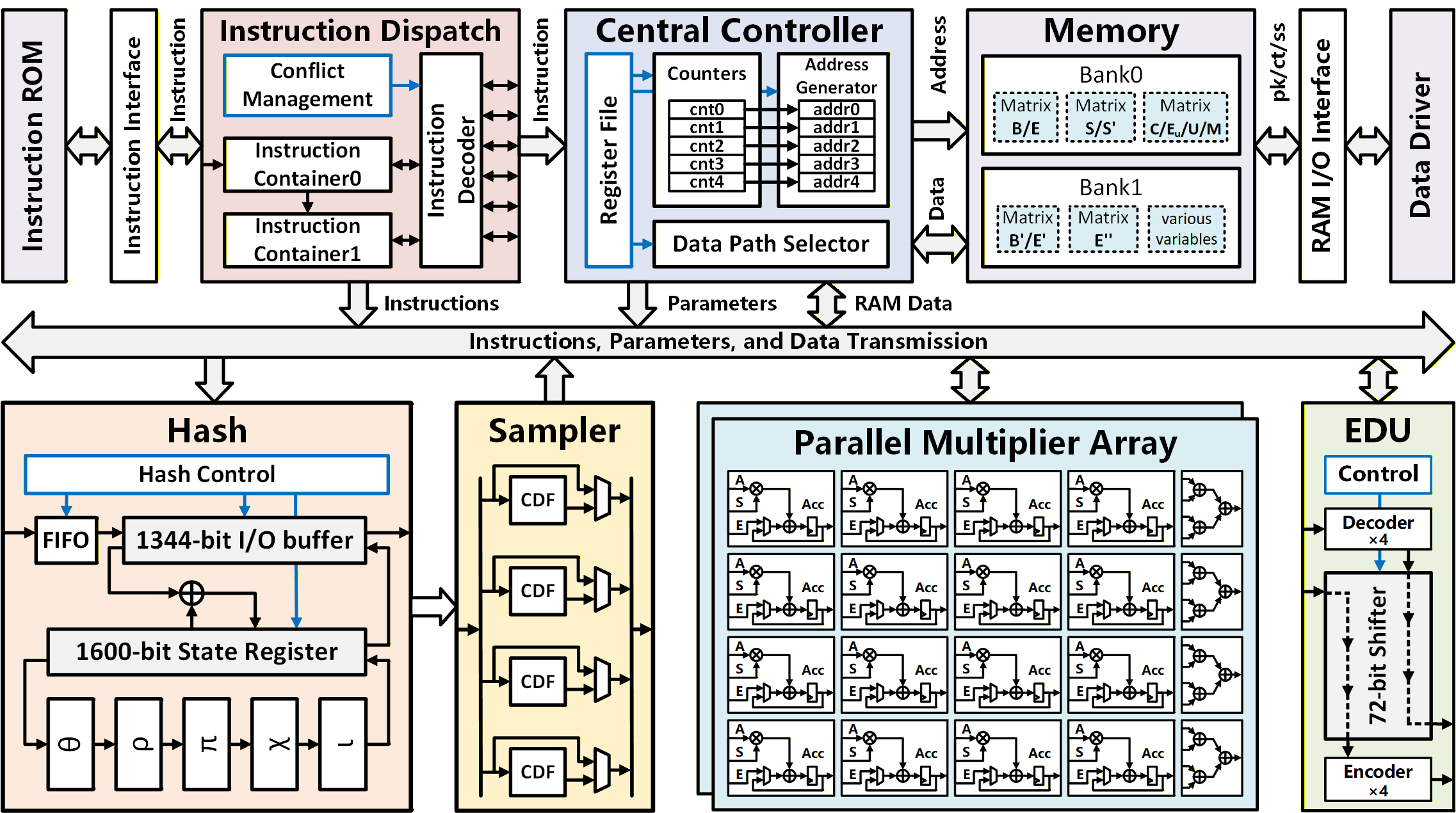
This work details a high-performance and efficient hardware architecture for FrodoKEM, leveraging parallelization and memory optimization techniques.
While the promise of post-quantum cryptography offers resilience against future computational threats, practical implementations of lattice-based schemes often suffer from performance bottlenecks and resource constraints. This paper presents a high-performance and efficient crypto-processor for FrodoKEM, a leading post-quantum key encapsulation mechanism, addressing these limitations through architectural innovations. Specifically, a reconfigurable parallel multiplier array, coupled with optimized memory scheduling and overlapped execution, significantly reduces latency and resource utilization on an Artix-7 FPGA. Does this design represent a viable path toward widespread adoption of post-quantum cryptography in resource-constrained environments?
The Looming Quantum Threat and the Promise of Lattice-Based Security
The bedrock of modern digital security, public-key cryptosystems such as RSA and Elliptic Curve Cryptography (ECC), face an existential threat from the rapidly advancing field of quantum computing. These systems rely on the computational difficulty of certain mathematical problems – factoring large numbers for RSA and solving the discrete logarithm problem for ECC – which classical computers struggle with. However, Shor's\,algorithm, a quantum algorithm, can efficiently solve both of these problems, rendering RSA and ECC insecure. This vulnerability necessitates a proactive shift towards post-quantum cryptography – developing and implementing cryptographic systems that are resistant to attacks from both classical and quantum computers. The stakes are high, as a successful quantum attack could compromise sensitive data, disrupt financial systems, and undermine national security, driving intense research and standardization efforts in this critical field.
Lattice-based cryptography distinguishes itself as a frontrunner in post-quantum security due to the challenging nature of the mathematical problems upon which it is built. These systems rely on the perceived intractability of solving certain problems involving lattices – regular arrangements of points in space. Specifically, problems like the Shortest Vector Problem (SVP) and the Closest Vector Problem (CVP) are believed to be exceptionally difficult for both classical and quantum computers to solve efficiently. While classical algorithms struggle with the exponential growth in complexity as lattice dimensions increase, current quantum algorithms offer, at best, only a modest speedup, suggesting a significant margin of safety. This inherent resistance stems from the fact that these lattice problems aren’t easily susceptible to the algorithmic breakthroughs – like Shor’s algorithm for factoring or Grover’s algorithm for searching – that threaten widely used cryptosystems such as RSA and ECC. Consequently, lattice-based approaches offer a pathway toward cryptographic security in a future where quantum computers pose a genuine threat to existing infrastructure.
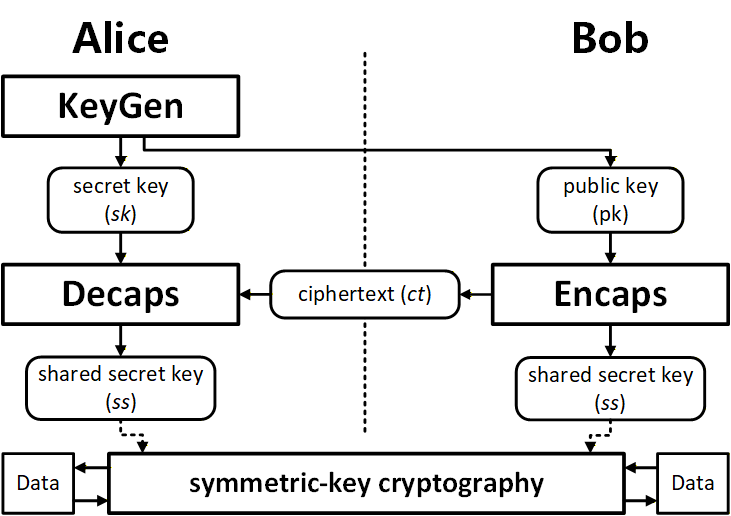
FrodoKEM represents a significant stride in post-quantum cryptography, functioning as a key encapsulation mechanism designed to securely exchange cryptographic keys even in the face of quantum computing threats. Built upon the presumed intractability of solving certain mathematical problems involving lattices – high-dimensional arrangements of points – FrodoKEM offers a compelling alternative to currently used public-key systems like RSA and ECC, which are vulnerable to Shor’s algorithm on quantum computers. The algorithm’s security stems from the difficulty of finding short vectors within these lattices, a problem believed to be resistant to both classical and quantum attacks. Currently a leading candidate in the NIST post-quantum cryptography standardization process, FrodoKEM distinguishes itself through its conservative design and reliance on well-studied lattice assumptions, aiming for a pragmatic balance between security and performance as the cryptographic landscape shifts toward a post-quantum future.
Accelerating Post-Quantum Security: Hardware Optimization for FrodoKEM
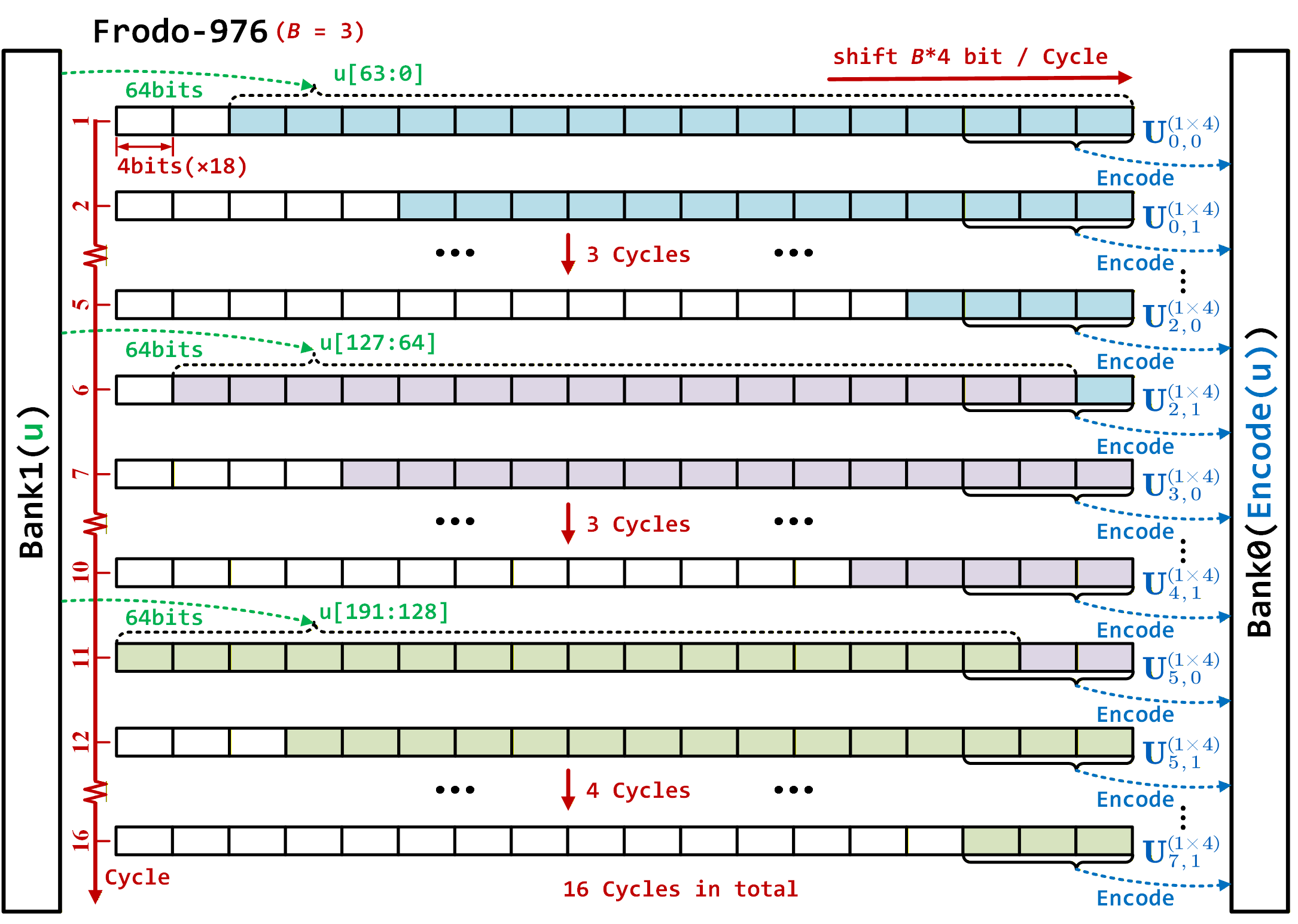
The FrodoKEM key encapsulation mechanism relies heavily on polynomial multiplications performed in \mathbb{Z}_q[x]/f(x) , which translate to a substantial number of matrix multiplications when implemented. Profiling reveals that these matrix operations contribute over 90% of the total execution time for typical parameter sets. Consequently, achieving practical performance for FrodoKEM necessitates dedicated hardware acceleration. General-purpose processors are insufficient to handle the computational load within acceptable timeframes for real-world applications, particularly concerning latency-sensitive scenarios. Therefore, specialized hardware architectures are crucial to reduce execution time and enable efficient implementation of the FrodoKEM algorithm.
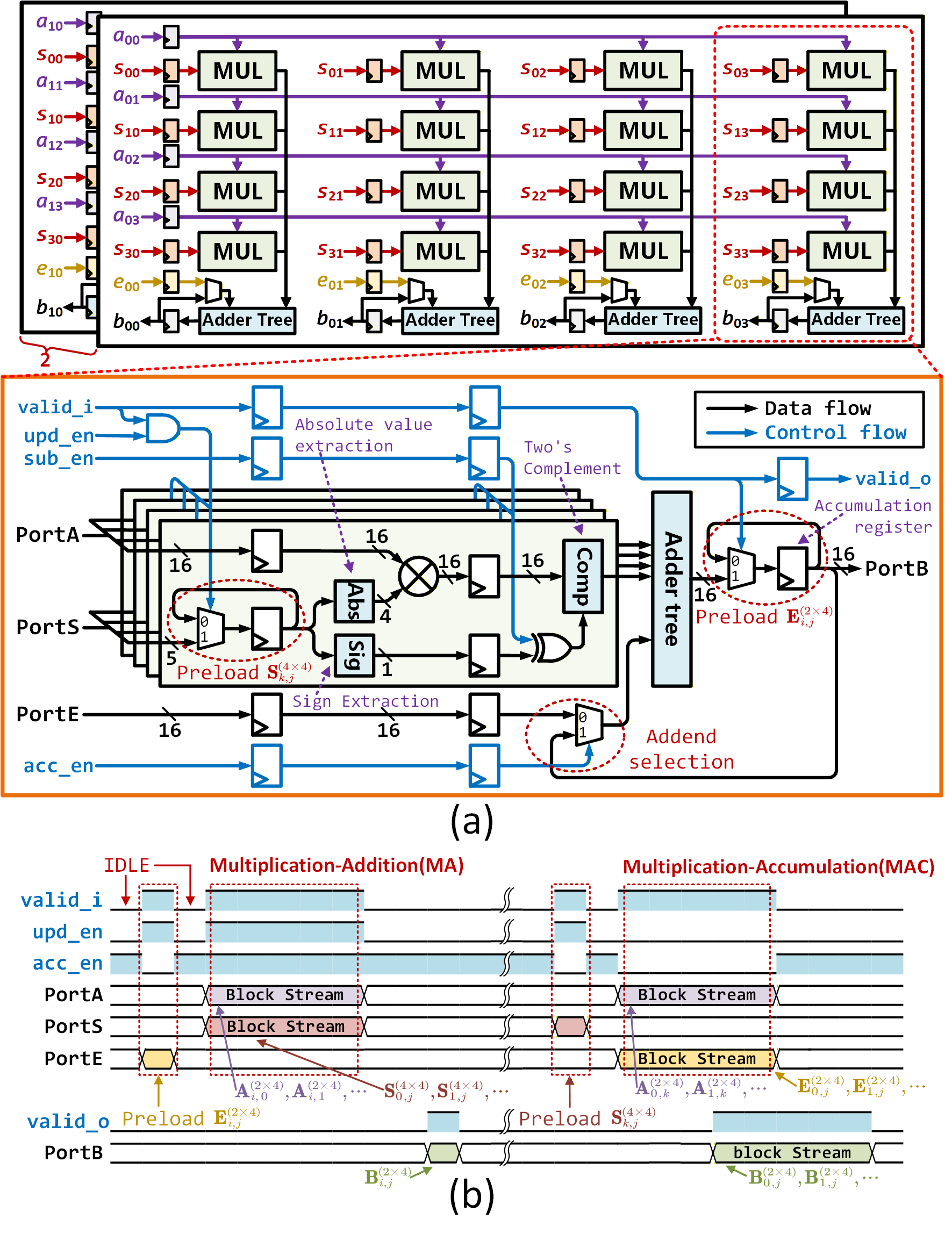
A custom Parallel Multiplier Array (PMA) was developed to address the computational bottleneck imposed by the numerous matrix multiplications within the FrodoKEM key encapsulation mechanism. This architecture consists of multiple multiplier units operating in parallel, enabling simultaneous calculations on different elements of the matrices. Benchmarks demonstrate that the PMA achieves a significant speedup compared to implementations relying on general-purpose central processing units (CPUs) and digital signal processing (DSP) blocks. The degree of parallelism within the PMA is configurable, allowing for trade-offs between hardware resource utilization and performance based on the specific implementation constraints. This parallel processing approach substantially reduces the overall execution time for FrodoKEM operations, making hardware acceleration a critical component for practical deployment.
The implementation of a Sign Extraction technique within the parallel multiplier array avoids the necessity of dedicated Digital Signal Processing (DSP) blocks. DSP blocks are typically resource-intensive in hardware due to their complex internal architectures and high power consumption. By extracting the sign bit during multiplication and utilizing this information to reconstruct the final result, the design bypasses the need for these complex blocks. This simplification directly translates to a reduction in hardware complexity, leading to a smaller footprint and lower power consumption for the overall FrodoKEM implementation. The technique focuses on efficiently handling the sign information without requiring the full precision of standard DSP operations.
Refining Dataflow for Optimal Performance: Strategies for Efficiency
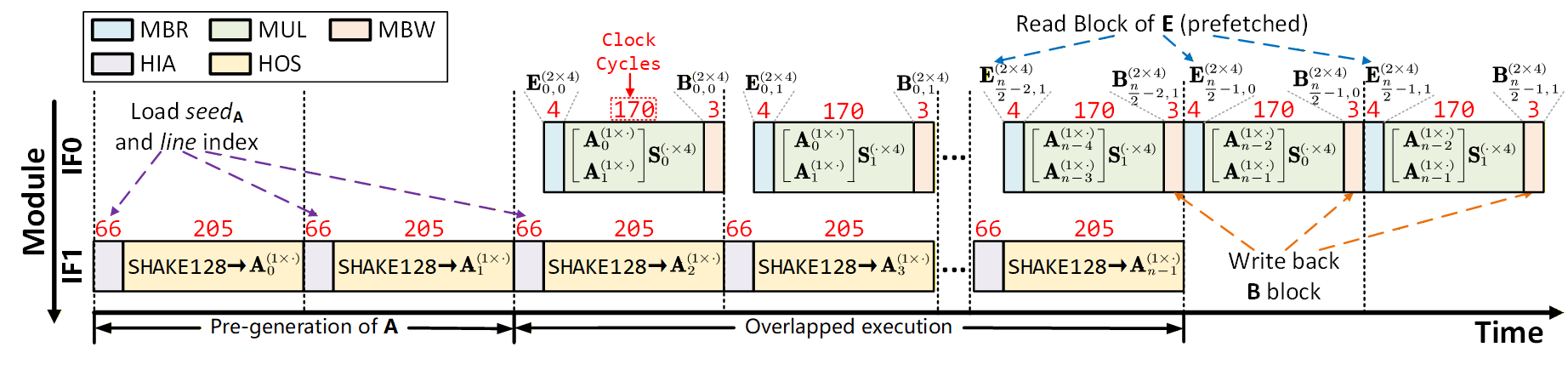
Multiple-Instruction Overlapped Execution (MIOE) is a technique used to enhance processing throughput by executing independent instructions concurrently. This is achieved by identifying operations that have no data dependencies and scheduling them to run in parallel, effectively utilizing available processing resources. Implementation of MIOE within the system resulted in a measured speedup of 1.65x compared to sequential execution of the same operations, demonstrating a significant performance gain through increased instruction-level parallelism.
Compact Memory Scheduling is a technique used to reduce Block RAM (BRAM) utilization by minimizing the storage duration of intermediate variables within a dataflow graph. This is achieved by strategically overlapping read and write operations and reusing memory locations whenever possible. A common implementation utilizes Ping-Pong Buffering, where two memory buffers are alternated for reading and writing data; while one buffer is being processed, the other is filled with new data, effectively extending the lifespan of data without requiring additional memory allocation. This approach reduces the overall BRAM footprint and improves resource utilization, particularly crucial in FPGA implementations with limited on-chip memory.
AXI DMA, or Advanced eXtensible Interface Direct Memory Access, facilitates high-throughput data transfer between external memory and the processing core without CPU intervention. This is achieved by allowing the DMA controller to independently manage data transfers, bypassing the core and reducing latency associated with software-driven data movement. By offloading data transfer tasks, the processing core remains available for computations, increasing overall system performance. AXI DMA supports burst transfers, maximizing bandwidth utilization and minimizing overhead.
Toward a Post-Quantum Future: Implementation and the Path Forward
A processor implementing the FrodoKEM key-encapsulation mechanism has been successfully realized on an Artix-7 field-programmable gate array (FPGA) utilizing High-Level Synthesis (HLS) techniques. This approach facilitated accelerated design exploration and validation, allowing for a rapid transition from algorithm specification to a functioning hardware implementation. The resulting design operates at a maximum frequency of 207 MHz, demonstrating the potential for high-throughput post-quantum cryptographic operations directly in hardware. By leveraging HLS, developers can efficiently prototype and optimize FrodoKEM for diverse applications, paving the way for practical deployment of quantum-resistant security solutions.
A recent implementation of the FrodoKEM algorithm on Field-Programmable Gate Array (FPGA) hardware demonstrates a significant advancement in the practicality of post-quantum cryptography. The system successfully completes key generation, encapsulation, and decapsulation operations in 0.86 milliseconds, 0.88 milliseconds, and 0.88 milliseconds respectively, all while operating at the FrodoKEM-640 security level. Critically, this hardware acceleration achieves an Area-Time Product (ATP) improvement ranging from 1.75 to 2.00 times better than currently available implementations, indicating a substantial gain in efficiency. This performance leap suggests that robust, high-speed post-quantum cryptographic systems are increasingly viable for real-world deployment, paving the way for secure communication in the face of emerging quantum computing threats.
The realization of FrodoKEM on an Artix-7 FPGA necessitates a specific allocation of field-programmable gate array resources; the design consumes 13,423 Look-Up Tables (LUTs) for its logic operations, 6,042 Flip-Flops (FFs) to store intermediate and final results, and 14 Block RAMs (BRAMs) for efficient data storage. This resource utilization profile demonstrates a tangible footprint for hardware acceleration of post-quantum algorithms, providing insight into the trade-offs between performance and hardware cost. Careful optimization of these resource allocations is crucial for deployment in resource-constrained environments, and these figures serve as a benchmark for future implementations aiming to improve efficiency and reduce the overall hardware overhead of post-quantum cryptographic systems.
The trajectory of cryptographic security is shifting, and FrodoKEM stands to be a foundational element in the protocols safeguarding future digital communications. With ongoing standardization processes, notably through initiatives like ISO/IEC 18033-2, this lattice-based key encapsulation mechanism is gaining recognition as a viable solution against emerging quantum computing threats. As classical encryption methods become increasingly vulnerable, FrodoKEM’s resilience – stemming from the mathematical hardness of solving lattice problems – positions it for widespread adoption. This standardization will facilitate interoperability and trust, enabling seamless integration into diverse applications ranging from secure data transmission and digital signatures to protecting critical infrastructure, ultimately ensuring continued confidentiality and integrity in a post-quantum world.
The presented work embodies a systemic approach to cryptographic implementation, mirroring the interconnectedness of urban infrastructure. Just as a city’s functionality relies on efficient resource allocation and adaptable systems, this FPGA implementation of FrodoKEM prioritizes parallelization and memory optimization to achieve high performance. This aligns with Marvin Minsky’s observation: “You can’t always get what you want; but if you try sometimes, you find, you get what you need.” The need here is a robust, efficient post-quantum crypto-processor, and the design strategically addresses this by evolving the processing structure-a reconfigurable multiplier array-rather than attempting a complete overhaul, ensuring the system’s longevity and adaptability. The emphasis on structural evolution within the hardware is key to achieving both performance gains and future-proofing against evolving cryptographic threats.
Beyond the Horizon
The presented work, while demonstrating substantial gains in performance for a specific instantiation of FrodoKEM on FPGA hardware, merely illuminates the constraints inherent in translating theoretical elegance into practical reality. Each optimization-the parallel multipliers, the memory management-represents a local victory, yet simultaneously introduces new dependencies. Every new dependency is the hidden cost of freedom. The structure, so carefully crafted for this particular algorithm and platform, dictates the limits of future adaptation. A truly flexible, post-quantum cryptographic solution necessitates a move beyond algorithm-specific acceleration.
The immediate challenge lies not simply in faster multiplication, but in a more holistic understanding of the interplay between algorithm, architecture, and memory. The current paradigm favors incremental improvements to existing lattice-based constructions. However, a genuinely disruptive approach might involve exploring radically different cryptographic primitives – those less reliant on complex arithmetic, or designed with inherent parallelism at their core.
The path forward isn’t simply about building faster engines for existing codes. It’s about re-examining the fundamental principles of cryptographic design, accepting that simplicity, not complexity, is the ultimate arbiter of long-term security and efficiency. The pursuit of post-quantum cryptography is, ultimately, an exercise in applied structuralism; a reminder that form, relentlessly, dictates function.
Original article: https://arxiv.org/pdf/2601.16500.pdf
Contact the author: https://www.linkedin.com/in/avetisyan/
See also:
- How to Unlock the Mines in Cookie Run: Kingdom
- Top 8 UFC 5 Perks Every Fighter Should Use
- Jujutsu Kaisen: Divine General Mahoraga Vs Dabura, Explained
- The Winter Floating Festival Event Puzzles In DDV
- MIO: Memories In Orbit Interactive Map
- Xbox Game Pass Officially Adds Its 6th and 7th Titles of January 2026
- Where to Find Prescription in Where Winds Meet (Raw Leaf Porridge Quest)
- Jujutsu: Zero Codes (December 2025)
- Upload Labs: Beginner Tips & Tricks
- Frieren Has Officially Been Dethroned By A New 2026 Anime Release
2026-01-26 07:55