Author: Denis Avetisyan
New research details a dynamic security framework that uses machine learning to analyze system behavior and prevent malicious encryption attempts.
This review presents a dual-layer access control system leveraging kernel tracing, SELinux, and machine learning to mitigate ransomware threats based on real-time risk assessment.
Traditional security approaches struggle to differentiate between legitimate and malicious encryption activity, creating a critical vulnerability to ransomware attacks. This research details the development and evaluation of ‘Building a Robust Risk-Based Access Control System to Combat Ransomware’s Capability to Encrypt: A Machine Learning Approach’, a novel system employing fine-grained kernel tracing, machine learning inference, and SELinux policies to dynamically regulate encryption permissions. By analyzing function-level execution traces, the framework achieves both high detection accuracy and rule-like responsiveness, enabling risk-proportionate control without disrupting normal cryptographic workflows. Can this dual-layer approach provide a practical path toward enforceable, explainable, and adaptive encryption control for production Linux systems facing increasingly sophisticated ransomware threats?
The Inevitable Arms Race: Encryption and Evasion
The escalating prevalence of ransomware attacks now centers heavily on data encryption, a tactic that effectively holds digital assets hostage until a ransom is paid. This shift necessitates a fundamental rethinking of detection strategies; traditional methods reliant on identifying known malicious signatures are proving inadequate against the constant stream of novel encryption algorithms and polymorphic ransomware variants. Attackers are increasingly adept at blending malicious encryption routines with legitimate system processes, making signature-based detection increasingly unreliable. Consequently, a robust defense demands proactive measures capable of identifying malicious activity before encryption occurs, focusing on the behaviors indicative of ransomware – such as rapid, widespread file modification and the use of cryptographic libraries – rather than simply recognizing known threats.
The escalating sophistication of ransomware presents a significant challenge to conventional cybersecurity defenses, particularly those reliant on signature-based detection. These methods, which identify threats by matching known malicious code patterns, are increasingly ineffective against modern ransomware strains employing polymorphic and metamorphic encryption techniques. Attackers routinely modify the encryption algorithms and code structures, generating countless variations that evade established signature databases. This constant evolution renders previously identified signatures obsolete almost immediately, creating a perpetual cycle of detection and evasion. Consequently, relying solely on signature-based approaches leaves systems vulnerable to new and rapidly changing ransomware threats, necessitating a proactive shift toward more dynamic and adaptive security measures.
To effectively counter the escalating threat of ransomware that leverages encryption, security measures are increasingly focused on observing system behavior rather than simply identifying known malicious signatures. This paradigm shift centers on analyzing kernel activity – the core of the operating system – for anomalous patterns. Rather than searching for a specific virus definition, these advanced detection methods establish a baseline of normal kernel operations and flag any deviations, such as unusual file encryption rates or unauthorized access attempts to system resources. By monitoring how processes interact with the kernel, rather than what those processes are, security systems can identify and neutralize ransomware even when faced with novel or polymorphic encryption techniques, offering a proactive defense against rapidly evolving threats and minimizing the potential for data loss.
Peering into the Machine: Kernel-Level Visibility
Kernel tracing, primarily enabled by the `ftrace` framework in Linux, functions by instrumenting the kernel to record events occurring during system execution. These events can include function calls, return values, interrupt entries, and scheduler activity. `ftrace` utilizes a ring buffer to store this event data with minimal performance overhead, allowing for both real-time analysis and post-mortem debugging. The framework supports various tracing methods, including function tracing, branch tracing, and instruction tracing, providing granular control over the collected data. This capability allows developers and system administrators to observe the precise sequence of operations within the kernel, facilitating performance analysis, bug identification, and security auditing. The collected trace data represents a detailed log of kernel activity, offering insights into system behavior that are otherwise difficult to obtain.
The FunctionGraphTracer is a kernel tracing tool designed to record the call stack and relationships between functions during system execution. This tracer doesn’t simply log function entries and exits; it builds a graph representing the complete call path, detailing which functions invoked others and the sequence of those calls. The resulting call graph data is particularly valuable for anomaly detection because deviations from expected call patterns – such as unexpected function calls, unusual call sequences, or excessive recursion – can indicate errors, security breaches, or performance bottlenecks. Analysis of these graphs allows for the identification of root causes by tracing the execution path leading to the anomalous behavior, offering a granular view beyond simple error messages or system logs.
Kernel tracing, while providing comprehensive system-level data, generates raw output streams that are not directly interpretable for analysis. This data typically consists of timestamped events detailing function entries, exits, and various kernel state changes. Effective utilization necessitates substantial feature engineering, involving aggregation, filtering, and transformation of these events into meaningful metrics. Common techniques include calculating event frequencies, tracing execution paths, identifying latency bottlenecks, and constructing call graphs. Without this preprocessing, the volume and complexity of raw trace data render it impractical for identifying performance issues, security vulnerabilities, or anomalous system behavior. Feature engineering is therefore a critical step in converting raw kernel trace data into actionable intelligence.
Extracting Signal from the Noise: Feature Engineering
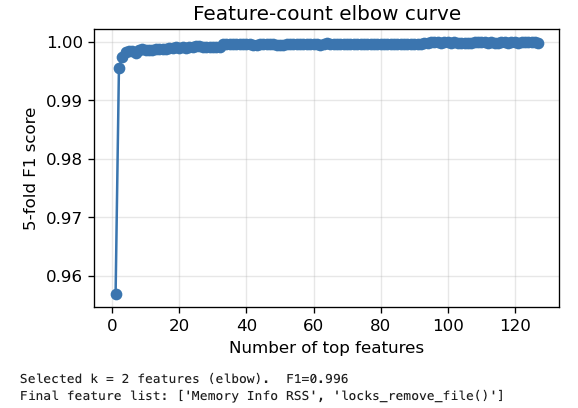
FeatureExtraction utilizes two primary data sources to represent system behavior: ResourceCounters and GraphMetrics. ResourceCounters provide quantitative measurements of system resource usage, including CPU time, memory allocation, and network I/O. Simultaneously, GraphMetrics capture the structure and characteristics of the system’s call graph, representing relationships between functions and processes. These metrics include node degree, path length, and centrality measures, providing insights into the control flow and interactions within the system. The combined data from these sources creates a comprehensive feature vector for representing system state and call graph structure, facilitating both rule-based and machine learning-based detection techniques.
Extracted features, encompassing both resource counter data and graph metrics, are utilized as input variables for diverse detection methodologies. Specifically, these features fuel both rule-based systems, where predefined thresholds and patterns trigger alerts, and machine learning models, including supervised algorithms trained to classify malicious or anomalous behavior. The feature set is standardized and normalized prior to input, ensuring compatibility across different model types and preventing bias due to varying scales. This dual-pronged approach allows for both immediate detection of known threats via rules and adaptive identification of novel attacks through machine learning inference.
Combining resource usage data with analysis of the system call graph yields a statistically significant improvement in detection accuracy. Evaluations demonstrate a Macro-F1 score of 0.97 when utilizing this combined feature set. This metric indicates a high degree of balance between precision and recall across all classes, suggesting the approach minimizes both false positives and false negatives in identifying anomalous system behavior. The Macro-F1 score is calculated by averaging the F1-scores for each individual class, providing an overall performance assessment.
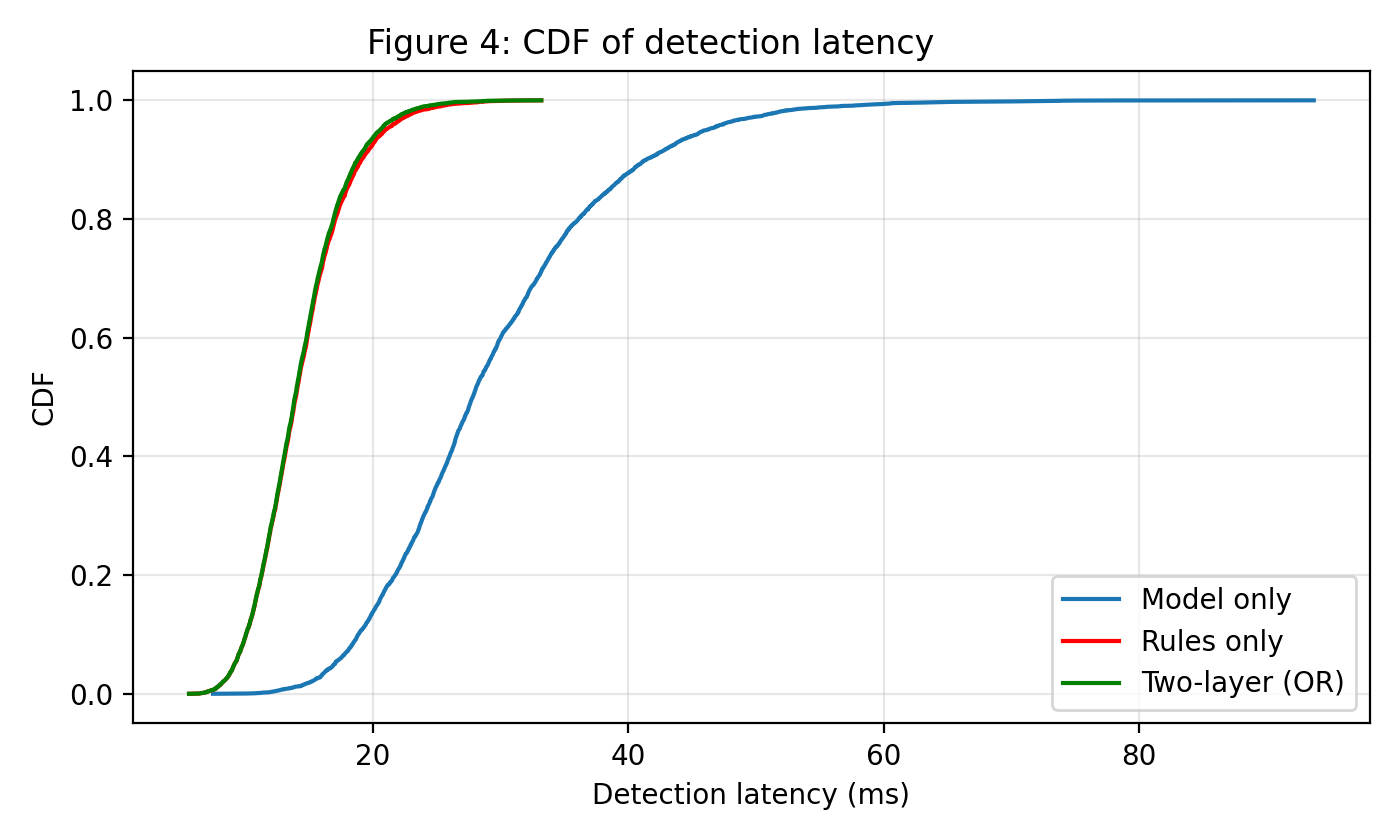
Layered Defenses: Speed and Adaptability
RuleBasedDetection utilizes pre-defined rules, implemented through models such as DecisionTree, to rapidly assess and filter network traffic or system events. This approach prioritizes speed by matching known malicious patterns or signatures, enabling immediate blocking of common threats without requiring complex analysis. While potentially generating false positives due to its reliance on static criteria, RuleBasedDetection serves as an efficient first line of defense, reducing the load on more computationally intensive detection layers and minimizing initial response times.
MachineLearningDetection employs algorithms, notably XGBoost, to provide a secondary layer of analysis beyond initial rule-based systems. Unlike static signature matching, XGBoost utilizes gradient boosting to learn complex patterns from data, enabling it to identify malicious activity based on numerous correlated features and adapt to evolving threats. This approach allows for the detection of zero-day exploits and polymorphic malware that bypass traditional signature-based detection methods, improving overall detection rates and reducing false positives through its ability to generalize from training data.
The DualLayerDetection system is engineered for high-throughput performance, achieving a decision latency of 22 milliseconds. Within this timeframe, the system successfully blocks 90% of malicious attempts, representing a rapid initial response to threats. The overall utility score for this system is 1950, a composite metric reflecting both detection rates and performance characteristics, and indicating a strong balance between speed and accuracy in identifying and mitigating malicious activity.
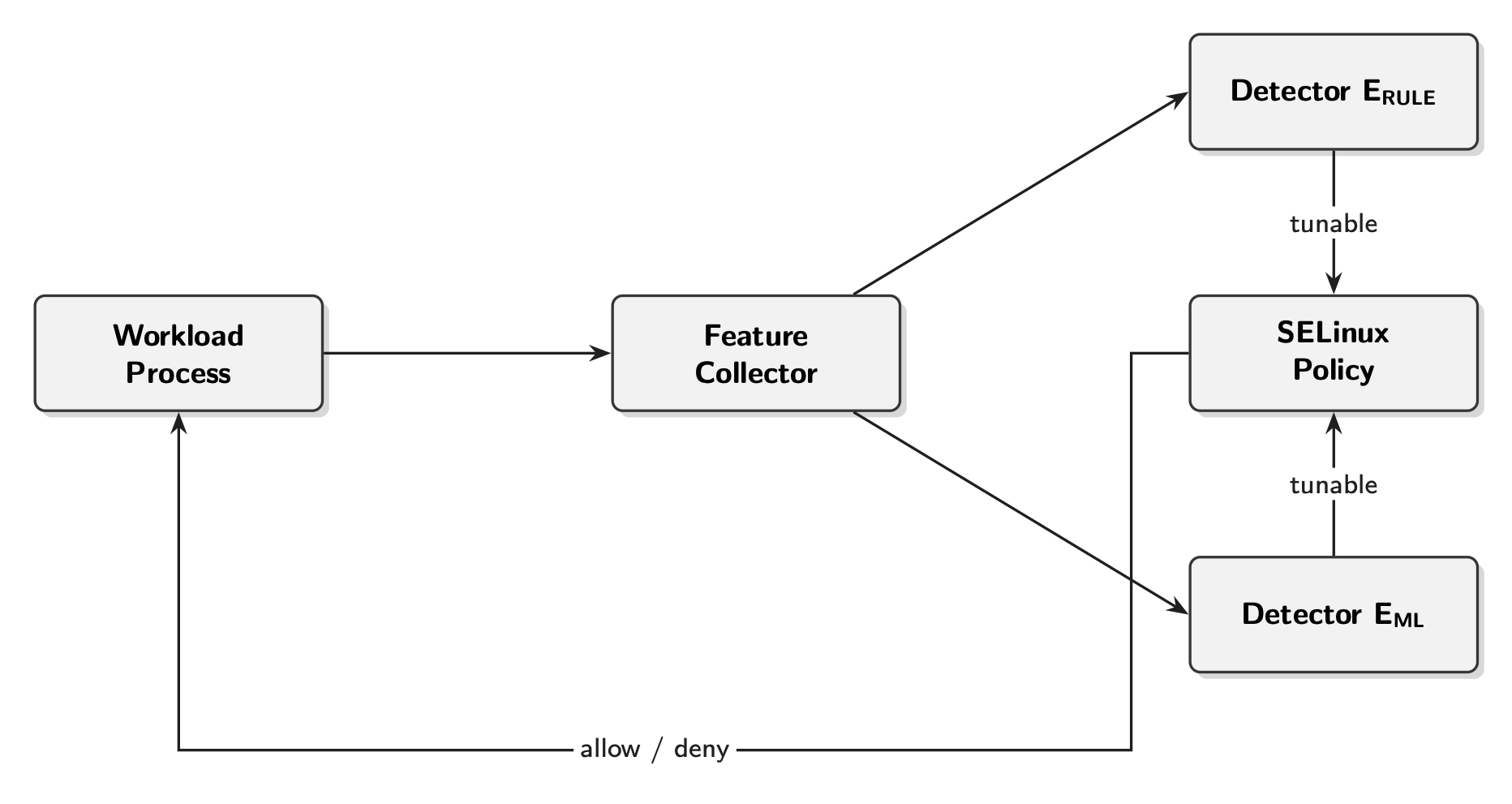
From Detection to Action: Policy and Enforcement
The value of sophisticated threat detection systems is fundamentally limited without effective policy enforcement mechanisms. Simply identifying malicious activity is insufficient; security truly strengthens when detections automatically trigger pre-defined actions, such as isolating compromised processes or blocking network communication. This translation of insight into action requires a robust and adaptable policy engine capable of responding to a diverse range of threats in real-time. Without such enforcement, security teams are left to manually intervene, creating bottlenecks and increasing the window of opportunity for attackers. A truly resilient system proactively responds to threats, minimizing damage and maintaining operational integrity – a feat achievable only through seamless integration of detection and automated policy enforcement.
Security-Enhanced Linux, or SELinux, establishes a highly granular and enforceable system of access control, moving beyond the traditional discretionary access control models. It operates by defining security contexts for all system resources – processes, files, network ports – and then defining policies that dictate interactions between these contexts. This mandatory access control prevents processes from accessing resources they are not explicitly authorized to use, even if a user account possesses the necessary permissions. Consequently, SELinux significantly limits the damage caused by compromised applications or malicious code, effectively containing breaches within defined boundaries and bolstering overall system resilience. The framework’s robust nature provides a powerful defense against a wide range of attacks, including privilege escalation and unauthorized data access, by enforcing strict isolation and minimizing the attack surface.
The developed prototype currently exhibits a memory footprint ranging from 31 to 35 GiB, a figure that, while demonstrating the feasibility of a comprehensive security solution, necessitates further refinement for widespread implementation. This substantial memory residency reflects the detailed, granular access controls and system isolation features currently integrated into the system. Researchers acknowledge that optimizing memory usage is critical for enabling deployment across a broader range of hardware configurations and scaling to larger, more complex environments. Ongoing development efforts are therefore focused on streamlining the prototype’s architecture and employing more efficient data structures without compromising its robust security capabilities, aiming to strike a balance between comprehensive protection and practical resource demands.
The pursuit of dynamic access control, as detailed in this research, feels…familiar. It’s all very elegant – kernel tracing, machine learning predicting ransomware behavior, SELinux enforcing policy. They’ll call it AI and raise funding, naturally. But one can’t help but recall Robert Tarjan’s observation: “Sometimes it’s better to be simple.” This framework, with its layers of complexity, is attempting to solve a problem that, at its core, started as a simple permissions issue. It’s a constant cycle: build something clever, production finds a way to break it, add more cleverness. The function graph analysis is neat, admittedly, but it’s just another layer of abstraction atop the fundamental question of who can encrypt what. The documentation lied again, probably.
The Road Ahead
This work, like so many attempts to ‘solve’ security, buys time. The proposed dual-layer system – kernel tracing feeding machine learning, ultimately modulating SELinux permissions – addresses a specific, current vector. However, ransomware, as a business model, will not remain static. Future iterations will inevitably prioritize evasion – techniques to mask malicious behavior from tracing, to poison the machine learning models, or to simply operate within the permitted parameters. The system’s efficacy hinges on maintaining a behavioral profile accurate enough to differentiate legitimate encryption from malicious encryption, a task guaranteed to degrade as the attack surface expands.
The reliance on behavioral analysis introduces a familiar tension: false positives. A system that aggressively blocks any unusual encryption activity will quickly become unusable. The inevitable accommodation of legitimate, if uncommon, behavior creates loopholes. Furthermore, the cost of maintaining and updating these behavioral models – the ongoing feature engineering, the retraining, the validation – will likely eclipse the initial development expense. It’s an expensive way to complicate everything, and if the code looks perfect, no one has deployed it yet.
The true next step isn’t necessarily more sophisticated machine learning, but a fundamental reconsideration of privilege. Can access control move beyond simply reacting to behavior, and instead enforce a principle of least privilege so strict that ransomware has nowhere to operate, even if undetected? That, of course, is a problem that has plagued security since its inception. The proposed system is a refinement, not a revolution.
Original article: https://arxiv.org/pdf/2601.16795.pdf
Contact the author: https://www.linkedin.com/in/avetisyan/
See also:
- How to Unlock the Mines in Cookie Run: Kingdom
- Top 8 UFC 5 Perks Every Fighter Should Use
- Jujutsu Kaisen: Divine General Mahoraga Vs Dabura, Explained
- The Winter Floating Festival Event Puzzles In DDV
- MIO: Memories In Orbit Interactive Map
- Deltarune Chapter 1 100% Walkthrough: Complete Guide to Secrets and Bosses
- Where to Find Prescription in Where Winds Meet (Raw Leaf Porridge Quest)
- Xbox Game Pass Officially Adds Its 6th and 7th Titles of January 2026
- USD RUB PREDICTION
- Quarry Rescue Quest Guide In Arknights Endfield
2026-01-26 13:20