Author: Denis Avetisyan
A new approach to fuzzing Ethereum clients uncovers hidden inconsistencies in RPC responses by intelligently simulating realistic blockchain conditions.
This paper introduces EthCRAFT, a context-aware fuzzing tool for detecting RPC bugs in Ethereum clients through diverse blockchain context generation and response analysis.
Despite the critical role of blockchain clients in maintaining network integrity, inconsistencies in Remote Procedure Call (RPC) responses pose a significant reliability challenge. This paper, ‘Is My RPC Response Reliable? Detecting RPC Bugs in Ethereum Blockchain Client under Context’, introduces EthCRAFT, a novel context-aware fuzzing tool designed to proactively identify RPC bugs in Ethereum clients. By systematically generating diverse blockchain contexts and analyzing discrepancies across multiple client implementations, EthCRAFT surpasses existing detection methods and has already uncovered six previously unknown vulnerabilities, three of which earned vulnerability bounties from the Ethereum Foundation. Will this approach pave the way for more robust and trustworthy blockchain infrastructure?
The Inevitable Decay of Foundations: Ethereum’s Client Implementations
The functionality of Ethereum, as a leading platform for decentralized applications and smart contracts, is fundamentally dependent on the performance of its client implementations, most notably Geth and Hyperledger Besu. These software programs act as the gateway to the blockchain, responsible for maintaining a complete and consistent record of the blockchain’s state and executing the complex computations defined within smart contracts. Without robust and reliable clients, the entire network’s operation is compromised; vulnerabilities or inefficiencies within these implementations can lead to network instability, data corruption, or even the potential for malicious actors to exploit weaknesses and compromise the integrity of the blockchain. Consequently, continuous development, rigorous testing, and ongoing security audits of these client implementations are paramount to ensuring the long-term viability and trustworthiness of the Ethereum ecosystem.
Ethereum clients, such as Geth and Hyperledger Besu, are fundamentally complex pieces of software tasked with the critical operations of maintaining the blockchain’s state and executing transactions. This intricacy, stemming from the demands of a decentralized, secure, and constantly evolving system, inevitably introduces potential vulnerabilities. These aren’t simply coding errors; they represent avenues for exploitation that could compromise the integrity of the entire network. The sheer volume of code – often exceeding millions of lines – coupled with the constant need for updates to address security concerns and improve performance, creates a challenging landscape for developers. Thorough auditing, formal verification techniques, and continuous testing are therefore paramount, but even these measures cannot guarantee the complete absence of flaws in such a sophisticated system. Consequently, the resilience of Ethereum hinges not only on the blockchain’s inherent cryptographic security, but also on the meticulous development and ongoing maintenance of these foundational client implementations.
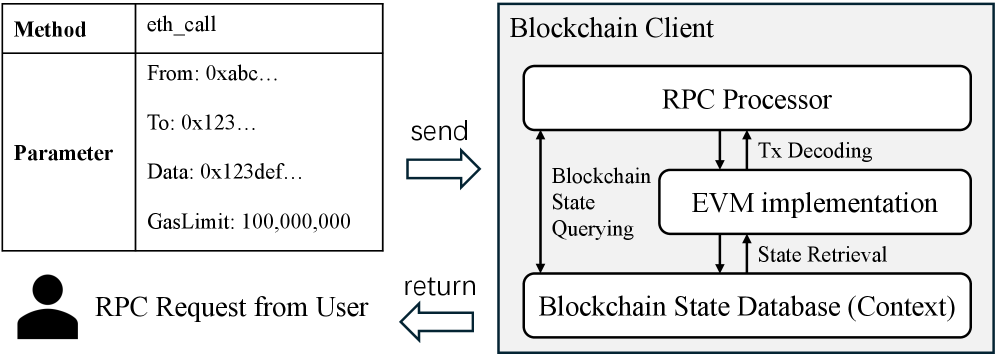
The Ethereum Virtual Machine (EVM) functions as the computational engine at the heart of the Ethereum blockchain, responsible for executing the code within smart contracts; however, the complex implementations of EVM clients – such as Geth and Hyperledger Besu – introduce potential vulnerabilities that can propagate with significant impact. Even seemingly minor coding errors within these clients can lead to unexpected behavior during contract execution, potentially allowing malicious actors to exploit flaws and manipulate the blockchain state. Because the EVM operates as a deterministic system, a bug in a client doesn’t necessarily halt the network, but rather introduces a divergence where different clients might interpret the same contract code differently, leading to inconsistencies and jeopardizing the fundamental trust upon which Ethereum relies. The consequences can range from denial-of-service attacks to the outright theft of funds, highlighting the critical need for rigorous testing and formal verification of these client implementations.
Beyond Static Tests: Uncovering Context-Dependent Flaws
Conventional Ethereum client testing, such as unit and integration tests, frequently proves insufficient for identifying context-dependent bugs. These bugs do not manifest under standard, isolated test conditions; instead, they are triggered by specific, often complex, combinations of blockchain state – encompassing account balances, smart contract storage, and block timestamps – and the precise sequence of transactions executed against that state. The inherent statefulness of the Ethereum Virtual Machine (EVM) and the interactions between smart contracts create a vast solution space that is difficult to comprehensively explore with traditional, static test cases. Consequently, bugs that only appear after a specific chain of events, or under uncommon state conditions, can bypass standard testing procedures and surface in production environments.
Remote Procedure Calls (RPC) constitute the primary means by which external applications – including wallets, decentralized applications, and blockchain explorers – interact with Ethereum clients. These methods allow for requests regarding blockchain state, transaction submission, and event filtering. However, the complexity inherent in handling numerous RPC methods, each with specific input parameters and expected behaviors, introduces significant potential for bugs. These bugs often manifest not as crashes, but as incorrect state transitions or unexpected responses, and are difficult to detect through standard unit or integration tests because they require specific, often complex, sequences of transactions and blockchain conditions to trigger. Consequently, vulnerabilities within RPC handling represent a substantial class of context-dependent bugs in Ethereum client software.
To effectively detect context-dependent bugs in Ethereum clients, testing methodologies must move beyond simple unit tests and incorporate techniques like transaction simulation and off-chain evaluation. Transaction simulation involves executing transactions against a locally-maintained state, allowing for observation of client behavior under controlled conditions and exploration of various edge cases. Off-chain evaluation, conversely, focuses on verifying the logic of smart contracts and client responses without deploying them to a live blockchain, enabling exhaustive testing of execution paths. These approaches are critical because they facilitate the exploration of a wide range of execution contexts – specific blockchain states and transaction sequences – that are often impossible to reliably reproduce on a public testnet or mainnet, thereby increasing bug detection rates.
EthCRAFT: Context-Aware Fuzzing for Ethereum Clients
EthCRAFT employs transaction mutation as a core technique for generating varied blockchain states during fuzzing. This process involves systematically altering valid transactions – modifying data fields such as recipient addresses, value transfers, or calldata – to create new transactions that, when executed, result in different global states. Unlike random transaction generation, EthCRAFT’s mutation strategies are informed by the Ethereum state and transaction format, ensuring the generated transactions remain syntactically and semantically valid, thereby increasing the likelihood of triggering edge cases and vulnerabilities within the Ethereum client’s execution logic. The system avoids invalid state transitions by adhering to Ethereum’s rules during mutation, focusing on generating diverse, yet valid, contexts for testing.
State-aware mutation strategies within EthCRAFT dynamically adjust transaction modifications based on the current runtime state of smart contracts. This approach differs from traditional fuzzing techniques that employ random or predefined mutations, which often generate invalid or irrelevant inputs. By tracking variables, balances, and storage values within the contract’s state, EthCRAFT can generate mutations that are more likely to trigger edge cases and expose vulnerabilities specific to the contract’s logic. This targeted approach significantly increases the effectiveness of bug discovery, as it focuses testing efforts on areas where state-dependent errors are most probable, leading to a higher rate of valid bug findings compared to state-agnostic fuzzing methods.
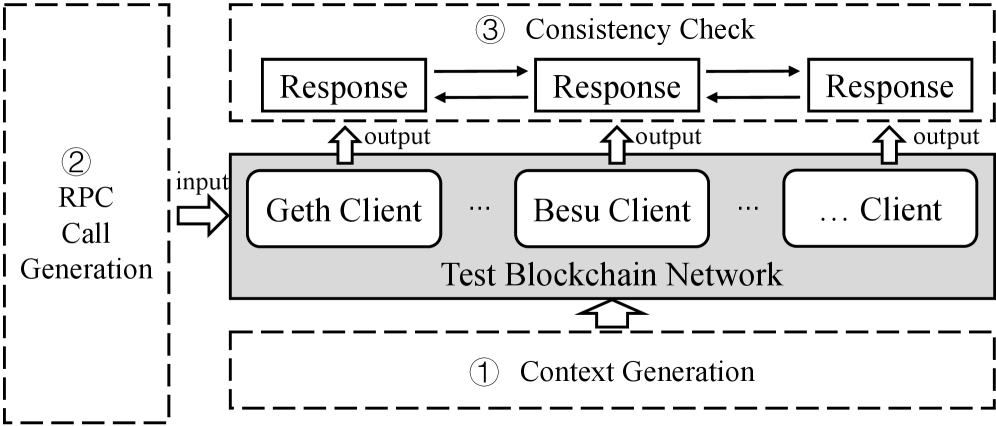
EthCRAFT employs a three-pronged approach to efficiently identify context-dependent Remote Procedure Call (RPC) bugs within Ethereum clients. First, transaction mutation generates a diverse set of blockchain states by intelligently modifying existing transactions. These mutated transactions are then subjected to off-chain evaluation, allowing for rapid assessment without the overhead of on-chain execution. Finally, code coverage analysis is performed during off-chain evaluation to determine which code paths are exercised by each mutated transaction, enabling targeted identification of bugs triggered by specific contextual conditions. This combination allows EthCRAFT to efficiently explore the state space and pinpoint vulnerabilities that would be difficult to discover through traditional fuzzing techniques.
EthCRAFT achieved a detection rate of 14 out of 30 known Remote Procedure Call (RPC) bugs present in Ethereum clients during evaluation. This performance represents a measurable improvement over baseline fuzzing techniques and previously published bug discovery methods. The identified bugs encompass a range of client vulnerabilities, and successful detection was verified through manual analysis and developer confirmation. The evaluation methodology involved systematically subjecting multiple Ethereum client implementations to a large volume of generated transactions and observing client behavior for anomalous conditions indicative of bugs.
During evaluation, EthCRAFT identified six previously unknown Remote Procedure Call (RPC) bugs within targeted Ethereum clients. These vulnerabilities were not present in existing bug databases and were subsequently confirmed as valid by the respective client developers. This demonstrates EthCRAFT’s capability to extend beyond known issue detection and proactively uncover novel vulnerabilities through context-aware fuzzing techniques. The identified bugs represent a significant contribution to Ethereum client security, addressing potential attack vectors that were previously unaddressed.
EthCRAFT builds upon existing Ethereum client analysis tools, notably EtherDiffer, by integrating transaction mutation and off-chain evaluation techniques. While EtherDiffer focuses on identifying differences in client execution traces based on existing transactions, EthCRAFT enhances this by dynamically generating new, context-aware transactions. This allows for broader state space exploration and the discovery of bugs that are triggered by specific transaction sequences or contract states, which may not be revealed through static analysis or replay of existing test cases. By combining these approaches, EthCRAFT provides a more comprehensive and effective methodology for identifying both known and previously unknown vulnerabilities within Ethereum clients.
The Inevitable Erosion and Paths Towards Resilience
The inherent flexibility of Remote Procedure Call (RPC) interfaces within blockchain networks, while enabling complex functionality, introduces vulnerabilities susceptible to context-dependent bugs. These bugs arise when the behavior of an RPC request is dictated by specific inputs or the current state of the blockchain, potentially leading to unpredictable outcomes. Malicious actors can exploit these inconsistencies to craft requests that overwhelm network resources, resulting in Denial of Service (DoS) attacks and disrupting transaction processing. Furthermore, these vulnerabilities aren’t limited to simple outages; they can be leveraged to manipulate smart contract execution, steal funds, or compromise the integrity of the entire blockchain. Consequently, ensuring the robustness of RPC handling is paramount to maintaining network stability and security, demanding meticulous code review and rigorous testing under varied conditions.
Context-dependent Remote Procedure Call (RPC) bugs frequently manifest due to intricate interactions with the gas limit, a crucial component governing computational cost on the Ethereum network. Transaction execution involves estimating gas consumption, and inaccuracies in this estimation, particularly when dealing with complex smart contract logic, can create vulnerabilities. These bugs arise when a transaction’s gas consumption unexpectedly deviates from the initial estimate, potentially leading to out-of-gas errors or, more critically, exploitable conditions where malicious actors can manipulate gas costs to disrupt network operations or even hijack contract functionality. Careful analysis of gas consumption patterns during transaction execution, including meticulous code review and rigorous testing with varying input parameters, is therefore essential for identifying and mitigating these vulnerabilities before they can be exploited.
Effective mitigation of blockchain vulnerabilities necessitates a concerted effort within the Ethereum community, moving beyond isolated fixes to systemic improvements. Security audits and vulnerability disclosures are crucial first steps, but lasting solutions often require formalizing changes through Ethereum Improvement Proposals, or EIPs. These proposals undergo rigorous peer review, ensuring that any modifications to the protocol – whether addressing RPC bugs or enhancing gas limit calculations – are thoroughly vetted and compatible with the broader ecosystem. Collaboration through EIPs fosters a transparent and inclusive approach to security, allowing developers, researchers, and stakeholders to collectively strengthen the resilience of the Ethereum network and establish robust, community-approved standards for future development.
Researchers are actively developing methods to automate the identification and remediation of vulnerabilities within blockchain systems, moving beyond manual patching. This involves integrating tools like EthCRAFT into continuous integration (CI) pipelines, enabling automated testing and bug fixing with each code change. The goal is to create a self-healing blockchain infrastructure where potential exploits are detected and resolved proactively, before they can be leveraged for malicious purposes. Such automation not only reduces response times to emerging threats but also lowers the barrier to entry for developers, encouraging greater participation in securing the network and fostering a more robust and resilient ecosystem. This shift towards automated security promises to significantly enhance the long-term stability and trustworthiness of blockchain technologies.
The pursuit of reliable systems, as demonstrated by EthCRAFT’s methodology for detecting RPC bugs, echoes a fundamental truth about software development. Brian Kernighan observes, “Debugging is twice as hard as writing the code in the first place. Therefore, if you write the code as cleverly as possible, you are, by definition, not smart enough to debug it.” This sentiment aligns perfectly with EthCRAFT’s approach; the tool doesn’t merely seek out errors, but actively crafts diverse, potentially problematic blockchain contexts to reveal latent inconsistencies. It acknowledges that even a seemingly functional system – an Ethereum client – carries within it the seeds of future failures. The very act of fuzzing, of systematically challenging the system, is a recognition that technical debt accumulates not just in code, but in assumptions about the operating environment – a debt that EthCRAFT aims to identify and address before it manifests as a critical failure.
What’s Next?
EthCRAFT, as presented, represents a commit in the ongoing annals of blockchain client verification. Each detected RPC bug is a symptom addressed, yet the underlying decay remains inevitable. The tool’s strength lies in context-aware fuzzing, but ‘context’ itself is a shifting landscape. Future iterations must grapple with the emergent properties of increasingly complex smart contract interactions-the subtle inconsistencies that manifest only after prolonged operation, or under conditions rarely mirrored in testing. Delaying these fixes is a tax on ambition, a compounding interest on potential vulnerabilities.
Current coverage metrics, while useful, are inherently incomplete. They measure what has been tested, not the infinite space of what could go wrong. The field needs to move beyond simply achieving higher code coverage, and towards more sophisticated methods for assessing the resilience of clients to unforeseen inputs and state transitions. Consider the value of formal verification, not as a replacement for fuzzing, but as a complementary method for identifying invariants and proving the absence of certain classes of bugs.
Ultimately, the quest for reliable blockchain clients is not about achieving perfection, but about managing entropy. Every version is a chapter, and each commit a record of temporary stasis. The real challenge lies in building systems that age gracefully, that can adapt to changing conditions and recover from inevitable failures-systems that acknowledge the relentless march of time, not as a metric to be optimized, but as the medium in which they exist.
Original article: https://arxiv.org/pdf/2601.21593.pdf
Contact the author: https://www.linkedin.com/in/avetisyan/
See also:
- How to Unlock the Mines in Cookie Run: Kingdom
- Gold Rate Forecast
- Top 8 UFC 5 Perks Every Fighter Should Use
- How To Upgrade Control Nexus & Unlock Growth Chamber In Arknights Endfield
- Most Underrated Loot Spots On Dam Battlegrounds In ARC Raiders
- MIO: Memories In Orbit Interactive Map
- Byler Confirmed? Mike and Will’s Relationship in Stranger Things Season 5
- How to Find & Evolve Cleffa in Pokemon Legends Z-A
- USD RUB PREDICTION
- All Pistols in Battlefield 6
2026-01-30 12:38