Author: Denis Avetisyan
Researchers have discovered a novel power side-channel attack that exploits operating system behavior to compromise the security of cryptographic keys.
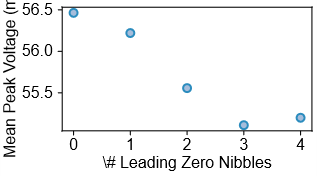
A cross-architecture vulnerability, dubbed SleepWalk, allows extraction of ECDSA nonces during OS context switches, potentially breaking cryptographic implementations.
While Elliptic Curve Digital Signature Algorithm (ECDSA) security relies on maintaining the secrecy of per-signature nonces, this work, ‘Sleep Reveals the Nonce: Breaking ECDSA using Sleep-Based Power Side-Channel Vulnerability’, introduces a novel cross-platform attack demonstrating that subtle power fluctuations during operating system context switches-induced by sleep functions-can leak sufficient information to recover these critical values. This “SleepWalk” vulnerability exploits power spikes correlated with nonce-dependent operations in scalar multiplication, even in implementations designed to be constant-time and masked, allowing for the extraction of 20 bits of the nonce across diverse cryptographic libraries and processor architectures. Does this previously unobserved leakage pathway necessitate a fundamental reconsideration of security assumptions within cryptographic systems and operating system design?
Unveiling the Processor’s Secrets: A New Vector for Attack
Modern processors, despite their computational prowess, are inherently vulnerable to power side-channel attacks due to the fundamental physics of transistor operation. These attacks don’t exploit logical flaws in the processor’s design, but rather monitor subtle variations in electrical power consumption. Each computational operation doesn’t require a uniform amount of energy; the specific data being processed directly influences power draw. For example, switching a transistor from off to on with a ‘1’ requires marginally more power than with a ‘0’. By precisely measuring these tiny fluctuations – often requiring sophisticated equipment and statistical analysis – an attacker can infer information about the data being processed, potentially revealing cryptographic keys, sensitive personal information, or other protected data. This leakage occurs because the processor’s power consumption is correlated with the Hamming weight – the number of ‘1’ bits – of the data it manipulates, creating a measurable signal that can be exploited.
The SleepWalk vulnerability represents a significant departure in side-channel attack methodologies by targeting processor behavior during context switches – the process of rapidly switching between different tasks. Unlike traditional attacks that monitor operations during active computation, SleepWalk exploits the brief period when a processor transitions into a low-power sleep state and subsequently resumes operation. This transition allows attackers to observe subtle power variations correlated with the data being processed during the switch, even if that data isn’t actively being used at the time of the leak. This innovative vector reveals sensitive information – cryptographic keys, user data, and other confidential material – by analyzing the energy spikes that occur when the processor restores the state of a different task, highlighting a previously overlooked vulnerability in modern processor design and demanding new security considerations.
The SleepWalk vulnerability hinges on a predictable relationship between a processor’s power consumption and the number of one bits-known as the Hamming weight-present in data being processed during a context switch. As the processor transitions between tasks, even during low-power sleep states, subtle power spikes occur while handling this data. Crucially, the magnitude of these spikes correlates directly with the Hamming weight; data with more one bits induces larger spikes. Attackers can monitor these power variations to deduce information about the data itself, effectively reconstructing sensitive values like cryptographic keys. This leakage occurs because the processor doesn’t fully isolate data during these transitions, creating a measurable side-channel that bypasses traditional security measures. The precision of this attack relies on accurately measuring and interpreting these minute power fluctuations, demonstrating a novel and potentially widespread threat to modern computing systems.
The escalating sophistication of side-channel attacks necessitates a thorough understanding of vulnerabilities like SleepWalk to effectively secure cryptographic implementations. This attack highlights how seemingly innocuous processor states – specifically, context switches during sleep modes – can become conduits for sensitive data leakage. By meticulously analyzing the correlation between power consumption and data characteristics during these transitions, attackers can reconstruct critical information, potentially compromising encryption keys or confidential data. Consequently, developers must move beyond traditional security measures and incorporate power-aware design principles, along with robust mitigation techniques targeting these context-switch vulnerabilities. Addressing SleepWalk isn’t merely patching a single flaw; it represents a crucial step towards building resilient cryptographic systems capable of withstanding increasingly subtle and inventive attacks in the ever-evolving landscape of computer security.
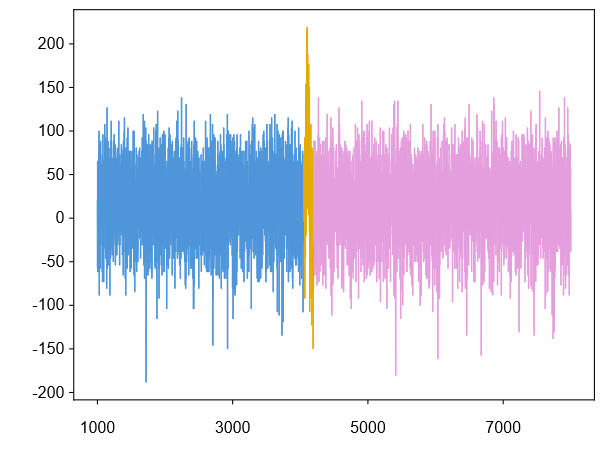
Decoding the Signal: ECDSA and the Spectre of Information Leakage
Elliptic Curve Digital Signature Algorithm (ECDSA) is a prevalent public-key cryptosystem utilized for digital signatures due to its efficiency and strong security when properly implemented. However, ECDSA implementations are susceptible to side-channel attacks, which exploit unintentional information leakage during cryptographic operations. Unlike attacks targeting the mathematical properties of the algorithm itself, side-channel attacks analyze physical characteristics such as timing variations, power consumption, electromagnetic radiation, or even sound emitted by the device performing the calculations. These characteristics are correlated with the secret key or intermediate values, allowing an attacker to deduce the key without directly breaking the cryptographic algorithm. The reliance on scalar multiplication within ECDSA, a computationally intensive process, amplifies the risk as variations in execution time or power usage can reveal information about the secret nonce or key.
ECDSA security fundamentally depends on scalar multiplication, an operation that repeatedly adds a point on an elliptic curve to itself a large number of times – the scalar. This computation is not simply a sequence of identical operations; the time and power consumption vary based on the individual bits of the scalar and the curve point being processed. Specifically, conditional branches within the scalar multiplication algorithm – for example, determining whether to add or double a point based on a bit value – introduce data-dependent variations in execution time. These variations, even if subtle, can be measured and exploited by attackers performing side-channel analysis, allowing them to infer information about the secret scalar without directly breaking the cryptographic algorithm itself. The computational intensity of scalar multiplication, combined with these data-dependent characteristics, creates a significant vulnerability in practical ECDSA implementations.
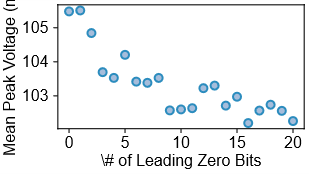
This research successfully implemented a nonce-extraction attack against Elliptic Curve Digital Signature Algorithm (ECDSA) by exploiting the SleepWalk vulnerability, a hardware flaw impacting modern CPUs. SleepWalk allows speculative execution to continue even after a branch misprediction, potentially leaking data through cache timings. The attack targeted the scalar multiplication operation within ECDSA, specifically focusing on the random nonce value. By analyzing these timing variations during the execution of ECDSA signatures, the research team was able to recover partial information about the nonce. This leakage, though subtle, proved sufficient to extract a statistically significant number of nonce bits, demonstrating a practical threat to ECDSA implementations even when utilizing cryptographic libraries.
Extraction of 20 bits of the ECDSA nonce across the RustCrypto, BearSSL, and GoCrypto cryptographic libraries demonstrates a practical vulnerability to side-channel attacks. This level of nonce leakage is sufficient to formulate a Hidden Number Problem (HNP) which, when solved, allows full recovery of the ECDSA private key. The HNP is constructed using the leaked nonce bits and the known signature and message data. The success of this attack across multiple, independently developed libraries highlights the systemic nature of the vulnerability and the difficulty of preventing such information leakage through standard coding practices alone.
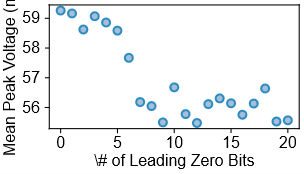
Forging Resilience: Constant-Time Cryptography as a Shield
Several cryptographic libraries, including RustCrypto, BearSSL, and GoCrypto, provide implementations of the Elliptic Curve Digital Signature Algorithm (ECDSA) designed for both performance and security. These libraries aim to offer optimized routines for cryptographic operations, focusing on speed without compromising the integrity of the encryption. Implementations often include techniques such as precomputation and assembly-level optimizations to accelerate calculations. Furthermore, these libraries are frequently updated to address newly discovered vulnerabilities and maintain compatibility with evolving cryptographic standards, making them suitable for use in a wide range of applications requiring secure communication and data protection.
Constant-time implementations of scalar multiplication are critical for mitigating side-channel attacks that exploit performance variations during cryptographic operations. Traditional scalar multiplication algorithms can exhibit data-dependent timing, where the execution time varies based on the values of the scalar and the point being multiplied. This variation can leak information about the secret key. Constant-time implementations ensure that all operations take the same amount of time regardless of the input data, thereby eliminating this timing leakage. This is achieved through careful algorithm selection and coding practices that avoid conditional branches and memory accesses dependent on secret data. Specifically, these implementations aim to ensure a consistent number of operations are performed for every possible input, effectively masking the secret key from observation via timing or power analysis.
Scalar multiplication, a core operation in Elliptic Curve Cryptography (ECDSA), is computationally intensive. To improve performance, implementations frequently utilize techniques such as fixed window methods and Booth recoding. Fixed window methods precompute multiples of the base point for a specific window size, reducing the number of point additions required. Booth recoding optimizes the representation of the scalar being multiplied, minimizing the number of additions and subtractions. Crucially, these optimizations are implemented to preserve constant-time properties; operations are structured to ensure execution time remains independent of the scalar’s value, preventing side-channel attacks that exploit data-dependent timing variations. These techniques represent a trade-off between performance gains and the complexity of ensuring constant-time execution.
Recent attacks have successfully exploited vulnerabilities in Elliptic Curve Digital Signature Algorithm (ECDSA) implementations on both ARM and RISC-V architectures. These exploits demonstrate that even when utilizing established cryptographic libraries like RustCrypto, BearSSL, and GoCrypto, constant-time execution is not consistently guaranteed. The successful targeting of two distinct processor architectures indicates this vulnerability is not limited to a specific instruction set or microarchitectural implementation, but rather represents a broader challenge in achieving truly constant-time cryptographic operations in practice. This highlights the need for rigorous testing and verification of constant-time properties across diverse hardware platforms.
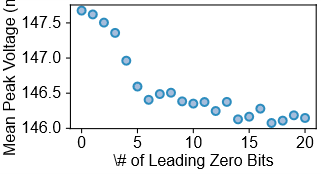
Architectural Fault Lines: The Processor as a Battleground
The foundation of secure cryptographic systems extends beyond algorithms and protocols to the very hardware on which they operate. Processor architecture profoundly influences the susceptibility of cryptographic implementations to attacks; subtle design choices dictate how data is processed and, consequently, how easily sensitive information can be leaked through side channels. Factors like instruction set architecture, memory organization, and cache behavior all contribute to the attack surface. For instance, certain architectures might inadvertently amplify timing variations, making timing attacks more feasible, or lack robust mechanisms for preventing power analysis. Consequently, developers must consider architectural vulnerabilities during the design and implementation of cryptographic software, adapting mitigation strategies to the specific characteristics of the underlying processor. This interconnectedness highlights the need for a holistic security approach that encompasses both software and hardware considerations.
Modern cryptographic libraries demonstrate remarkable architectural flexibility, enabling deployment across a diverse landscape of processor types. Projects like RustCrypto, BearSSL, and GoCrypto are deliberately designed with portability in mind, supporting established architectures such as ARM – prevalent in mobile devices and embedded systems – alongside the increasingly popular, open-standard RISC-V. This cross-platform compatibility isn’t merely a matter of convenience; it’s a crucial security consideration, allowing developers to leverage the same rigorously tested cryptographic code on a wider range of hardware. Furthermore, the ability to run these libraries on open architectures like RISC-V fosters a more transparent and auditable security ecosystem, as the underlying hardware can be thoroughly examined for potential vulnerabilities, backdoors, or weaknesses, enhancing trust in the overall cryptographic solution.
Processor architecture significantly influences the feasibility and efficacy of side-channel attack mitigation. Certain architectures may inherently offer features that simplify the implementation of countermeasures, such as fine-grained control over memory access or instruction timing. Conversely, designs lacking these features necessitate more complex and potentially less effective mitigation strategies. The very characteristics of an architecture-its instruction set, memory model, and cache organization-can create or exacerbate vulnerabilities exploitable through side channels. Consequently, a robust security posture isn’t solely determined by cryptographic algorithms but is deeply coupled with the underlying hardware, demanding careful architectural consideration during system design and implementation to protect against increasingly sophisticated attacks.
The move towards open-standard processor architectures, notably RISC-V, represents a significant shift in hardware security paradigms by fostering unprecedented transparency. Unlike traditionally closed, proprietary designs, RISC-V’s open instruction set architecture (ISA) allows for public verification of the hardware’s intended behavior. This accessibility enables independent security researchers and developers to thoroughly examine the design for vulnerabilities, backdoors, or weaknesses in its security features – a process severely limited with closed architectures. Greater scrutiny, facilitated by the ability to audit the hardware description, leads to quicker identification and remediation of potential flaws, ultimately enhancing the trustworthiness and resilience of cryptographic implementations relying on the processor. The collaborative nature of the RISC-V ecosystem further accelerates this process, allowing for community-driven security improvements and the development of specialized hardware mitigations against emerging threats.

The Path Forward: Building Truly Resilient Systems
The discovery of SleepWalk underscores a critical shift in cryptographic security: the necessity of acknowledging vulnerabilities inherent in the underlying hardware itself. Traditional cryptographic design often focuses on the strength of the algorithms, assuming a secure foundation at the hardware level; however, side-channel attacks like SleepWalk demonstrate that speculative execution and caching mechanisms can inadvertently leak sensitive information. This isn’t a flaw in the cryptography, but rather a consequence of how modern processors optimize performance. Consequently, future cryptographic systems must incorporate defenses against these hardware-based side-channels, potentially through architectural modifications, specialized instructions, or cryptographic algorithms designed to minimize exploitable data leakage. Ignoring these vulnerabilities leaves systems open to attacks that bypass even the most robust encryption, highlighting the need for a holistic approach to security that considers both software and hardware components.
A comprehensive understanding of how hardware vulnerabilities interact with cryptographic algorithms remains a critical area for investigation. Current cryptographic designs often assume a secure hardware foundation, yet flaws like those exposed by SleepWalk demonstrate this assumption can be dangerously flawed. Future research must move beyond algorithm-centric security to encompass a holistic view, examining how subtle hardware behaviors – timing variations, power consumption, electromagnetic emissions – can be exploited to break even mathematically sound encryption. This necessitates the development of new testing methodologies, capable of uncovering these hidden weaknesses, and the creation of cryptographic algorithms specifically designed to be resilient against hardware-based side-channel attacks. Such an integrated approach promises a more robust and dependable cryptographic landscape, capable of withstanding increasingly sophisticated threats.
The Hidden Number Problem (HNP) poses a significant threat to modern cryptography because it allows attackers to potentially recover secret keys from seemingly secure systems. This problem centers on distinguishing between a hidden number and random noise, a task surprisingly achievable with sufficient data obtained through side-channel analysis. Current cryptographic defenses often assume that the core mathematical problems are impenetrable, but fail to adequately address vulnerabilities arising from how these algorithms are implemented in hardware. Exploiting the HNP allows attackers to bypass these mathematical protections by directly observing the physical characteristics of the computation, such as power consumption or electromagnetic emissions. Consequently, developing robust defenses requires a shift in focus – not merely on improving algorithmic complexity, but on actively masking sensitive data and operations within the hardware itself, effectively raising the bar for side-channel attacks that attempt to solve the Hidden Number Problem and extract cryptographic keys.
A truly resilient cryptographic future demands a shift towards provably secure systems, moving beyond reliance on assumptions about attacker capabilities and computational hardness. This necessitates the development of cryptographic libraries built upon formal verification techniques, where mathematical proofs guarantee the correctness and security of the code itself. Simultaneously, hardware architectures must be designed with security as a foundational principle, incorporating formal methods to validate the absence of exploitable side-channels and vulnerabilities at the physical level. Such an approach-combining provably correct software with secure hardware-offers the strongest defense against both current and future threats, including those leveraging yet-undiscovered attack vectors and increasingly sophisticated adversaries. It’s a paradigm shift from reactive patching to proactive assurance, building trust not just in algorithms, but in the very foundations upon which they operate.
The research meticulously details how subtle system behaviors-specifically, power fluctuations during context switches-can reveal critical cryptographic data. This echoes a sentiment articulated by Donald Knuth: “Premature optimization is the root of all evil.” The team didn’t initially set out to break ECDSA via sleep states; rather, by deeply examining the underlying mechanisms-the ‘code’ of the operating system-they uncovered an unexpected vulnerability. It’s a testament to the idea that reality is open source, and careful reverse-engineering-even of seemingly unrelated system processes-can expose hidden flaws. The successful nonce extraction demonstrates that security isn’t solely about the strength of algorithms, but also about controlling the entire system environment.
Where Do We Go From Here?
The demonstration of SleepWalk isn’t merely about extracting a nonce; it’s a reminder that the fortress of cryptography isn’t built of algorithms alone. It’s built on the stubbornly analog world underneath-the fluctuations of voltage, the timing of context switches, the very act of doing. To believe a system is secure because the math checks out is to misunderstand how systems actually fail. The ease with which the nonce was recovered suggests a fundamental naivete in assuming the operating system would remain a silent, trustworthy partner in cryptographic operations.
Future work isn’t about patching ECDSA, but about re-evaluating the entire stack. Constant-time implementations, while laudable, address only a symptom. The real challenge lies in constructing systems where side-channels aren’t simply avoided-but are actively anticipated and neutralized at the hardware level. Perhaps the focus should shift from proving implementations correct to proving their unexploitability, a subtly but critically different goal.
One wonders, too, about the broader implications. If a seemingly innocuous system function like a context switch can become an attack vector, what other ‘background’ processes are silently leaking information? The search for cryptographic weaknesses often focuses on the obvious, the deliberately complex. The true vulnerabilities, it seems, are more likely to be found in the mundane, the overlooked, the things everyone assumes ‘just work’.
Original article: https://arxiv.org/pdf/2602.01491.pdf
Contact the author: https://www.linkedin.com/in/avetisyan/
See also:
- Gold Rate Forecast
- How to Unlock the Mines in Cookie Run: Kingdom
- How to Find & Evolve Cleffa in Pokemon Legends Z-A
- Most Underrated Loot Spots On Dam Battlegrounds In ARC Raiders
- Gears of War: E-Day Returning Weapon Wish List
- The Saddest Deaths In Demon Slayer
- FromSoftware’s Duskbloods: The Bloodborne Sequel We Never Knew We Needed
- All Pistols in Battlefield 6
- Jujutsu: Zero Codes (December 2025)
- Epic Pokemon Creations in Spore That Will Blow Your Mind!
2026-02-03 13:15