Author: Denis Avetisyan
This review explores how combining different encryption methods can dramatically improve data security and reduce communication delays in intelligent transportation systems.
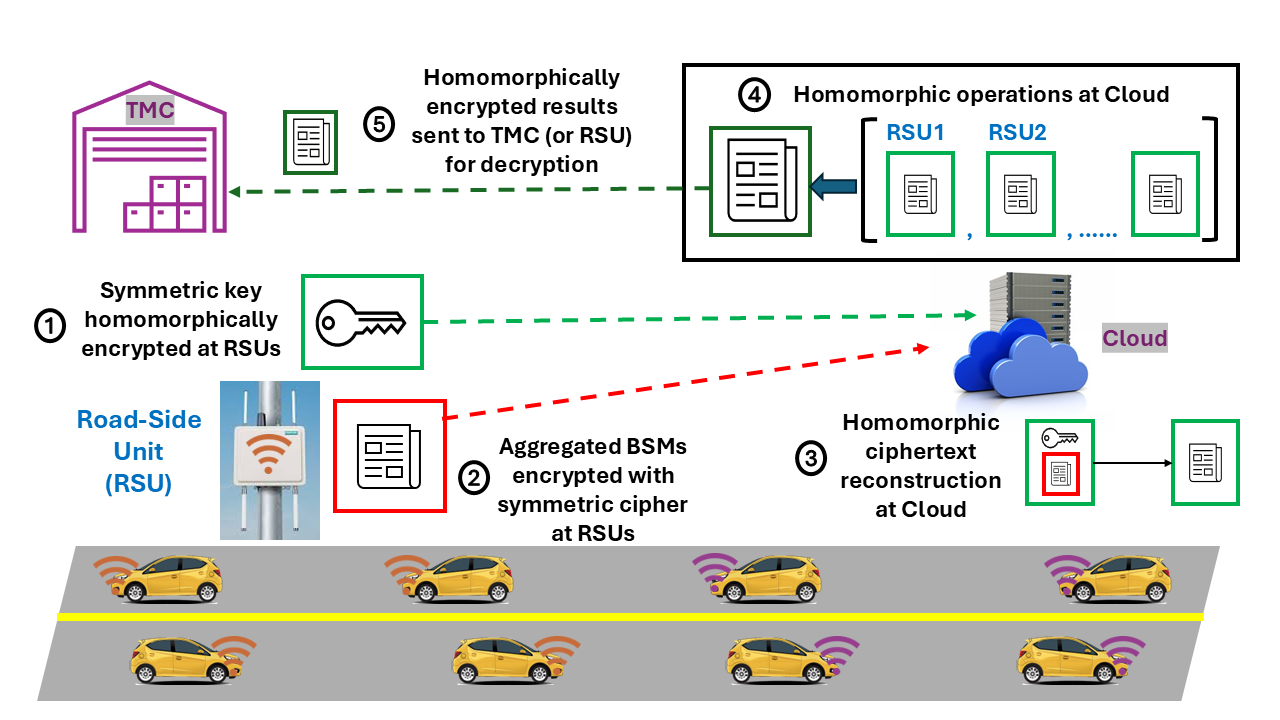
Hybrid Homomorphic Encryption offers a practical solution for privacy-preserving computation in Vehicle-to-Everything (V2X) communication and cloud-based ITS applications.
Protecting user privacy in increasingly data-driven Intelligent Transportation Systems (ITS) presents a fundamental challenge given the sensitivity of vehicular data and the need for real-time processing. This paper, ‘On the Feasibility of Hybrid Homomorphic Encryption for Intelligent Transportation Systems’, investigates the potential of hybrid homomorphic encryption (HHE) to reconcile privacy with practicality. Our analysis demonstrates that HHE can substantially reduce ciphertext expansion and communication overhead-orders of magnitude compared to conventional homomorphic encryption-while maintaining robust cryptographic security. Will this enhanced efficiency unlock the widespread adoption of privacy-preserving computation in latency-constrained vehicular applications and cloud-based ITS services?
The Inherent Vulnerability of Data in Use
Conventional cryptographic methods excel at safeguarding data when it’s stored – ‘at rest’ – or as it moves across networks – ‘in transit’. However, a significant vulnerability emerges the moment data is actively being processed. Modern applications routinely demand computations on the data itself, requiring decryption before analysis or manipulation. This decryption phase exposes sensitive information to potential compromise, as the data exists in an unencrypted state within the processor’s memory. Consider scenarios like fraud detection, personalized medicine, or financial modeling – each requires accessing and utilizing data while it’s being used, creating a critical window for attacks. This limitation has become increasingly problematic with the proliferation of cloud-based services and the growing need for real-time data analytics, demanding a new approach to secure computations.
The escalating reliance on cloud computing and data analytics is fundamentally reshaping data security requirements. Traditionally, data was most vulnerable while actively being processed – a gap that existing encryption methods failed to address. As organizations increasingly outsource computation and leverage data insights, the need to perform operations directly on encrypted data becomes paramount. This shift necessitates a new paradigm where sensitive information remains protected throughout its entire lifecycle – from storage and transmission to active analysis. Maintaining confidentiality during computation isn’t merely a feature, but a core requirement for enabling trustworthy and secure data-driven applications in the modern era, fostering innovation while upholding privacy standards.
Homomorphic Encryption (HE) represents a paradigm shift in data security, offering the unprecedented ability to perform computations on encrypted data without requiring decryption first. This innovation circumvents a fundamental limitation of traditional cryptographic methods, which only protect data when it is stored or moving between locations. With HE, sensitive information remains shielded throughout the entire processing lifecycle – from analysis and calculations to machine learning applications – effectively eliminating the risk of exposure during use. The implications are profound, particularly in scenarios involving cloud computing and collaborative data analysis, where entrusting data to third-party infrastructure introduces inherent vulnerabilities. By enabling secure computation directly on ciphertexts, HE unlocks the potential for truly private data processing, fostering trust and enabling innovation in a data-driven world.
Initial iterations of Homomorphic Encryption, while theoretically groundbreaking, suffered from substantial performance limitations that impeded widespread implementation. Early schemes required computational resources orders of magnitude greater than processing equivalent plaintext data, rendering them impractical for many real-world applications. These bottlenecks stemmed from the complex mathematical operations inherent in manipulating encrypted data – operations that involved large keys and intricate algorithms. Consequently, even relatively simple computations could take prohibitively long, effectively nullifying the security benefits if usability was severely compromised. Researchers recognized this critical hurdle and dedicated significant effort to optimizing HE schemes, focusing on reducing computational overhead and key sizes to bridge the gap between theoretical promise and practical feasibility.
Foundational Constructs for Secure Computation
Several foundational Homomorphic Encryption (HE) schemes were developed to enable computation on encrypted data. The BFV scheme, introduced by Breyer, Vaikuntanathan, and others, operates on integer polynomials and supports additively homomorphic operations, as well as limited multiplication. The BGV scheme, building upon BFV, improves upon its capabilities by allowing for leveled homomorphic evaluation of circuits of arbitrary depth, though it requires bootstrapping to overcome noise growth. CKKS, introduced by Cheon, Kim, and Song, extends HE to approximate computations on real numbers using fixed-point arithmetic, making it suitable for machine learning applications. Each scheme presents trade-offs; BFV and BGV prioritize exact computation but have limitations in multiplicative depth, while CKKS allows for more complex computations with a controlled error bound, at the cost of approximate results.
The security of leveled and fully homomorphic encryption schemes is predicated on the presumed hardness of specific mathematical problems, notably the Learning with Errors (LWE) problem and its ring-based variant, Ring-LWE. These problems involve distinguishing between random linear equations and those with added, carefully constructed noise. The noise is typically sampled from a Discrete Gaussian Distribution, a probability distribution over real numbers that is discrete due to its finite precision. The parameters defining both the LWE problem (dimension of the lattice, modulus size) and the Discrete Gaussian Distribution (standard deviation) are critical security parameters; larger parameters generally offer greater security but increase computational cost. The hardness of LWE stems from the fact that solving it would allow efficient solutions to well-studied lattice problems, for which no efficient classical algorithms are known.
Fully homomorphic encryption (FHE) schemes, despite their theoretical capability to perform arbitrary computations on encrypted data, are characterized by significant computational overhead compared to operations on plaintext. This overhead stems primarily from the complex mathematical operations required for both encryption and decryption, as well as the growth in ciphertext size during homomorphic operations. Specifically, each homomorphic operation-addition or multiplication-introduces noise into the ciphertext; managing this noise requires complex lattice-based techniques and results in a ciphertext that expands in size with each operation. The size of the parameters used within the scheme – specifically the dimension of the underlying lattice and the modulus used – directly impacts both security and performance, creating a trade-off. Consequently, practical deployments of FHE often require specialized hardware acceleration and careful parameter selection to mitigate these performance limitations.
Partially homomorphic encryption (PHE) schemes, exemplified by the Paillier Cryptosystem, provide computational efficiency gains over fully homomorphic encryption (FHE) by supporting only a limited set of operations on encrypted data. Specifically, the Paillier cryptosystem natively supports additive homomorphic properties, allowing for the evaluation of addition and multiplication by a constant on ciphertexts without decryption; however, operations like subtraction or multiplication of two ciphertexts are not directly possible. This restriction to a limited operation set reduces the computational complexity and overhead associated with encryption and decryption, making PHE suitable for applications where only those specific operations are required, such as privacy-preserving statistical analysis or threshold cryptography. While lacking the generality of FHE, PHE offers a pragmatic trade-off between functionality and performance.
Optimized Strategies for Practical Implementation
Hybrid Homomorphic Encryption (HE) strategies combine the strengths of fully homomorphic encryption (FHE) schemes with those of more efficient, yet limited, partially homomorphic schemes such as Paillier. FHE allows for arbitrary computation on encrypted data but suffers from significant computational overhead and large ciphertext sizes. By integrating a partially homomorphic scheme, certain operations can be performed directly on the ciphertext using the faster, less resource-intensive Paillier encryption, while more complex operations are handled by the FHE component. This division of labor reduces the overall computational burden and minimizes ciphertext expansion, leading to improved performance without compromising the ability to perform all necessary computations securely.
Real-to-Finite-field Transciphering is a technique employed in homomorphic encryption schemes like Rubato and HERA to optimize performance and ciphertext size. This approach involves mapping real numbers to finite field elements, allowing for homomorphic operations to be conducted on these finite representations. By carefully selecting parameters and utilizing this mapping, these schemes achieve a balance between maintaining small parameter sizes – crucial for efficient computation – and enabling rapid homomorphic evaluation. This contrasts with traditional HE schemes that often require significantly larger parameters to achieve comparable security levels, leading to substantial computational overhead and larger ciphertext expansion.
Recent advancements in Homomorphic Encryption (HE) schemes are demonstrably reducing computational overhead and improving practical applicability. Specifically, schemes like Rubato have achieved significant reductions in ciphertext size, ranging from 41 to 195 bytes. This represents a substantial improvement over traditional HE implementations, which often result in ciphertext expansions of 660 to 5250 bytes for comparable security levels. The smaller ciphertext size directly translates to reduced bandwidth requirements for data transmission, lower storage costs, and faster computation times, making HE more viable for resource-constrained environments and real-time applications.
Achieving a practical balance between security, computational efficiency, and functional capability is central to the advancement of homomorphic encryption (HE). Traditional HE schemes often suffer from substantial ciphertext expansion, hindering their usability in bandwidth-constrained or performance-critical applications. However, schemes like Rubato demonstrate significant improvements in this area; in Intelligent Transportation Systems (ITS) applications, Rubato achieves a ciphertext expansion of only 1.6-1.7, a considerable reduction compared to the 660-5250 observed in conventional HE implementations. This minimized expansion directly translates to lower storage requirements and faster data processing, making HE a more viable solution for real-world deployments.
The Transformative Potential for Connected Transportation
The increasing sophistication of Intelligent Transportation Systems (ITS) relies on the continuous collection and analysis of substantial quantities of data, creating inherent privacy vulnerabilities. These systems, designed to optimize traffic flow and enhance safety, gather information ranging from vehicle location and speed to driver behavior and personal preferences. This data, if compromised, could reveal sensitive details about individuals’ routines, habits, and even their identities. The sheer volume of data generated, coupled with the interconnectedness of vehicles, infrastructure, and data processing centers, expands the potential attack surface for malicious actors. Consequently, ensuring the confidentiality and integrity of this information is paramount, necessitating the development and implementation of robust privacy-preserving technologies to safeguard against unauthorized access and misuse.
Homomorphic encryption (HE) presents a compelling solution for safeguarding the continuous stream of data vital to intelligent transportation systems. This innovative approach allows for computations to be performed directly on encrypted data, meaning sensitive information – such as Basic Safety Messages detailing vehicle speed, position, and potential hazards – can be processed by infrastructure and other vehicles without ever being decrypted. This preserves data privacy while still enabling critical functions like collision avoidance and traffic flow optimization. Unlike traditional security measures that require decryption before processing, HE maintains confidentiality throughout the entire data lifecycle, effectively shielding crucial communications from potential eavesdropping or manipulation and bolstering the overall security posture of connected vehicle ecosystems.
The seamless operation of future transportation systems hinges on the reliable exchange of data between vehicles and infrastructure, necessitating sophisticated security credential management systems. These systems are not merely about preventing unauthorized access; they fundamentally guarantee the integrity of information – ensuring data hasn’t been tampered with during transmission. A compromised credential could allow malicious actors to inject false data, potentially causing accidents or disrupting traffic flow. Therefore, robust management protocols are critical for establishing trust, verifying the authenticity of each data source, and maintaining a secure communication network. Without this foundation of trust, the benefits of intelligent transportation systems – improved safety, efficiency, and sustainability – remain unrealized, as operators and passengers alike would lack confidence in the data guiding critical decisions.
Homomorphic encryption (HE) stands to revolutionize Intelligent Transportation Systems by enabling secure data exchange without compromising functionality, ultimately enhancing safety, efficiency, and sustainability. Traditional HE methods, however, often generate excessively large ciphertexts, creating transmission bottlenecks-previous schemes required fragmentation into 90 to 700+ packets to fit standard network constraints. The Rubato scheme addresses this limitation by drastically reducing ciphertext size, allowing fully encrypted data to be transmitted within a single Maximum Transmission Unit (MTU) packet. This efficiency is critical for real-time applications like cooperative collision avoidance and traffic flow optimization, as it minimizes latency and ensures timely delivery of crucial information between vehicles and infrastructure, paving the way for truly connected and automated transportation networks.
The pursuit of efficiency in data processing, as demonstrated by the exploration of Hybrid Homomorphic Encryption within Intelligent Transportation Systems, demands a similar rigor. This paper’s focus on minimizing ciphertext expansion and latency aligns perfectly with the need for provable solutions, not merely functional ones. As Linus Torvalds once stated, “Talk is cheap. Show me the code.” The research presented doesn’t simply propose a concept; it provides a detailed analysis of how HHE can be implemented to address real-world challenges in V2X communication, emphasizing a quantifiable improvement over existing HE schemes. This commitment to demonstrable results-to code that works and can be verified-is the hallmark of true innovation.
The Road Ahead
The demonstrated reduction in communication latency through Hybrid Homomorphic Encryption is, predictably, not an end in itself. The pursuit of efficiency should not overshadow the fundamental question of algorithmic cost. While ciphertext expansion remains a practical concern, a focus on minimizing computational complexity – measured not in clock cycles, but in asymptotic behavior with respect to data volume – must guide future work. The elegance of a solution lies not in its ability to merely function on a testbed, but in its provable scalability.
Current explorations into parameter selection for HHE schemes appear largely empirical. A rigorous mathematical framework for determining optimal configurations, balancing privacy guarantees with computational overhead, is conspicuously absent. Furthermore, the assumption of trusted setup, common in many HE implementations, feels increasingly precarious. Protocols resilient to untrusted setup, though undoubtedly more complex, represent the only path toward truly robust privacy-preserving computation.
The application to Intelligent Transportation Systems, while illustrative, serves as a reminder that data utility is paramount. The preservation of privacy must not come at the expense of meaningful information. The challenge, therefore, is to develop HHE schemes capable of supporting not just simple computations, but also the complex analytical tasks required for genuinely intelligent systems – a task that demands a re-evaluation of the very definition of ‘efficient’ computation.
Original article: https://arxiv.org/pdf/2602.02717.pdf
Contact the author: https://www.linkedin.com/in/avetisyan/
See also:
- Solo Leveling: Ranking the 6 Most Powerful Characters in the Jeju Island Arc
- How to Unlock the Mines in Cookie Run: Kingdom
- Gold Rate Forecast
- Gears of War: E-Day Returning Weapon Wish List
- Bitcoin’s Big Oopsie: Is It Time to Panic Sell? 🚨💸
- Most Underrated Loot Spots On Dam Battlegrounds In ARC Raiders
- Top 8 UFC 5 Perks Every Fighter Should Use
- The Saddest Deaths In Demon Slayer
- How to Find & Evolve Cleffa in Pokemon Legends Z-A
- Fantasy Life i: How to Get Elder Oak Logs
2026-02-05 00:27