Author: Denis Avetisyan
Researchers have developed Spinel, a novel signature scheme building on the widely-adopted SPHINCS+ framework, to enhance its theoretical underpinnings and resilience against future attacks.
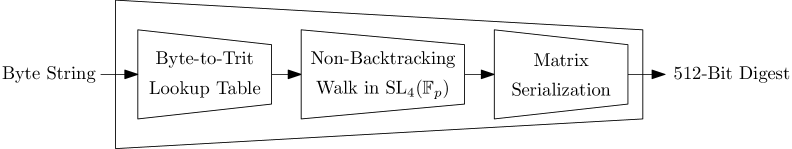
Spinel leverages an algebraic hash function based on SL4(Fp) to strengthen the security of hash-based digital signatures in a post-quantum world.
The looming threat of quantum computation necessitates cryptographic solutions beyond classically-hard problems. This paper introduces ‘Spinel: A Post-Quantum Signature Scheme Based on SLn(Fp) Hashing’, a novel digital signature scheme built upon the established security of SPHINCS+ but fortified with a new family of algebraic hash functions derived from SL_n(F_p) group actions. Spinel aims to enhance the theoretical underpinnings of hash-based cryptography by grounding its security in the presumed hardness of navigating expander graphs over this algebraic structure. Does this approach pave the way for a new generation of robust, algebraically-founded post-quantum cryptographic primitives?
The Inevitable Fracture: Preparing for a Post-Quantum Security Landscape
The bedrock of modern digital security, public-key cryptography – encompassing widely used algorithms like RSA and Elliptic Curve Cryptography (ECC) – faces an existential threat from the advent of quantum computing. These algorithms rely on the mathematical difficulty of factoring large numbers or solving the discrete logarithm problem, challenges easily overcome by sufficiently powerful quantum computers employing algorithms such as Shor’s algorithm. This isn’t a hypothetical concern; the potential for ‘cryptographic breakout’ – where previously secure data is suddenly exposed – looms as quantum computing technology matures. Consequently, sensitive information currently protected by these methods – encompassing financial transactions, government communications, and personal data – is increasingly vulnerable to decryption and manipulation, necessitating a proactive shift towards quantum-resistant cryptographic solutions to maintain confidentiality and integrity in the digital age.
The advent of quantum computing necessitates a proactive shift in cryptographic strategies, as existing public-key systems – the bedrock of modern digital security – face an existential threat. While currently theoretical for many applications, the potential of quantum computers to break widely used algorithms like RSA and ECC demands the immediate development and implementation of Post-Quantum Cryptography (PQC). This emerging field focuses on creating cryptographic systems that are resistant to attacks from both classical and quantum computers, ensuring the continued confidentiality and integrity of sensitive data. Safeguarding future communications, financial transactions, and critical infrastructure relies on transitioning to these new algorithms, a process requiring significant research, standardization, and ultimately, widespread adoption before sufficiently powerful quantum computers become a reality. The stakes are considerable; a failure to prepare for this quantum-driven security paradigm shift could have devastating consequences for global cybersecurity.
Conventional cryptographic systems often rely on maintaining persistent state – a continuous record of past interactions – to ensure security, a process that introduces complexities in distributed systems and hinders scalability. This approach clashes with the demands of modern applications, such as cloud computing and the Internet of Things, which require seamless operation across vast networks and a high degree of flexibility. Stateless cryptographic designs, where each transaction is independent and doesn’t rely on prior exchanges, offer a compelling solution, but achieving comparable security levels without state information presents significant challenges. Furthermore, the increasing volume of encrypted data and the need for real-time processing necessitate cryptographic algorithms that can be efficiently scaled to handle massive workloads, a feat that many traditional methods struggle to accomplish. Consequently, the development of cryptographic solutions optimized for statelessness and scalability is paramount to securing future digital infrastructure.
SPHINCS+: A Stateless Bastion Against the Quantum Tide
SPHINCS+ is a post-quantum digital signature scheme relying solely on cryptographic hash functions, eliminating the need for trapdoor assumptions like those used in RSA or ECC. This construction provides inherent resistance to attacks from both classical and quantum computers; Grover’s algorithm offers a quadratic speedup for exhaustive key search, while Shor’s algorithm breaks the mathematical foundations of widely used public-key cryptography, neither of which pose a threat to a hash-based signature scheme like SPHINCS+. Security is derived from the collision resistance of the underlying hash function; an attacker attempting to forge a signature must find a hash collision, which is computationally infeasible with strong hash functions like SHA-256 or SHAKE. The scheme’s parameters, specifically the hash function output size and tree height, directly influence the security level and signature size, allowing for configurable security margins.
The stateless nature of SPHINCS+ is enabled by a Hypertree structure, a multi-layered tree of hash functions that eliminates the need for a persistent state during signature generation or verification. This architecture contrasts with stateful signature schemes which require tracking of used keys or counters, introducing complexity and potential vulnerabilities. The Hypertree facilitates efficient key management by deriving all necessary signing keys from the initial public and private key pair, without requiring external storage or updates. Scalability is achieved through the hierarchical structure; increasing the height and width of the Hypertree allows for a greater number of signatures to be generated without compromising security or efficiency, as each layer represents an additional level of key derivation and authentication.
SPHINCS+ relies on the combination of several cryptographic primitives to construct a secure signature scheme. Specifically, it employs ‘WOTS+’ (Winternitz One-Time Signature+) for authenticating the leaf nodes within its Merkle tree-like structure; WOTS+ provides a method for generating one-time signatures from hash functions. Underlying this is ‘FORS’ (Forest of Random Subsets), a stateless hash-based signature scheme that serves as the foundational building block, enabling the creation of few-time signatures. FORS is utilized to generate a set of signatures from a single private key, increasing efficiency while maintaining security. The combination of FORS and WOTS+ within the SPHINCS+ architecture facilitates both efficient signature generation and verification, while simultaneously providing resistance against various attacks, including those leveraging quantum computers.
SL4(Fp) Hash: The Geometric Foundation of Resilience
The SL4(Fp) hash function, employed within the SPHINCS+ signature scheme, is a cryptographic hash algorithm constructed using the special linear group SL4 over a finite field, denoted as F_p. This group consists of 4×4 matrices with determinant 1 over the field F_p, where p is a prime number. The use of SL4(Fp) provides a mathematically defined structure for the hashing process, enabling operations based on matrix multiplication and inversion within the finite field. This approach differs from traditional hash functions like SHA-256, which rely on bitwise operations and compression functions, and is designed to offer resistance against known attacks and to provide a foundation for post-quantum cryptographic systems.
The SL4(Fp) hash function employs the Tillich-Zémor construction, a method for building cryptographic primitives from graphs. Specifically, it utilizes the Cayley graph of the special linear group SL4 over a finite field F_p. This construction achieves diffusion and confusion – core properties of cryptographic hash functions – by representing data as paths on the Cayley graph and applying linear transformations based on the graph’s structure. The Cayley graph’s connectivity ensures that small changes to the input propagate rapidly, contributing to diffusion, while the linear transformations introduce confusion by obscuring the relationship between input and output.
The integration of the SL4(Fp) Hash function into the SPHINCS+ signature scheme has yielded a demonstrably functional post-quantum cryptographic system. Performance evaluations indicate a computational cost ranging from 2.65 x 1012 to 2.93 x 1012 CPU cycles for signature generation. In contrast, signature verification is substantially more efficient, requiring between 5.71 x 109 and 7.11 x 109 CPU cycles. These measured performance characteristics establish SPHINCS+ as a viable post-quantum signature candidate, though signature generation remains computationally intensive.
The Inevitable Erosion: Acknowledging the Limits of Resilience
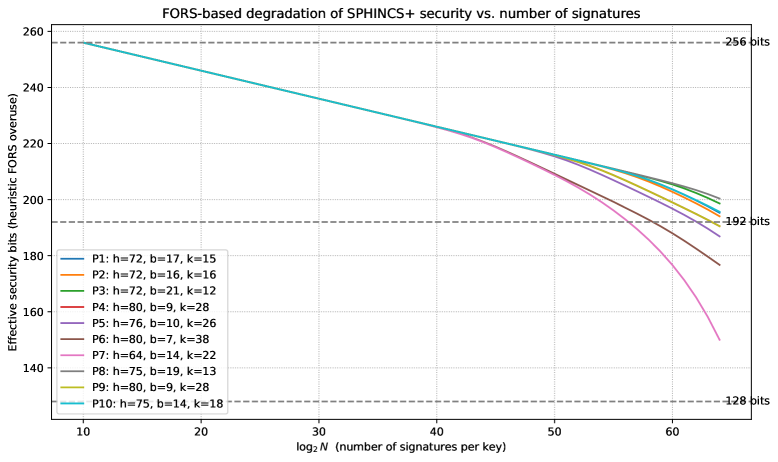
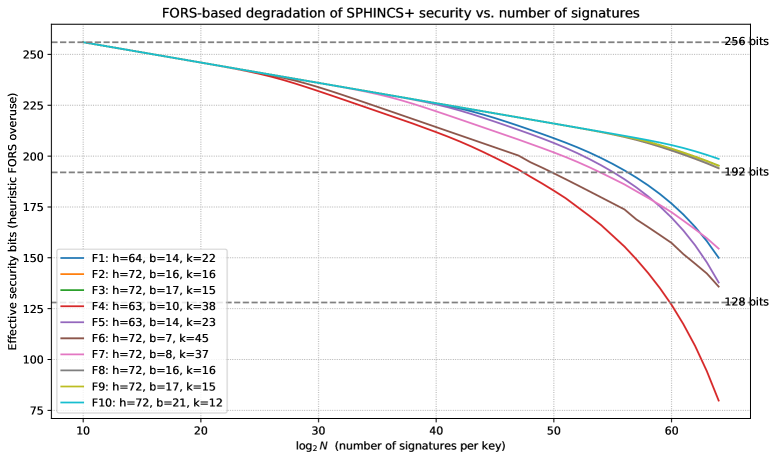
The foundation of security within the SPHINCS+ signature scheme relies heavily on the ‘FORS’ component, but its inherent structure presents a vulnerability to degradation with repeated use. Each time a signature is generated with the same key, the security of the ‘FORS’ component is incrementally reduced, as information about the private key leaks through the signature process. This isn’t a catastrophic failure with each signature, but rather a gradual weakening that necessitates careful key management and limits the number of signatures that can be safely generated with a single key pair. Developers and implementers must therefore consider strategies for key rotation or other mitigation techniques to prevent an attacker from accumulating enough information to compromise the private key over time, ultimately ensuring the long-term integrity of the system.
The integrity of cryptographic signatures within SPHINCS+ hinges on a principle called ‘Domain Separation’. This critical security measure ensures that each invocation of the hash function operates on distinct, unrelated data, preventing attackers from exploiting relationships between different hash calculations. This independence is achieved through the implementation of ‘Tweakable Hash Functions’, which allow for the introduction of unique, randomly generated values – or ‘tweaks’ – into the hashing process. By modifying the input to the hash function with these tweaks, each hash invocation effectively operates within its own isolated ‘domain’, hindering attempts to forge signatures by manipulating the underlying hash computations. Without robust domain separation, vulnerabilities could arise, allowing attackers to correlate hash values and compromise the security of the entire signature scheme.
SPHINCS+ currently generates signatures ranging from 56 to 60 kilobytes in size, a characteristic that defines a necessary compromise between computational performance and data transmission costs. While larger than signatures produced by currently dominant algorithms, this size is considered acceptable for applications demanding resilience against attacks from quantum computers – a threat projected to render many existing cryptographic systems obsolete. This viability, however, hinges on continued optimization and refinement of the algorithm, alongside active participation in standardization bodies to establish SPHINCS+ as a widely trusted and implemented post-quantum cryptographic standard. Further research focuses on reducing signature size without compromising security, aiming to broaden the scope of applications where SPHINCS+ can be effectively deployed and integrated into existing infrastructure.
The pursuit of cryptographic robustness, as demonstrated by Spinel’s exploration of SL4(Fp) hashing, echoes a fundamental truth about complex systems. It isn’t about achieving static perfection, but about building in the capacity to adapt and endure. As Blaise Pascal observed, “The dignity of man lies in thought.” This paper doesn’t seek a signature scheme impervious to all future attacks – such a thing is an illusion. Instead, it proposes a shift in the underlying algebraic structure, introducing a new layer of complexity intended to raise the bar for potential adversaries. The system doesn’t strive for invulnerability; it aims to propagate resilience, acknowledging that every defense will eventually require refinement and that true security lies in the capacity for continuous evolution.
The Horizon Recedes
Spinel’s substitution of conventional hashing with SL4(Fp) algebra is not an optimization-it is an admission. The pursuit of cryptographic strength through increasingly complex algebraic foundations reveals a fundamental truth: security isn’t a property to be built into a system, but a tension maintained against inevitable reduction. Each layer of abstraction introduces a new surface for attack, a new point of predictable failure. Monitoring, in this context, is the art of fearing consciously.
The long-term viability of any hash-based scheme hinges not on the cleverness of its mathematics, but on the rate at which assumptions erode. The shift toward algebraic hashing, while theoretically sound, merely postpones the encounter with the unavoidable: the limits of formal verification. True resilience begins where certainty ends-where one accepts that ‘bugs’ are not errors in implementation, but revelations of systemic vulnerability.
The next phase will not be about finding stronger hashes, but about cultivating systems that anticipate, rather than resist, their own obsolescence. The field must move beyond the notion of cryptographic ‘solutions’ and embrace the inherent impermanence of all digital structures. Spinel, then, isn’t a destination, but a particularly well-charted detour on a path that ultimately leads to entropy.
Original article: https://arxiv.org/pdf/2602.09882.pdf
Contact the author: https://www.linkedin.com/in/avetisyan/
See also:
- How to Unlock the Mines in Cookie Run: Kingdom
- YAPYAP Spell List
- How to Build Muscle in Half Sword
- Bitcoin Frenzy: The Presales That Will Make You Richer Than Your Ex’s New Partner! 💸
- Gears of War: E-Day Returning Weapon Wish List
- Bitcoin’s Big Oopsie: Is It Time to Panic Sell? 🚨💸
- How to Find & Evolve Cleffa in Pokemon Legends Z-A
- The Saddest Deaths In Demon Slayer
- How to Get Wild Anima in RuneScape: Dragonwilds
- Most Underrated Loot Spots On Dam Battlegrounds In ARC Raiders
2026-02-11 18:03