Author: Denis Avetisyan
New research introduces a hierarchical control system that dramatically speeds up the process of building effective cyber defenses in complex networks.
MetaDOAR efficiently solves simulation-based network security games by leveraging device selection and cached critic evaluations for scalable, game-theoretic cyber defense.
Effective cyber defense in large-scale networks is often hampered by the computational demands of game-theoretic solution methods. This paper, ‘A Scalable Approach to Solving Simulation-Based Network Security Games’, introduces MetaDOAR, a hierarchical meta-controller that accelerates multi-agent reinforcement learning by intelligently filtering device selections and caching critic evaluations. Through a partition-aware filtering layer and Q-value caching, MetaDOAR demonstrably achieves higher player payoffs than state-of-the-art baselines without incurring prohibitive memory or training costs. Could this approach unlock practical, scalable solutions for securing increasingly complex cyber infrastructures?
Beyond Reaction: Proactive Cyber Defense Through Anticipation
Conventional cyber defense historically operates on a reactive footing, responding to threats after they manifest – a strategy proving increasingly inadequate against modern adversaries. This approach typically involves signature-based detection, firewall rules triggered by known malicious activity, and incident response protocols enacted following a breach. However, the sheer volume and velocity of contemporary attacks, coupled with the rising sophistication of techniques like polymorphic malware and zero-day exploits, rapidly overwhelm these systems. Attackers are now adept at evading detection by blending malicious code with legitimate processes, exploiting previously unknown vulnerabilities, and leveraging automated tools to scan for and exploit weaknesses at scale. Consequently, defenses built on simply recognizing and blocking known threats struggle to keep pace, creating a persistent asymmetry favoring the attacker and necessitating a shift towards more proactive security postures.
While traditional cybersecurity often reacts to threats as they emerge, game-theoretic security proposes a shift towards anticipating and strategically countering potential attacks. This proactive approach frames cyber defense as a continuous interaction between an attacker and a defender, allowing for the optimization of defensive strategies based on predicted adversary behavior. However, the promise of game-theoretic solutions is significantly hampered by computational complexity as network scale increases. Calculating optimal strategies requires considering an exponentially growing number of possible attacker actions and network states; even moderately sized networks quickly become intractable for all but the most simplified models. This limitation necessitates approximations and heuristics, potentially sacrificing optimality and leaving systems vulnerable to novel or sophisticated attacks that fall outside the modeled scenarios. Consequently, translating the theoretical benefits of game-theoretic security into practical, scalable defenses remains a substantial challenge in modern cybersecurity.
The application of game theory to cybersecurity, specifically framing interactions as a Partially Observable Stochastic Game (POSG), offers a rigorous framework for anticipating attacker strategies and optimizing defenses. This approach acknowledges the inherent uncertainty in real-world scenarios – defenders rarely possess complete information about an adversary’s capabilities or intentions. However, translating this theoretical soundness into practical application presents significant hurdles. The computational complexity of solving POSGs scales exponentially with network size and the number of possible attacker actions, rendering exact solutions intractable for all but the simplest systems. Researchers are actively exploring approximation algorithms, heuristic methods, and dimensionality reduction techniques to manage this complexity, but a fundamental trade-off remains between solution accuracy and computational feasibility; effectively securing large, complex networks demands innovative methods to overcome the limitations of current computational resources and algorithms.
MetaDOAR: Scaling Cyber Defense Through Meta-Control
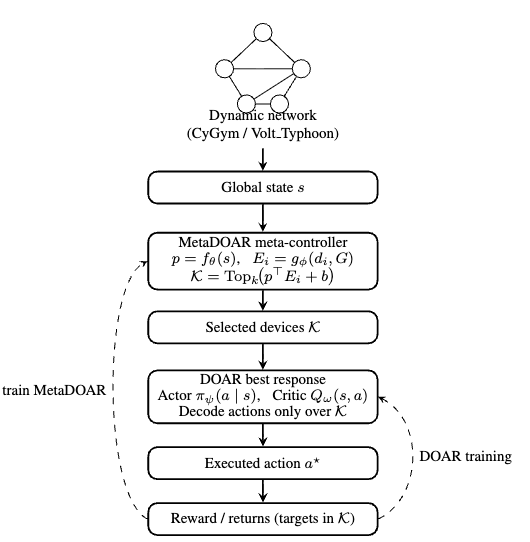
MetaDOAR functions as a meta-controller designed to improve the scalability of the Double Oracle algorithm for cyber defense applications. The Double Oracle, while effective, faces computational challenges when deployed in large networks due to its need to evaluate security policies across numerous devices. MetaDOAR addresses this by acting as a supervisory layer that manages and optimizes the operation of the Double Oracle, allowing it to efficiently handle the increased complexity associated with larger network deployments. This is achieved through techniques like Top-KK Filtering and LRU caching, which reduce computational load without compromising the overall security posture. Consequently, MetaDOAR enables the effective implementation of the Double Oracle algorithm in environments characterized by a high volume of network devices and traffic.
Top-KK Filtering within MetaDOAR operates by identifying the K devices exhibiting the highest critic values at each control epoch. This approach strategically reduces the computational load by focusing analysis and mitigation efforts on a limited, demonstrably critical subset of the network. The selection process prioritizes devices assessed as posing the greatest immediate threat or vulnerability, effectively narrowing the scope of required security actions. By limiting the active device set to the top K, MetaDOAR maintains security efficacy while significantly decreasing the computational complexity associated with large-scale network defense, as the critic values of the remaining devices are not evaluated in that epoch.
To improve computational efficiency, MetaDOAR incorporates a Least Recently Used (LRU) Cache for storing the evaluations generated by its critic component. This cache mechanism avoids recalculating critic evaluations for network states that have been previously assessed. When a new network state is encountered, the critic first checks the LRU Cache; if the evaluation exists, it is retrieved in O(1) time. If not, the evaluation is computed, stored in the cache, and then returned. The LRU policy ensures that the least recently accessed evaluations are evicted from the cache when it reaches capacity, minimizing storage overhead while maximizing the probability of cache hits and reducing redundant computations.
MetaDOAR utilizes structural embeddings to represent the network topology as a vector space, where node proximity in the embedding space correlates to network proximity. These embeddings, generated using techniques like node2vec or DeepWalk, capture inherent network structure and relationships between devices. The controller employs these embeddings to assess device criticality; devices with high centrality or those bridging important network segments, as indicated by their embedding vectors, are prioritized for monitoring and defense. This approach allows MetaDOAR to move beyond simple degree centrality and consider broader network context when selecting devices for Top-KK filtering, improving the effectiveness of the Double Oracle algorithm in large-scale networks.
Empirical Validation: Performance in CyGym
MetaDOAR was evaluated using CyGym, a simulation platform designed to facilitate research in cyber operations through scalable network environments. CyGym allows for the creation of large-scale cyber networks, enabling the assessment of algorithms like MetaDOAR under realistic conditions and at scales difficult to replicate in physical deployments. The platform provides a standardized interface for controlling network devices and observing agent interactions, ensuring reproducibility and comparability of results. Its architecture supports the simulation of thousands of devices, making it suitable for evaluating the scalability and performance of multi-agent reinforcement learning algorithms in complex cyber scenarios.
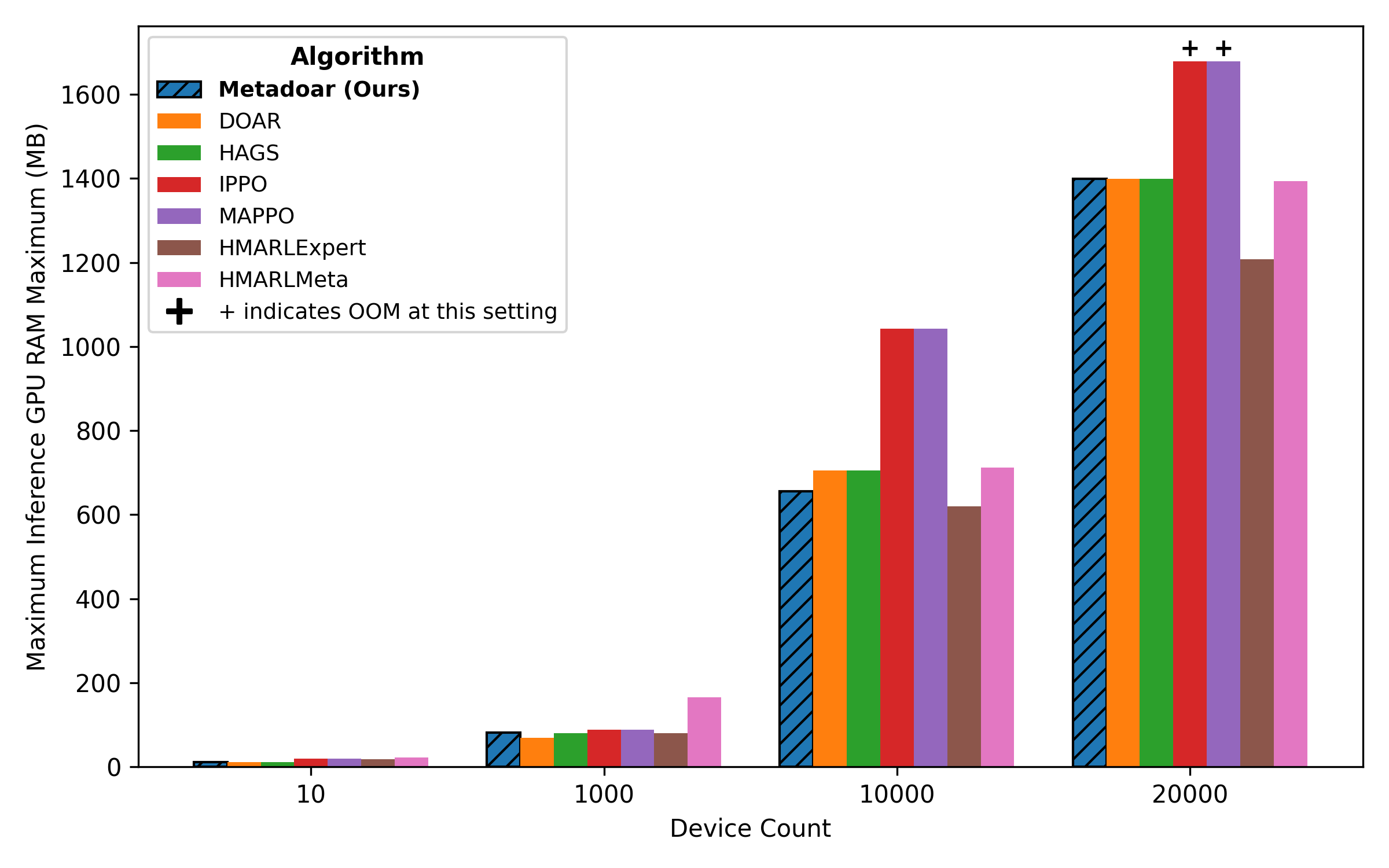
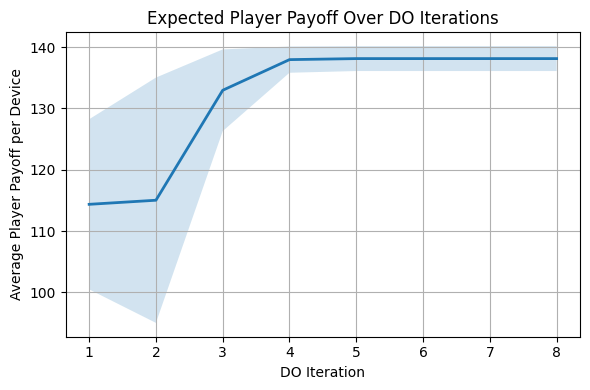
Evaluations conducted within the CyGym environment indicate MetaDOAR’s superior performance compared to established Multi-Agent Reinforcement Learning (MARL) baselines. Specifically, MetaDOAR consistently yielded higher results than MAPPO, IPPO, HAGS, HMARLExpert, and HMARLMeta across a range of cyber operation simulations. This outperformance was observed in terms of player payoffs and overall system efficiency, establishing MetaDOAR as a competitive solution within the MARL landscape for network security applications. The comparative analysis demonstrates a quantifiable advantage of MetaDOAR’s architecture and algorithms over existing state-of-the-art methods.
Evaluations within the CyGym environment demonstrate that MetaDOAR achieves approximately doubled player payoffs at a network scale of 10,000 devices when compared to prior implementations of the DOAR (Distributed Opponent Aware Reinforcement Learning) approach. This performance improvement indicates a substantial gain in collective reward for agents operating within the simulated cyber environment at large scale. Specifically, tests reveal a consistent doubling of cumulative payoffs, suggesting enhanced strategic coordination and resource allocation enabled by the MetaDOAR architecture as network complexity increases.
Evaluations within the CyGym environment demonstrated MetaDOAR’s ability to function effectively with networks comprising 10,000 devices, a scale at which several baseline Multi-Agent Reinforcement Learning algorithms exhibited instability or experienced substantial performance degradation. Specifically, MAPPO, IPPO, HAGS, HMARLExpert, and HMARLMeta either failed to converge to stable policies or became computationally intractable as network size increased. MetaDOAR, conversely, maintained operational stability and acceptable computation times at this scale, indicating a significant advancement in scalability for distributed cyber operations simulations.
Performance evaluations demonstrate that MetaDOAR exhibits consistent resource utilization as network scale increases. Specifically, forward pass latency remains low, averaging between ∼1-2 ms, even when simulating networks of 10,000 devices. Concurrent with this scaling, MetaDOAR maintains relatively constant memory usage of approximately ∼1.4 GB throughout the tested network sizes. These results indicate efficient computational performance and scalability, allowing for the simulation of large-scale cyber operations without significant performance degradation.
Beyond Defense: Implications and Future Trajectories
In an increasingly interconnected world, large-scale networks face constant threats from sophisticated cyber attacks, demanding robust and adaptable defense mechanisms. MetaDOAR addresses this critical need by offering a practical solution grounded in game theory and modern reinforcement learning. This approach allows the system to not simply react to threats, but to proactively anticipate and counter them, effectively shifting the defensive posture from passive to active. By learning from simulated attack scenarios and continuously refining its strategies, MetaDOAR aims to provide a resilient shield against evolving cyber threats, minimizing potential damage and ensuring the continued functionality of vital network infrastructure. The system’s design prioritizes scalability and real-world applicability, positioning it as a valuable asset in the ongoing battle to secure digital systems.
MetaDOAR distinguishes itself as a resilient network defense system through the synergistic application of game theory and reinforcement learning. It models the interaction between a network and potential attackers as a strategic game, allowing the system to anticipate and respond to evolving threats. Unlike static defenses, MetaDOAR employs reinforcement learning algorithms to continuously refine its strategies based on observed attack patterns and network vulnerabilities. This adaptive capability is crucial; the system doesn’t simply react to known attacks, but proactively learns optimal defensive actions, maximizing network security while minimizing potential disruptions. The combination allows MetaDOAR to navigate the complexities of modern cyber warfare, offering a robust and evolving shield against increasingly sophisticated adversaries, and promising a proactive stance against future, unknown threats.
Continued development of MetaDOAR prioritizes scaling its capabilities to address increasingly sophisticated cyber threats, moving beyond simulated environments toward practical deployment. Researchers aim to expand the system’s capacity to model and respond to multi-stage attacks, zero-day exploits, and coordinated campaigns that leverage diverse attack vectors. A key focus involves integrating MetaDOAR with existing security information and event management (SIEM) systems, intrusion detection systems, and firewalls to create a cohesive and automated defense layer. This integration will facilitate real-time threat analysis, proactive vulnerability patching, and dynamic network reconfiguration, ultimately enhancing an organization’s overall security posture and resilience against evolving cyber risks.
Advancements in network security increasingly rely on accurately representing the complex state of a system, and further research into State Embedding techniques promises to significantly refine this process. These techniques aim to distill raw network data – encompassing traffic patterns, system logs, and vulnerability assessments – into a condensed, meaningful format that machine learning algorithms can readily interpret. By creating more nuanced and informative state embeddings, MetaDOAR’s ability to predict and counter sophisticated cyber attacks is expected to improve; a richer understanding of network vulnerabilities allows for the development of preemptive defenses and more effective resource allocation. Ongoing investigations explore novel embedding methods, including those leveraging graph neural networks and unsupervised learning, with the ultimate goal of creating a dynamic, self-learning system capable of adapting to evolving threat landscapes and bolstering overall network resilience.
The presented work prioritizes efficiency in a complex domain, mirroring a fundamental tenet of effective system design. MetaDOAR’s hierarchical approach to managing network security games-specifically, its caching of critic evaluations to accelerate strategy selection-demonstrates a commitment to minimizing unnecessary computation. This aligns with Vinton Cerf’s observation that, “The Internet treats everyone the same.” While initially referring to network neutrality, the sentiment extends to computational resources; efficient algorithms treat data and processing time with equal consideration, avoiding wasteful expenditure. The core concept of scalability, enabled by MetaDOAR, exemplifies this principle; a streamlined system affords equitable access to security, even as network dimensions increase.
Where Do We Go From Here?
The presented work offers acceleration, not absolution. MetaDOAR streamlines the selection process, a necessary concession when confronting the combinatorial explosion inherent in network security games. However, the fundamental challenge remains: perfect defense is a phantom, best response an asymptotic ideal. Future efforts should not chase increasingly granular simulations-complexity for complexity’s sake-but instead focus on distilling the essential asymmetries within network topologies. What truly differentiates a critical node from merely another? What vulnerabilities are consistently exploitable, regardless of specific configuration?
The reliance on cached critic evaluations, while pragmatic, introduces a degree of historical bias. A network perpetually optimized against past attacks is, inevitably, vulnerable to the novel. Research must explore methods for dynamically adjusting these caches, incorporating elements of adversarial learning to anticipate-not merely react to-emerging threats. Intuition suggests that a blend of model-based and model-free reinforcement learning may offer the requisite adaptability.
Ultimately, the pursuit of scalable cyber defense is a constant negotiation between computational tractability and realistic modeling. Code should be as self-evident as gravity. The true measure of progress will not be the size of the networks addressed, but the simplicity with which they are secured.
Original article: https://arxiv.org/pdf/2602.16564.pdf
Contact the author: https://www.linkedin.com/in/avetisyan/
See also:
- Poppy Playtime Chapter 5: Engineering Workshop Locker Keypad Code Guide
- Jujutsu Kaisen Modulo Chapter 23 Preview: Yuji And Maru End Cursed Spirits
- 8 One Piece Characters Who Deserved Better Endings
- God Of War: Sons Of Sparta – Interactive Map
- Mewgenics Tink Guide (All Upgrades and Rewards)
- Top 8 UFC 5 Perks Every Fighter Should Use
- Who Is the Information Broker in The Sims 4?
- Sega Declares $200 Million Write-Off
- Full Mewgenics Soundtrack (Complete Songs List)
- Pressure Hand Locker Code in Poppy Playtime: Chapter 5
2026-02-19 21:18