Author: Denis Avetisyan
A new framework streamlines multi-party cryptographic operations by distributing the signing process across multiple Trusted Platform Modules.

PiTPM enables efficient and scalable multi-signature schemes using deterministic commitment computation and reduced coordination overhead for enhanced security and performance.
While Trusted Platform Modules (TPMs) offer robust hardware-based security for cryptographic operations, existing multi-signature schemes demand synchronous coordination between participants, creating scalability bottlenecks and potential failure points. This paper introduces PiTPM: Partially Interactive Signatures for Multi-Device TPM Operations, a novel framework that eliminates this interactive requirement through a hybrid trust architecture and deterministic commitment computation. By leveraging pre-shared randomness securely stored in an aggregator, PiTPM achieves constant-size signatures regardless of participant count, offering a paradigm shift in TPM-based cryptographic system design. Could this approach unlock truly scalable and resilient distributed cryptographic applications across diverse device landscapes?
The Inherent Limitations of Redundant Signature Schemes
Traditional multi-signature schemes, designed to enhance security through redundancy, frequently demand intricate coordination and multiple communication rounds between all participating parties. This process isn’t simply a matter of collecting signatures; each participant must verify the legitimacy of the transaction and the other signers, often requiring back-and-forth messaging to confirm agreement and prevent malicious activity. The necessity for this sequential interaction introduces significant latency, hindering real-time applications and increasing the potential for network congestion. Moreover, the complexity of these protocols creates a larger attack surface, as each communication channel and verification step presents a potential vulnerability. Consequently, the practical implementation of these schemes is often limited by the logistical challenges of managing this extensive inter-party dialogue, especially within large or geographically dispersed groups.
Traditional multi-signature schemes, despite their intent to enhance security through redundancy, frequently encounter practical limitations stemming from scalability and susceptibility to denial-of-service attacks. Each additional participant in the signature process introduces further communication overhead and computational burden, drastically reducing transaction speeds and increasing costs as the group grows. This inherent complexity makes these schemes less viable for applications requiring high throughput or large numbers of signers. Moreover, malicious actors can exploit the requirement for all signers to participate by overwhelming the system with requests, effectively halting the signature process and rendering the scheme unusable-a significant concern in resource-constrained environments or when dealing with unreliable networks. Consequently, the practical applicability of these schemes is often confined to scenarios with a limited and trusted group of participants.
Despite the efficiency gains offered by signature aggregation techniques like BLS signatures, practical deployment faces a significant hurdle: limited hardware support. While BLS signatures reduce signature size and verification complexity, currently widespread hardware security modules (HSMs)-critical for secure key storage and cryptographic operations-do not natively support the BLS signature algorithm. This necessitates software-based implementations, which introduce performance overhead and potential security vulnerabilities compared to dedicated hardware acceleration. Consequently, organizations heavily invested in existing HSM infrastructure face substantial costs and complexities when attempting to integrate BLS signatures, hindering broader adoption despite the algorithmic advantages. The lack of native support effectively restricts BLS signatures to environments where software-based cryptography is acceptable, limiting their use in high-security or performance-critical applications.
A significant vulnerability inherent in many multi-signature schemes centers around the potential for a ‘Rogue Key Attack’. This occurs when a subset of participants collude or are compromised, allowing them to forge signatures without the genuine consent of all required parties. The core issue lies in the distributed key generation process; if malicious actors gain control over enough key shares, they can construct a fraudulent signature that appears valid to verifiers. While multi-signature schemes are designed to prevent single points of failure, they often lack robust defenses against such collusive attacks, particularly when the number of participants is large and trust assumptions are not carefully managed. This risk underscores the need for advanced cryptographic techniques and secure key management protocols to mitigate the threat of forged signatures and maintain the integrity of the system.

Threshold Signatures: A Foundation of Robustness and Efficiency
Threshold signature schemes represent an advancement over traditional multi-signature schemes by reducing the number of required participants for signature generation. While multi-signatures typically necessitate the cooperation of all designated parties, a threshold scheme only demands a pre-defined subset – the threshold – to produce a valid signature. This is achieved by dividing a private key into shares distributed among participants. Consequently, the scheme’s fault tolerance is significantly improved; the failure or unavailability of participants below the threshold number does not impede signature creation, ensuring continued functionality even with partial system failures or compromised nodes. The threshold, denoted as t, is a parameter set during scheme initialization, and requires t out of n participants to cooperate.
Lagrange interpolation is a polynomial interpolation method used in threshold signature schemes to combine individual secret shares into a single signature without revealing the complete private key. Each participant holds a share, which is a point on a polynomial. Given n shares, a unique polynomial of degree n-1 can be constructed. Evaluating this polynomial at x=0 reveals the secret signature. The formula for Lagrange interpolation is f(x) = \sum_{j=0}^{n-1} y_j \prod_{k=0, k \neq j}^{n-1} \frac{x - x_k}{x_j - x_k} , where (x_j, y_j) represents the jth share. This allows reconstruction of the signature with only a threshold number of shares, eliminating the need for all participants to contribute their shares directly and maintaining security.
Feldman Verifiable Secret Sharing (VSS) is a critical element in threshold signature schemes, guaranteeing the validity of secret shares distributed among participants. Unlike standard secret sharing, Feldman VSS allows each participant to verify that other participants’ shares are consistent with their own, and that no single participant is reporting a share that would allow for the reconstruction of an incorrect secret. This verification process involves each participant publishing a commitment to their share, and then revealing a “proof” demonstrating the consistency of all shares. The process relies on cryptographic commitments and zero-knowledge proofs to ensure that shares are valid without revealing the secret itself. By confirming the correctness of shares, Feldman VSS mitigates the risk of malicious or faulty participants corrupting the signature generation process, bolstering both the security and reliability of the threshold signature scheme.
Threshold signatures mitigate single points of failure inherent in traditional digital signature schemes by distributing signing power amongst multiple participants. In a standard scheme, compromise of a single private key allows for the forgery of signatures. Conversely, threshold signatures require collusion amongst a pre-defined threshold – t – of n key holders to construct a valid signature. If fewer than t keys are compromised, the security of the system remains intact. This dramatically increases the effort required for a malicious actor to forge a signature, as they must gain control of a substantial proportion of the key distribution, thereby significantly reducing the risk associated with individual key compromises.
Deterministic Commitments and Hardware-Rooted Security
The Aggregator Framework addresses commitment scheme inefficiencies by facilitating pre-shared randomness among participants. This pre-shared randomness is utilized to deterministically compute a global commitment value, effectively removing the requirement for an interactive commitment exchange process. Traditional multi-signature schemes typically necessitate each participant to individually commit and then reveal their commitments, creating communication overhead and potential vulnerabilities. By pre-sharing randomness, the Aggregator Framework allows a single entity to compute the global commitment based on participant inputs and the shared randomness, significantly reducing communication complexity and streamlining the commitment phase of the protocol. This deterministic approach ensures all participants arrive at the same commitment value without needing to exchange individual commitments.
The Aggregator Framework’s security is fundamentally dependent on the use of Pseudorandom Functions (PRFs) for generating randomness. PRFs are deterministic functions that, given a secret key and an input, produce a pseudorandom output which is computationally indistinguishable from a truly random value. This generated randomness is then used in the commitment scheme; therefore, the cryptographic strength of the PRF directly impacts the security of the commitments. Any weakness or predictability in the PRF output would compromise the randomness needed to ensure the commitments are unlinkable and prevent attackers from manipulating the system. The selection of a robust and well-vetted PRF is, therefore, a critical design consideration for the framework.
Integration of the Aggregator Framework with Trusted Platform Modules (TPMs) provides a hardware-backed security layer for cryptographic keys and operations. TPMs are dedicated hardware security modules that offer secure key generation, storage, and usage, preventing key compromise through software vulnerabilities. By leveraging the TPM, the Aggregator Framework avoids exposing sensitive cryptographic material to the operating system or potentially malicious software. Specifically, the TPM can perform cryptographic functions, such as PRF evaluations and signature generation, within a protected environment, ensuring the integrity and confidentiality of these operations and thereby enhancing the overall security of the commitment scheme.
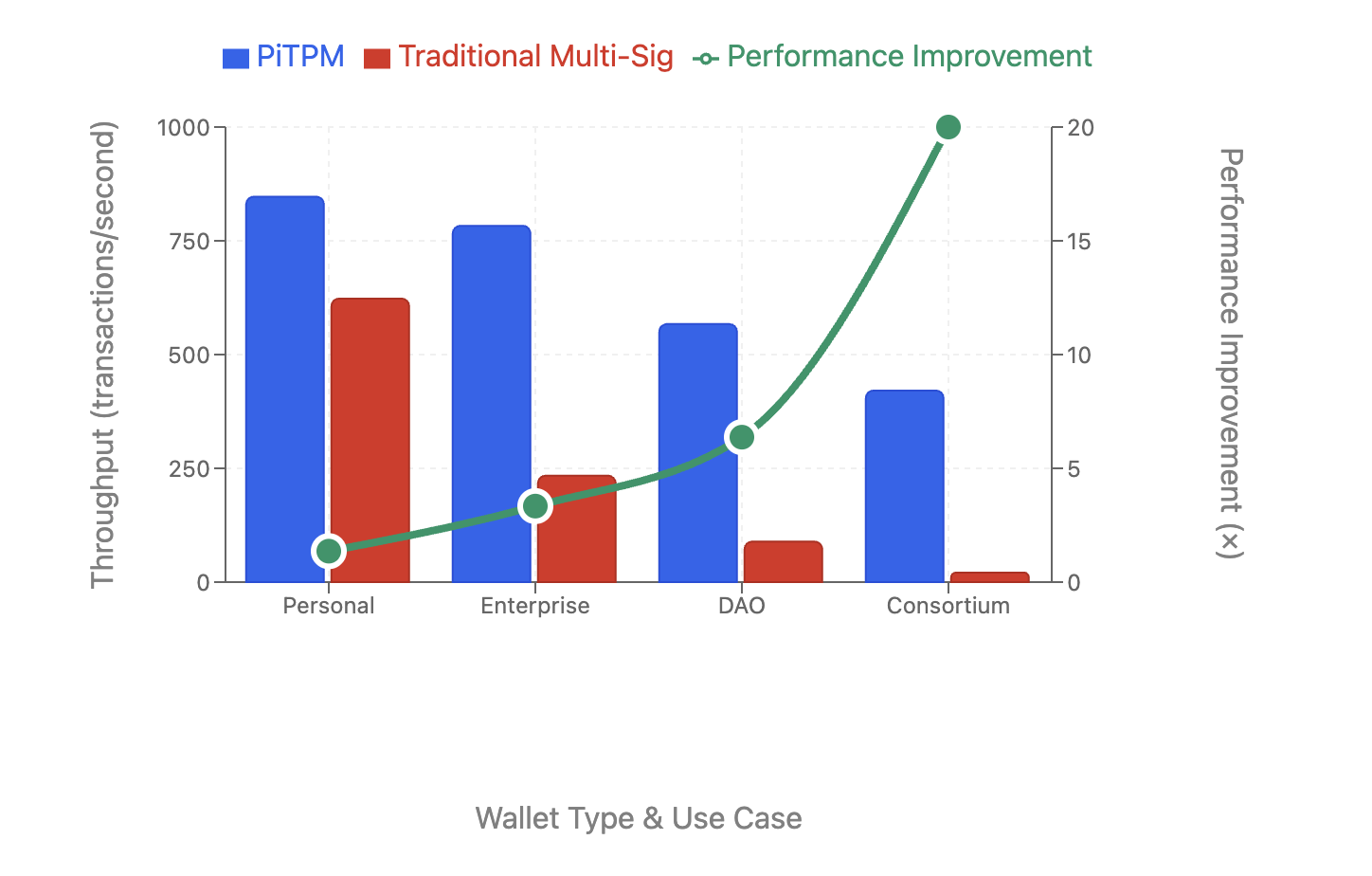
The PiTPM multi-signature framework, leveraging Trusted Platform Modules, achieves signature generation times ranging from 89.4ms to 108.8ms. Importantly, these generation times remain constant regardless of the number of participating signers, indicating scalability. Performance analysis demonstrates a 15-25% overhead compared to traditional multi-signature schemes, representing a trade-off for the enhanced security and deterministic properties provided by the TPM-based implementation.
The Implications for Scalable and Secure Distributed Systems
Traditional multi-signature schemes, while enhancing security, often struggle with scalability due to the extensive communication required between all participating parties to authorize a single transaction. This new approach circumvents these limitations by significantly minimizing this overhead; instead of requiring full interaction amongst all signers, it allows for a streamlined process where commitments are made and verified more efficiently. This reduction in coordination not only accelerates transaction speeds but also reduces the computational burden on each participant, making it particularly suitable for large consortia or systems with numerous stakeholders. By decoupling the need for synchronous communication, the scheme enables a far more responsive and scalable solution for secure, distributed transactions.
The design of this system prioritizes seamless integration and operational efficiency through deterministic commitments. Unlike probabilistic schemes that require multiple rounds of verification or rely on randomness, these commitments yield consistent results regardless of computational environment. This predictability drastically simplifies implementation across diverse platforms, from powerful servers to embedded devices with limited processing power and memory. Consequently, resource-constrained environments, such as IoT networks or mobile applications, can participate reliably without incurring substantial overhead. The deterministic nature not only streamlines integration but also enhances overall performance by eliminating the need for complex validation processes, fostering broader applicability and scalability of secure multi-party computation.
The integration of Trusted Platform Modules (TPMs) establishes a foundational hardware security layer, critically safeguarding cryptographic keys from compromise and physical tampering. These specialized microchips create a secure enclave, isolating sensitive data and operations from the broader system-even if the operating system is compromised by malware or subjected to a physical attack. By binding keys to the TPM, the system ensures that private keys never fully exist in software, substantially diminishing the attack surface available to malicious actors. This approach not only shields against remote attacks but also provides resilience against physical intrusions, as any attempt to extract or manipulate the keys without the TPM’s authorization is detectable and prevents unauthorized use – offering a substantial enhancement to the overall security posture of distributed systems and multi-signature schemes.
Performance evaluations reveal that PiTPM substantially enhances transaction throughput compared to conventional multi-signature methods. Testing demonstrates a 15 to 18-fold increase in speed, enabling the processing of 421 transactions per second utilizing a 50-of-75 consortium wallet. This represents a significant leap forward from traditional approaches, which were limited to approximately 21 transactions per second under the same conditions. The enhanced efficiency offered by PiTPM positions it as a viable solution for applications demanding high scalability and rapid transaction confirmation, particularly within consortium and enterprise blockchain deployments.
The pursuit of scalable cryptographic signatures, as demonstrated by PiTPM, fundamentally relies on deterministic commitment – a principle mirroring the elegance of mathematical invariants. As John McCarthy observed, “The best way to program is to write code that doesn’t have to be debugged.” This resonates deeply with the framework’s design; by eliminating coordination bottlenecks and embracing deterministic computation, PiTPM strives for a solution verifiable through inherent correctness, rather than relying on complex runtime validation. The paper’s focus on minimizing external dependencies and maximizing internal consistency directly addresses the ideal of provable algorithms, ensuring that the signature’s validity isn’t merely observed through testing, but guaranteed by its foundational principles. Let N approach infinity – what remains invariant is the signature’s trustworthiness.
What Remains to Be Proven?
The elegance of PiTPM lies in its attempt to impose order on an inherently chaotic problem – distributed consensus. While the framework demonstrably reduces coordination overhead, a critical question persists: how robust is the deterministic commitment computation against subtle, yet systemic, hardware failures? The claim of enhanced security hinges on the absolute predictability of TPM behavior, an assumption that, given the realities of silicon, feels… optimistic. Reproducibility, after all, is not merely a statistical observation; it’s a prerequisite for trust.
Future work must rigorously address the error modes of TPMs themselves. A truly provable system demands a formal model of the underlying hardware, accounting for manufacturing variations, thermal drift, and even cosmic rays. Furthermore, the scalability of PiTPM remains largely unexplored. While the framework may function efficiently with a modest number of devices, the computational complexity could quickly become prohibitive as the network grows. The pursuit of efficiency should not come at the expense of verifiability.
Ultimately, the success of distributed cryptographic systems like PiTPM will not be measured by benchmarks, but by their resilience against adversarial forces and the relentless march of entropy. The goal is not simply to build a secure system, but to prove its security, and that requires a level of mathematical rigor often absent in practical implementations. The devil, predictably, resides in the details – and in the silicon.
Original article: https://arxiv.org/pdf/2602.09707.pdf
Contact the author: https://www.linkedin.com/in/avetisyan/
See also:
- Epic Games Store Free Games for November 6 Are Great for the Busy Holiday Season
- EUR USD PREDICTION
- How to Unlock & Upgrade Hobbies in Heartopia
- Battlefield 6 Open Beta Anti-Cheat Has Weird Issue on PC
- Sony Shuts Down PlayStation Stars Loyalty Program
- The Mandalorian & Grogu Hits A Worrying Star Wars Snag Ahead Of Its Release
- ARC Raiders Player Loses 100k Worth of Items in the Worst Possible Way
- Unveiling the Eye Patch Pirate: Oda’s Big Reveal in One Piece’s Elbaf Arc!
- TRX PREDICTION. TRX cryptocurrency
- Prime Gaming Free Games for August 2025 Revealed
2026-02-12 05:54