Author: Denis Avetisyan
A new mathematical proof establishes, with greater rigor than ever before, that honest nodes will consistently outpace malicious actors in the Bitcoin network.
![The system models a punctuated arrival process wherein intervals of length Δ are systematically removed, effectively deleting honest blocks and influencing a cumulative score-<span class="katex-eq" data-katex-display="false">B(i)[latex]-that reflects the impact of these deletions on a fully-delayed chain, with the score growth within each interval-[latex]S_{b,i}[latex]-being statistically independent and identically distributed due to the consistent [latex]\Delta</span>-length removal.](https://arxiv.org/html/2601.09082v1/x2.png)
Researchers demonstrate, under defined network conditions, that the probability of an honest chain dominating approaches one, resolving key limitations in previous security analyses and extending to generalized Bitcoin protocols.
Despite ongoing analysis, formally proving the security of the Bitcoin protocol remains a complex challenge, particularly when accounting for realistic network conditions. This is addressed in 'Rigorous and Generalized Proof of Security of Bitcoin Protocol with Bounded Network Delay', which presents a simplified yet rigorous security proof for a generalized Bitcoin model allowing variable block scores and bounded network delays. The paper demonstrates, with probability one, that honest blocks will infinitely outpace adversarial ones so long as the honest mining rate-even accounting for full transmission delay-exceeds the adversary’s rate, correcting a flaw in prior random walk-based proofs. Could this formalized approach pave the way for more secure and adaptable blockchain consensus mechanisms beyond Bitcoin itself?
The Illusion of Decentralized Trust
The Bitcoin protocol introduces a revolutionary approach to digital currency by eliminating the need for a central authority. Instead of relying on a bank or financial institution to validate transactions, Bitcoin operates as a decentralized network where every participant, or node, contributes to maintaining the integrity of the system. This distributed trust model hinges on the assumption that the majority of network nodes will act honestly - verifying transactions and adhering to the protocol’s rules. The security of the entire system, therefore, isn’t guaranteed by a single entity, but by a collective agreement amongst a potentially vast and geographically dispersed group of participants. This fundamental reliance on honest participation allows Bitcoin to function without the vulnerabilities inherent in centralized systems, but simultaneously introduces a unique set of challenges regarding network security and the potential for adversarial behavior.
The Bitcoin protocol represents a novel approach to establishing trust in a digital currency, yet its security isn't simply assumed-it demands careful mathematical scrutiny. Recent research rigorously analyzes the conditions necessary for the Bitcoin network to remain secure against malicious actors. This work demonstrates that the probability of the ‘honest chain’ - the longest sequence of valid transactions maintained by legitimate network participants - remaining dominant doesn't just increase with time, it increases exponentially. This means that as the network matures and more blocks are added to the chain, the likelihood of a successful attack diminishes at an accelerating rate, providing a robust foundation for long-term stability. The study quantifies this security margin, revealing that the network's resilience isn't a static property, but rather a dynamically strengthening shield against potential threats.
The long-term security of Bitcoin hinges on a delicate balance between computational power controlled by honest network participants and that wielded by potential adversaries. Recent research rigorously demonstrates that the probability of an adversary successfully constructing a longer, dominating chain-effectively rewriting the transaction history-decreases exponentially with time. Specifically, the probability scales as Aexp(-ct'), where ‘A’ and ‘c’ represent constants dependent on network parameters, and ‘t’ signifies time. This mathematical formulation illustrates a crucial point: while an attack is theoretically possible, the likelihood of it succeeding diminishes rapidly as the blockchain matures and honest participation continues, offering a quantifiable measure of the network’s increasing resilience against malicious actors. This analysis provides a foundation for understanding the conditions under which Bitcoin’s trustless system can reliably maintain its integrity over extended periods.
Mapping the Boundaries of Honest Growth
The SecurityRegion of the Bitcoin network delineates the parameter space where the cumulative work of the honest chain consistently exceeds that of any potential attacker. This region is fundamentally defined by the probability that an adversary, even with a significant initial advantage, will fail to construct a longer chain than the honest chain over time. Specifically, the SecurityRegion is determined by factors such as the honest network’s hashing power, the adversary’s hashing power, and the network’s propagation delay; it represents the conditions under which the honest chain’s expected growth consistently outpaces that of the attacker, ensuring the integrity and immutability of the blockchain. A larger SecurityRegion indicates a more robust network, less susceptible to a 51% attack or chain reorganization.
AdversaryScoreGrowth and HonestScoreGrowth quantify the rate at which competing chains - one controlled by an attacker and one by honest nodes - extend their respective leads in a network security context. Security is fundamentally dependent on the honest chain’s blockrate λ_h exceeding the adversary’s blockrate λ_a. A higher λ_h relative to λ_a indicates a faster accumulation of confirmations on the honest chain, making it increasingly difficult and costly for the adversary to overtake it. Conversely, if λ_a approaches or exceeds λ_h, the adversary’s chain can grow at a comparable or faster rate, threatening the integrity and immutability of the network. These growth rates are directly influenced by factors such as hashpower distribution, block propagation times, and network latency.
Adversarial and honest chain growth rates, \lambda_a and \lambda_h respectively, are directly influenced by probabilistic network characteristics including block propagation delays, node connectivity, and the distribution of hashing power. Accurate modeling requires accounting for variations in these parameters; simple deterministic models fail to capture the stochastic nature of block dissemination. Robust techniques incorporate propagation delay distributions, orphan rates, and the impact of network topology on block acceptance probability. Furthermore, models must consider the finite speed of light and geographical distribution of nodes to realistically simulate competitive block propagation scenarios and accurately predict security region boundaries.
The Illusion of Control: Modeling Network Delays
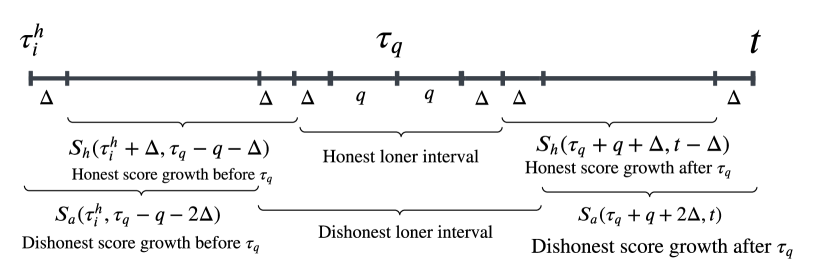
The BoundedDelayNetworkModel offers a rigorous approach to evaluating Bitcoin’s resilience against attacks by establishing a defined upper limit on message transmission times across the network. This framework simplifies the complex reality of variable network latency, allowing researchers to model worst-case scenarios and calculate the probability of successful attacks with greater precision. By assuming a maximum propagation delay, the model creates a constrained environment where the impact of network conditions can be isolated and analyzed. This is particularly valuable for assessing the vulnerability of the system to attacks that rely on quickly propagating invalid blocks or transactions, as it provides a quantifiable basis for understanding how quickly malicious information can spread relative to honest confirmations. The resulting insights are crucial for refining Bitcoin’s consensus mechanisms and bolstering its overall security posture.
The FullyDelayedHonestChain represents a deliberately pessimistic, yet crucial, scenario for evaluating Bitcoin network security. This model postulates that honest miners experience the maximum possible propagation delay for their newly mined blocks, effectively creating the most challenging conditions for rapid confirmation. By assuming this worst-case latency, researchers can rigorously assess the network's resilience against attacks, specifically examining how quickly a malicious actor might attempt to create a competing chain. The analysis focuses on the probability that a dishonest miner can successfully propagate a conflicting block before the honest chain gains sufficient confirmations, thereby establishing a higher degree of certainty regarding the network’s ability to withstand manipulation even under severely constrained conditions. This approach allows for a quantifiable measure of security, independent of real-world network performance, providing a valuable benchmark for system improvements and parameter adjustments.
To rigorously assess Bitcoin network security under realistic conditions, researchers employ the PuncturedArrivalProcess, a probabilistic model that simulates block propagation while accounting for the δ -constrained delays inherent in the BoundedDelayNetworkModel. This process doesn't simply count arriving blocks; instead, it ‘punctures’ the expected arrival stream to reflect the maximum allowable delay, providing a conservative estimate of successful block delivery. Crucially, this analysis leverages the ChernoffBound - a mathematical tool for bounding the probability of deviations from the expected value - to calculate the likelihood of an attacker successfully propagating a competing chain. By determining the probability that a malicious chain gains sufficient confirmations despite these propagation constraints, the PuncturedArrivalProcess, in conjunction with the ChernoffBound, offers a quantifiable measure of the network's resilience against attacks and helps define the parameters needed to maintain a secure blockchain.
The Fragility of Consensus: Private and Selfish Mining
Private and Selfish Mining attacks pose substantial risks to the Bitcoin network by exploiting the block withholding strategy to undermine the consensus mechanism. In these attacks, an adversary mines blocks but intentionally does not immediately broadcast them to the network. This allows the attacker to build a private chain, potentially longer than the public chain, and then selectively release blocks to either overtake the public chain or create competing forks. The success of these attacks doesn’t rely on creating invalid blocks, but rather on manipulating the block propagation delay and leveraging probabilistic outcomes to gain control over chain growth, disrupting the established order and potentially leading to double-spending or censorship.
Private and selfish mining attacks function by strategically withholding mined blocks from the public Bitcoin network. An adversary, rather than immediately broadcasting a solved block, maintains it locally and continues mining on top of it, creating a private, longer chain in secret. The attacker’s goal is to eventually release this private chain, which, due to its greater accumulated proof-of-work, would be accepted by the network as the valid chain, effectively overwriting the honest chain and allowing the attacker to potentially double-spend funds or disrupt network consensus. The success of this strategy relies on the attacker’s ability to achieve a higher block production rate than the honest miners, and on the time it takes for the network to recognize the discrepancy and switch to the longer chain.
The probability of a successful private or selfish mining attack is directly correlated to the relationship between the NakamotoInterval - the expected time between blocks on the Bitcoin network - and the rate at which an adversary can generate blocks. A higher adversarial blockrate, representing greater computational power controlled by the attacker, increases the likelihood of the adversary building a longer chain than the honest network participants. This dynamic is formally captured within the SecurityRegion, a quantifiable space defining conditions for network security. Our proofs demonstrate that Merged Bitcoin becomes inherently vulnerable when the adversary’s blockrate surpasses the honest blockrate; specifically, r_a > r_h, where r_a is the adversarial blockrate and r_h represents the honest blockrate. This imbalance allows the attacker to consistently create longer chains, eventually leading to consensus disruption and potentially a successful double-spend attack.
The pursuit of absolute certainty in complex systems is, invariably, a fool’s errand. This work, detailing the rigorous proof of Bitcoin protocol security under bounded network delay, exemplifies this truth. While the demonstration that honest blocks dominate the chain with probability one offers a valuable advance, it doesn’t eliminate risk - it merely shifts the focus. As Edsger W. Dijkstra observed, “It’s not enough to do your best; you must do your best better.” The protocol’s resilience isn’t found in a static guarantee, but in the continuous refinement of its defenses against evolving adversary attacks. Monitoring, in this context, isn’t about preventing failure, but about fearing consciously-acknowledging the inevitable revelation of vulnerabilities and preparing to adapt. The score growth analysis isn't a final answer, but a starting point for a more nuanced understanding of systemic fragility.
What Lies Ahead?
This demonstration of probabilistic dominance, while elegant, merely clarifies a boundary condition. Every dependency is a promise made to the past, and the assumptions regarding bounded network delay are, inevitably, a debt accruing interest. The paper illuminates a path to security, yet the forest remains largely unexplored. Consider the adversary: this analysis presupposes a rational actor. But systems, given sufficient time, attract the irrational. The true test isn’t whether an honest chain can dominate, but whether it will survive the inevitable storms of unpredictable behavior.
The focus on ‘score growth’ suggests a fascination with quantification, a desire to map the messy reality of consensus onto a neat, numerical scale. But control is an illusion that demands SLAs. The pursuit of absolute security, of a chain impervious to all attack, is a fool’s errand. Instead, attention must turn to resilience-to the capacity of the system to absorb damage and continue functioning, even in degraded form.
Everything built will one day start fixing itself. The long game isn't about preventing failure-it’s about designing for graceful degradation, for the emergence of self-healing mechanisms. This work is not an endpoint, but a seed. The next phase will not be about proving security, but about cultivating the ecosystem that ensures survivability.
Original article: https://arxiv.org/pdf/2601.09082.pdf
Contact the author: https://www.linkedin.com/in/avetisyan/
See also:
- God Of War: Sons Of Sparta – Interactive Map
- Poppy Playtime Chapter 5: Engineering Workshop Locker Keypad Code Guide
- Poppy Playtime 5: Battery Locations & Locker Code for Huggy Escape Room
- Poppy Playtime Chapter 5: Emoji Keypad Code in Conditioning
- Someone Made a SNES-Like Version of Super Mario Bros. Wonder, and You Can Play it for Free
- Why Aave is Making Waves with $1B in Tokenized Assets – You Won’t Believe This!
- Who Is the Information Broker in The Sims 4?
- One Piece Chapter 1175 Preview, Release Date, And What To Expect
- How to Unlock & Visit Town Square in Cookie Run: Kingdom
- All Kamurocho Locker Keys in Yakuza Kiwami 3
2026-01-16 00:28