Author: Denis Avetisyan
A new framework embeds security directly within the interposer layer, enabling distributed authentication for complex, multi-chip packages.
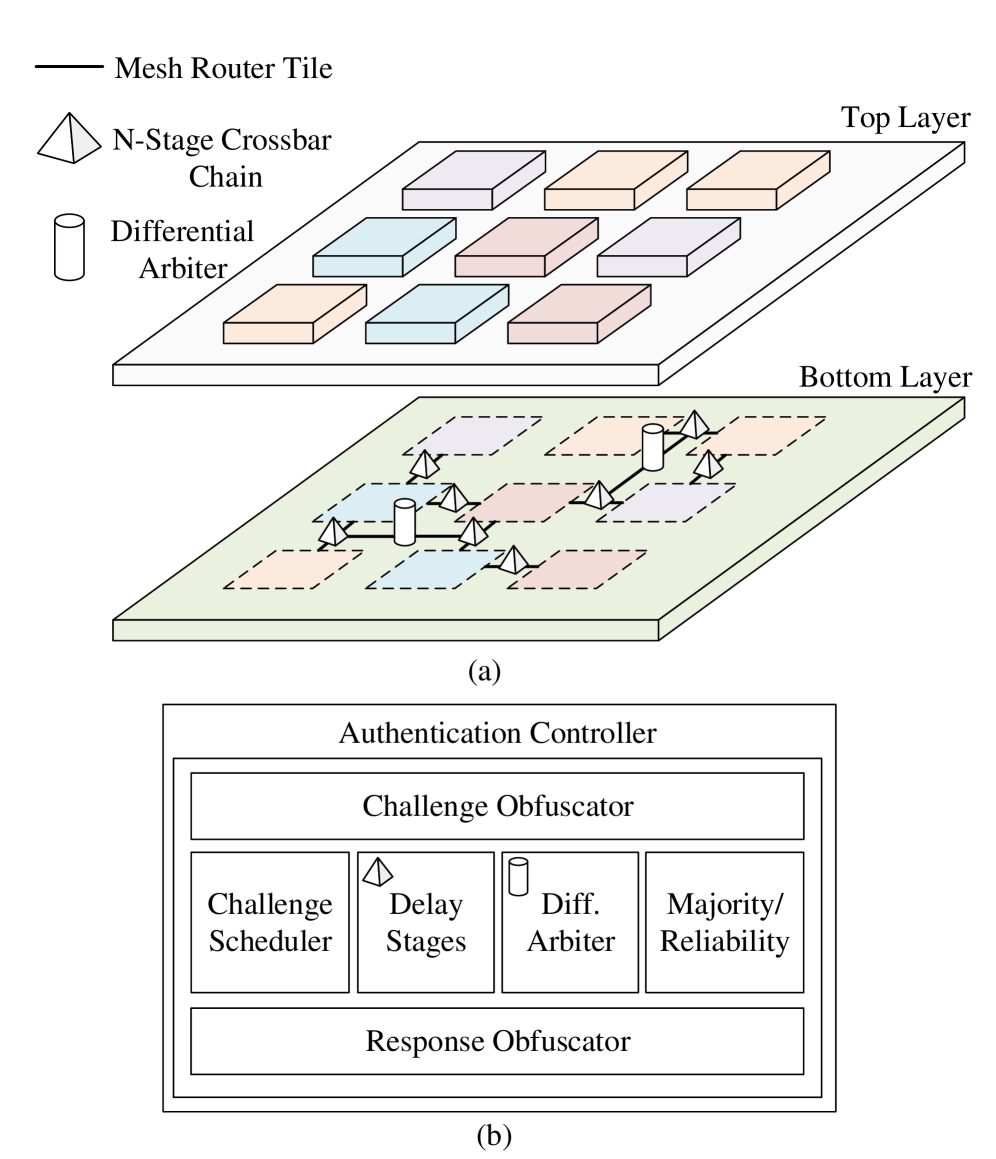
InterPUF leverages physically unclonable functions and multi-party computation to establish a root of trust without relying on centralized hardware.
The increasing flexibility of chiplet-based systems-in-package introduces critical trust challenges absent in traditional monolithic designs. This paper introduces InterPUF: Distributed Authentication via Physically Unclonable Functions and Multi-party Computation for Reconfigurable Interposers, a novel framework that embeds a distributed root of trust directly within the interposer fabric. By leveraging route-based delay PUFs and secure multi-party computation, InterPUF authenticates chiplets with minimal overhead and without reliance on a centralized anchor. Could this approach pave the way for truly decentralized and secure heterogeneous integration in future electronic systems?
Deconstructing Trust: The Vulnerabilities of Heterogeneous Integration
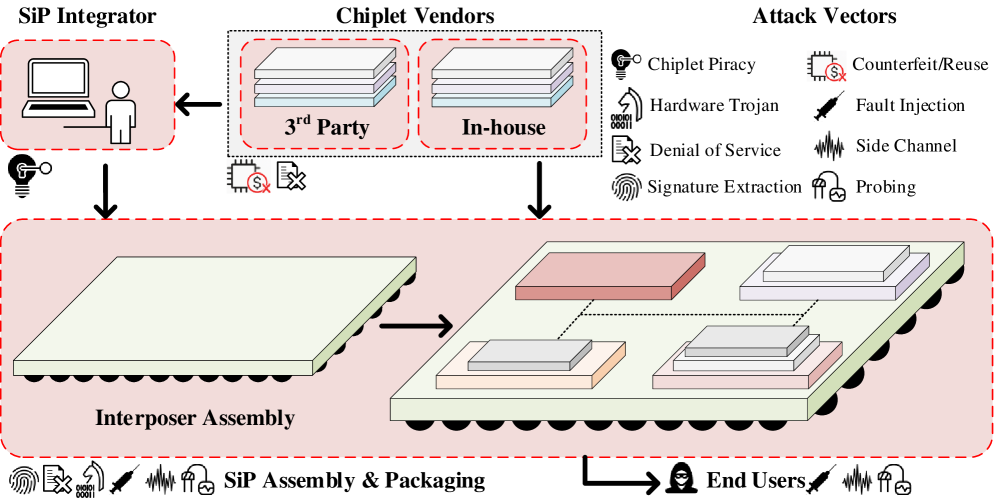
Contemporary Systems-in-Package (SiP) designs, increasingly reliant on the integration of diverse chiplets and advanced interposers to achieve performance gains, are simultaneously creating novel vulnerabilities within the semiconductor supply chain. This shift towards heterogeneous integration, while boosting computational power and reducing energy consumption, introduces a greater number of potential attack vectors. Each chiplet originates from potentially different foundries, design houses, and geographical locations, expanding the surface area susceptible to tampering, counterfeiting, or the insertion of malicious hardware. The complex interconnectivity facilitated by interposers further complicates verification and introduces challenges in ensuring the integrity of the entire system, demanding a re-evaluation of traditional security protocols and a move towards more robust, supply-chain-aware design methodologies.
Contemporary security protocols, largely developed for software-based threats, are proving increasingly ineffective against the evolving landscape of hardware attacks. Modern Systems-in-Package (SiP) and the integration of diverse chiplets introduce a significantly expanded attack surface, exceeding the capabilities of conventional defenses. Sophisticated adversaries are now capable of exploiting vulnerabilities at the physical layer – manipulating signals, extracting sensitive data through side-channel analysis, or even introducing malicious functionality directly into the hardware itself. These attacks often bypass traditional security checks, leaving designs vulnerable to counterfeiting, data theft, and functional disruption. The increasing complexity of chip design, coupled with the globalization of the semiconductor supply chain, further exacerbates these challenges, demanding a fundamental rethinking of security strategies to prioritize inherent, hardware-rooted trust.
The semiconductor industry’s reliance on Foundry-Provided Process Design Kits (PDKs) presents a growing challenge to design security and innovation. While these kits offer a cost-effective pathway for accessing complex fabrication processes, they inherently limit a designer’s control over the underlying hardware. A significant portion of the design is dictated by the foundry, potentially introducing undocumented functionalities or backdoors, and restricting the implementation of custom security features. This dependence creates a single point of failure, as vulnerabilities within the PDK itself can propagate across numerous designs. Moreover, the black-box nature of these kits hinders thorough security analysis and complicates the verification of trust, ultimately diminishing a designer’s ability to build truly secure and differentiated Systems-in-Package.
The escalating complexities of modern chip design and manufacturing demand a fundamental rethinking of system security. Traditional safeguards, often implemented at the software level or relying on post-fabrication testing, are proving inadequate against increasingly resourceful hardware attacks targeting heterogeneous systems. A shift is therefore crucial towards establishing inherent trust, embedded directly within the hardware itself. This necessitates the development of novel architectures and methodologies that establish a root of trust from the earliest stages of design and fabrication, leveraging features like physically unclonable functions, secure enclaves, and cryptographic cores integrated directly into the chiplets and interposers. Such a paradigm moves beyond detecting attacks to actively preventing them, ensuring the integrity and authenticity of the entire system and fostering resilience against supply chain compromises and malicious modifications.
Rooting Trust: Interconnect PUFs as a Decentralized Defense
Interconnect Physical Unclonable Functions (PUFs) provide a decentralized and scalable approach to authenticating individual chiplets within a System-in-Package (SiP) and establishing a comprehensive root of trust for the entire assembly. Unlike traditional security measures concentrated in a single controller, Interconnect PUFs distribute the authentication process across the interconnect fabric linking the chiplets. This distributed architecture enhances security by eliminating a single point of failure and improves scalability as additional chiplets can be integrated without requiring significant modifications to the existing security infrastructure. The resulting SiP-wide root of trust enables secure boot, key generation, and supply chain verification at the chiplet level, improving overall system security and resilience.
Interconnect Physical Unclonable Functions (PUFs) generate unique identifiers by exploiting the naturally occurring, random variations introduced during the manufacturing process of on-chip interconnects. These variations, resulting from lithography, etching, and deposition tolerances, create slight differences in interconnect lengths, widths, and resistances across individual chips. The PUF circuitry measures these physical characteristics of the interconnect routing – specifically, delays or signal strengths – and translates them into a digital signature. Because the manufacturing variations are both random and extremely difficult to control or replicate with precision, the resulting digital signature is unique to each chip and highly resistant to cloning or counterfeiting.
The Network-on-Interconnect (NoI) architecture is particularly well-suited for Physical Unclonable Function (PUF) integration due to its pervasive presence within System-on-Chip (SoC) and chiplet-based designs. By embedding PUF circuitry directly within the NoI’s routing fabric, a significantly higher proportion of the overall device area is covered compared to peripheral PUF implementations. This distributed architecture also minimizes the performance overhead associated with PUF challenges and responses, as the critical path remains largely within the existing interconnect structure rather than adding substantial latency. The inherent mesh topology of many NoI designs further facilitates scalability, enabling the creation of larger, more complex PUFs with improved security characteristics without requiring significant redesign efforts.
Interconnect Physical Unclonable Functions (PUFs) build upon existing PUF architectures, such as Arbiter and Ring Oscillator (RO) PUFs, by utilizing the inherent variations present in chip-to-chip interconnect routing. Measurements demonstrate a mean inter-chip Hamming distance of 0.4648, calculated from the differing PUF responses across multiple fabricated devices. This metric indicates a substantial level of uniqueness between individual chips, signifying a strong resistance to counterfeiting and cloning attempts, and establishing a reliable basis for hardware identification and authentication within a System-on-Package (SiP).
Fortifying the Ecosystem: InterPUF in Action
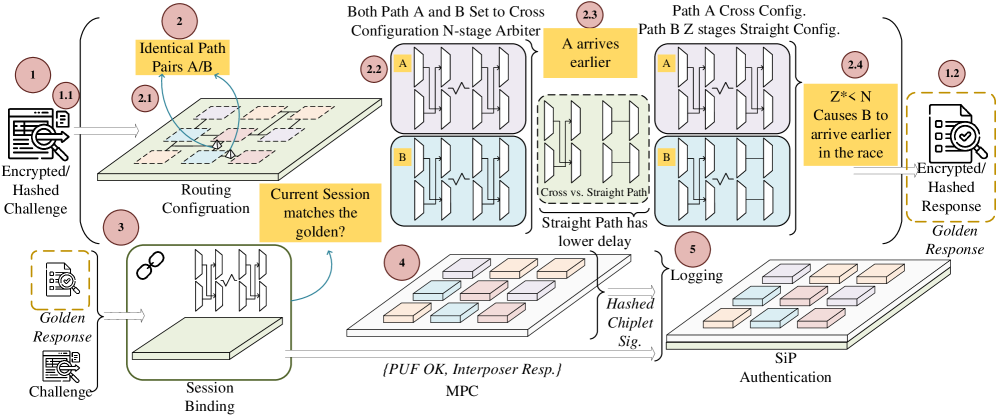
InterPUF employs Multi-Party Computation (MPC) to facilitate secure authentication and key exchange within a System-in-Package (SiP) environment. This protocol allows multiple chiplets within the SiP to jointly compute a function – in this case, verifying identity and establishing a secure key – without any single chiplet revealing its private data to the others. MPC achieves this through cryptographic techniques that distribute computation and data access, ensuring that no single point of failure compromises the overall security. Specifically, InterPUF utilizes MPC to protect the challenge-response pairs derived from the Interconnect Physical Unforgeable Function (PUF) during authentication, preventing unauthorized access and enabling secure communication between chiplets.
The Interconnect Physical Unclonable Function (PUF) serves as the foundation for generating a Golden Route Digest, a unique digital fingerprint directly tied to each chiplet’s individual characteristics. This digest is derived from the specific physical interconnects within the chiplet, creating a hardware-based identity that is extremely difficult to replicate. The PUF’s challenge-response pairs are used to create this digest, ensuring that each chiplet possesses a statistically unique identifier. This binding of identity to the hardware itself is critical for establishing trust and preventing the introduction of counterfeit or unauthorized components within the System in Package (SiP).
The InterPUF system employs SHA-256 hashing to create a Golden Route Digest, a critical component in its security architecture. This digest functions as a unique, cryptographically-secured identifier intrinsically linked to the individual chiplet. The SHA-256 algorithm ensures that any modification to the chiplet’s internal routing will result in a different digest value, effectively preventing counterfeiting by making it computationally infeasible to replicate the original digest without authorized access. Verification of the digest confirms the chiplet’s authenticity and integrity, denying access to unauthorized devices and mitigating the risk of supply chain attacks by establishing a robust root of trust.
InterPUF employs advanced Multi-Party Computation (MPC) techniques, specifically Yao Garbled Circuits and Oblivious Transfer, to safeguard the Physical Unclonable Function (PUF) challenge-response pairs during the verification process. These MPC methods prevent exposure of sensitive PUF data, enhancing security. Performance testing demonstrates a reliability of 98.2% across repeated verification queries, indicating consistent and stable operation. Furthermore, InterPUF exhibits resilience against modeling attacks, achieving an accuracy of 46.7% in preventing successful reconstruction of the PUF’s internal characteristics through such attacks.
The Hardware Imperative: Building Resilience Through Inherent Trust
Silicon Package (SiP) security benefits significantly from the implementation of Physically Unclonable Functions (PUFs), specifically InterPUF and Interconnect PUFs, which establish an inherent resistance to reverse engineering and cloning attempts. These PUFs leverage the unavoidable manufacturing variations present in silicon interconnects to create a unique ‘fingerprint’ for each device; this fingerprint serves as a cryptographic key, inextricably linked to the physical structure of the chip. Unlike software-based security measures susceptible to hacking, the physical nature of these PUFs makes replication exceptionally difficult, as precisely duplicating the random variations in silicon at a microscopic level is practically impossible. The resulting hardware-rooted security offers a robust defense against malicious actors seeking to compromise the integrity or intellectual property embedded within the SiP, protecting sensitive data and ensuring device authenticity.
Traditional cybersecurity strategies heavily depend on software-based protections, creating inherent vulnerabilities due to the malleable nature of code and its susceptibility to exploits. Shifting security primitives directly into hardware offers a fundamentally more robust defense, as these protections are physically embedded within the chip’s circuitry. This approach minimizes the attack surface by reducing reliance on potentially compromised software layers and making reverse engineering significantly more difficult and costly. The immutable nature of hardware-based security means that attacks require physical access and specialized equipment, dramatically raising the barrier to entry for malicious actors and providing a more resilient safeguard against evolving cyber threats.
The integration of hardware-based security, specifically through InterPUF and Interconnect PUFs, strategically complements Split Manufacturing (SM) techniques by obfuscating critical design details at the physical layer. This method actively shields sensitive intellectual property from reverse engineering and cloning attempts, enhancing overall system security. Importantly, this heightened protection is achieved with minimal performance impact; implementation introduces a mere 0.23% increase in silicon area and a negligible 0.072% overhead in power consumption across the entire system. This efficiency positions the approach as a practical and scalable solution for safeguarding complex, multi-chiplet architectures without significantly compromising resource utilization.
The increasing complexity of modern systems, particularly those employing multi-chiplet architectures, demands security solutions that can scale effectively without introducing prohibitive overhead. Hardware-based security primitives, like InterPUF and Interconnect PUF technologies, address this need by distributing security functionality across the system’s physical components. This decentralization mitigates the risks associated with centralized security cores, which represent single points of failure and attractive targets for attackers. Rather than relying on a single, vulnerable point of control, the inherent randomness of silicon interconnects provides a unique and unclonable identifier for each chiplet. This approach not only enhances overall system resilience but also simplifies security management in complex heterogeneous integrations, proving particularly beneficial as chiplet counts continue to rise and system designs become increasingly distributed.
The presented InterPUF system, with its distribution of trust across chiplets, embodies a fascinating exercise in controlled demolition of conventional security paradigms. It dismantles the reliance on a singular, centralized trust anchor – a vulnerability elegantly bypassed through the integration of delay-based PUFs and multi-party computation. This approach mirrors a hacker’s mindset: understanding how a system fails is paramount to building something truly resilient. As Brian Kernighan aptly stated, “Debugging is twice as hard as writing the code in the first place. Therefore, if you write the code first, debug it twice.” The InterPUF framework, in essence, debugs the conventional security model by proactively distributing the ‘debugging’ – authentication – across the system, forcing a re-evaluation of what constitutes a secure foundation.
Beyond the Interposer: Cracking the System
The InterPUF framework, by distributing trust to the interposer, performs a necessary act of deconstruction. It dismantles the conventional centralized root-of-trust model, exposing its single point of failure. However, the very success of this approach highlights a critical, and largely unaddressed, vulnerability: the inherent limitations of any physical implementation. Delay-based PUFs, while offering a degree of obfuscation, are ultimately susceptible to advanced characterization techniques and environmental manipulation. The question isn’t if they can be bypassed, but rather how much effort-and ingenuity-is required.
Future work must move beyond simply securing the chiplets themselves. The focus should shift to understanding the entire integration stack as a target for attack. This necessitates exploring techniques for dynamic key derivation, potentially leveraging post-quantum cryptographic primitives, to mitigate the risks posed by increasingly sophisticated adversaries. Moreover, a deeper investigation into the side-channel leakage from both the PUF itself and the MPC protocols is crucial. It’s not enough to hide the key; one must actively obscure the very act of computation.
Ultimately, InterPUF represents a compelling, if imperfect, step towards a more resilient heterogeneous system. The true challenge lies not in building better locks, but in accepting that any system-no matter how cleverly designed-is, at its core, a puzzle waiting to be solved. And the solving, inevitably, will begin.
Original article: https://arxiv.org/pdf/2601.11368.pdf
Contact the author: https://www.linkedin.com/in/avetisyan/
See also:
- Epic Games Store Free Games for November 6 Are Great for the Busy Holiday Season
- EUR USD PREDICTION
- Battlefield 6 Open Beta Anti-Cheat Has Weird Issue on PC
- How to Unlock & Upgrade Hobbies in Heartopia
- The Mandalorian & Grogu Hits A Worrying Star Wars Snag Ahead Of Its Release
- Sony Shuts Down PlayStation Stars Loyalty Program
- Unveiling the Eye Patch Pirate: Oda’s Big Reveal in One Piece’s Elbaf Arc!
- Someone Made a SNES-Like Version of Super Mario Bros. Wonder, and You Can Play it for Free
- ARC Raiders Player Loses 100k Worth of Items in the Worst Possible Way
- God Of War: Sons Of Sparta – Interactive Map
2026-01-20 00:43