Securing the Future: Minimal IKE Takes a Quantum Leap
A new implementation of the Minimal IKE protocol integrates post-quantum cryptography, offering a path to secure communication in a world threatened by quantum computers.
A new implementation of the Minimal IKE protocol integrates post-quantum cryptography, offering a path to secure communication in a world threatened by quantum computers.

A new analysis reveals critical vulnerabilities in nuclear power plant security stemming from the rapidly approaching era of quantum computing.
New research explores how noncommutative geometry and qq-derivatives can create a family of compact quantum spaces on the circle, challenging classical notions of distance.
![A tensor completion algorithm, leveraging alternating least squares optimization and weighted least-squares solutions derived from matricized tensor representations, effectively decomposes incomplete data to estimate direction-of-arrival (DOA) angles via factorization of the data into component matrices-specifically, extracting angular information directly from the elements of the estimated factor matrix [latex]\hat{\mathbf{H}}[/latex] to recover automatically paired 2D DOA estimates.](https://arxiv.org/html/2602.21146v1/59.4.png)
Researchers have developed a novel method for accurately pinpointing sound sources even when sensors in the array are damaged or malfunctioning.
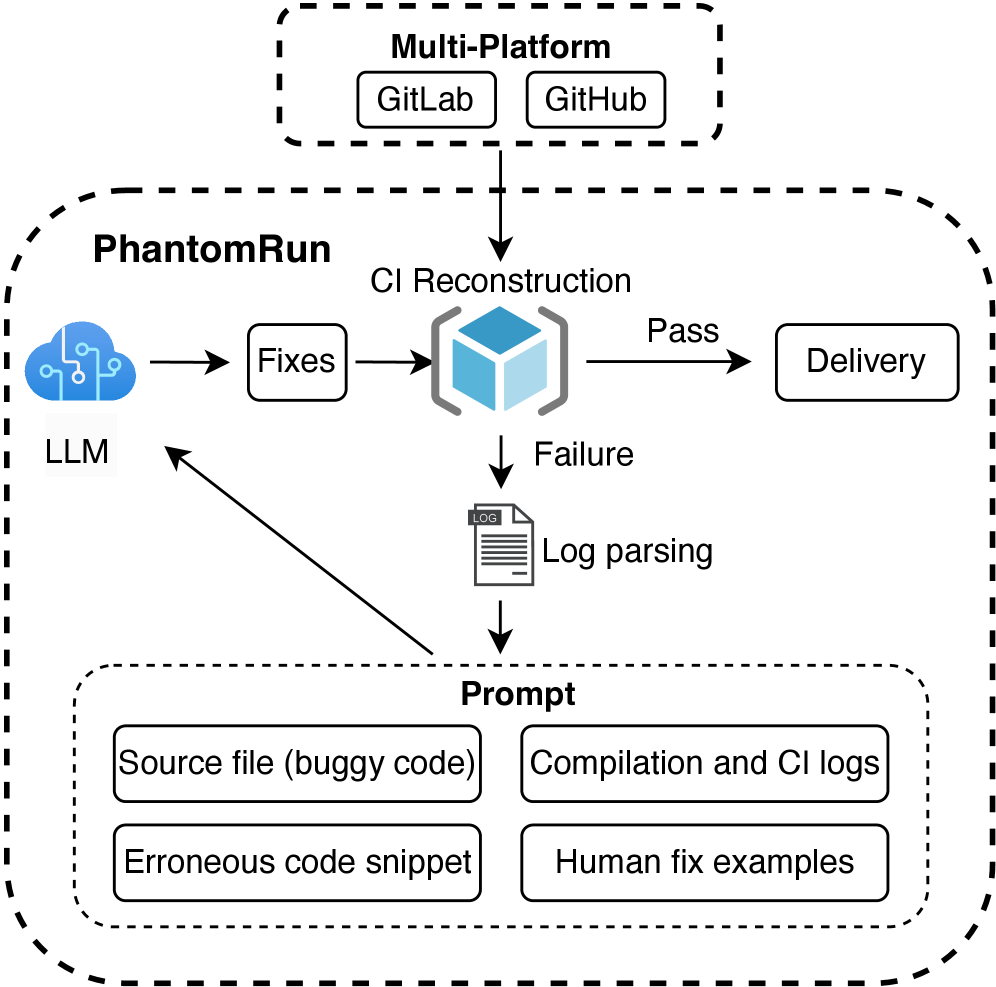
Researchers have developed a system that uses the power of artificial intelligence to automatically repair compilation errors in the complex world of embedded system development.

A new quantization technique dynamically adjusts model precision token-by-token, offering significant speedups and efficiency gains for large language models.
New research illuminates the intricate relationship between quantum wreath products and $p$-adic general linear groups, offering a powerful framework for understanding their representations.
![The study explores interactions involving a virtual tachyon φ, detailing how its exchange with fermions generates a long-range oscillating potential that disrupts Lorentz invariance, its capacity to mix with the Higgs boson, and the resulting mixed quartic interaction [latex]\phi^{2}h^{2}[/latex].](https://arxiv.org/html/2602.20474v1/x2.png)
A new analysis rigorously demonstrates the impossibility of building a consistent quantum field theory incorporating virtual particles that travel faster than light.
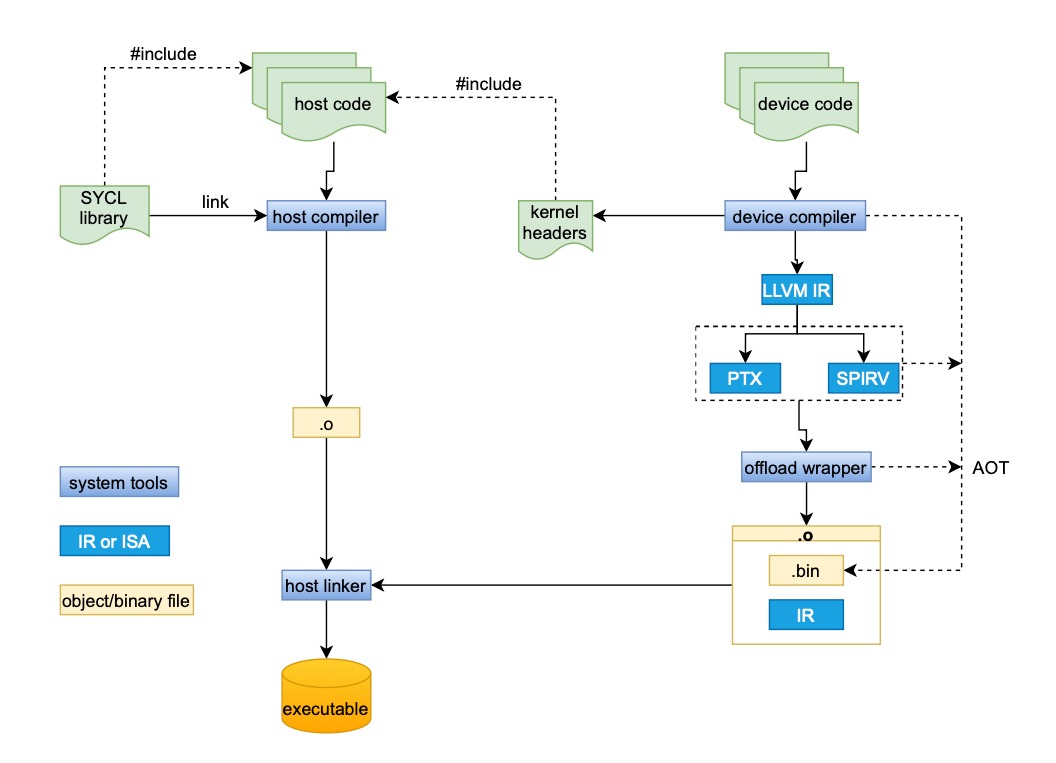
This review examines the latest innovations in SYCL compiler implementations and their impact on performance and portability across diverse hardware platforms.
Researchers have developed improved methods for reconstructing polynomials represented by complex arithmetic circuits, offering potential benefits for circuit verification and lower bound proofs.