Decoding High-Degree Polynomials: New Algorithms for Circuit Verification
Researchers have developed improved methods for reconstructing polynomials represented by complex arithmetic circuits, offering potential benefits for circuit verification and lower bound proofs.
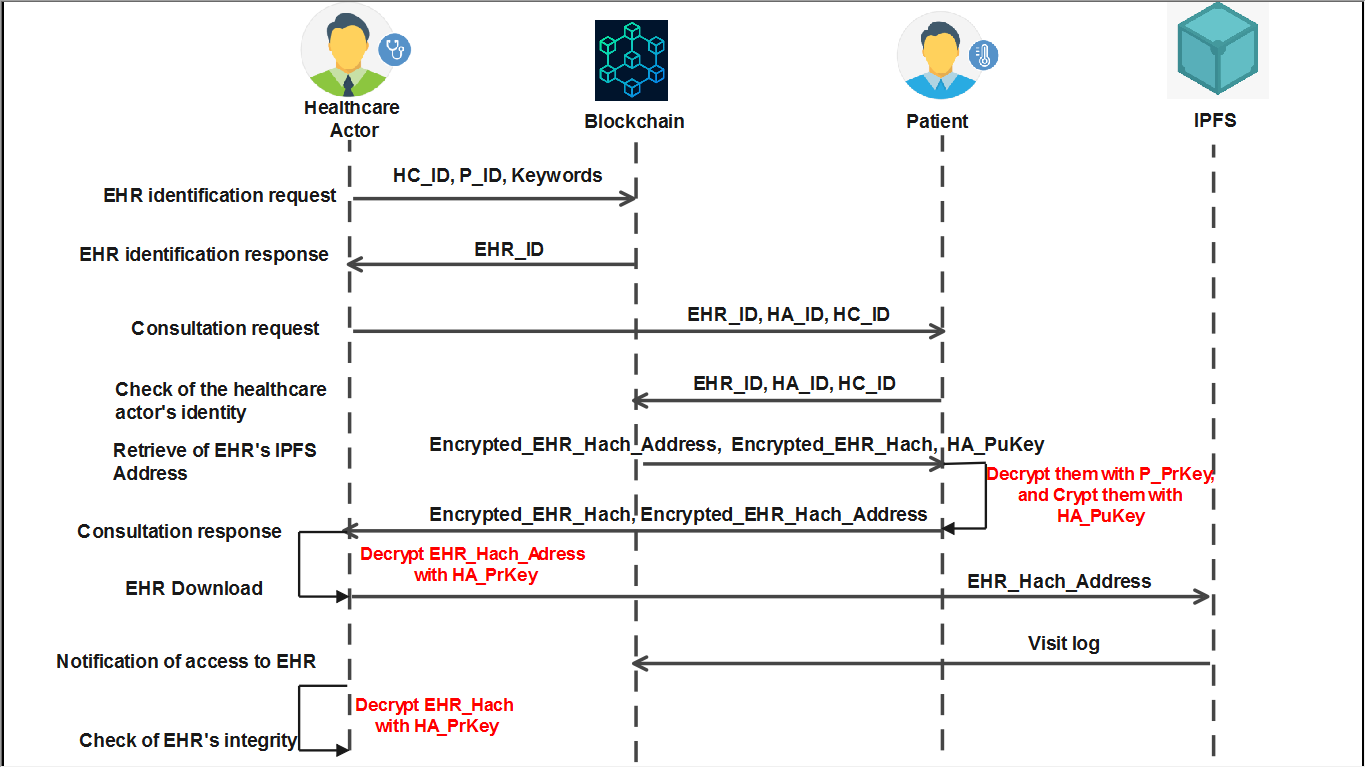
![Spatial-keyword queries, encompassing both range and [latex]22NN[/latex] approaches, demonstrate versatile application across diverse scenarios, highlighting the adaptability of these methods in information retrieval systems.](https://arxiv.org/html/2602.20952v1/x1.png)
![The study demonstrates that a de Bruijn graph, constructed from a string set-specifically [latex]I=\{X=ACTAGATCCGTTGGCAACTA, ACTAC, CTAGG, TAGAC, AGATA, GATCT, ATCCC, TCCGG, CCGTA, CGTTA, GTTGT, TTGGA, TGGCG, GGCAT, GCAAA, CAACG, AACTT\} [/latex] with [latex] fork=4 [/latex], [latex] k=4 [/latex], and [latex] n=|\Sigma|^{k-2}=4^{2}=16 [/latex]-can yield a concise, closed necklace representation requiring 32 symbols and 32 parentheses (64 characters total), or alternatively, an Euler tig solution generating 80 plaintext characters, highlighting a fundamental tension between representational efficiency and direct textual output.](https://arxiv.org/html/2602.19408v1/x2.png)
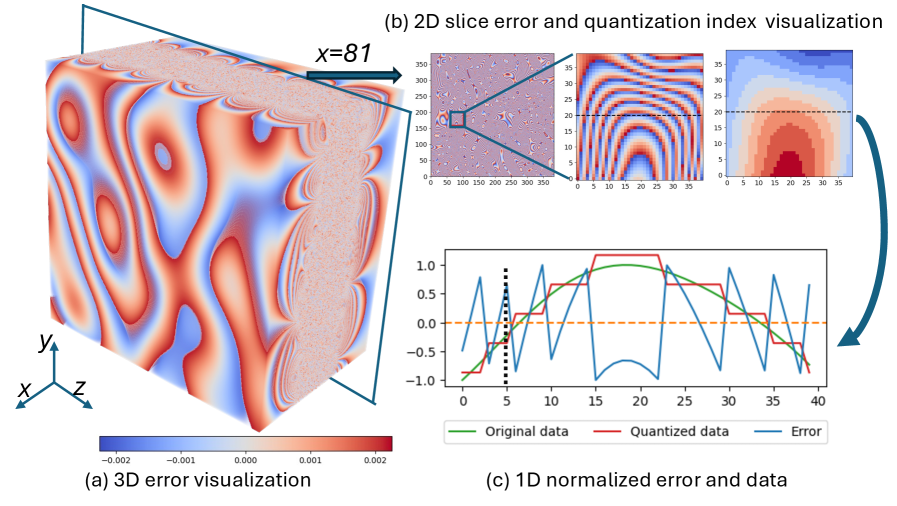
![This research demonstrates that a refined time-driven learning control (rTLC) strategy-evaluated with a time step of [latex]\Delta t = 0.85[/latex] and a discrete time step of [latex]dt = 0.1[/latex]-offers a compelling performance profile in terms of speed, control, and safety, distinguishing itself from traditional time-driven and event-driven learning control approaches.](https://arxiv.org/html/2602.20076v1/x1.png)