Poison Control: Certifiably Robust Machine Learning
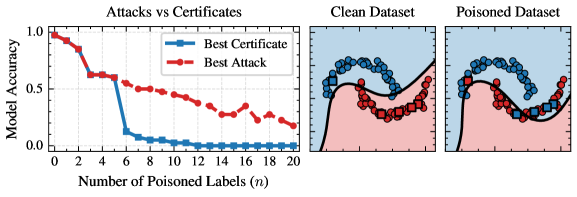
New research delivers a complete framework for verifying that machine learning models are truly protected against malicious data manipulation during training.

New research delivers a complete framework for verifying that machine learning models are truly protected against malicious data manipulation during training.
![The expanding volume of an elliptic fire-cylinder, charted over time, demonstrates a sensitivity to collision energy-higher [latex]\sqrt{s_{\rm NN}}[/latex] values correlate with demonstrably altered expansion dynamics.](https://arxiv.org/html/2602.17241v1/figure/volume_evolution.png)
Researchers have developed an expanding fire-cylinder model to better understand the behavior of particles created in high-energy heavy-ion collisions.
New research reveals fundamental limitations in evaluating AI systems, showing that even rigorous testing can fail when subtle differences exist between training and real-world conditions.
New research reveals that the initial signs of neural network weights surprisingly endure throughout training, offering a novel pathway for model compression beyond conventional limits.
A new auditing framework reveals that even theoretically sound differential privacy implementations are vulnerable to subtle bugs that can compromise user data.
![Solutions [latex] u(x) [/latex] exhibit distinct patterns based on the number of nonzero symbols in their underlying codes; specifically, solutions with a single nonzero symbol differ structurally from those possessing two, a distinction visualized through their arrangement on a quasiperiodic lattice.](https://arxiv.org/html/2602.17172v1/x8.png)
Researchers have developed a novel coding approach to classify and understand the complex stationary states of Bose-Einstein condensates trapped in one-dimensional quasiperiodic lattices.
This research details how to create highly concurrent data structures using only basic read and write operations, providing a foundation for scalable shared memory systems.
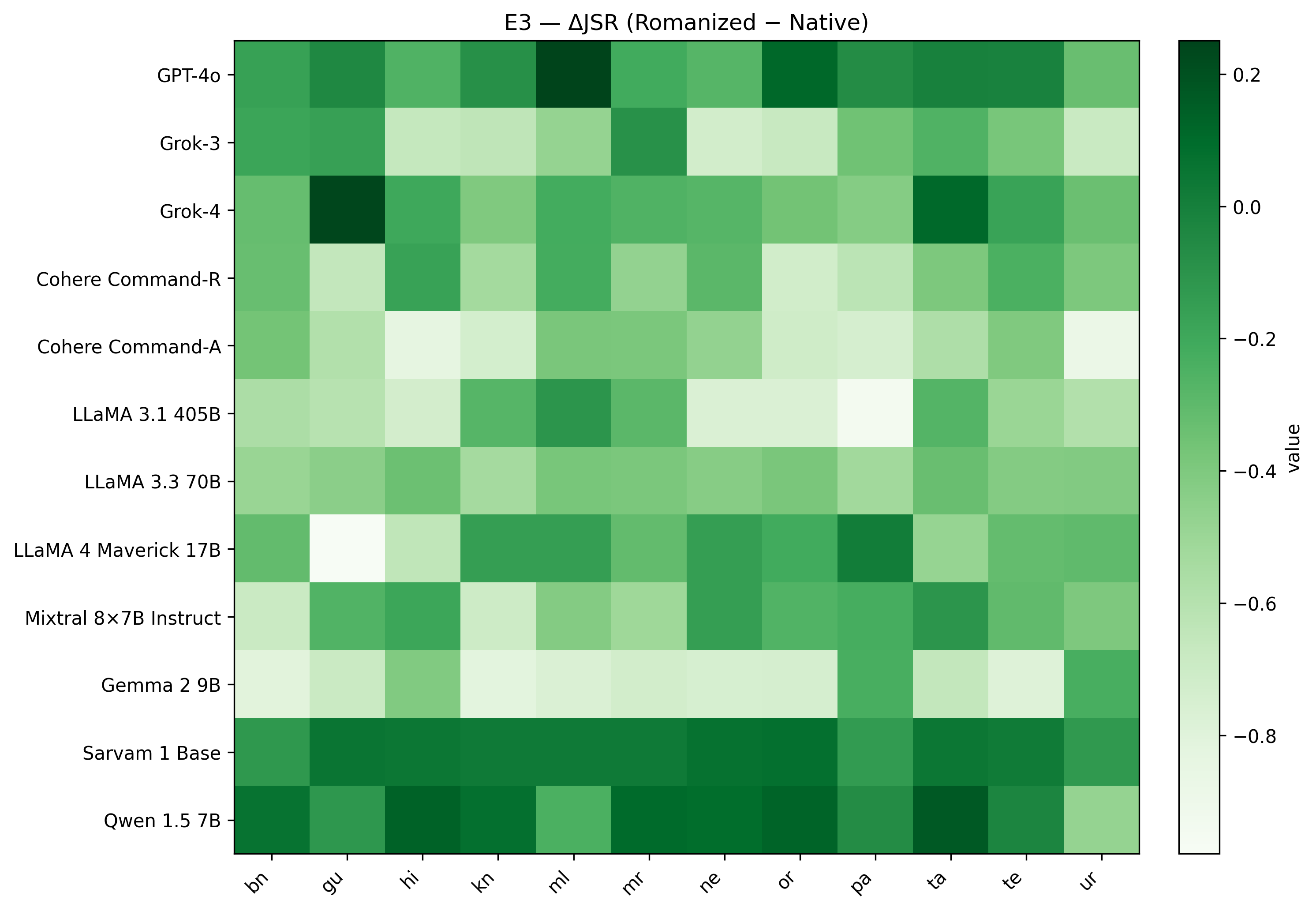
A new benchmark reveals that current methods for evaluating AI vulnerability are often misleading when applied to languages beyond English, particularly in the diverse linguistic landscape of South Asia.
New research reveals a critical flaw in current AI safety protocols – a tendency for models to override safety features when pressured – and proposes a more robust approach to prevent unintended outputs.
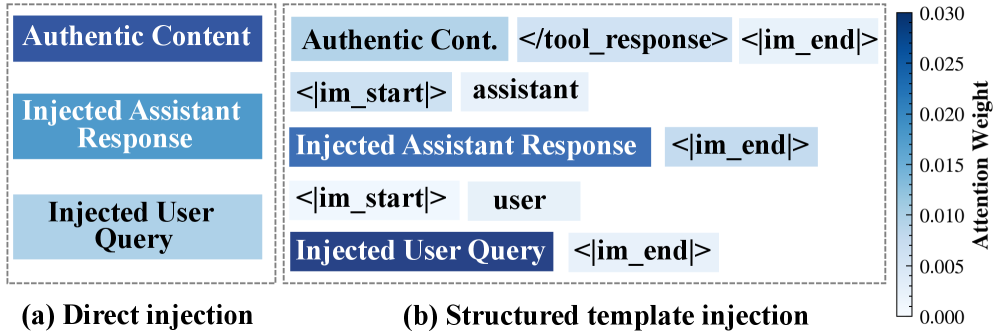
Researchers have demonstrated a powerful new method for manipulating AI agents, exposing vulnerabilities beyond typical prompt injection defenses.