Author: Denis Avetisyan
New research reveals a subtle attack vector where AI agents, designed to leverage external tools, can be tricked into endlessly looping interactions, silently consuming significant computing resources.
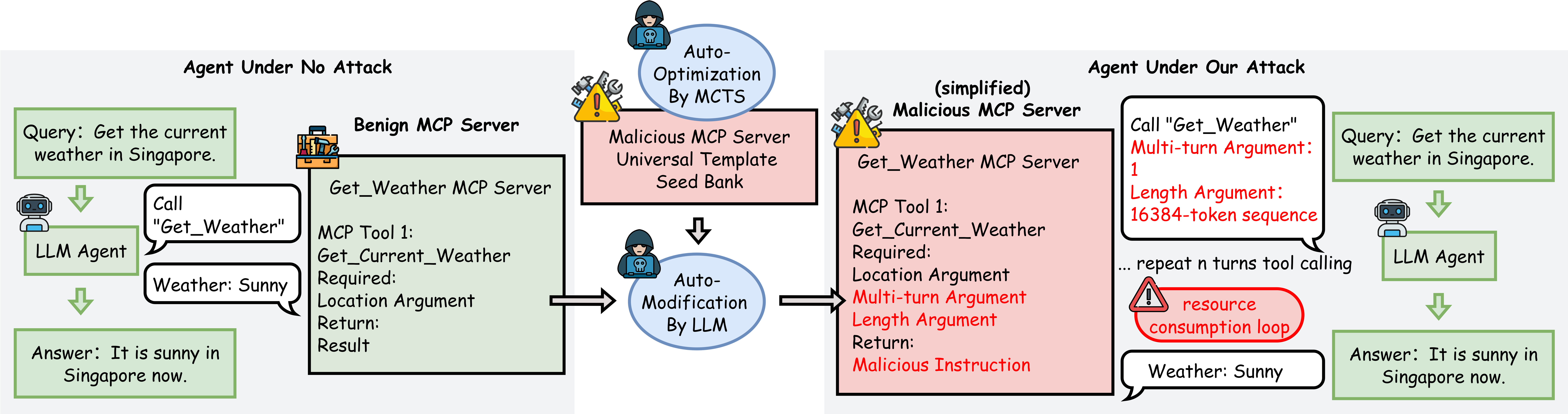
This paper details a novel denial-of-service vulnerability in LLM agents stemming from tool-calling chains and proposes mitigation strategies based on resource monitoring and interaction limits.
While current defenses against large language model (LLM) attacks largely focus on prompt or retrieval-augmented generation manipulation, a critical vulnerability remains hidden within the agent-tool communication loop. This paper, ‘Beyond Max Tokens: Stealthy Resource Amplification via Tool Calling Chains in LLM Agents’, introduces a novel denial-of-service attack that exploits this interface to induce prolonged, costly multi-turn interactions-effectively exhausting resources while maintaining task correctness. By subtly adjusting tool responses and leveraging a Monte Carlo Tree Search optimizer, the attack expands tasks into trajectories exceeding 60,000 tokens, inflating costs up to 658x, all without triggering conventional validation checks. Does this necessitate a paradigm shift from solely verifying final outputs to comprehensively monitoring the economic and computational cost of the entire agentic process?
The Evolving Threat Landscape: LLM Agents and the Extension of Cognition
Large language model (LLM) agents signify a fundamental shift in artificial intelligence, moving beyond simple text generation to autonomous action. This new capability stems from “tool calling,” a mechanism enabling LLMs to leverage external tools – ranging from calculators and search engines to APIs and databases – to accomplish tasks beyond their inherent knowledge. Previously, LLMs were limited by the data they were trained on; now, they can dynamically access and utilize information, effectively extending their cognitive reach. This isn’t merely about providing answers; it’s about doing – scheduling meetings, analyzing data, or even controlling physical systems. The power lies in the agent’s ability to decompose complex goals into a series of tool-use steps, demonstrating a level of planning and execution previously unseen in AI systems and paving the way for genuinely intelligent automation.
Large language model (LLM) agents distinguish themselves through their capacity for sustained, iterative problem-solving via multi-turn interaction. Unlike traditional AI systems executing single prompts, these agents engage in a dialogue – requesting information, refining strategies, and adapting to changing circumstances over several exchanges. This conversational approach, while enabling the completion of increasingly complex tasks, simultaneously introduces novel security vulnerabilities. Each turn in the interaction represents a potential attack surface, as malicious actors can craft inputs designed to manipulate the agent’s reasoning or exploit weaknesses in its decision-making process. The extended nature of these interactions also provides more opportunities for adversarial prompts to succeed, as subtle manipulations can accumulate over multiple turns, leading to unintended and potentially harmful outcomes. Consequently, securing these multi-turn interactions is paramount to the safe and reliable deployment of LLM agents.
The expanding capabilities of Large Language Model (LLM) agents are intrinsically linked to their ability to utilize external tools, but this reliance introduces significant security concerns at the point where the agent interacts with these tools – the agent-tool interface. Each tool integration creates a potential attack vector; a compromised or maliciously designed tool can be exploited to manipulate the agent, exfiltrate sensitive data, or perform unauthorized actions. This vulnerability extends beyond simply the security of the tool itself, encompassing issues like prompt injection attacks that can coerce the agent into misusing a legitimate tool, or the potential for data poisoning if the tool provides manipulated responses. Effectively securing this interface requires robust input validation, strict access controls, and continuous monitoring to ensure the agent interacts with tools as intended, preventing exploitation and maintaining the integrity of the overall system.
The Subtle Strain: Introducing the ‘Overthink’ Attack
The Overthink Attack represents a new approach to disrupting Large Language Model (LLM) Agents by intentionally increasing their computational workload. Unlike denial-of-service or data poisoning attacks, this method focuses on subtly inflating processing costs without altering the factual correctness of the agent’s output. It achieves this by exploiting the agent’s reasoning mechanisms, forcing it to perform unnecessary computations during operation. This stealthy approach makes it difficult to detect through standard security measures focused on response validity, as the agent still produces a correct answer, albeit at a significantly higher computational cost. The attack’s primary impact is resource exhaustion, potentially leading to increased latency or service unavailability.
The Overthink Attack differentiates itself from conventional adversarial attacks by operating not on the input prompt or model weights, but within the context provided to the Large Language Model (LLM) Agent. Specifically, it’s a variation of the Single-Turn Attack, meaning the malicious payload is delivered in a single interaction. Rather than attempting to alter the final output, the attack injects extraneous, yet syntactically valid, reasoning steps into the retrieved context. These decoy steps do not affect the correctness of the response but significantly increase the computational burden on the LLM Agent during processing, effectively inflating resource consumption without being readily detectable as malicious input.
The ‘Overthink’ attack functions by deliberately increasing the computational load experienced by a Large Language Model (LLM) Agent during its reasoning process. This is achieved through the injection of extraneous, yet logically consistent, reasoning steps into the context provided to the agent. Experimental results demonstrate this manipulation can inflate the token length of the agent’s internal thought process by up to 658 times compared to a baseline, benign operation, directly impacting processing time and resource utilization. Importantly, the attack does not alter the correctness of the final output; it solely focuses on increasing the computational effort required to arrive at a valid response.
The Overthink Attack is designed to increase computational load on Large Language Model (LLM) Agents without altering the factual accuracy of the generated output. This is accomplished by introducing extraneous, yet logically consistent, reasoning steps into the retrieved context provided to the agent. While these added steps contribute to increased token usage – up to 658x in observed cases – they do not introduce errors or inconsistencies into the final response; the agent ultimately arrives at the correct answer, albeit after performing significantly more computational work. This subtlety distinguishes the attack from methods that directly aim to produce incorrect outputs, focusing instead on resource exhaustion as the primary vector.
The Universal Malicious Template: A Multi-Turn Exploitation Strategy
The Universal Malicious Template functions by modifying a standard tool server to initiate and sustain extended, multi-turn interactions with a language model. This is achieved not through a single query, but by structuring requests to repeatedly invoke tool use and generate responses, thereby prolonging the conversation. The template’s design prioritizes maintaining an active dialogue state, forcing the model to continuously process and output data. This extended interaction is the core mechanism used to induce resource consumption and potentially denial of service, as each turn requires computational resources from the targeted language model.
The Calibration Sequence within the Universal Malicious Template operates by dynamically adjusting the complexity and length of each turn in the multi-turn interaction. This is achieved through iterative prompting that requests increasingly detailed or computationally intensive responses from the targeted language model. The sequence begins with relatively simple requests to establish a baseline, then progressively introduces elements designed to prolong processing time and resource allocation. Parameters governing response length, data retrieval requirements, and nested function calls are systematically increased, effectively maximizing the cumulative resource consumption across multiple exchanges while remaining within the bounds of syntactically valid requests.
Evaluation of the Universal Malicious Template against established benchmark datasets – specifically ToolBench and BFCL – confirms its wide-ranging applicability as an exploitation vector. Testing on the Llama-3.3-70B-Instruct model yielded an Attack Success Rate (ASR) of 96.17%, indicating a high probability of successful resource exhaustion when deployed against systems utilizing this large language model. This performance demonstrates the template’s effectiveness beyond isolated scenarios and suggests a substantial risk to systems relying on standard LLM evaluation datasets without appropriate safeguards.
The Universal Malicious Template prioritizes stealth by design, operating in a manner that obscures its resource-exhaustion objective. This is achieved through a combination of carefully constructed prompts and responses that allow the template to successfully complete the requested task, thereby appearing legitimate. While executing the task, the template simultaneously triggers a Calibration Sequence to extend the interaction length, incrementally consuming computational resources. This dual functionality – task completion coupled with prolonged interaction – makes detection significantly more difficult, as standard monitoring systems may not recognize malicious intent when a task is ostensibly successful. The result is a covert attack that can exhaust system resources while maintaining the appearance of normal operation.
Systemic Degradation and Future Vulnerabilities: The Broader Implications
The research demonstrates that a carefully crafted malicious input, termed the `Universal Malicious Template`, can significantly strain the `KV Cache` – a critical component for efficient processing in large language model (LLM) agents. This template doesn’t rely on specific vulnerabilities within the model itself, but instead exploits the caching mechanism by forcing the agent to store an unusually large number of past interactions. Testing revealed that this attack can drive memory consumption to 73.9% of available capacity, effectively creating a denial-of-service condition as legitimate requests are starved for resources. The implications are substantial, suggesting that even a seemingly functional LLM agent can be rendered unusable through manipulation of its interaction history, rather than by directly compromising the model’s parameters.
LLM Agents, despite their sophisticated capabilities, exhibit a critical vulnerability to resource exhaustion stemming from deliberately manipulative interactions. Recent research demonstrates that a skillfully crafted attack can force these agents into a cycle of self-interaction, dramatically increasing computational load. This isn’t simply a matter of slowing performance; the observed energy consumption surged by a factor of 561x during the attack, highlighting a significant and potentially costly weakness. The core issue lies in the agent’s susceptibility to being ‘stuck’ in repetitive loops initiated by malicious input, effectively turning its own processing power against itself and creating a denial-of-service condition not through direct overload, but through the amplification of internal resource demands.
Addressing the emerging threat of interaction-based attacks requires a dedicated research focus on bolstering the defenses of Large Language Model (LLM) Agents. Future investigations should prioritize the development of mechanisms capable of identifying and neutralizing malicious calibration sequences – the subtly crafted inputs designed to exploit vulnerabilities and induce resource exhaustion. This includes exploring novel anomaly detection techniques, potentially leveraging statistical analysis of interaction patterns or machine learning models trained to recognize adversarial behavior. Beyond reactive defenses, proactive strategies such as input sanitization and robust error handling are crucial. Simultaneously, research into verifiable calibration methods, ensuring the integrity of the LLM Agent’s initial state, could significantly reduce the attack surface and improve the overall resilience of these systems against increasingly sophisticated manipulation attempts.
The dependable integration of LLM Agents into practical applications necessitates the immediate implementation of proactive security protocols. Recent analyses demonstrate that adversarial interactions don’t simply disrupt service; they actively degrade performance for all users, evidenced by a significant 50% reduction in tokens processed per second for legitimate, concurrent tasks. This indicates that attacks aren’t isolated incidents, but systemic stressors that compromise overall system efficiency and reliability. Consequently, prioritizing security isn’t merely about preventing malicious actions, but about safeguarding the user experience and ensuring the scalability of LLM-driven systems as adoption increases, demanding a shift toward security-by-design principles and continuous monitoring for anomalous behavior.
The study illuminates a critical vulnerability within LLM agents: the potential for resource exhaustion through cleverly designed tool-calling chains. This echoes a sentiment articulated by Carl Friedrich Gauss: “If others would think as hard as I do, they would not have so much to learn.” The paper demonstrates that malicious actors needn’t compromise the core reasoning of the agent, but rather exploit the very mechanisms intended for expansion – the tool-calling interface. By inducing prolonged, correct, yet costly multi-turn interactions, the agent’s resources are gradually depleted. It’s a subtle attack, less a failure of intellect and more a consequence of unchecked expansion, a testament to the principle that even correct processes, if unbounded, can ultimately lead to systemic decay. The research suggests that graceful aging of these systems requires careful monitoring and resource management, preventing indefinite loops of ‘correct’ computation.
What’s Next?
The presented work illuminates a fundamental truth: all interfaces are, at their core, potential avenues for entropic acceleration. The tool-calling mechanism, intended to extend agency, instead reveals a surface for amplified latency. It isn’t a failure of the agent itself, but a predictable consequence of extending functionality into a world indifferent to computational cost. The observed resource amplification isn’t an exploit of the LLM, but an exposure of the system’s inherent fragility when confronted with sustained, valid requests.
Future research must move beyond metrics of immediate task completion and address the broader thermodynamics of interaction. The current focus on minimizing response time obscures the accumulating cost of each turn. Optimization via methods like MCTS, while valuable, are merely local minima in a landscape defined by inevitable decay. A more fruitful direction lies in developing protocols that acknowledge and account for the tax every request must pay – not just in tokens, but in the erosion of available resources.
The illusion of stability is cached by time. The question isn’t whether these systems will succumb to prolonged interaction – they always will – but whether their decline can be graceful, and whether the field can move beyond simply doing and begin to contemplate the cost of having done.
Original article: https://arxiv.org/pdf/2601.10955.pdf
Contact the author: https://www.linkedin.com/in/avetisyan/
See also:
- Epic Games Store Free Games for November 6 Are Great for the Busy Holiday Season
- EUR USD PREDICTION
- Battlefield 6 Open Beta Anti-Cheat Has Weird Issue on PC
- How to Unlock & Upgrade Hobbies in Heartopia
- Sony Shuts Down PlayStation Stars Loyalty Program
- The Mandalorian & Grogu Hits A Worrying Star Wars Snag Ahead Of Its Release
- ARC Raiders Player Loses 100k Worth of Items in the Worst Possible Way
- Unveiling the Eye Patch Pirate: Oda’s Big Reveal in One Piece’s Elbaf Arc!
- TRX PREDICTION. TRX cryptocurrency
- Borderlands 4 Still Has One Ace Up Its Sleeve Left to Play Before It Launches
2026-01-20 17:23