Author: Denis Avetisyan
A new analysis reveals the economic limits of bribery in blockchain alerting systems and introduces practical protocols to maximize security.
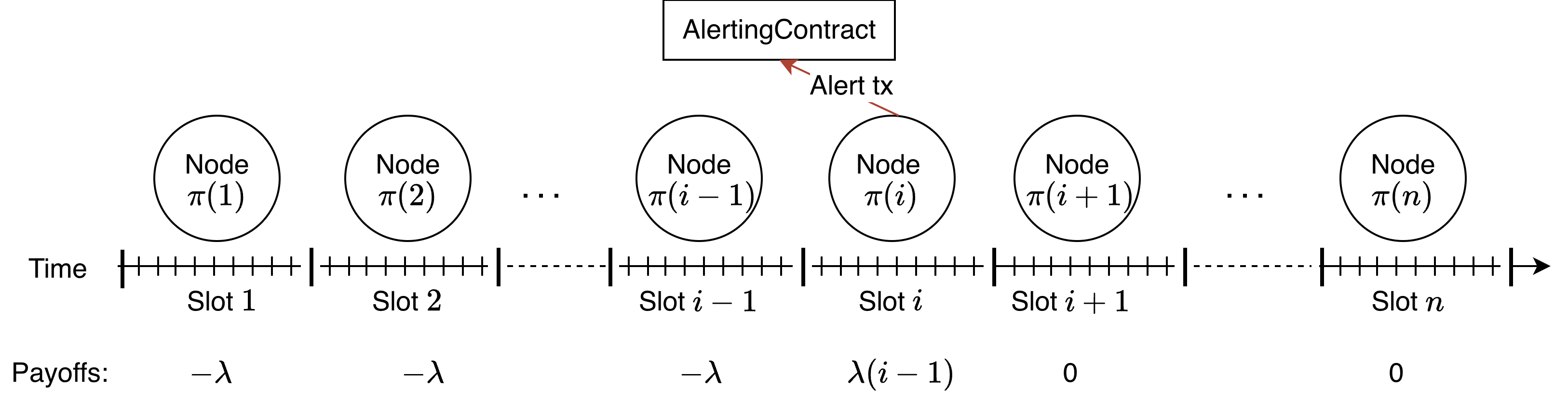
This review establishes a quadratic upper bound on bribery resistance and details three protocols – Lockstep, TEE-based, and Sequential – that approach this bound using game theory and cryptoeconomic incentives.
While smart contracts secure trillions of dollars in on-chain value, their reliance on external alerts introduces a critical vulnerability: bribery-based suppression of information. This paper, ‘Resilient Alerting Protocols for Blockchains’, analyzes this ‘alerting problem’ through a cryptoeconomic lens, establishing a O(n^2) upper bound on optimal bribery resistance. We then present three distinct protocols – Lockstep, TEE-based, and Sequential – each approaching this bound with differing tradeoffs in on-chain storage, execution time, and network assumptions. Given the growing complexity of decentralized applications, how can we best engineer robust and economically-sound alerting mechanisms to safeguard the integrity of blockchain systems?
The Nervous System of Modern Infrastructure: Alerting in a Connected World
The seamless operation of modern infrastructure, from financial networks to automated supply chains and increasingly, smart contracts, hinges on the swift and reliable delivery of alerts. These signals function as the nervous system of complex systems, notifying operators and automated processes of critical events – a sudden surge in demand, a potential security breach, or a failing component. Without timely and accurate alerts, systems risk cascading failures, financial losses, or compromised security. Consider smart contracts, self-executing agreements on blockchains; they require constant monitoring for unexpected behavior or vulnerabilities, necessitating a robust alerting mechanism to trigger interventions before irreversible damage occurs. The increasing complexity of these interconnected systems amplifies this reliance, making dependable alerts not merely a convenience, but a foundational requirement for continued functionality and trust.
The very systems designed to safeguard modern infrastructure face a significant paradox: their alerts, crucial for identifying and responding to threats, are susceptible to deliberate manipulation. A malicious actor, termed the ‘Adversary’, can actively work to suppress or distort these critical signals, effectively blinding the system to impending danger. This isn’t simply a matter of technical failure; it’s a targeted attack on the information pipeline itself. By compromising the alerting mechanisms, the Adversary can create a false sense of security, allowing vulnerabilities to persist undetected and potentially enabling catastrophic consequences within the interconnected network – be it financial systems, energy grids, or the complex logic of a blockchain system. This highlights the necessity for proactive defenses against signal suppression, rather than relying solely on reactive measures after an alert has already been compromised.
Designing dependable alerting systems within decentralized blockchain environments presents a unique integrity challenge. Traditional centralized systems are susceptible to single points of failure and bribery, but replicating this model on a blockchain doesn’t automatically ensure trustworthiness. The very mechanisms enabling decentralization – economic incentives and open participation – can be exploited by a malicious actor seeking to suppress critical alerts. Successfully mitigating this requires innovative approaches that align the incentives of all participants, making it economically irrational to conceal or manipulate warning signals. This isn’t simply about technical safeguards; it demands a careful consideration of game theory and economic modeling to ensure the alerting system remains robust against corruption, even when substantial financial rewards are offered for silence or misinformation. Achieving this level of resilience is paramount for the continued secure operation of smart contracts and the broader blockchain ecosystem.
Strategic Interactions: A Game-Theoretic Framework for Alerting
Game theory provides a framework for modeling the strategic interactions between rational actors within an alerting system. Specifically, it allows analysis of the incentives faced by ‘Rational Nodes’ – components designed to detect and report threats – and the ‘Adversary’ – an entity attempting to compromise system integrity by suppressing or manipulating alerts. This analysis assumes both actors are rational, meaning they will act in a manner to maximize their own utility, whether that is accurately reporting threats or successfully avoiding detection. By defining the potential payoffs for each actor based on various alerting actions – raising a true positive, raising a false positive, suppressing an alert, or failing to detect a threat – we can predict the likely behavior of both the Rational Nodes and the Adversary, and design systems to encourage desired outcomes. The core principle is that each actor’s decision is not made in isolation, but in anticipation of the other’s response, leading to a strategic equilibrium.
The interaction between a rational node and an adversary regarding alert generation can be modeled using game theory, specifically through extensions of established game models. The Stackelberg Game, where one player moves first and the other responds, is applicable when considering a node strategically raising alerts to deter adversarial action. Conversely, the Simultaneous Alerting Game, where both node and adversary act concurrently, reflects scenarios where the adversary simultaneously attempts to suppress alerts while the node generates them. Adapting these models to the alerting context requires defining payoff functions that represent the costs and benefits to each player – including the node’s cost of raising alerts and the adversary’s cost of suppression – allowing for analysis of optimal strategies and equilibrium outcomes. These models allow for the quantitative analysis of strategic interactions, moving beyond simplistic assumptions about rational actors and providing a framework for predicting behavior.
Traditional alerting systems often rely on fixed thresholds and simple anomaly detection, offering limited resistance to manipulation. A game-theoretic approach reframes security as a cost-benefit analysis for an adversary attempting to suppress alerts. The resulting ‘Bribery Resistance’ isn’t an inherent property but a configurable function of system design choices; specifically, it’s determined by factors like the number of independent data sources contributing to an alert, the complexity of the alerting logic, and the diversity of detection methods. Increasing these factors raises the cost – in resources, effort, or risk of detection – required to successfully suppress a legitimate alert, effectively strengthening the system’s defense against malicious interference. Therefore, a higher Bribery Resistance is achieved through deliberate architectural decisions that increase the adversary’s operational costs.
Architecting Resilience: Protocol Designs for Enhanced Bribery Resistance
Alerting protocols designed to detect and respond to malicious activity exhibit varying levels of bribery resistance, necessitating trade-offs between security, scalability, and resource utilization. Protocols such as Lockstep Alerting prioritize simplicity but depend on a strong synchrony assumption which can limit performance in distributed environments. The TEE-Based Alerting Protocol utilizes timed commitment schemes to enhance security, introducing computational overhead associated with trusted execution environments. Conversely, Sequential Alerting Protocols minimize on-chain storage requirements, potentially at the expense of increased communication complexity or latency. These protocols are not mutually exclusive, and their effectiveness is contingent upon specific deployment parameters and threat models; no single protocol offers optimal resistance without some compromise.
The Lockstep Alerting Protocol operates by requiring all participants to confirm the validity of an alert within a predetermined, synchronized timeframe – the ‘Synchrony Assumption’. This approach simplifies alert verification and reduces the computational burden on individual nodes. However, this reliance on strict temporal coordination introduces scalability limitations; the protocol’s performance is directly affected by network latency and the number of participating nodes. Specifically, a large number of nodes, or significant network delays, can make it increasingly difficult to satisfy the Synchrony Assumption, potentially leading to protocol failures or requiring substantial communication overhead to maintain synchronization. This contrasts with protocols that utilize asynchronous mechanisms or rely less on precise timing, offering greater resilience to network conditions and scalability to larger networks.
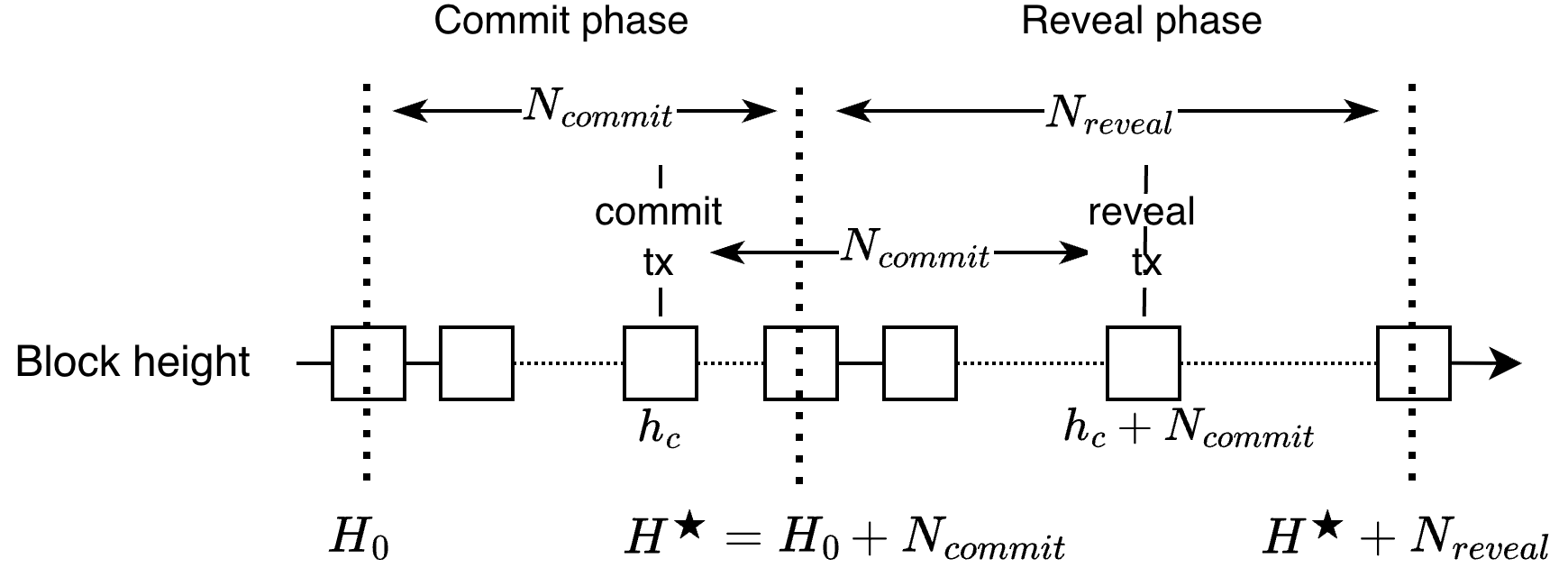
The TEE-Based Alerting Protocol utilizes Timed Commitment Schemes to establish secure commitments regarding alert data, effectively binding alerters to their submissions without revealing them prematurely. These schemes allow for a commitment to be made at a specific future time, preventing manipulation after commitment. Conversely, the Sequential Alerting Protocol minimizes on-chain storage requirements by processing alerts in a serial fashion; each alert is validated and processed before the next is submitted. This approach limits the need to store multiple alert candidates simultaneously, reducing storage to O(1) but potentially increasing latency compared to parallel processing methods.
Analysis within this paper demonstrates that the examined alerting protocols – Lockstep, TEE-Based, and Sequential – achieve a maximum bribery resistance approaching an upper bound of O(n^2), where ‘n’ represents the number of participants. This represents a quantifiable improvement in security compared to previously analyzed protocols, though it also establishes a practical limit on achievable resistance through these design approaches. The established O(n^2) complexity indicates that the computational cost of successfully bribing the system scales quadratically with the number of participants, effectively increasing the difficulty and expense of malicious manipulation as the network grows. This finding provides a baseline for evaluating the security of future alerting protocol designs and informs practical considerations for deployment in large-scale systems.
The Lockstep and Trusted Execution Environment (TEE)-based alerting protocols are designed to achieve constant-time execution, but this performance relies on the validity of their underlying assumptions – specifically, a strong synchrony assumption for Lockstep and a secure TEE for the TEE-based protocol. In contrast, the Sequential alerting protocol prioritizes minimizing on-chain storage requirements, achieving a storage complexity of O(1) by processing alerts sequentially and discarding data after verification; however, this approach trades off constant-time execution for reduced storage overhead. These differing design choices demonstrate a fundamental trade-off between computational complexity and storage efficiency in bribery-resistant protocol design.

Towards Provably Secure Alerting: A Foundation for Trustworthy Systems
Alerting systems, vital for the reliable operation of smart contracts and decentralized applications, face constant threats from malicious actors seeking to suppress critical notifications. Maximizing ‘Quadratic Bribery Resistance’ is therefore paramount; this concept quantifies a system’s ability to withstand attacks where adversaries attempt to bribe stakeholders into withholding or misreporting information. Unlike traditional linear bribery models, quadratic resistance accounts for the escalating cost of influencing a larger number of stakeholders, making large-scale manipulation prohibitively expensive. A system with high quadratic bribery resistance isn’t simply harder to corrupt, but exhibits a cost structure that inherently discourages coordinated attacks, ensuring that genuine alerts are far more likely to propagate and trigger appropriate responses, even under duress. This focus on game-theoretic security properties represents a significant advancement over reactive security measures and forms a crucial foundation for building truly robust and trustworthy decentralized systems.
Recent research delineates a definitive limit to the bribery resistance achievable in alerting systems, establishing an upper bound of O(n2), where ‘n’ represents the number of potential attackers. This finding is significant because it moves the field beyond speculative security assessments and provides a concrete benchmark against which new and existing alerting mechanisms can be rigorously evaluated. Previously, assessing resistance relied on ad-hoc analysis; now, protocols can be demonstrably proven to approach – or fall short of – this theoretical maximum. Consequently, developers gain a quantifiable metric for improving security, and users receive increased assurance regarding the reliability of decentralized applications that depend on these alerting systems, fostering greater trust in the underlying technology.
The resilience of smart contracts and decentralized applications hinges directly on the robustness of their alerting systems; a heightened level of bribery resistance within these systems demonstrably amplifies overall security and reliability. When an alerting mechanism can withstand attempts to manipulate its reporting – to suppress genuine issues or falsely flag benign events – the application avoids potentially catastrophic consequences such as unauthorized fund withdrawals or incorrect state transitions. This resistance isn’t merely about preventing nuisance alerts, but about ensuring the integrity of the entire system, fostering trust among users, and safeguarding assets. Consequently, improvements in bribery resistance translate into a more dependable and trustworthy foundation for decentralized technologies, encouraging broader adoption and innovation within the space.
Alerting systems, vital for the reliable operation of smart contracts and decentralized applications, have traditionally relied on reactive, ad-hoc security measures. However, a shift towards proactive, mathematically grounded security is now achievable through rigorous protocol design and game-theoretic analysis. This approach moves beyond simply responding to attacks by anticipating malicious behavior and building inherent resistance. By formally modeling the incentives of potential attackers – their potential ‘payoffs’ for manipulating the system – researchers can identify vulnerabilities and construct protocols where rational actors are disincentivized from acting maliciously. This isn’t merely about patching flaws; it’s about establishing provable security guarantees – demonstrating, with mathematical certainty, the system’s resilience against specific attack vectors and establishing a new standard for trust in decentralized technologies.
Enhanced security within decentralized technologies is not merely a technical refinement, but a foundational requirement for broader acceptance and practical implementation. As smart contracts and decentralized applications increasingly manage valuable assets and critical infrastructure, the potential for malicious attacks necessitates robust and demonstrably trustworthy systems. Improved security protocols directly address user anxieties surrounding vulnerabilities and potential financial losses, fostering confidence in these emerging technologies. This increased trust, in turn, encourages greater participation and investment, accelerating the development and deployment of decentralized solutions across diverse sectors – from finance and supply chain management to healthcare and governance. Ultimately, a demonstrably secure foundation is paramount for unlocking the full potential of decentralized technologies and realizing their transformative impact on a global scale.
The pursuit of robust blockchain security, as detailed in this exploration of alert suppression, inherently demands a focus on systemic simplicity. The protocols – Lockstep, TEE-based, and Sequential – each represent attempts to navigate the complex interplay between incentive mechanisms and potential bribery attacks, striving for efficiency without sacrificing resilience. This echoes Robert Tarjan’s observation: “If a design feels clever, it’s probably fragile.” A truly effective system, particularly one governing a decentralized network, cannot rely on intricate, easily exploited logic; instead, it must prioritize a clear, understandable structure that minimizes potential attack vectors and approaches the established quadratic upper bound on bribery resistance. The elegance lies in minimizing complexity, maximizing predictability.
What Lies Ahead?
The established quadratic bound on bribery resistance, while theoretically satisfying, serves as a stark reminder that security is not about absolute thresholds, but about raising the cost of attack beyond practical reach. These protocols – Lockstep, TEE-based, and Sequential – each represent a point in a design space, trading assumptions about trust and computational resources. The true challenge isn’t merely achieving resistance, but understanding which trade-offs are viable within complex, evolving blockchain ecosystems.
Future work must address the inherent fragility of any system built on incentive structures. The analysis presented here assumes rational actors; deviations from this, whether malicious or simply irrational, represent significant vulnerabilities. Exploring the interplay between formal verification of smart contract code and game-theoretic guarantees remains a crucial, largely unexplored area. Scaling these protocols beyond isolated alerts also presents a substantial hurdle – an alert network is only as strong as its weakest link, and maintaining a robust, decentralized monitoring infrastructure will require innovative approaches to data aggregation and validation.
Ultimately, the pursuit of resilient alerting is a search for elegant simplicity. The most effective solutions will likely be those that minimize the number of moving parts, and rely on fundamental cryptographic and economic principles. It is not about building more complex defenses, but about designing systems where the cost of subversion naturally exceeds any potential gain – a principle that applies as much to blockchain security as it does to the stability of any living organism.
Original article: https://arxiv.org/pdf/2602.10892.pdf
Contact the author: https://www.linkedin.com/in/avetisyan/
See also:
- EUR USD PREDICTION
- Epic Games Store Free Games for November 6 Are Great for the Busy Holiday Season
- How to Unlock & Upgrade Hobbies in Heartopia
- Battlefield 6 Open Beta Anti-Cheat Has Weird Issue on PC
- Sony Shuts Down PlayStation Stars Loyalty Program
- The Mandalorian & Grogu Hits A Worrying Star Wars Snag Ahead Of Its Release
- ARC Raiders Player Loses 100k Worth of Items in the Worst Possible Way
- Unveiling the Eye Patch Pirate: Oda’s Big Reveal in One Piece’s Elbaf Arc!
- TRX PREDICTION. TRX cryptocurrency
- Prime Gaming Free Games for August 2025 Revealed
2026-02-13 02:06