Author: Denis Avetisyan
A new hardware defense, SPOILER-GUARD, combats side-channel vulnerabilities by introducing uncertainty into how memory access dependencies are predicted.

SPOILER-GUARD mitigates the SPOILER side-channel attack through randomized dependency prediction in the Load-Store Queue with minimal performance impact.
Modern processors, while leveraging speculative execution for performance gains, remain vulnerable to side-channel attacks that exploit transient execution. This paper introduces ‘SPOILER-GUARD: Gating Latency Effects of Memory Accesses through Randomized Dependency Prediction’, a hardware defense designed to mitigate the SPOILER attack by disrupting latency amplification caused by partial address aliasing. SPOILER-GUARD achieves this through dynamic randomization of physical address bits used in load-store dependency resolution, demonstrably reducing misspeculation to minimal levels with negligible performance and hardware overhead-less than 70 ps latency, 0.064 mm² area, and 5.863 mW power. Can this approach to obfuscating memory access patterns be extended to defend against other emerging microarchitectural attacks?
The Illusion of Speed: Speculative Execution and its Shadows
Modern processors achieve significant performance gains through a technique called speculative execution, where the processor predicts which instructions will likely be needed and executes them ahead of time. This preemptive approach, while boosting speed, introduces inherent vulnerabilities because these predictions aren’t always correct. When a misprediction – termed ‘misspeculation’ – occurs, the processor must discard the results of the incorrectly executed instructions. However, the transient effects of this speculative work – subtle changes in cache states or branch prediction history – can be observed by attackers. These side-channel leaks, though seemingly minor, can reveal sensitive information, such as cryptographic keys or user data, effectively turning a performance optimization into a significant security risk. The core issue isn’t simply about incorrect results, but about the observable traces left behind by the process of correction.
Modern processors, in their pursuit of speed, often predict future operations – a technique known as speculative execution. However, when these predictions are incorrect – a state called misspeculation – the processor doesn’t simply discard the partially completed work. Instead, subtle changes to the processor’s internal state, known as microarchitectural side effects, remain. Attacks like Spectre and Meltdown cleverly leverage these residual effects to infer sensitive information. By carefully observing changes in cache timings or branch prediction behavior, attackers can deduce data that should have remained inaccessible, effectively turning the processor’s optimization against itself. This isn’t a flaw in implementation, but a fundamental consequence of the design choice to prioritize performance, highlighting a critical need for security considerations at the very core of processor architecture.
The emergence of attacks like Spectre and Meltdown signifies a fundamental shift in computer security paradigms. Historically, processor design prioritized performance gains, often with security considerations addressed as afterthoughts or patches. These vulnerabilities, however, reveal that optimizing solely for speed creates inherent risks; speculative execution, while boosting performance, introduces avenues for data leakage through observable microarchitectural effects. Consequently, a proactive, security-centric approach is now essential, demanding that security features be integrated directly into the processor’s architectural design – not merely added on top. This necessitates a re-evaluation of how processors are conceived, built, and secured, acknowledging that performance and security are inextricably linked and must be co-designed for truly robust systems.
Unveiling the Attack Surface: Dependency Confusion
The `SPOILER` attack functions by exploiting false dependencies introduced during memory access operations. Specifically, it targets scenarios where a processor speculatively accesses memory locations that are partially aliased – meaning they share some, but not all, address bits. This speculative access, even if ultimately faulted, can leave transient traces in the cache hierarchy that reveal information about the physical address of the accessed data. By carefully crafting memory access patterns and observing these cache-based side channels, an attacker can deduce physical address bits without legitimate authorization, effectively bypassing traditional memory protection mechanisms. The attack doesn’t require successful memory access; the attempt at access is sufficient to leak information.
The `SPOILER` attack distinguishes itself from many side-channel attacks by removing the dependency on branch prediction mechanisms. Traditional attacks, such as those exploiting branch prediction, create observable patterns tied to conditional execution; these patterns are then analyzed to leak information. `SPOILER`, however, operates by manipulating memory access patterns directly, revealing physical address information through partially aliased accesses, irrespective of branch outcomes. This independence from branch prediction significantly complicates detection and mitigation strategies, as common defenses targeting branch prediction-based attacks are ineffective against `SPOILER`. Consequently, defenses must focus on memory access control and data layout randomization to disrupt the attack’s ability to reveal address information.
The effectiveness of the `SPOILER` attack can be amplified through the utilization of existing memory attack techniques. Specifically, `Prime+Probe` can be employed to reliably create the necessary false sharing conditions between victim and attacker memory locations, facilitating the observation of physical address information. Furthermore, `Rowhammer`-style attacks, which induce bit flips in adjacent memory rows, can be leveraged to bypass certain mitigations or to enhance the reliability of the false sharing setup, thereby broadening the scenarios in which `SPOILER` can be successfully executed and increasing its potential impact on system security.
Mitigating the Risk: Defending Against Dependency Confusion
Current mitigation strategies against dependency confusion attacks, such as Numbered Data Access (NDA) and Speculative Store Bypass Disable (SSBD), function by either preventing or sanitizing potentially unsafe speculative loads. NDA assigns unique identifiers to memory locations, enabling the processor to verify access permissions during speculative execution. SSBD disables speculative loads that might bypass store instructions, preventing the processor from reading data before it has been fully written. While effective in preventing exploitation, both techniques introduce performance overhead. NDA requires additional tracking and verification logic, while SSBD restricts speculative execution, potentially reducing instruction-level parallelism and overall throughput. The degree of performance impact varies depending on the specific implementation and workload characteristics.
SPOILER-ALERT mitigates dependency confusion by detecting load-store aliasing during runtime. This is achieved through the implementation of a cuckoo filter within the Store Buffer. The cuckoo filter tracks recently stored addresses; when a load instruction is encountered, the filter is checked to determine if the load address overlaps with a recently stored address. A match indicates potential aliasing, triggering a stall or other mitigation to prevent speculative execution from proceeding with potentially incorrect data. This runtime detection allows SPOILER-ALERT to address dependency confusion without requiring recompilation or static analysis, but introduces latency based on the filter lookup performance.
SPOILER-GUARD employs a proactive defense against dependency confusion by introducing randomization and tagging during dependency resolution. This technique obfuscates the predictable patterns attackers exploit in speculative execution, effectively reducing the rate of misspeculation to 0.0004%. Unlike reactive mitigation strategies that attempt to block or sanitize unsafe loads after they occur, SPOILER-GUARD aims to prevent misspeculation from happening in the first place by increasing the complexity for attackers to accurately predict memory dependencies. This approach significantly minimizes the attack surface and offers a substantial improvement in security with minimal performance impact.

Validating the Defense: Simulation and Performance Analysis
gem5 is a modular platform used for computer architecture research, enabling detailed modeling of processor components and execution of workloads. This simulation capability was essential for evaluating SPOILER-GUARD, allowing researchers to systematically vary parameters such as cache size, branch predictor configuration, and workload characteristics. By simulating a wide range of conditions, gem5 facilitated the identification of performance bottlenecks and the optimization of SPOILER-GUARD’s implementation before hardware prototyping. The platform supports various instruction set architectures and allows for the analysis of metrics including execution time, power consumption, and resource utilization, providing a comprehensive assessment of the defense mechanism’s impact on system performance.
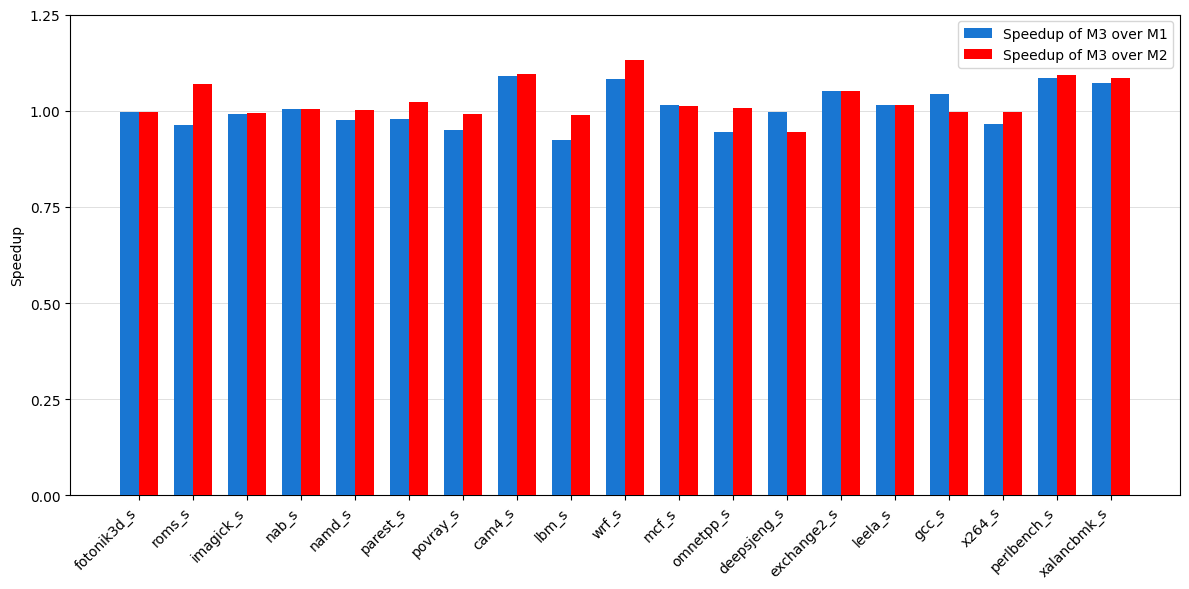
Performance evaluation of the defense mechanism utilized the Standard Performance Evaluation Corporation (SPEC) CPU2017 benchmark suite to establish a realistic baseline and quantify any performance overhead. Results indicate that implementation of the defense yielded performance improvements of 2.12% for integer workloads and 2.87% for floating-point workloads when compared to the baseline, demonstrating a net positive impact on performance despite the added security measures. These gains were achieved through optimizations focused on minimizing the impact of the defense on critical path operations during benchmark execution.
Analysis of SPOILER-GUARD’s impact on the Load-Store Queue and Dependence Predictor demonstrates a latency increase of 69 picoseconds. Implementation of this defense introduces an area overhead of 0.064 mm², which represents less than 0.8% of the 8.73 mm² area occupied by a Skylake processor core. These measurements indicate a minimal performance and resource footprint for the proposed defense mechanism, suggesting a viable implementation within existing architectural constraints.

Charting the Course: The Future of Secure Speculation
The efficacy of SPOILER-GUARD hinges on unpredictability, making a robust random number source critical; therefore, a true Random Number Generator is considered paramount for optimal security. However, practical implementation often necessitates compromise, and research indicates that even the computationally efficient Mersenne Twister algorithm can offer a viable, though less resilient, alternative. While a true RNG introduces entropy from a physical source, bolstering defense against sophisticated attacks, Mersenne Twister provides a pseudo-random sequence that, while predictable in theory, presents a substantial barrier to exploitation in a carefully designed system. This trade-off allows for broader applicability of SPOILER-GUARD across various hardware platforms, balancing security with performance and implementation complexity.
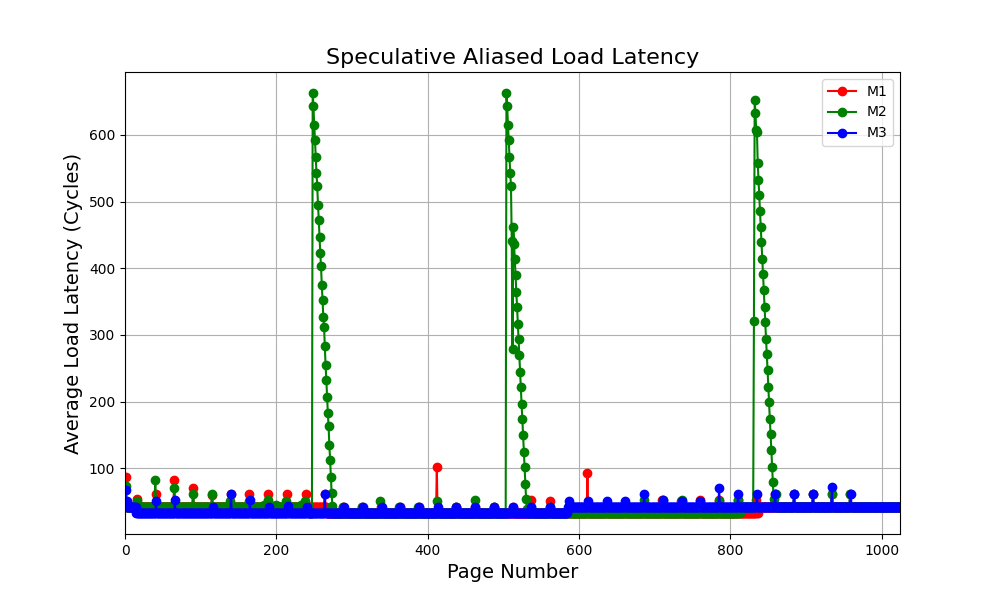
Advancing computer security demands a synergistic approach, integrating hardware-level protections with refined software mitigations, as demonstrated by the development of SPOILER-GUARD. This system showcases a significant reduction in speculative execution-induced vulnerabilities; on M3 processors, it limits SPOILER violations to a mere 14, a dramatic improvement from the 255,941 observed on M2 processors. Crucially, SPOILER-GUARD doesn’t simply address the number of violations, but also minimizes the performance impact-reducing attacker-induced processor stalls to just one. Such results highlight the potential of layered defenses, suggesting future research should prioritize the coordinated evolution of both hardware and software security features to build more resilient computing architectures.
Maintaining the integrity of contemporary computing systems necessitates a proactive approach to security, acknowledging the inherent limitations of current defenses and anticipating novel attack vectors. Recent research demonstrates that bolstering systems – specifically those utilizing SkyLake Core architectures – doesn’t necessarily demand substantial resource investment; the proposed security enhancements exhibit a minimal area overhead of only 0.2% when compared to a 32 KB L1 data cache. Furthermore, power consumption remains remarkably low, registering at just 5.863 mW. This efficiency suggests that robust security measures can be integrated without significantly impacting performance or increasing the cost of modern processors, paving the way for more resilient and trustworthy computing experiences.
The pursuit of microarchitectural security, as demonstrated by SPOILER-GUARD, often necessitates a delicate balance between complexity and efficacy. If the system looks clever, it’s probably fragile. This defense, mitigating the SPOILER side-channel attack through randomized dependency prediction, exemplifies this principle. It addresses partial address aliasing within the Load-Store Queue – a subtle, yet critical aspect of memory access – without incurring substantial performance penalties. The design implicitly acknowledges that structure dictates behavior; by obfuscating dependency information, it alters the attacker’s ability to exploit speculative execution. Linus Torvalds once stated, “Talk is cheap. Show me the code.” SPOILER-GUARD delivers on that demand, presenting a tangible, code-level solution to a complex security challenge.
The Horizon Beckons
SPOILER-GUARD represents a localized refinement within a fundamentally complex system. The mitigation of partial address aliasing, while valuable, does not dissolve the underlying tension between performance and security. Any attempt to ‘fix’ a microarchitectural vulnerability invariably shifts the problem – creating new surfaces for attack, or exacerbating existing constraints elsewhere in the memory hierarchy. The architecture’s behavior over time will reveal these emergent properties.
Future work must move beyond reactive defenses. The pursuit of truly robust security necessitates a deeper understanding of the information leakage inherent in speculative execution. Dependency prediction, a cornerstone of modern processors, is inherently probabilistic – and therefore, a source of side-channel information. The challenge lies not simply in obscuring the signals, but in designing systems where the absence of predictable dependency information isn’t a vulnerability in itself.
Ultimately, the field must confront the fact that performance gains and security are not orthogonal concerns. They are coupled, and optimizing for one will always introduce trade-offs in the other. The true measure of progress will not be the elimination of individual attacks, but the creation of architectures that gracefully accommodate – and even anticipate – the inevitable emergence of new threats.
Original article: https://arxiv.org/pdf/2601.21211.pdf
Contact the author: https://www.linkedin.com/in/avetisyan/
See also:
- Poppy Playtime Chapter 5: Engineering Workshop Locker Keypad Code Guide
- Jujutsu Kaisen Modulo Chapter 23 Preview: Yuji And Maru End Cursed Spirits
- God Of War: Sons Of Sparta – Interactive Map
- 8 One Piece Characters Who Deserved Better Endings
- Mewgenics Tink Guide (All Upgrades and Rewards)
- Who Is the Information Broker in The Sims 4?
- Pressure Hand Locker Code in Poppy Playtime: Chapter 5
- Top 8 UFC 5 Perks Every Fighter Should Use
- Sega Declares $200 Million Write-Off
- Full Mewgenics Soundtrack (Complete Songs List)
2026-01-31 00:57