Author: Denis Avetisyan
The rise of QUIC’s connection migration is forcing a rethink of how network middleboxes handle stateful connections.
This paper presents QASM, a novel framework for enabling QUIC-aware stateful middleboxes to accurately track connections during migration, preserving functionality like firewalls, rate limiting, and NAT.
While stateful middleboxes are critical for network security and service delivery, the emergence of HTTP/3 and the QUIC protocol presents a significant challenge to their traditional operation. This paper introduces ‘QASM: A Novel Framework for QUIC-Aware Stateful Middleboxes’, a novel approach designed to address the disruptions caused by QUIC’s encryption and, crucially, connection migration. QASM enables reliable tracking of QUIC connections-even as endpoints change IP addresses or port numbers-preserving essential middlebox functionality with minimal performance overhead. Will this framework prove essential for maintaining network manageability and security in an increasingly QUIC-dominated internet?
Deconstructing TCP: The Rise of HTTP/3 and QUIC
The modern web, characterized by rich media, dynamic content, and an expectation of instant access, relentlessly challenges the capabilities of foundational technologies like TCP. Originally designed for a simpler internet, TCP struggles with issues such as head-of-line blocking – where a single lost packet can stall an entire stream of data – and slow connection establishment times. Consequently, delivering a seamless user experience now necessitates protocols capable of minimizing latency and maximizing throughput. This demand has fueled exploration into alternatives that prioritize speed, reliability, and security, pushing the boundaries of network communication and driving the development of innovative solutions to overcome the limitations of established infrastructure. The need for enhanced performance isn’t merely about convenience; it’s critical for supporting increasingly complex web applications and ensuring equitable access to online resources.
The evolution of web performance has led to the development of HTTP/3, a protocol designed to overcome longstanding limitations within TCP connections. Traditional TCP, while reliable, suffers from head-of-line blocking – where a single lost packet can stall the delivery of all subsequent data. HTTP/3 circumvents this issue by utilizing the QUIC transport protocol, fundamentally changing how data is transmitted. QUIC operates on top of UDP, allowing for multiplexed, independent streams of data within a single connection. This means that if one packet is lost, only that specific stream is affected, leaving others to continue unimpeded. Furthermore, QUIC incorporates advanced error correction and security features, reducing latency and enhancing the overall user experience by delivering web content more efficiently and reliably.
The QUIC protocol represents a significant departure from traditional internet communication by building directly upon User Datagram Protocol (UDP). While TCP meticulously establishes connections and guarantees delivery, UDP prioritizes speed, sacrificing guaranteed delivery and order. QUIC cleverly integrates reliability and security into the UDP foundation, employing forward error correction to recover from packet loss without retransmission and implementing robust encryption from the connection’s outset. This approach minimizes connection establishment time – crucial for mobile users and high-latency networks – and reduces head-of-line blocking, a common TCP bottleneck where a single lost packet can stall the entire connection. Furthermore, QUIC’s connection migration capabilities allow seamless transitions between networks-such as switching from Wi-Fi to cellular-without interrupting data streams, resulting in a more resilient and responsive web experience.
Connection Resilience: Beyond Static IPs with QUIC
QUIC’s Connection Migration feature enables a persistent network connection despite changes to a client’s IP address, a capability not inherent in TCP. Traditionally, TCP connections are tied to a 4-tuple consisting of source IP, source port, destination IP, and destination port; any change to the source IP necessitates connection re-establishment. QUIC circumvents this limitation by utilizing Connection IDs (CIDs) which function as connection identifiers independent of the underlying IP addresses. This allows a client to switch networks-for example, transitioning from Wi-Fi to cellular-without interrupting active data streams, as the server continues to associate the CID with the ongoing connection regardless of IP address modifications.
Connection IDs (CIDs) are 64-bit identifiers generated at the initiation of a QUIC connection and function as the primary means of identifying that connection for the duration of its lifespan. Unlike traditional TCP connections which are tied to a 4-tuple of source IP, source port, destination IP, and destination port, QUIC utilizes CIDs to maintain connection state even if the client’s IP address changes during a session. This decoupling of the connection identifier from the IP address enables connection migration, allowing a continuous experience across network changes. Both the client and server negotiate and exchange CIDs during the handshake process, and all subsequent packets are tagged with the CID, ensuring packets are correctly associated with the established connection regardless of IP address fluctuations.
Connection Migration, while enhancing user experience for mobile devices by maintaining connections across IP address changes, introduces challenges for network infrastructure designed around IP address-based connections. Traditional network devices, such as firewalls and load balancers, often rely on source and destination IP addresses to track connection state and enforce security policies; the persistence of a connection with a changing source IP address can bypass these mechanisms. This necessitates updates to network middleboxes to correctly identify and manage connections based on the Connection ID (CID) rather than solely on IP addresses, potentially requiring significant configuration changes and upgrades to maintain network visibility and control. Furthermore, existing logging and monitoring systems may need adaptation to accurately track connections when the source IP changes mid-session.
Kubernetes and the QUIC Challenge: When Stability Meets Mobility
Kubernetes utilizes IP addresses as fundamental identifiers for service discovery and load balancing. When a service is created, Kubernetes assigns it a virtual IP (VIP) and associated port. Internal DNS then resolves the service name to this VIP, enabling clients to consistently reach the service regardless of pod failures or scaling events. Load balancing is achieved by directing traffic to the appropriate pod IP addresses associated with the service. This system inherently depends on a stable mapping between service names, VIPs, and pod IPs; changes to these mappings must be reliably propagated throughout the cluster for continued operation. Consequently, Kubernetes assumes predictable IP address behavior for all network traffic entering and exiting services.
QUIC’s connection migration feature allows a client to seamlessly switch between different IP addresses or network paths without re-establishing the connection. Within a Kubernetes environment, this presents a challenge because services are typically accessed via stable virtual IP addresses managed by the kube-proxy. When a QUIC client migrates to a new IP address not registered with kube-proxy, service discovery fails, resulting in dropped connections and potential service unavailability. Furthermore, a malicious actor could exploit connection migration to rapidly cycle through numerous IP addresses, overwhelming the Kubernetes service with connection requests and potentially causing a denial-of-service condition. This is because the service remains unaware of the client’s changing source IP, and standard rate limiting or security policies based on IP addresses become ineffective.
QUIC-aware Stateful Middleboxes (QASM) address the challenges posed by QUIC connection migration within Kubernetes by implementing stateful tracking of connections. Unlike traditional load balancers which rely on initial IP addresses for service discovery, QASM maintains a record of QUIC connections as they migrate, ensuring continued routing to the correct backend pod. The research demonstrates that this stateful tracking introduces minimal overhead – less than 1% in measured tests – while preserving the functionality of standard middlebox operations such as firewalling and intrusion detection. This negligible performance impact allows for the deployment of QASM without significantly affecting cluster resources or application latency, offering a practical solution to maintain service availability and security in QUIC-enabled Kubernetes environments.
QASM: Orchestrating Connection Stability in a Dynamic World
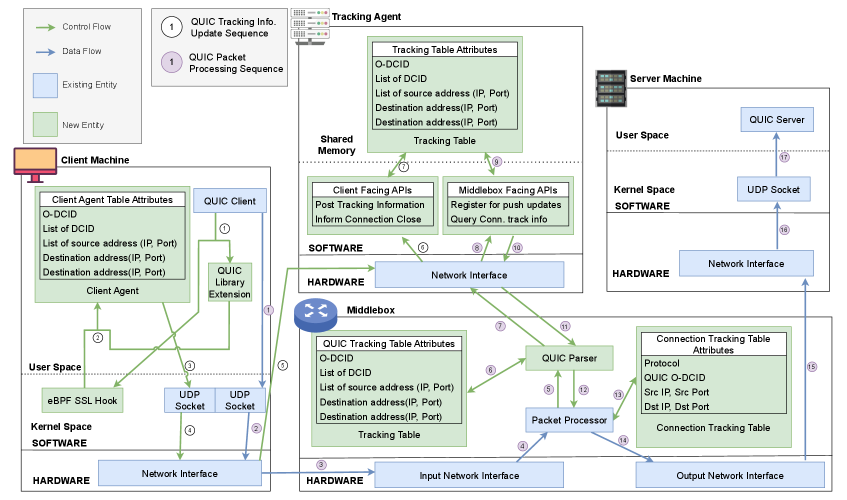
The core of connection stability within the QASM framework relies on its Tracking Agent, a component designed to meticulously maintain detailed connection tracking information. This agent functions as an anchor, firmly establishing each QUIC connection within the Kubernetes cluster’s operational environment. By persistently monitoring and recording key connection parameters – such as source and destination addresses, ports, and cryptographic keys – the Tracking Agent ensures that connections remain identifiable and manageable even as they migrate between different pods or nodes. This persistent tracking is crucial for seamless connection migration, allowing the system to correctly route packets and maintain session state, effectively shielding applications from disruptions caused by underlying infrastructure changes.
The Client Agent functions as a critical intermediary in maintaining stable QUIC connections within a Kubernetes environment. This agent actively gathers essential connection tracking data directly from the client application – information such as source and destination IPs, port numbers, and connection timestamps. This data isn’t simply collected, but carefully formatted and reliably relayed to the Tracking Agent, which then anchors the connection to the Kubernetes cluster. This continuous data stream enables QASM to monitor connection health and proactively respond to network changes, ensuring minimal disruption even as clients migrate between different network interfaces or experience temporary connectivity issues. The agent’s role is therefore paramount in bridging the gap between the application and the underlying orchestration platform, providing the necessary visibility for seamless connection management.
QASM fundamentally enhances Kubernetes capabilities by introducing a system aware of individual QUIC connections, enabling seamless migration as network conditions change. This is achieved through coordinated operation of Client and Tracking Agents; the former gathers connection data from the initiating endpoint, while the latter maintains this information within the Kubernetes environment, effectively ‘anchoring’ the connection. Rigorous testing demonstrates that this added functionality introduces a negligible performance impact – a maximum of 5% overhead in packet processing – while maintaining comparable latency and throughput figures to standard Kubernetes configurations, ensuring a robust and efficient user experience even during network transitions.
The research delves into the inherent tension between innovation and established network infrastructure, a challenge elegantly captured by Paul Erdős who once stated, “A mathematician knows how to solve a problem; an engineer knows how to prevent it.” QASM attempts to prevent the disruption caused by QUIC’s connection migration-a feature designed to improve user experience-to the operation of stateful middleboxes. These devices, crucial for security and network management, rely on consistent connection tracking, and the paper highlights how QUIC fundamentally undermines this assumption. The framework essentially reverse-engineers the QUIC protocol to allow middleboxes to adapt, revealing a pragmatic approach to maintaining functionality in the face of evolving network standards.
What Lies Beyond?
The presented framework, QASM, addresses a symptom of progress – the inevitable friction between innovation and established infrastructure. It is a temporary bulwark against the tide, acknowledging that stateful middleboxes, however crucial today, represent a fundamentally brittle approach to network management. The real question isn’t how to patch these devices to accommodate QUIC’s connection migration, but whether such patching is merely delaying the inevitable architectural shift. One suspects the universe favors elegant solutions, and the continued complexity required to reconcile QUIC with legacy systems feels… unsustainable.
Future work should not focus solely on refining QASM-like approaches. Instead, it should interrogate the very notion of statefulness in a network increasingly defined by ephemeral connections and client-driven control. Can machine learning techniques predict connection migration patterns before they occur, allowing for proactive state adjustments? Or, more radically, can middlebox functionality be decomposed and distributed to endpoints, effectively dissolving the need for centralized state altogether? The pursuit of perfect tracking feels increasingly like a fool’s errand.
Ultimately, this research highlights a recurring paradox: the tools designed to secure and manage networks often become the greatest impediments to their evolution. One anticipates a future where network intelligence resides not in dedicated appliances, but in a distributed, adaptive mesh – a system that doesn’t react to change, but embraces it as a fundamental property. The challenge lies in recognizing that chaos is not an enemy, but a mirror of architecture reflecting unseen connections.
Original article: https://arxiv.org/pdf/2602.03354.pdf
Contact the author: https://www.linkedin.com/in/avetisyan/
See also:
- Poppy Playtime Chapter 5: Engineering Workshop Locker Keypad Code Guide
- God Of War: Sons Of Sparta – Interactive Map
- Jujutsu Kaisen Modulo Chapter 23 Preview: Yuji And Maru End Cursed Spirits
- Poppy Playtime 5: Battery Locations & Locker Code for Huggy Escape Room
- Who Is the Information Broker in The Sims 4?
- Poppy Playtime Chapter 5: Emoji Keypad Code in Conditioning
- Why Aave is Making Waves with $1B in Tokenized Assets – You Won’t Believe This!
- Pressure Hand Locker Code in Poppy Playtime: Chapter 5
- All 100 Substory Locations in Yakuza 0 Director’s Cut
- One Piece Chapter 1175 Preview, Release Date, And What To Expect
2026-02-04 09:19