Author: Denis Avetisyan
New research assesses how effectively RISC-V systems can isolate critical tasks from less sensitive ones, ensuring safety and reliability in complex applications.
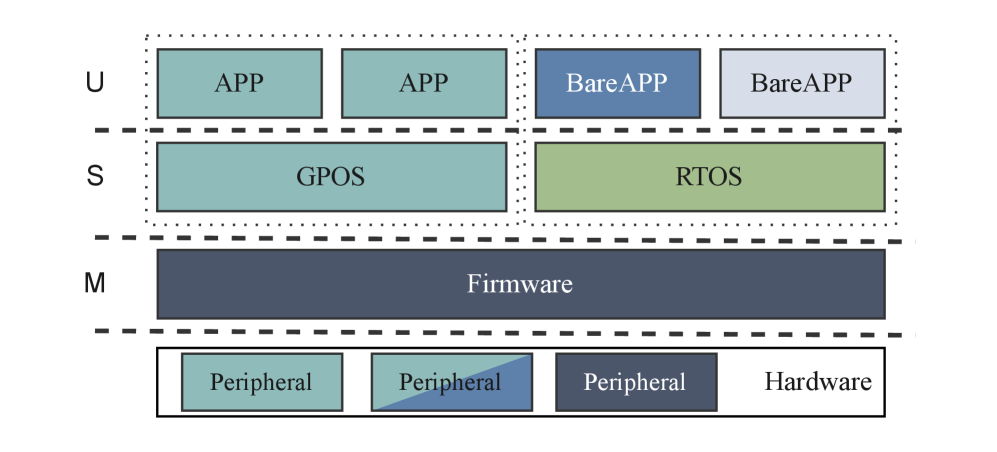
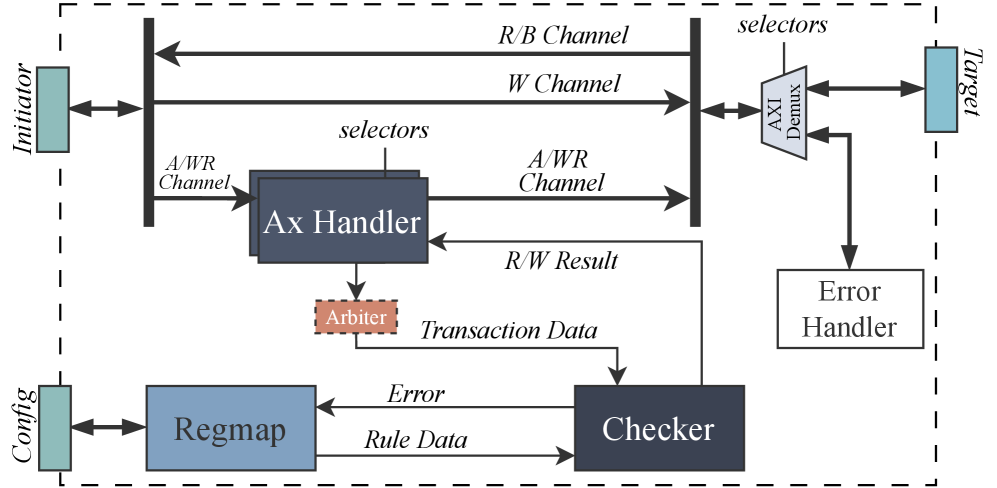
Target-side protection mechanisms, including the World Checker, are evaluated and optimized for deterministic, low-latency isolation in mixed-criticality RISC-V SoCs.
Achieving robust system-level isolation in increasingly complex embedded systems remains a significant challenge, particularly as heterogeneous architectures become commonplace. This is the central focus of ‘System-Level Isolation for Mixed-Criticality RISC-V SoCs: A “World” Reality Check’, which comparatively analyzes hardware isolation primitives-including RISC-V Worlds and IOPMP-within the context of modern Systems-on-Chip designs. Our evaluation demonstrates that a World-based checker offers deterministic, low-latency isolation suitable for real-time applications, and that modifications to the baseline specification can improve both scalability and area efficiency by up to 5%. Will these findings accelerate the adoption of robust, secure, and efficient RISC-V SoCs across safety-critical domains?
The Inevitable Security Debt of Open Architectures
The RISC-V instruction set architecture is experiencing a surge in adoption, swiftly becoming a cornerstone of modern computing across a remarkably broad spectrum of applications. Initially gaining momentum in embedded systems, its open-source nature and inherent flexibility are now driving integration into safety-critical arenas like the automotive sector, where it powers advanced driver-assistance systems and in-vehicle infotainment. Simultaneously, the proliferation of Internet of Things (IoT) devices – from smart home appliances to industrial sensors – increasingly relies on RISC-V’s low power consumption and customizable design. Furthermore, the demands of industrial control systems, requiring reliable and adaptable processing, are accelerating the shift towards RISC-V based solutions, establishing it as a truly versatile architecture poised to redefine computing landscapes.
As the RISC-V architecture permeates increasingly critical systems – from the intricacies of automotive engineering to the pervasive network of Internet of Things devices and the precision of industrial controls – the demand for comprehensive security measures escalates proportionally. The open nature of RISC-V, while fostering innovation, simultaneously broadens the attack surface, requiring proactive defenses against a constantly evolving threat landscape. System integrity, encompassing data confidentiality, operational reliability, and protection against malicious manipulation, is no longer simply a desirable feature, but a fundamental prerequisite for deployment in these sensitive domains. Without robust security protocols woven into the core architecture, the benefits of RISC-V’s flexibility and customizability are undermined, potentially exposing users and infrastructure to significant vulnerabilities and risks.
The increasing prevalence of RISC-V architecture across critical infrastructure presents a unique security challenge, largely stemming from the non-native integration of established security extensions. While technologies like TrustZone have proven effective in safeguarding other processor architectures, adapting them to RISC-V requires significant overhead and can introduce compatibility issues. This often necessitates complex workarounds or the development of entirely new security layers, increasing both development time and potential vulnerabilities. The lack of seamless integration isn’t merely a technical hurdle; it impacts the overall system performance and introduces a degree of fragmentation that complicates long-term maintenance and updates, ultimately demanding a re-evaluation of established security paradigms for this burgeoning open-source platform.
RISC-V Worlds: A Band-Aid on a Fundamental Problem
RISC-V Worlds establishes a system-level isolation paradigm by partitioning the operating environment into discrete execution contexts termed ‘worlds’. Each world operates with a defined set of privileges and is allocated a dedicated memory space, preventing unauthorized access between them. This approach differs from traditional isolation techniques by operating at a lower level, directly within the hardware architecture, and offering a more robust and granular control over resource access. The isolation is enforced through the separation of memory and privilege domains, ensuring that code executing within one world cannot directly interfere with the operations or data of another, thereby enhancing system security and stability.
World Identifiers (WIDs) function as unique, immutable tags associated with all security-sensitive operations and data within the RISC-V Worlds framework. These WIDs are utilized by the Worlds Checker (WC) to determine permissible access. Specifically, each memory access, instruction execution, and inter-process communication attempt is tagged with the WID of the originating world. The WC then compares this originating WID against the access control policy associated with the target resource, enforcing isolation by permitting access only if the WIDs are compatible according to the defined policy. This WID-based access control mechanism enables fine-grained protection, allowing for the creation of isolated execution environments with distinct privilege levels and resource access rights, thereby safeguarding sensitive data and preventing unauthorized operations.
The Worlds Checker (WC) is a dedicated hardware unit integrated into the system to enforce access control policies defined by World Identifiers (WIDs). It operates by intercepting memory accesses and privileged instructions, verifying that the originating world – identified by its WID – possesses the necessary permissions for the requested operation. This verification process occurs prior to execution, preventing unauthorized access to memory regions or resources allocated to other worlds. The WC’s design prioritizes performance by implementing these checks in hardware, minimizing latency and overhead compared to software-based isolation mechanisms. Specifically, the WC maintains a mapping of WIDs to permitted access rights, allowing for rapid determination of policy compliance on each memory access and privileged instruction execution.
SmMTT and the WC: More Layers, More Complexity
SmMTT (Secure Memory Management and Translation Table) is a privileged architecture extension for the RISC-V instruction set architecture (ISA) intended to enhance system security by isolating both physical memory and access to peripheral devices. It operates in conjunction with the RISC-V Worlds model, which establishes isolated execution environments or “Worlds”. SmMTT provides the hardware mechanisms necessary to enforce the boundaries defined by the Worlds model, preventing unauthorized access between these isolated environments. This is achieved through a combination of memory translation and access control features, allowing the system to define which Worlds have access to specific physical memory regions and devices. By complementing the Worlds model, SmMTT enables the creation of more robust and secure systems, particularly those requiring strong isolation for security-critical applications.
Supervisor Domain Access Protection, a core component of the SmMTT architecture, mitigates the risk of unauthorized memory access originating from privileged software executing in supervisor mode. This protection is achieved by enforcing strict access control policies, ensuring that even software with the highest privileges cannot bypass established security boundaries. Specifically, SmMTT utilizes World IDs (WIDs) to define isolated memory regions, and the Supervisor Domain Access Protection mechanism verifies that any memory access initiated by supervisor-level code is authorized for the corresponding WID. This prevents malicious or compromised supervisor software from directly accessing or modifying data belonging to other isolated worlds, thereby enhancing system security and reliability. The implementation details ensure minimal performance overhead while providing a robust security layer against internal threats.
The World Checker (WC) implements access control by defining memory regions using Start-End Address Matching. This technique allows the system to associate a specific range of physical addresses with a World Identifier (WID), effectively creating isolated memory spaces. Access requests are then checked to ensure the requesting WID possesses permission for the target address range. This granular control enables the definition of arbitrary, non-contiguous memory regions protected by specific WIDs, moving beyond traditional page-based memory protection schemes and offering a more flexible and precise security model. The WC compares the start and end addresses of the access request against the defined regions associated with the requesting WID to determine access permission.
General Read Permission within the SmMTT architecture enables the sharing of read-only memory regions across multiple World Identifiers (WIDs). This functionality avoids redundant memory duplication and associated performance overhead by allowing several WIDs to simultaneously access the same read-only data without requiring separate physical copies. Security is maintained because the permission explicitly restricts write access; while multiple WIDs can read the shared region, no WID is authorized to modify its contents, ensuring data integrity and preventing unauthorized modification. This approach optimizes system performance by reducing memory footprint and bandwidth requirements, particularly beneficial in resource-constrained environments.
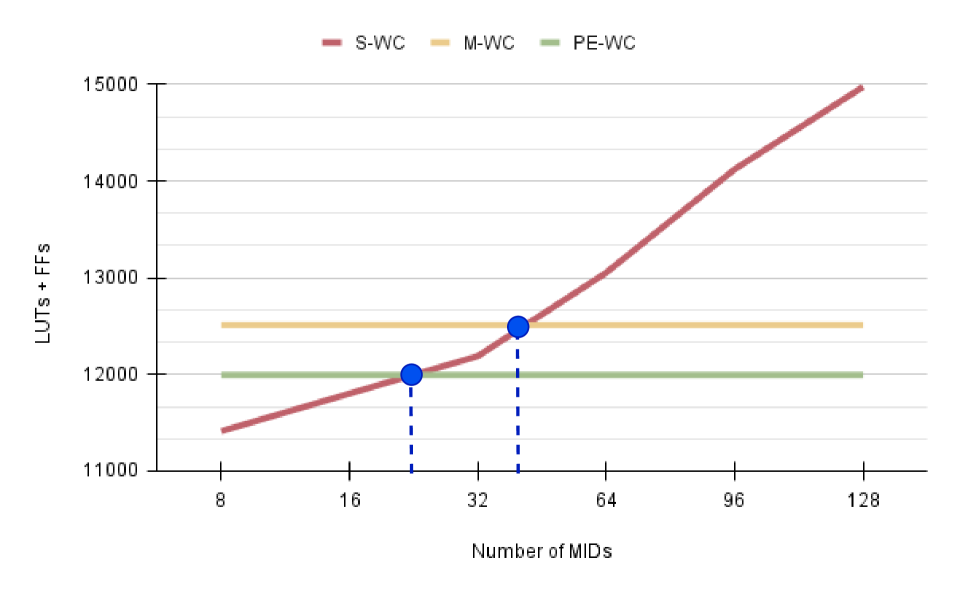
Evaluations detailed in this paper indicate that modified World Checker (M-WC) implementations achieve reductions in hardware resource consumption of up to 5% when configured with a large number of World Identifiers (WIDs). These gains are realized without negatively impacting access latency; measured performance demonstrates low and, crucially, deterministic access times, making these M-WC designs suitable for deployment in real-time operating systems and other latency-sensitive applications. The resource reduction is primarily attributed to optimizations in the address decoding and identifier comparison logic within the World Checker.
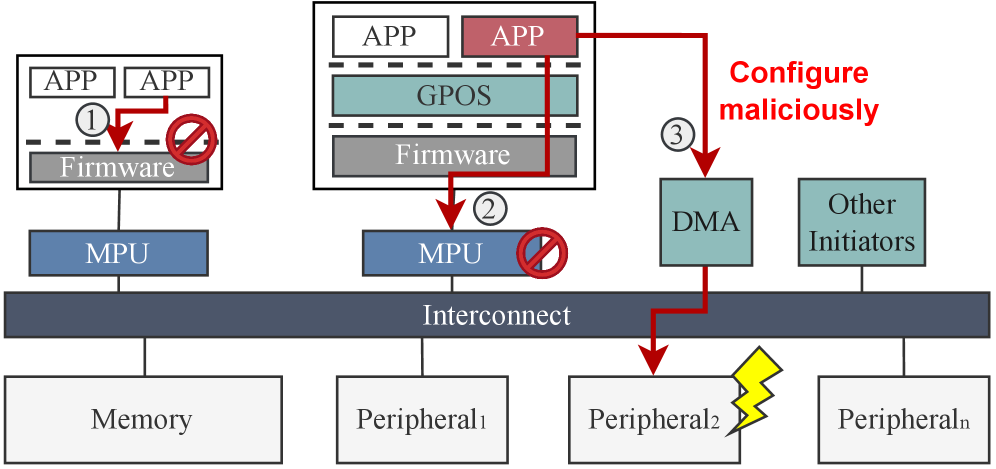
Peripheral Control: A Necessary, But Insufficient, Safeguard
The IOPMP Checker functions as a dedicated hardware component that rigorously enforces peripheral access control policies within a RISC-V system. It operates by verifying that any software attempting to interact with critical peripherals possesses the necessary authorization, effectively preventing unauthorized access and potential malicious activity. This enforcement isn’t achieved through software-based checks, which can be bypassed, but through a physically implemented security barrier at the hardware level. By directly controlling access rights, the IOPMP Checker ensures that only trusted software can manipulate essential system components, thereby safeguarding data integrity and enhancing overall system security against a broad range of threats. This proactive approach to security is particularly crucial in embedded systems and applications where vulnerabilities can have significant real-world consequences.
The IOPMP Checker doesn’t operate in isolation; rather, it forms a crucial component of a layered security approach for RISC-V systems. When integrated with the Memory Protection Controller (WC) and the Single Multi-Threaded Test (SmMTT), a robust and comprehensive security architecture emerges. The WC establishes broad memory access controls, preventing unauthorized access to memory regions, while SmMTT provides a mechanism for testing and validating system behavior. The IOPMP Checker then builds upon this foundation by adding fine-grained control over peripheral access, ensuring that even if memory access is granted, only authorized software can interact with critical hardware components. This synergistic combination of technologies creates a defense-in-depth strategy, significantly enhancing the overall security posture of the RISC-V system and safeguarding it against a wide range of potential attacks.
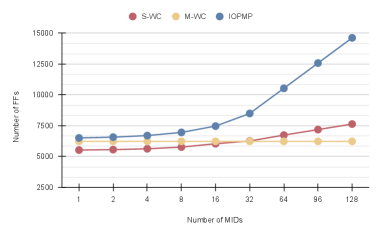
The integrated security architecture, encompassing the IOPMP Checker, WC, and SmMTT, underwent rigorous validation utilizing the CVA6 RISC-V processor as a testbed. This evaluation confirmed the practical functionality of the system, demonstrating its ability to enforce peripheral access control policies at the hardware level. Performance metrics were carefully assessed during testing, revealing the latency impacts of each component – a 2-cycle increase for both the M-WC and S-WC, and a best-case 3-cycle latency introduced by the IOPMP Checker. These results provide crucial data for system designers, illustrating the trade-offs between security and performance when implementing this comprehensive security framework. The successful validation with CVA6 signifies a substantial step towards deploying secure and reliable RISC-V systems in demanding applications.
The increasing prevalence of embedded systems in safety-critical domains, such as automotive and industrial control, demands unwavering data integrity and system reliability. Consequently, a robust security foundation is no longer optional, but a necessity. Compromised systems in these environments can lead to catastrophic failures, impacting both human life and critical infrastructure. The architecture described provides a hardened defense against malicious attacks and unintentional errors by rigorously controlling peripheral access. This level of security ensures that sensitive operations and data remain protected, fostering trust in the system’s ability to function predictably and safely, even in the face of adversarial conditions or unexpected events. This is particularly crucial for applications where even minor deviations from expected behavior can have severe consequences, making a secure and dependable foundation paramount.
The implementation of enhanced security measures inevitably introduces a performance trade-off; analysis reveals that both the Memory Write Checker (M-WC) and the Secure Memory Tagging Table (S-WC) incur a 2-cycle latency increase when accessing memory. The IOPMP Checker, responsible for hardware-level peripheral access control, exhibits a slightly greater latency, adding 3 cycles in optimal scenarios. While these increases represent a measurable impact on execution speed, they are considered acceptable given the substantial gains in system security and data integrity. This carefully balanced approach ensures robust protection against unauthorized access without unduly compromising overall performance, a crucial consideration for resource-constrained embedded systems and safety-critical applications.
The pursuit of robust system-level isolation, as detailed in this work regarding RISC-V SoCs, inevitably reveals the chasm between theoretical elegance and practical implementation. The paper’s focus on deterministic, low-latency isolation with World Checker designs is admirable, yet one anticipates the eventual complexities that production environments will introduce. As Alan Turing observed, “There is no escaping the fact that the machine can only do what we tell it.” This rings true; the authors meticulously craft a protective ‘world,’ but the real test will be how it withstands unforeseen interactions and the relentless pressure for optimization. Scalability improvements are presented, but history suggests those gains rarely remain untouched for long. It’s a solid foundation, certainly, but the inevitable accumulation of technical debt is already being written.
What’s Next?
The pursuit of clean isolation-of neatly partitioned “worlds”-in embedded systems invariably encounters the messiness of production. This work demonstrates a pathway to deterministic isolation using World Checker within RISC-V SoCs, a commendable feat. However, the implied next step isn’t further refinement of the checker itself, but an honest accounting of the costs of that determinism. Each added layer of protection isn’t merely computation; it’s future debugging time, increased verification complexity, and a larger attack surface for subtle timing violations. The scalability improvements, while valuable, merely delay the inevitable: the point at which the isolation mechanism itself becomes the dominant performance bottleneck.
The paper rightly focuses on target-side protection, a necessary constraint for real-time systems. But the real challenge lies in integrating these mechanisms with existing, often chaotic, software stacks. Expect a proliferation of ad-hoc wrappers and compatibility layers-a testament to the fact that elegant theory rarely survives contact with legacy code. CI is, of course, the temple, and the daily prayers involve hoping nothing breaks with each new integration.
Ultimately, the true metric of success won’t be isolation latency, but the total cost of ownership. The long-term viability of these approaches hinges not on architectural novelty, but on minimizing the operational burden. Documentation, as always, remains a myth invented by managers; the real knowledge will reside in the tribal memory of those maintaining these systems after the initial research funding has dried up.
Original article: https://arxiv.org/pdf/2602.05002.pdf
Contact the author: https://www.linkedin.com/in/avetisyan/
See also:
- God Of War: Sons Of Sparta – Interactive Map
- Poppy Playtime 5: Battery Locations & Locker Code for Huggy Escape Room
- Overwatch is Nerfing One of Its New Heroes From Reign of Talon Season 1
- Someone Made a SNES-Like Version of Super Mario Bros. Wonder, and You Can Play it for Free
- Poppy Playtime Chapter 5: Engineering Workshop Locker Keypad Code Guide
- One Piece Chapter 1175 Preview, Release Date, And What To Expect
- Meet the Tarot Club’s Mightiest: Ranking Lord Of Mysteries’ Most Powerful Beyonders
- Why Aave is Making Waves with $1B in Tokenized Assets – You Won’t Believe This!
- Bleach: Rebirth of Souls Shocks Fans With 8 Missing Icons!
- New Naruto Anime Is Officially Coming In 2026
2026-02-06 18:36