Author: Denis Avetisyan
A comprehensive dataset reveals widespread susceptibility to bad randomness in Ethereum smart contracts, exposing critical gaps in current security tooling.
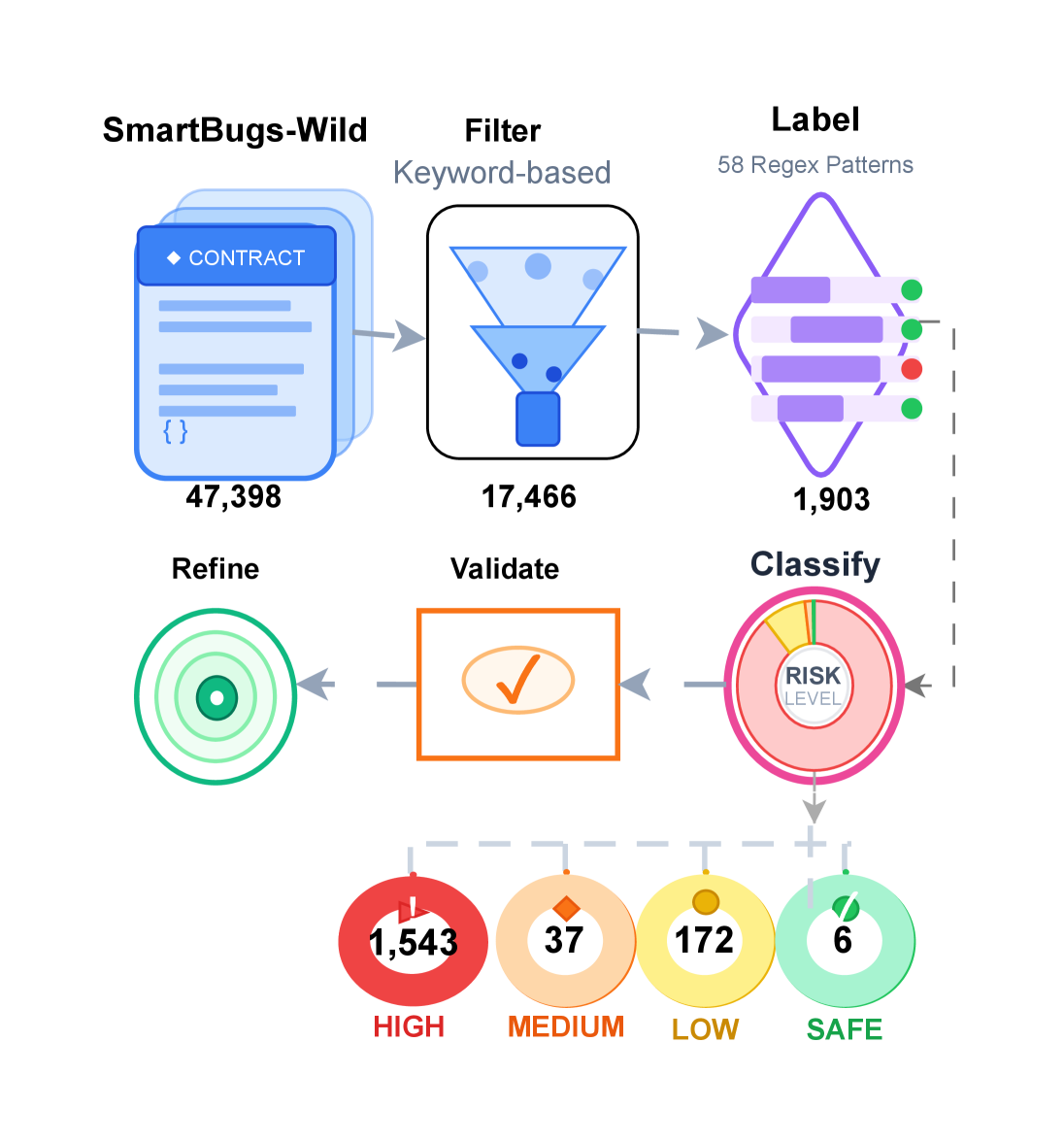
Researchers present SWC-120, a risk-stratified benchmark of 120 vulnerable contracts demonstrating the ineffectiveness of existing static analysis techniques.
Despite the critical need for secure randomness in blockchain applications, Ethereum smart contracts frequently rely on predictable and manipulable block attributes, creating exploitable Bad Randomness (SWC-120) vulnerabilities. This paper introduces ‘A Risk-Stratified Benchmark Dataset for Bad Randomness (SWC-120) Vulnerabilities in Ethereum Smart Contracts’, a collection of 1,752 validated contracts demonstrating a surprisingly high prevalence of unprotected or inadequately protected code. Our analysis reveals that existing static analysis tools exhibit significant detection gaps, failing to identify the majority of vulnerable instances-and that nearly half of contracts believed to be protected are, in fact, exploitable. Can this newly available, risk-stratified dataset catalyze the development of more robust smart contract security tools and ultimately safeguard decentralized applications from randomness-based attacks?
The Illusion of Predictability: Smart Contracts and the Entropy Gap
The foundational logic of decentralized finance (DeFi) and non-fungible token (NFT) markets relies heavily on smart contracts, yet these contracts are demonstrably vulnerable due to inadequacies in how randomness is generated and utilized. Many smart contracts require unpredictable values for various functions-from fairly distributing NFTs to determining winners in lotteries or executing complex financial trades. However, developers frequently employ deterministic or easily predictable methods for generating these random numbers, often deriving them from readily available blockchain data such as block timestamps or hash values. This reliance on predictable sources introduces significant security risks, allowing malicious actors to anticipate outcomes and exploit contract logic for financial gain. The consequences can range from the theft of assets to the manipulation of market prices, highlighting the critical need for secure and truly random number generation within smart contract development.
The integrity of many smart contracts hinges on the generation of truly random numbers, yet a common pitfall lies in deriving these values from predictable block attributes like timestamps or block hashes. This practice introduces exploitable weaknesses because these attributes are publicly known and, crucially, manipulable by malicious actors. Consequently, outcomes intended to be random – such as the distribution of NFTs, the selection of winners in a lottery, or the assignment of resources in a decentralized application – become foreseeable. An attacker can analyze these block attributes and calculate the precise outcome of the random function, allowing them to strategically position themselves to benefit from the predictable result, effectively undermining the contract’s intended functionality and potentially leading to significant financial losses.
The security of decentralized applications increasingly relies on the integrity of random number generation within smart contracts, yet a formally recognized vulnerability – ‘Weak Sources of Randomness’ (SWC-120) – poses a significant threat. This issue, now cataloged within a dedicated registry, stems from predictable or manipulable randomness, creating openings for attackers to exploit contract logic. To quantify this risk, a comprehensive benchmark dataset comprising 1,758 demonstrably vulnerable smart contracts has been assembled. This resource underscores the prevalence of weak randomness implementations and provides a critical testing ground for the development of more robust detection and mitigation strategies, ultimately aiming to fortify the foundations of decentralized finance and non-fungible token ecosystems.
Automated Scrutiny: The Limits of Static Analysis
Static analysis tools, including Slither, Mythril, and SmartCheck, represent a foundational security practice in Solidity development by examining source code for potential vulnerabilities without executing the program. These tools operate by applying a set of predefined rules and patterns to identify common flaws such as reentrancy, timestamp dependence, and arithmetic overflows. Proactive application of static analysis allows developers to address security concerns early in the development lifecycle, significantly reducing the risk of deploying vulnerable smart contracts. While not a replacement for dynamic analysis or auditing, static analysis provides an efficient and scalable method for initial vulnerability detection and contributes to a more secure codebase by identifying a broad range of potential issues before deployment to a blockchain network.
Symbolic execution, combined with taint analysis, facilitates the identification of vulnerabilities in random number generation within smart contracts. Taint analysis tracks the flow of data from its origin – in this case, sources of randomness – through the contract’s code. By observing how potentially untrusted external data influences critical operations, such as the seeding of random number generators, these techniques can pinpoint instances where predictable or manipulable values are used. Tools like TaintSentinel implement these methods to determine if randomness is compromised, potentially leading to exploitable outcomes in applications reliant on secure, unpredictable numbers.
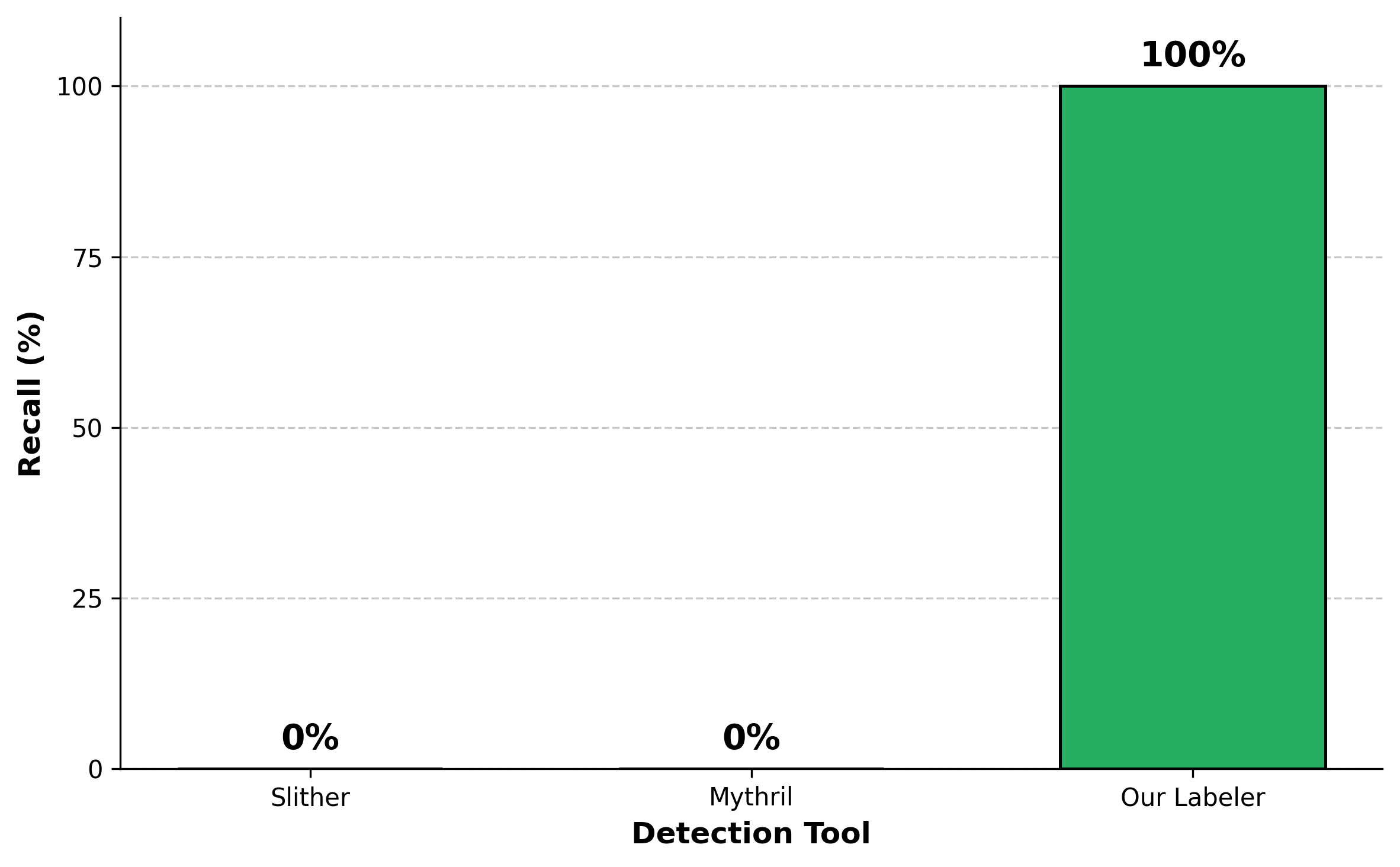
Static analysis tools, while valuable for proactive vulnerability detection in Solidity code, are demonstrably limited in their effectiveness. Research utilizing a dataset of 1,758 vulnerable contracts revealed that established tools, specifically Slither and Mythril, exhibited 0% recall. This indicates a complete failure to identify any of the vulnerabilities present within the tested contracts, necessitating thorough manual validation and refinement of results to mitigate the risk of both false positives and, critically, false negatives that could lead to exploitable code being deployed. The inability to reliably detect existing vulnerabilities highlights the need for improved detection methodologies and more comprehensive evaluation benchmarks.
The evaluation of automated vulnerability detection tools relies on curated datasets of vulnerable smart contracts. Currently, RNVulDet is a commonly used benchmark, comprising 34 contracts. To address the limitations of this relatively small dataset, a new benchmark has been created consisting of 1,758 vulnerable contracts – a 51-fold increase in size. This expanded dataset facilitates a more comprehensive and statistically significant evaluation of detection tool effectiveness, enabling more robust comparisons and driving continuous improvement in the field of smart contract security analysis.
The Illusion of Control: Entropy and the Blockchain
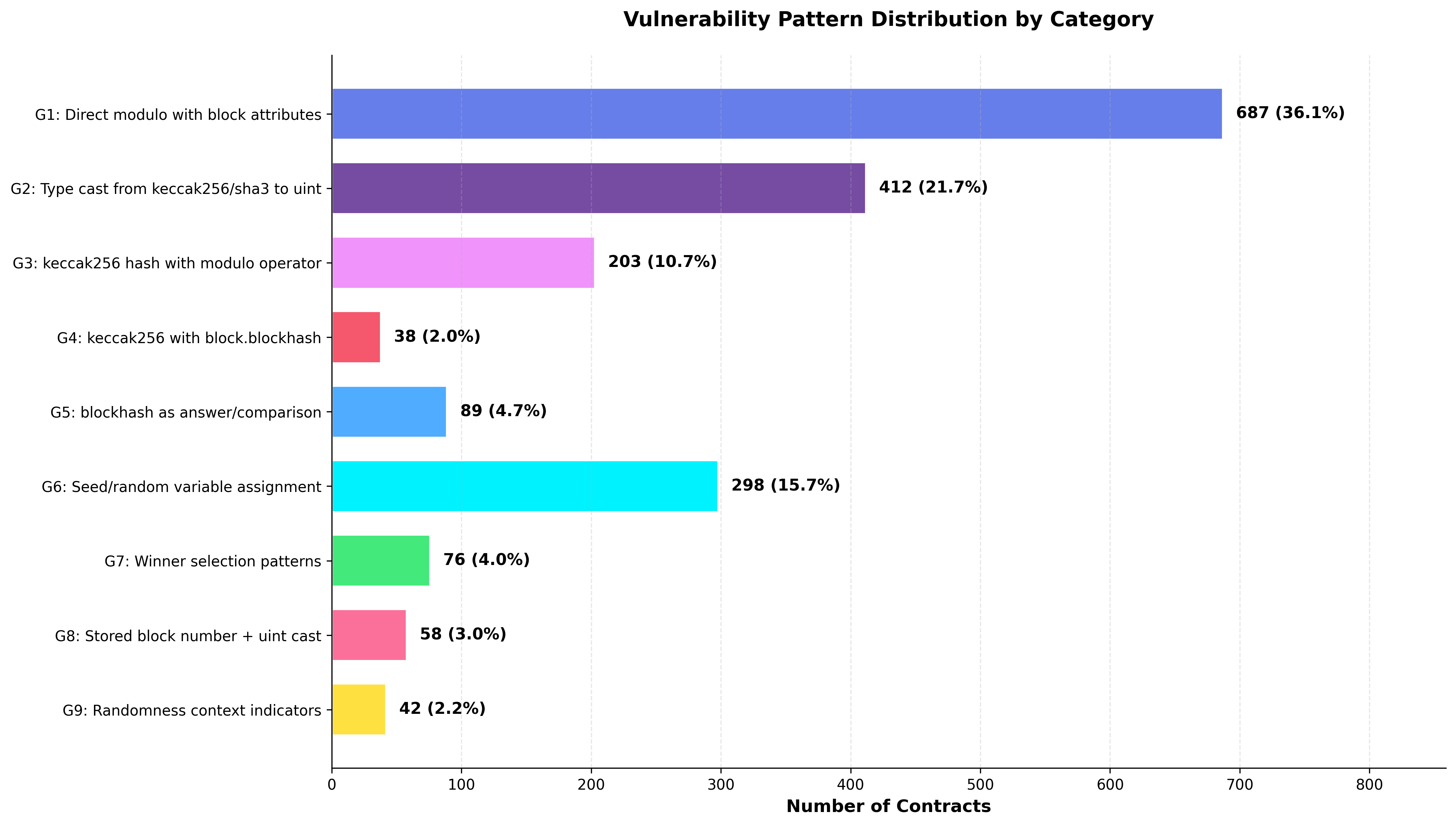
The utilization of block attributes – specifically timestamp, hash, difficulty, and block number – as sources of randomness within smart contracts introduces significant security vulnerabilities. These attributes are susceptible to manipulation by miners, who have direct control over their values prior to block propagation. A miner can strategically select values that benefit them, potentially biasing the outcome of any process relying on this “randomness.” Furthermore, the predictability of these attributes – even without malicious intent – allows for pre-computation of possible outcomes, enabling exploitation. This inherent lack of true randomness compromises the fairness and security of applications such as lotteries, gaming, and NFT minting, making reliance on block attributes an unacceptable practice for secure on-chain randomness.
Cryptographically secure randomness solutions address the inherent unpredictability requirements of on-chain applications by leveraging techniques that provide both verifiability and unbiased results. Chainlink VRF (Verifiable Random Function) utilizes cryptographic commitments and on-chain computation to generate and verify a random number, ensuring that no party can influence the outcome. Commit-Reveal Schemes function similarly, involving an initial commitment of random data followed by its reveal, allowing verification of the randomness without pre-knowledge. These methods contrast with pseudo-random number generators often found in blockchain environments, which are susceptible to manipulation by miners or other actors with control over block parameters. The core principle is to separate randomness generation from on-chain execution, utilizing off-chain computation and cryptographic proofs to guarantee the integrity and impartiality of the random value used within the smart contract.
Effective access control is paramount when integrating randomness sources into smart contracts to prevent unauthorized modification of generated values. This requires carefully restricting which accounts or contracts can interact with the randomness source, typically through the use of modifiers that verify sender authorization. Implementation should include a clear separation of duties, ensuring that the contract owner or a designated administrator has exclusive control over critical randomness parameters or the selection of randomness providers. Insufficient access control can allow malicious actors to influence the random number generation process, potentially exploiting vulnerabilities for financial gain or to manipulate contract outcomes; a recent analysis of existing contracts revealed that 87.8% currently lack adequate mitigation against such manipulation.
Keccak256 is a widely adopted cryptographic hash function used in secure randomness solutions for smart contracts due to its strong collision resistance and preimage resistance. Its integration helps ensure the unpredictability and integrity of generated random values. However, analysis of a substantial contract dataset reveals that 87.8% currently lack any implemented mitigation against vulnerabilities related to predictable or manipulable randomness, representing a significant security risk. This widespread absence of defensive measures suggests a critical gap in smart contract security practices, potentially exposing a large number of deployed contracts to exploitation.
The Fragility of Trust: Proactive Security and the Path Forward
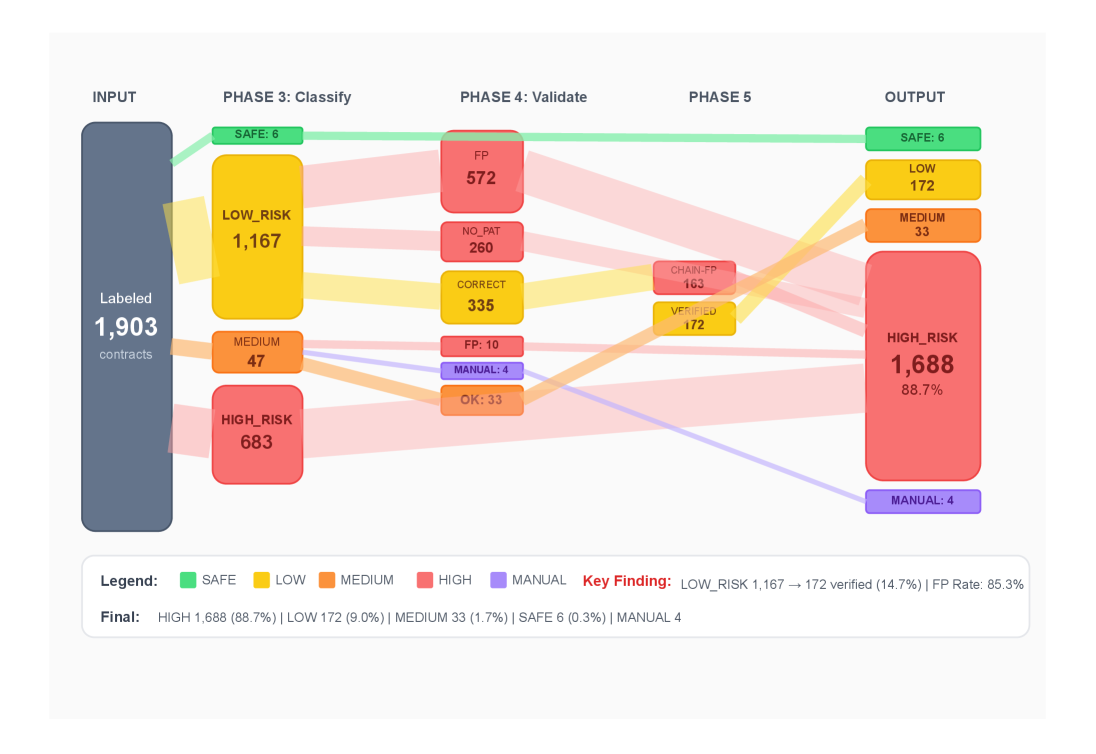
Function-level validation represents a critical layer of defense in smart contract security, focusing on ensuring that protective modifiers – code segments designed to restrict access or alter behavior – are functioning as intended. This process rigorously tests whether these modifiers accurately control access to sensitive functions, preventing unauthorized execution and potential exploitation. By verifying that modifiers correctly enforce preconditions, limit input values, or restrict state changes, developers can significantly reduce the attack surface of their contracts. Effective validation involves crafting comprehensive test cases that explore various scenarios, including both valid and invalid inputs, to confirm that the modifiers consistently uphold the intended security boundaries and prevent unintended consequences, ultimately bolstering the resilience of decentralized applications.
Smart contract security benefits significantly from risk-based stratification, a process of categorizing contracts according to their inherent vulnerability to exploits. This classification isn’t arbitrary; it relies on a detailed assessment of factors like contract complexity, the value of assets managed, and the potential impact of a successful attack. Contracts deemed ‘high-risk’ – those handling substantial funds or possessing intricate logic – receive prioritized security audits, often involving multiple independent reviews and more extensive testing. Conversely, simpler, lower-value contracts may undergo streamlined assessments. This tiered approach optimizes resource allocation, ensuring that the most critical systems receive the most thorough scrutiny, ultimately bolstering the overall security posture within decentralized finance and non-fungible token ecosystems.
A multi-layered defense strategy proves essential in fortifying smart contracts against increasingly sophisticated attacks. Static analysis tools meticulously scan code for vulnerabilities before deployment, identifying potential weaknesses in logic and implementation. Complementing this, the integration of secure randomness solutions-critical for applications like lotteries or NFT minting-prevents manipulation of outcomes and ensures fairness. Finally, rigorous validation, encompassing both functional testing and formal verification, confirms that the contract behaves as intended under all foreseeable circumstances. This combined approach systematically reduces the attack surface-the total sum of potential entry points for malicious actors-and significantly minimizes the risk of exploitation, thereby bolstering the security and reliability of decentralized applications.
The burgeoning landscapes of Decentralized Finance (DeFi) and Non-Fungible Tokens (NFTs) are fundamentally reliant on the perception of security; a single significant exploit can erode user confidence and destabilize entire platforms. Consequently, a shift towards proactive security measures – encompassing continuous monitoring, formal verification, and comprehensive testing – is no longer optional, but essential for sustained growth. These ecosystems, characterized by permissionless access and immutable code, present unique vulnerabilities that demand constant vigilance and the implementation of robust defenses before exploits occur. Prioritizing preventative strategies not only safeguards user assets but also fosters a more trustworthy environment, attracting further innovation and participation, ultimately cementing the long-term viability of these transformative technologies.
“`html
The presented dataset, a catalog of vulnerabilities stemming from unpredictable randomness, reveals a disturbing pattern. It isn’t merely a collection of flawed contracts, but a testament to the inevitable decay inherent in complex systems. As Alan Turing observed, “There is no pleasure in easy things.” This holds true here; the ease with which attackers exploit predictable randomness isn’t a failing of skill, but a symptom of foundational assumptions about control. The study demonstrates that static analysis tools, built on the premise of perfect foresight, consistently fail to detect these vulnerabilities, revealing a belief in architecture that denies the entropy of real-world deployment. The proliferation of unprotected contracts isn’t a bug; it’s a predictable consequence of building on shaky ground.
What’s Next?
The creation of a benchmark, even one as meticulously curated as this, does not solve the underlying problem. It merely illuminates the extent of the shadow. Existing static analysis tools, proven largely ineffective against these ‘bad randomness’ vulnerabilities, will undoubtedly undergo refinement. But chasing perfect detection is a fool’s errand. The system will evolve new weaknesses, new vectors for exploitation. A guarantee of security is simply a contract with probability, and the cost of that contract is eternal vigilance-a price no ecosystem can truly afford.
The field’s attention should shift from seeking absolute defense to accepting inherent fragility. The prevalence of unprotected contracts within this dataset isn’t a bug; it’s a feature. A decentralized system, by its nature, prioritizes openness and flexibility over rigid control. Stability is merely an illusion that caches well. Future work should explore mechanisms for graceful degradation, for limiting the blast radius of these vulnerabilities, rather than attempting their total eradication.
Ultimately, this work suggests that the real challenge isn’t building better tools, but fostering a more nuanced understanding of risk. Chaos isn’t failure-it’s nature’s syntax. The focus must move beyond identifying ‘vulnerabilities’ and toward modeling the emergent behavior of these complex systems, accepting that predictability is a comforting fiction.
Original article: https://arxiv.org/pdf/2601.09836.pdf
Contact the author: https://www.linkedin.com/in/avetisyan/
See also:
- God Of War: Sons Of Sparta – Interactive Map
- Overwatch is Nerfing One of Its New Heroes From Reign of Talon Season 1
- Someone Made a SNES-Like Version of Super Mario Bros. Wonder, and You Can Play it for Free
- Poppy Playtime 5: Battery Locations & Locker Code for Huggy Escape Room
- Poppy Playtime Chapter 5: Engineering Workshop Locker Keypad Code Guide
- Why Aave is Making Waves with $1B in Tokenized Assets – You Won’t Believe This!
- Meet the Tarot Club’s Mightiest: Ranking Lord Of Mysteries’ Most Powerful Beyonders
- One Piece Chapter 1175 Preview, Release Date, And What To Expect
- Bleach: Rebirth of Souls Shocks Fans With 8 Missing Icons!
- All Kamurocho Locker Keys in Yakuza Kiwami 3
2026-01-16 22:45