Author: Denis Avetisyan
A new signature aggregation protocol, Wonderboom, promises to dramatically improve the scalability and censorship resistance of blockchain systems.

Wonderboom efficiently aggregates signatures from millions of validators to enhance finality and Byzantine fault tolerance.
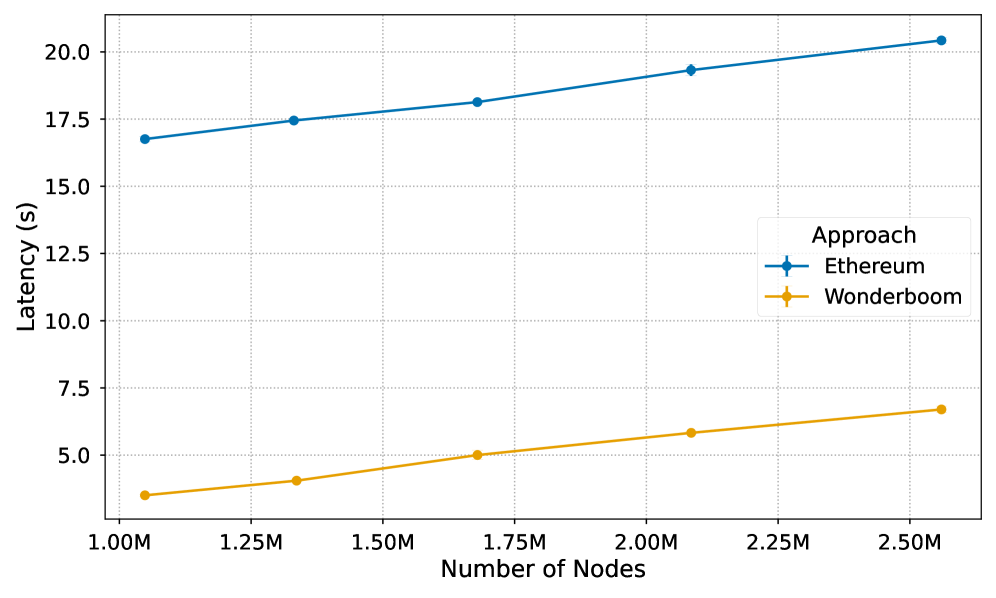
Ethereum’s growing role as a global financial platform-securing hundreds of millions in assets-is paradoxically hampered by slow block finalization times. This limitation stems from the challenges of aggregating signatures from its massive validator set, a problem addressed in ‘Wonderboom — Efficient, and Censorship-Resilient Signature Aggregation for Million Scale Consensus’. This paper introduces Wonderboom, a novel protocol capable of aggregating millions of validator signatures within a single Ethereum slot-achieving up to a 3x faster finality-while also bolstering censorship resistance. Could Wonderboom pave the way for blockchain systems to truly scale and meet the demands of a rapidly growing user base?
The Blockchain Paradigm: From Promise to Peril
Blockchain technology emerged from the creation of Bitcoin as a fundamental departure from traditional centralized transaction systems. Rather than relying on intermediaries like banks, blockchain distributes a digital ledger across a network of computers, making it remarkably resistant to single points of failure or control. Each transaction is bundled into a ‘block’ cryptographically linked to the previous one – hence the ‘chain’ – creating an immutable record. This design ensures both security and transparency; while transactions are publicly verifiable, the identities of participants remain protected through cryptography. The revolutionary aspect lies in establishing trust not through a central authority, but through the consensus of the network itself, opening doors to a wide range of applications beyond cryptocurrency, including supply chain management, voting systems, and secure data storage.
The advent of Ethereum marked a significant evolution beyond Bitcoin’s initial application as a cryptocurrency. By introducing the concept of smart contracts – self-executing agreements written into code – Ethereum unlocked blockchain’s potential for a vast range of decentralized applications, often referred to as dApps. These applications span diverse fields, including decentralized finance (DeFi), supply chain management, and gaming. Crucially, this platform also facilitated the creation of Stablecoins, cryptocurrencies designed to maintain a stable value relative to a traditional asset like the US dollar. By mitigating the price volatility often associated with cryptocurrencies, Stablecoins have become pivotal in enabling wider adoption and use within the burgeoning decentralized ecosystem, providing a bridge between traditional finance and the world of blockchain technology.
Despite their reputation for immutability, contemporary blockchain networks face a growing threat from censorship attacks, which undermine the very principles of decentralized control. These attacks don’t typically target the blockchain’s code itself, but rather the infrastructure around it – specifically, the nodes that validate transactions and the internet service providers (ISPs) that connect them. Coordinated pressure on these entities – through legal demands, economic incentives, or even denial-of-service campaigns – can effectively isolate portions of the network, preventing the confirmation of transactions originating from specific addresses or involving particular smart contracts. While a fully decentralized network should be resilient to such interference, the reality is that node operation remains concentrated in the hands of relatively few actors, and ISPs exert significant control over internet access. This centralization creates vulnerabilities that, if exploited, could stifle free exchange and erode trust in blockchain technology, turning what was intended as a censorship-resistant system into one susceptible to external control.
The Foundations of Trust: Byzantine Fault Tolerance and Consensus
Byzantine Fault Tolerance (BFT) consensus algorithms are foundational to achieving robust finality in decentralized networks by ensuring agreement even when some nodes fail or act maliciously. These algorithms operate on the principle that a system should continue to function correctly as long as a majority of nodes are honest. BFT algorithms typically involve multiple rounds of message exchange and voting amongst network participants to reach consensus on the order and validity of transactions. Different BFT variants, such as Practical Byzantine Fault Tolerance (pBFT) and Tendermint, employ varying strategies to optimize performance and scalability, but all aim to guarantee that once a transaction is confirmed, it cannot be reversed or altered, even in the presence of adversarial actors. The effectiveness of a BFT algorithm is directly correlated with its ability to withstand a certain percentage of faulty nodes – commonly expressed as f \le \frac{n-1}{3}, where ‘n’ represents the total number of nodes and ‘f’ is the maximum number of faulty nodes the system can tolerate.
Traditional consensus mechanisms, such as Proof-of-Work and early Byzantine Fault Tolerance implementations, often exhibit scalability limitations as network size increases, resulting in decreased transaction throughput and higher latency. A core issue is the potential for “Free Riding,” where network participants can validate transactions and benefit from the system without actively contributing sufficient resources-such as computational power or stake-to secure the network. This behavior undermines the incentive structure, potentially leading to decreased security and an increased vulnerability to attacks. The lack of robust mechanisms to prevent or penalize Free Riding necessitates careful economic modeling and the implementation of sophisticated incentive schemes to ensure adequate participation and network health.
Efficient transaction verification and incentivized participation are critical for decentralized network robustness, particularly when facing adversarial actors. Current blockchain implementations, such as Ethereum, demonstrate the practical limitations of achieving rapid finality; the network presently requires approximately 15 minutes to confirm transactions. This delay poses challenges for applications requiring near-instantaneous confirmation, like point-of-sale systems or high-frequency trading platforms. Consequently, research focuses on developing consensus mechanisms that reduce finality times while maintaining security and preventing malicious behavior, including strategies to mitigate free-riding and ensure adequate participation from network validators.
Wonderboom: A Blueprint for Scalable, Censorship-Resistant Blockchains
Wonderboom is a blockchain protocol designed as an extension to Ethereum, focusing on improvements to transaction finality and censorship resistance. Unlike Ethereum’s typical finality timeframe of approximately 15 minutes, Wonderboom achieves finality within two slots-the time it takes to produce two blocks. This represents a substantial reduction in confirmation time, enhancing user experience and reducing the window of opportunity for potential attacks or reversions. The protocol’s architecture is specifically designed to minimize latency in reaching consensus, thereby offering a more responsive and secure blockchain environment compared to Ethereum’s current capabilities.
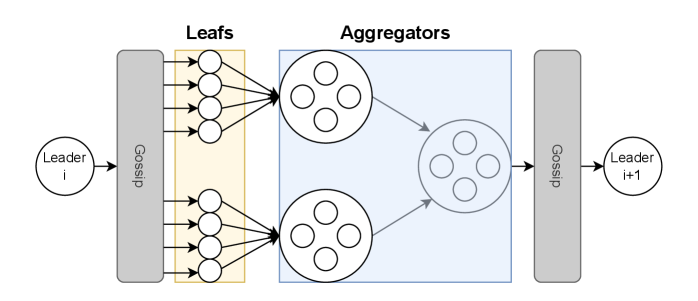
Tree Aggregation is a core component of Wonderboom’s architecture, designed to drastically reduce the data requirements for block verification. This method efficiently combines the digital signatures of multiple validators into a single, aggregated signature. Utilizing techniques such as Boneh-Lynn-Shacham (BLS) Signatures and Public Key Aggregation, Wonderboom can combine signatures from over 1 million validators within a single slot. This process minimizes on-chain data, enabling faster block propagation and verification, and ultimately increasing the network’s throughput and scalability without compromising security.
Wonderboom utilizes Roaring Bitmaps, a compressed data structure, to efficiently store and manipulate large sets of validator data, enabling rapid membership tests and reduced storage overhead as the network scales. To enhance security and mitigate censorship, Wonderboom decouples validator and proposer IP addresses; this separation prevents malicious actors from easily identifying and targeting validators responsible for block production. The architecture supports validator sets scaling to 2 million nodes while maintaining consistent performance through optimized data handling and network communication, exceeding the capacity of many contemporary blockchain systems.
Optimizing the Network: Topology, Communication, and Efficiency
Wonderboom’s architecture incorporates a novel approach called Geographic Self-Selection, deliberately encouraging validators to concentrate in specific geographic locations. This isn’t random; the protocol anticipates that minimizing the physical distance between nodes drastically reduces network latency-the delay in data transmission. By strategically clustering, validators experience faster transaction propagation, meaning information about transactions reaches a larger portion of the network more quickly. This improved communication speed isn’t simply about faster confirmations; it also enhances the network’s resilience against attacks and improves its overall efficiency, as nodes spend less time waiting for information and more time processing legitimate transactions. The system effectively leverages the laws of physics – specifically, the speed of light – to optimize performance and build a more robust blockchain infrastructure.
Wonderboom leverages a Gossip Network to facilitate remarkably efficient and decentralized communication between nodes within the blockchain. This system operates on the principle of probabilistic broadcasting, where each node randomly selects a subset of its peers to share information with, and those peers, in turn, propagate the data further. This cascading effect ensures that information disseminates rapidly across the network – even in the presence of node failures or malicious actors – without relying on a central authority or single point of failure. The inherent redundancy of a Gossip Network bolsters reliability, while its decentralized nature enhances censorship resistance, as no single entity controls the flow of information. Consequently, transaction confirmations and block propagation within Wonderboom are achieved with speed and resilience, contributing significantly to the protocol’s overall scalability and robustness.
Wonderboom distinguishes itself as a blockchain solution by directly addressing both scalability and censorship resistance through a synergistic design. The protocol doesn’t simply enhance one aspect at the expense of the other; instead, it strategically integrates network-level optimizations – such as geographically-informed validator clustering and a robust Gossip Network – with innovative data aggregation techniques. This combination yields a compelling result: comparable censorship resilience to that of Ethereum, traditionally requiring six epochs for confirmation, is achieved within a remarkably reduced timeframe of only two epochs. This accelerated confirmation process significantly improves transaction finality and overall network responsiveness, positioning Wonderboom as a potentially transformative approach to overcoming the limitations of existing blockchain architectures.
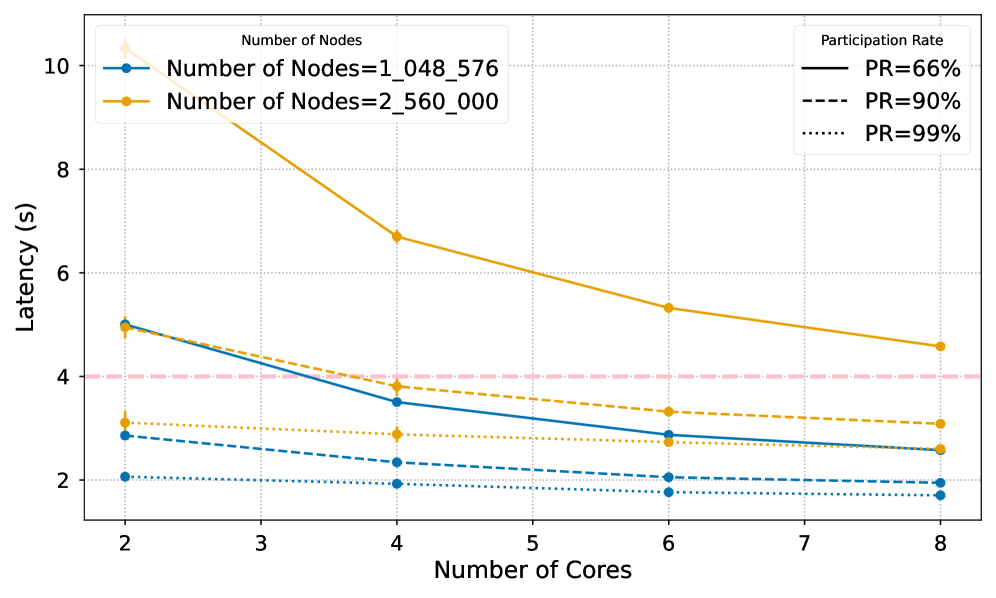
Wonderboom addresses a critical bottleneck in blockchain systems: achieving consensus at scale. The protocol’s efficient signature aggregation directly combats the growing computational burden as validator numbers increase. This pursuit of streamlined efficiency echoes Donald Davies’ sentiment: “Simplicity is the ultimate sophistication.” Abstractions age, principles don’t. Wonderboom isn’t about adding layers of complexity; it’s about distilling the core requirements for secure and scalable consensus into a minimalist design. Every complexity needs an alibi, and this protocol offers a compelling case for its elegant simplicity, enhancing both finality and censorship resistance.
What Remains to be Seen
The presented work addresses a practical bottleneck – the scaling of consensus – through a predictably efficient mechanism. However, efficiency is merely a local optimization. The broader problem of distributed trust remains stubbornly resistant to elegant solutions. Wonderboom demonstrably reduces the bandwidth required for finality, yet it does not fundamentally alter the underlying assumptions regarding validator honesty – or, more accurately, the cost of incentivizing it. The system’s performance relies on a critical mass of participation; the consequences of substantial validator capture or collusion remain an open question, and likely require examination beyond the purely cryptographic.
Future iterations should consider the interplay between signature aggregation and other scaling techniques – sharding, state channels, and optimistic rollups, for example. These are not mutually exclusive solutions, but rather components of a complex system. Furthermore, a rigorous analysis of the protocol’s behavior under adverse network conditions – high latency, packet loss, or targeted denial-of-service attacks – is essential. The pursuit of scalability should not come at the expense of demonstrable robustness.
Ultimately, the true measure of success will not be the number of transactions processed per second, but the degree to which the system resists both technical failure and deliberate manipulation. Emotion is a side effect of structure; clarity is compassion for cognition. A system that prioritizes speed over verifiable integrity is, by definition, incomplete.
Original article: https://arxiv.org/pdf/2602.06655.pdf
Contact the author: https://www.linkedin.com/in/avetisyan/
See also:
- Epic Games Store Free Games for November 6 Are Great for the Busy Holiday Season
- How to Unlock & Upgrade Hobbies in Heartopia
- EUR USD PREDICTION
- Battlefield 6 Open Beta Anti-Cheat Has Weird Issue on PC
- Sony Shuts Down PlayStation Stars Loyalty Program
- The Mandalorian & Grogu Hits A Worrying Star Wars Snag Ahead Of Its Release
- Someone Made a SNES-Like Version of Super Mario Bros. Wonder, and You Can Play it for Free
- Unveiling the Eye Patch Pirate: Oda’s Big Reveal in One Piece’s Elbaf Arc!
- ARC Raiders Player Loses 100k Worth of Items in the Worst Possible Way
- God Of War: Sons Of Sparta – Interactive Map
2026-02-09 18:53