Author: Denis Avetisyan
Researchers have unveiled CVA6-CFI, a RISC-V core featuring hardware-accelerated control-flow integrity extensions designed to bolster security in embedded systems and beyond.
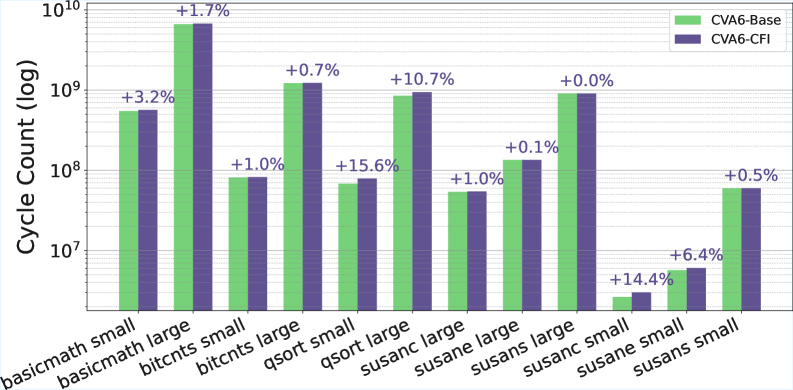
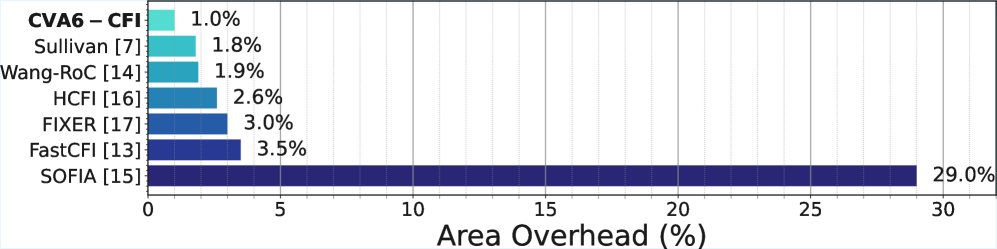
CVA6-CFI achieves standard CFI functionality with minimal area overhead (1.0%) and a moderate performance impact (up to 15.6%) on benchmark tests.
Despite growing sophistication in software security, control-flow hijacking remains a persistent threat to embedded systems. This paper introduces ‘CVA6-CFI: A First Glance at RISC-V Control-Flow Integrity Extensions’, detailing the design, integration, and evaluation of standard RISC-V extensions for Control-Flow Integrity (CFI) within the open-source CVA6 core. Our implementation, leveraging shadow stack and landing pad primitives, achieves hardware-accelerated forward- and backward-edge protection with a minimal area overhead of 1.0% and a performance impact of up to 15.6% on automotive benchmarks. Will these CFI extensions become a standard feature in future RISC-V implementations seeking robust security for embedded applications?
The Rising Tide of Control-Flow Attacks
Contemporary software faces a rising tide of control-flow hijacking attacks, a consequence of increasingly complex codebases and expanding attack surfaces. These attacks exploit vulnerabilities in how a program manages its execution path, allowing malicious actors to redirect the program to unintended, and often harmful, code locations. Attackers commonly leverage weaknesses like buffer overflows, format string bugs, and return-oriented programming (ROP) to overwrite critical program data, effectively seizing control of the application’s flow. The prevalence of just-in-time (JIT) compilation and dynamic code generation further exacerbates the issue, introducing new avenues for exploitation. Consequently, software reliant on predictable execution, such as operating systems, browsers, and security-critical applications, are particularly susceptible, necessitating robust defenses against these increasingly sophisticated threats.
Contemporary software security architectures, while long considered foundational, are increasingly challenged by the ingenuity of modern exploitation techniques. Attackers are no longer reliant on simple buffer overflows; instead, they employ complex strategies like Return-Oriented Programming (ROP) and Jump-Oriented Programming (JOP) to bypass traditional defenses such as Data Execution Prevention (DEP) and Address Space Layout Randomization (ASLR). These advanced methods cleverly repurpose existing code fragments within a program to achieve malicious goals, rendering conventional safeguards less effective. Consequently, the field demands a shift towards more robust and proactive security paradigms, necessitating innovative defenses that can anticipate and neutralize sophisticated attacks before they compromise system integrity. Research is actively focused on techniques like fine-grained control-flow integrity, shadow stacks, and capability-based security to address these evolving threats and bolster software resilience.
Control-Flow Integrity (CFI) represents a foundational security principle, aiming to prevent malicious redirection of a program’s execution flow – a common tactic in modern exploits. The concept hinges on establishing a strict policy defining legitimate execution paths, effectively creating a “safe zone” for code execution. However, realizing this principle in practice proves remarkably challenging. Precisely defining these valid paths requires deep program analysis, often complicated by dynamic code generation, indirect function calls, and the inherent complexity of real-world applications. Furthermore, even with a defined policy, enforcing it without introducing substantial performance penalties – a critical barrier to widespread adoption – remains a significant hurdle for developers and security researchers alike. Consequently, while CFI offers a powerful defense against control-flow hijacking, its effective implementation demands continuous innovation to balance security with practicality.
Despite the recognized importance of Control-Flow Integrity (CFI) as a security measure, widespread adoption faces a substantial hurdle: performance overhead. Current CFI implementations often introduce significant computational costs, stemming from the rigorous checks required to validate every program control-flow transition. These checks, while crucial for security, can drastically slow down execution, particularly in resource-constrained environments like mobile devices, embedded systems, and even within performance-critical server applications. The overhead arises from the need to frequently consult shadow stacks, utilize fine-grained policy enforcement, or perform complex validation routines, creating a trade-off between security and usability. Consequently, developers frequently prioritize performance, leaving systems vulnerable, or resort to less comprehensive CFI approaches that offer reduced protection. Research continues to explore methods for minimizing this performance penalty, including hardware acceleration and optimized policy representations, but a truly lightweight and effective CFI solution remains a key challenge.
RISC-V: A Foundation for Extensible Security
The RISC-V instruction set architecture (ISA) is designed with extensibility as a core principle, enabling the modular addition of features without compromising existing code. This flexibility is achieved through a base ISA and a standardized extension mechanism, allowing developers to incorporate advanced security features like Control-Flow Integrity (CFI) as optional modules. Unlike fixed ISAs, RISC-V’s open nature and customizable extensions facilitate the implementation of diverse security solutions tailored to specific application requirements and threat models. The architecture supports both hardware and software implementations of security features, offering a balance between performance and flexibility, and enabling a layered approach to system security.
The Zicfilp and Zicfiss extensions to the RISC-V ISA implement Control-Flow Integrity (CFI) through distinct hardware mechanisms. Zicfilp utilizes landing pads – specific instruction sequences inserted at potential indirect branch targets – to verify the validity of the target address at runtime. These landing pads check against a pre-defined set of allowed targets. Conversely, Zicfiss employs a shadow stack, a separate memory region mirroring the call stack, to store return addresses. This shadow stack is used to validate return instructions, preventing attackers from manipulating the return address on the standard call stack – a core technique in return-oriented programming (ROP) exploits. Both extensions operate at the hardware level, minimizing performance overhead compared to purely software-based CFI implementations.
The Zicfilp extension enables forward-edge Control-Flow Integrity (CFI) by verifying the validity of indirect jump targets at runtime. This is achieved through the use of labeled landing pads, special instructions inserted into the code to mark legitimate target addresses. When an indirect jump occurs, the target address is compared against the labels associated with the landing pad. If the target matches a valid label, the jump proceeds normally; otherwise, a violation is detected, and the program execution is halted. This mechanism effectively prevents attackers from redirecting control flow to arbitrary addresses by ensuring that indirect branches only land on pre-approved locations, mitigating a class of exploitation techniques.
The Zicfiss extension implements backward-edge Control-Flow Integrity (CFI) by utilizing a shadow stack, a separate stack dedicated to storing return addresses. During a function call, the return address is duplicated – stored on both the standard stack and the shadow stack. Upon function return, the return address is popped from both stacks and compared; a mismatch indicates potential malicious manipulation, triggering a fault. This mechanism effectively mitigates Return-Oriented Programming (ROP) attacks by preventing attackers from redirecting control flow to arbitrary code gadgets by overwriting return addresses on the standard stack, as any alteration will be detected during the comparison process.
CVA6-CFI: An Integrated and Validated Core
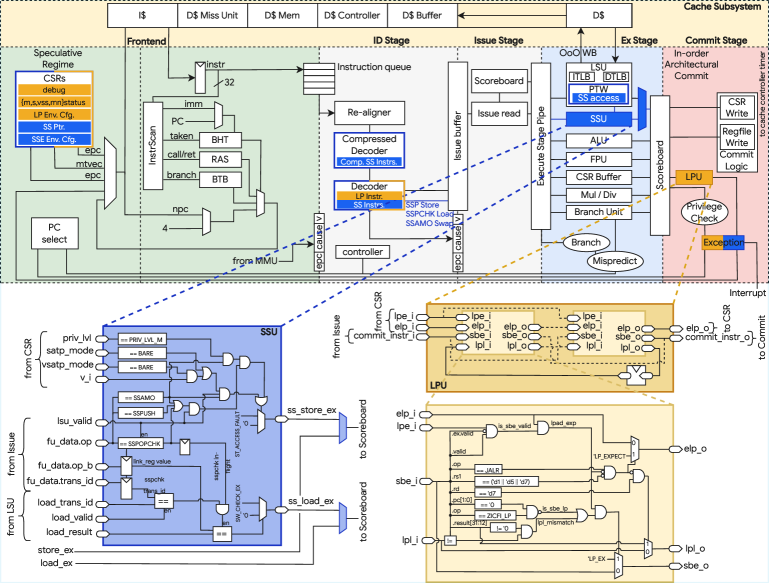
The CVA6-CFI core is a full implementation of the Control-Flow Integrity (CFI) extensions for the RISC-V instruction set architecture, built upon the foundation of the established CVA6 core. This extension incorporates the necessary hardware to enforce CFI, preventing exploitation of control-flow hijacking vulnerabilities. By extending a widely adopted core, the CVA6-CFI facilitates ease of integration and validation within existing RISC-V ecosystems and designs. The implementation aims to provide a practical and readily deployable solution for enhancing system security through hardware-based CFI enforcement.
The CVA6-CFI core utilizes the Zicfilp and Zicfiss RISC-V extensions to provide comprehensive Control-Flow Integrity (CFI) protection. Zicfilp focuses on forward-edge CFI, preventing malicious redirection to unintended targets, while Zicfiss addresses backward-edge CFI violations, such as return-oriented programming (ROP) attacks. These extensions operate by verifying the validity of control-flow transitions against a pre-defined policy, ensuring that execution remains within expected program logic and preventing exploitation of control-flow hijacking vulnerabilities. Combined, Zicfilp and Zicfiss offer robust defense against a wide range of CFI attacks by validating both direct and indirect branches.
The CVA6-CFI core utilizes the `sspopchk` and `ssamoswap` instructions for efficient shadow stack management, which is central to Control-Flow Integrity (CFI) enforcement. The `sspopchk` instruction validates the return address against the shadow stack during function returns, detecting potential control-flow hijacking attempts. `ssamoswap` atomically swaps the current shadow stack pointer with a new value, facilitating context switching and ensuring consistent shadow stack management across different execution contexts. These instructions minimize the performance impact of CFI checks by providing dedicated hardware support for shadow stack operations, as opposed to relying on software-based emulation.
Performance analysis of the CVA6-CFI core, conducted using the MiBench benchmark suite, indicates a low implementation cost and acceptable performance impact. Area overhead was measured at 1.0%, representing the additional hardware resources required for CFI functionality. Performance overhead, specifically when executing the MiBench automotive subset, reached a maximum of 15.6%. These results demonstrate the practicality of integrating the CFI extensions into the CVA6 core without incurring excessive penalties to area or performance, validating the design for resource-constrained applications.
Beyond Validation: Real-World Implementation & Compatibility
The CVA6-CFI core’s fabrication leverages the GF22FDX process technology, a fully depleted silicon-on-insulator (FD-SOI) process renowned for its low power consumption and high performance. This choice demonstrably positions the core as compatible with currently available and widely utilized manufacturing infrastructure, bypassing the need for specialized or experimental fabrication runs. Utilizing GF22FDX allows for efficient production scaling and integration into existing supply chains, crucial for practical deployment across diverse embedded systems. The successful synthesis with this process validates the design’s readiness for real-world implementation and underscores its potential for broad adoption in applications ranging from resource-constrained IoT devices to safety-critical automotive systems, where reliable and scalable manufacturing is paramount.
The CVA6-CFI core’s inherent adaptability positions it as a versatile component for diverse embedded systems. Its design isn’t rigidly tailored to a single application; instead, it scales effectively from the resource-constrained environments of Internet of Things (IoT) devices – where minimizing power consumption and footprint are paramount – to the stringent safety and performance demands of automotive systems. This broad compatibility stems from configurable features and an optimized instruction set, allowing developers to tailor the core’s functionality to meet specific requirements without substantial redesign. Consequently, the CVA6-CFI offers a unified platform for secure computation across a spectrum of embedded applications, streamlining development and reducing time-to-market for innovative devices.
Hardware-level implementation of Control-Flow Integrity (CFI) presents a marked improvement over software-only approaches by shifting the burden of security checks from runtime to the processor itself. Traditional software CFI relies heavily on intricate runtime checks to verify the validity of indirect branches, introducing performance overhead and potential vulnerabilities if those checks are bypassed or compromised. By embedding CFI directly into the processor’s design, the CVA6-CFI core achieves a more robust and efficient security mechanism; validation occurs as part of the instruction execution pipeline, minimizing performance penalties and eliminating the risk of runtime manipulation. This architectural approach results in a system where security isn’t an added layer of software, but an inherent property of the hardware, offering a more dependable safeguard against control-flow hijacking attacks.
Performance evaluations of the CVA6-CFI implementation, conducted using the MiBench benchmark suite, reveal a modest increase in code size – ranging from 7.6 to 9.2 percent. This translates to an absolute overhead of 22 to 23 kilobytes, a quantifiable impact demonstrating the practical cost of hardware-based control-flow integrity. Importantly, despite this addition, the CFI instructions themselves constitute less than 0.5% of the total instructions executed during benchmark runs, indicating a minimal runtime performance penalty and suggesting that the hardware implementation efficiently manages the added security checks. This balance between code size impact and runtime efficiency positions CVA6-CFI as a viable security enhancement for resource-constrained embedded systems.
CVA6-CFI prioritizes streamlined security. The design elegantly addresses control-flow integrity with a minimal footprint – a mere 1.0% area overhead. This echoes a principle of efficient design; abstractions age, principles don’t. Marvin Minsky observed, “The more we learn about the brain, the more we realize how much of what we think is automatic.” Similarly, CVA6-CFI automates essential security checks, reducing the burden on the core and minimizing performance impact. Every complexity needs an alibi, and this core provides a clear justification for its additions – robust protection without undue cost.
Further Refinements
The presented work establishes a baseline. A functional, if not elegant, implementation of control-flow integrity within the RISC-V ecosystem. The achieved area overhead is, predictably, the more readily quantifiable success. The performance penalty, while moderate, invites scrutiny. It is not merely a matter of shaving cycles; it is a question of architectural cost. Each hardware acceleration introduces a trade-off, a binding commitment. Future iterations must prioritize discerning which threats warrant dedicated silicon, and which are adequately addressed through software mitigation.
The current study focuses on a limited benchmark suite. Embedded systems, the stated target, present a far more fractured landscape. Real-world deployments exhibit constraints and peculiarities that standardized tests rarely capture. A truly robust evaluation demands exploration of diverse architectures, memory configurations, and operational profiles. Such an investigation will likely reveal subtle interactions, unexpected bottlenecks, and the limitations of a universally applied solution.
Ultimately, the challenge lies not in building more complex defenses, but in achieving a more efficient simplicity. The pursuit of perfect security is a fool’s errand. The goal should be to minimize the attack surface, reduce the cost of compromise, and accept a calculated level of risk. A refined architecture will not eliminate vulnerabilities; it will merely raise the bar, forcing adversaries to expend more effort for diminishing returns.
Original article: https://arxiv.org/pdf/2602.04991.pdf
Contact the author: https://www.linkedin.com/in/avetisyan/
See also:
- God Of War: Sons Of Sparta – Interactive Map
- Someone Made a SNES-Like Version of Super Mario Bros. Wonder, and You Can Play it for Free
- Overwatch is Nerfing One of Its New Heroes From Reign of Talon Season 1
- One Piece Chapter 1175 Preview, Release Date, And What To Expect
- Meet the Tarot Club’s Mightiest: Ranking Lord Of Mysteries’ Most Powerful Beyonders
- How to Unlock & Upgrade Hobbies in Heartopia
- Epic Games Store Free Games for November 6 Are Great for the Busy Holiday Season
- Sony Shuts Down PlayStation Stars Loyalty Program
- The Mandalorian & Grogu Hits A Worrying Star Wars Snag Ahead Of Its Release
- Unveiling the Eye Patch Pirate: Oda’s Big Reveal in One Piece’s Elbaf Arc!
2026-02-08 05:50