Author: Denis Avetisyan
A new framework leverages fuzzy logic and zero-knowledge proofs to fortify data privacy and security in decentralized edge computing environments.
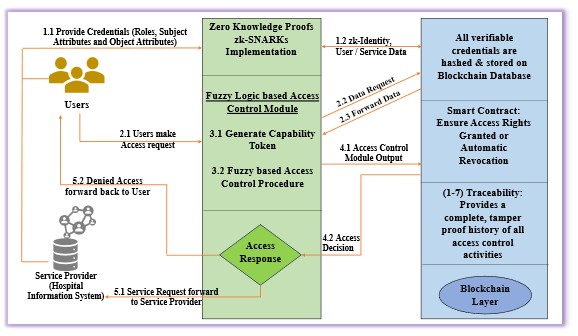
This review details Fuzzychain-edge, a novel access control model integrating blockchain, fuzzy logic, and zero-knowledge proofs for enhanced IoT security, particularly within healthcare applications.
While the proliferation of IoT devices in edge computing environments promises advancements in areas like healthcare, it simultaneously exacerbates critical vulnerabilities in data privacy and security. This research introduces ‘Fuzzychain-edge: A novel Fuzzy logic-based adaptive Access control model for Blockchain in Edge Computing’, a framework designed to address these limitations through the integration of blockchain, zero-knowledge proofs, and fuzzy logic. By enabling adaptive, context-aware access control and ensuring data transparency, the proposed model significantly enhances security and user trust in sensitive IoT applications. Could this approach pave the way for truly secure and privacy-preserving decentralized systems in critical domains beyond healthcare?
The Expanding Digital Landscape: Security and Privacy Imperatives
The exponential growth of the Internet of Things is unleashing a deluge of data, presenting formidable challenges to both data security and individual privacy. Billions of interconnected devices – from smart home appliances to industrial sensors – continuously collect, transmit, and store information, creating an expansive and increasingly vulnerable attack surface. This unprecedented data generation strains existing security infrastructures, as traditional methods are often ill-equipped to handle the scale, diversity, and dynamic nature of IoT environments. Beyond the sheer volume, the sensitive nature of much of this data – including personal habits, location information, and even biometric data – amplifies the risks, potentially exposing individuals to identity theft, surveillance, and other malicious activities. Consequently, securing this expanding digital frontier requires innovative approaches to data encryption, access control, and threat detection, alongside robust regulatory frameworks to protect user privacy.
Conventional cybersecurity approaches, designed for static networks with clearly defined perimeters, are proving inadequate for the Internet of Things. IoT environments are characterized by a vast number of diverse devices, often resource-constrained and deployed in unpredictable locations, creating a constantly shifting attack surface. These devices frequently lack robust built-in security features and are susceptible to compromise, while their interconnectedness means a single vulnerability can quickly cascade across an entire system. Consequently, static rule-based systems and signature-based detection methods struggle to keep pace with evolving threats. This necessitates a move towards more adaptive and intelligent security solutions, such as machine learning-driven anomaly detection, decentralized security architectures, and proactive threat hunting, capable of understanding device behavior and responding to threats in real-time within these dynamic ecosystems.
The increasing integration of Internet of Things devices within healthcare environments introduces uniquely critical security vulnerabilities. These systems, ranging from wearable health monitors to remotely controlled drug delivery mechanisms, routinely collect, store, and transmit highly sensitive patient data – including personally identifiable information, medical histories, and real-time physiological readings. Consequently, a breach in a healthcare IoT system doesn’t simply expose data; it can directly compromise patient safety and wellbeing. This necessitates the implementation of robust access control mechanisms that go beyond traditional cybersecurity protocols, incorporating multi-factor authentication, granular permission settings, and continuous monitoring to ensure only authorized personnel and devices can access protected health information. Furthermore, data encryption both in transit and at rest is paramount, alongside adherence to stringent regulatory frameworks like HIPAA to mitigate risks and maintain patient trust.
Decentralized Access Control: The Foundation of Trust
Blockchain technology provides a secure and tamper-resistant foundation for data management through its inherent cryptographic properties and distributed consensus mechanisms. Data is structured into blocks chained together chronologically, with each block containing a hash of the previous block, creating an immutable audit trail. Any alteration to a block necessitates changing all subsequent hashes, which is computationally infeasible without controlling a majority of the network. This immutability enhances data security by preventing unauthorized modification and strengthens data privacy by ensuring a verifiable record of access and changes, minimizing the risk of data breaches and supporting compliance with data protection regulations. The distributed nature further mitigates single points of failure and censorship, bolstering the overall resilience of the system.
Smart contracts facilitate automated enforcement of access control policies by defining pre-programmed conditions that govern data access. These self-executing contracts eliminate the need for manual intervention in authorization processes, thereby minimizing the potential for human error and associated security vulnerabilities. The granularity of permissions is significantly enhanced as smart contracts allow for the specification of access rights at a highly detailed level – for example, granting read-only access to specific data fields or restricting access based on time, location, or other contextual factors. This fine-grained control improves data security and enables compliance with complex regulatory requirements by ensuring that only authorized entities can access sensitive information, and only under defined circumstances.
Zero-Knowledge Proofs (ZKPs) are a cryptographic method allowing one party (the prover) to demonstrate to another party (the verifier) that a statement is true, without revealing any information beyond the fact that the statement is true. This is achieved through interactive or non-interactive protocols where the verifier can be convinced of the statement’s validity without learning the witness – the underlying data that makes the statement true. Applications requiring high data privacy, such as identity verification, secure authentication, and confidential transactions, benefit significantly from ZKPs as they minimize data exposure. Several ZKP schemes exist, including zk-SNARKs, zk-STARKs, and Bulletproofs, each offering different trade-offs between proof size, verification time, and computational cost.
Data integrity and reliability in blockchain-based access control systems are maintained through the implementation of consensus algorithms. Simulations conducted demonstrate performance variations between different algorithms: the Solo protocol achieved an average latency of 300 ms. This represents a 25% improvement over the Raft protocol, which recorded an average latency of 400 ms. A hybrid approach, utilizing the Solo-Raft protocol, resulted in an average latency of 430 ms, indicating a 30.23% decrease in speed compared to the Solo protocol and a 7.5% decrease compared to the Raft protocol. These results suggest that the Solo protocol offers the most efficient latency for maintaining consensus within these systems, though alternative implementations may prioritize other performance characteristics.
Granular Permissions: Adapting Access Control to a Dynamic World
Traditional Role-Based Access Control (RBAC) assigns permissions based on predefined roles, which can prove insufficient in dynamic Internet of Things (IoT) environments. These environments are characterized by a large number of devices, frequent changes in device status and data sensitivity, and diverse user access needs. RBAC’s reliance on static roles often results in over-provisioning of permissions – granting users more access than necessary – or under-provisioning, hindering legitimate operations. The inflexibility of RBAC complicates managing access for temporary or conditional access scenarios common in IoT, and its broad permissions increase the potential impact of compromised accounts or malicious devices. Consequently, more granular and adaptable access control mechanisms are required to address the specific challenges posed by the scale and dynamism of IoT deployments.
Attribute-Based Access Control (ABAC) departs from traditional role-based systems by defining access permissions based on attributes associated with users, resources, and the environment. These attributes can include user department, resource classification, data sensitivity level, and time of day. Instead of assigning permissions to roles, ABAC policies directly evaluate these attributes to determine access, allowing for highly granular and context-aware control. This approach offers increased flexibility as permissions are not tied to static roles, simplifying management and adaptation to dynamic environments where user attributes or resource characteristics change frequently. Policies are typically expressed as rules, such as “Allow access to documents classified as ‘Confidential’ to users with a ‘Security Clearance’ attribute value of ‘Top Secret’ and a ‘Department’ attribute of ‘Research’”.
Capability-Based Access Control (CBAC) operates by granting access not based on the identity of the requesting subject, but on possession of a capability – an unforgeable token representing permission to perform a specific action on a specific object. Unlike Access Control Lists (ACLs) or Role-Based Access Control (RBAC), capabilities are directly held by the subject and are passed between principals as needed. This approach inherently limits the scope of access, as a compromised subject can only perform actions for which it possesses a valid capability, minimizing the potential for privilege escalation. Capabilities can be delegated, allowing temporary or limited access without modifying core permissions, and revocation is achieved by simply removing the capability. The system relies on the unforgeability of capabilities, often implemented through cryptographic signatures or hardware security modules.
Fuzzy logic enhances access control schemes by introducing the capacity to evaluate permissions based on degrees of truth rather than strict binary conditions. Traditional systems require clearly defined criteria for access; fuzzy logic allows policies to incorporate imprecise or uncertain data, such as time of day, location proximity, or device sensor readings. This enables context-aware decision-making where access is granted or denied based on a calculated membership value within defined fuzzy sets – for example, a “high security risk” set based on multiple contributing factors. The resulting policies are adaptive, allowing for more granular control and a reduction in both false positives and false negatives compared to rigid, rule-based systems. This approach is particularly beneficial in dynamic environments where conditions are constantly changing and absolute certainty is rarely achievable.
Optimizing Deployment: Balancing Scale with Responsiveness
Cloud computing offers a powerful and readily scalable infrastructure for the centralized management of access control policies, proving particularly beneficial for organizations with geographically dispersed resources or fluctuating demands. However, this centralized approach inherently introduces latency – the delay between a request and its fulfillment – which can significantly impede the performance of real-time applications. Every access request must travel to the cloud for authorization, and the return trip adds to the overall delay, creating bottlenecks in scenarios requiring immediate responses, such as autonomous systems, industrial automation, or augmented reality. This trade-off between scalability and responsiveness necessitates a careful consideration of application requirements when designing access control systems, prompting exploration into distributed and edge-based solutions that can minimize latency while maintaining robust security.
Edge computing addresses the limitations of centralized cloud infrastructure by strategically positioning computational resources closer to the origin of data. This proximity significantly reduces latency, as data doesn’t need to travel long distances to a remote server for processing, thereby enhancing the responsiveness of applications – a critical factor for real-time services like autonomous vehicles or augmented reality. Beyond speed, edge computing conserves bandwidth by processing data locally and transmitting only essential information to the cloud, lowering communication costs and network congestion. This distributed approach isn’t merely about faster responses; it’s about enabling a new class of applications that demand both immediate action and efficient resource utilization, fundamentally altering how data is handled and value is extracted.
A synergistic integration of edge and cloud computing architectures offers a compelling solution for modern access control systems, skillfully balancing the demands of scalability, responsiveness, and robust security. By strategically distributing processing tasks, critical decisions can be made rapidly at the network edge, minimizing latency and preserving bandwidth – vital for real-time applications and resource-constrained environments. Simultaneously, the cloud provides a centralized, scalable infrastructure for managing complex policies, conducting global audits, and ensuring consistent enforcement. This hybrid approach avoids the limitations of relying solely on either paradigm; the edge handles immediate, localized access requests, while the cloud provides the overarching governance and long-term data management, ultimately creating a more resilient and adaptable security framework.
Efficient privacy-preserving access control at the edge relies on zero-knowledge proofs, and a novel model integrating zk-SNARKs, fuzzy logic, and blockchain technology has demonstrated significant performance gains. This approach achieved a throughput of 900 transactions per second (TPS) at a send rate of 300 requests per second, representing a substantial improvement over the established baseline of 200 TPS. While incorporating these advanced security features did introduce a slight increase in transaction latency, the average observed across varying send rates was only 16.5%. These results indicate a viable pathway for deploying secure and scalable access control mechanisms directly at the network edge, balancing the need for privacy with high-performance requirements.
The pursuit of robust access control, as detailed in the proposed Fuzzychain-edge framework, mirrors a fundamental tenet of elegant design. It strips away unnecessary complexity to reveal the core mechanics of security. G.H. Hardy observed, “The most powerful weapon in the hands of a mathematician is simplicity.” This sentiment resonates deeply with the article’s integration of fuzzy logic into a blockchain-based system. By employing fuzzy logic, the model navigates the nuanced requirements of healthcare IoT security – moving beyond rigid, binary access permissions to a system that acknowledges degrees of trust and risk. This isn’t merely about adding another layer of technology; it’s about refining the existing structure until only the essential elements remain, creating a system as self-evident as gravity.
Where Do We Go From Here?
The integration of blockchain, zero-knowledge proofs, and fuzzy logic, as demonstrated, addresses a specific anxiety regarding data access in edge computing. Yet, complication rarely yields simplification. This framework, while theoretically sound, introduces its own set of dependencies. The computational cost of fuzzy inference, coupled with the cryptographic demands of zero-knowledge proofs, remains a significant obstacle, especially when scaled across resource-constrained IoT devices. A truly useful solution must demonstrate efficiency, not merely possibility.
Future work should not focus on adding layers of complexity – more logic, more cryptography – but on ruthless subtraction. Can the fuzzy logic component be streamlined, perhaps through pre-computed inference tables or a reduction in rule complexity, without sacrificing necessary nuance? More importantly, the reliance on a permissioned blockchain should be critically re-examined. The benefits of centralized control must be weighed against the very privacy concerns this model attempts to alleviate.
Ultimately, the true test lies not in elegant architectures, but in demonstrable resilience. The system must withstand not just theoretical attacks, but the messy, unpredictable reality of deployment. If it cannot be explained, implemented, and maintained with relative simplicity, then it remains an interesting exercise, and little more.
Original article: https://arxiv.org/pdf/2601.10105.pdf
Contact the author: https://www.linkedin.com/in/avetisyan/
See also:
- God Of War: Sons Of Sparta – Interactive Map
- Poppy Playtime 5: Battery Locations & Locker Code for Huggy Escape Room
- Overwatch is Nerfing One of Its New Heroes From Reign of Talon Season 1
- Someone Made a SNES-Like Version of Super Mario Bros. Wonder, and You Can Play it for Free
- Poppy Playtime Chapter 5: Engineering Workshop Locker Keypad Code Guide
- One Piece Chapter 1175 Preview, Release Date, And What To Expect
- Meet the Tarot Club’s Mightiest: Ranking Lord Of Mysteries’ Most Powerful Beyonders
- Why Aave is Making Waves with $1B in Tokenized Assets – You Won’t Believe This!
- Bleach: Rebirth of Souls Shocks Fans With 8 Missing Icons!
- All Kamurocho Locker Keys in Yakuza Kiwami 3
2026-01-17 13:54