Author: Denis Avetisyan
A comprehensive framework leverages trusted execution, semantic technologies, and blockchain to fortify the rapidly expanding Internet of Things.
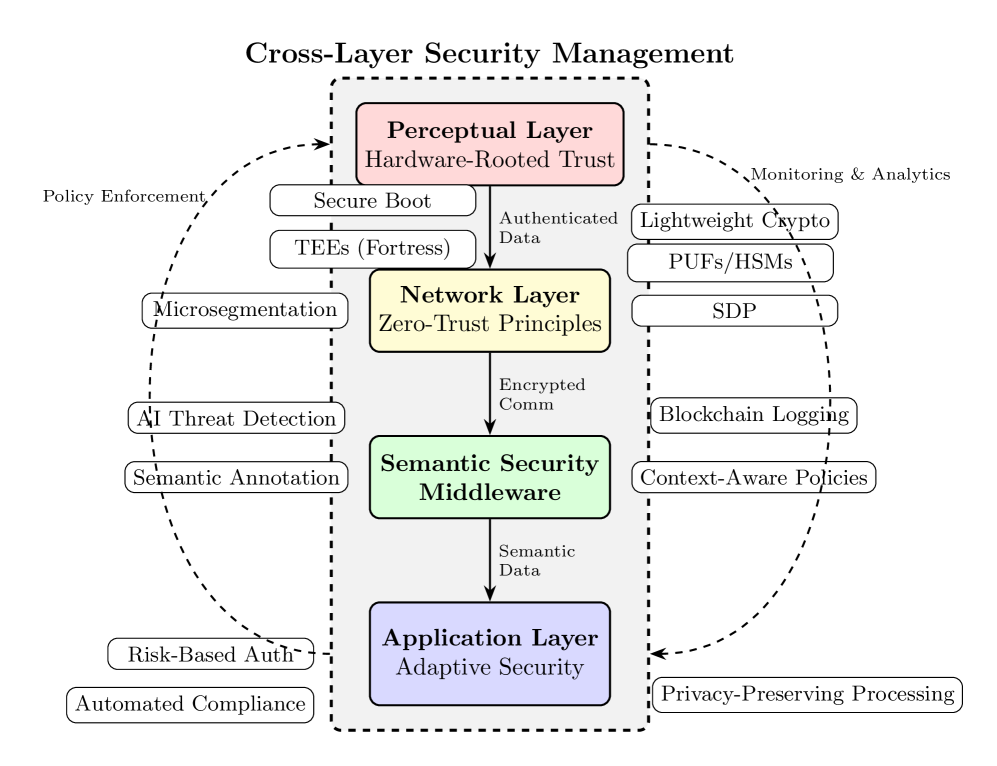
This review proposes an integrated architecture combining trusted execution environments, semantic middleware, and blockchain to address IoT vulnerabilities and enhance security across all layers.
Despite the increasing connectivity of the Internet of Things (IoT), inherent vulnerabilities continue to challenge the security and trustworthiness of these systems. This paper, ‘Architecting Trust: A Framework for Secure IoT Systems Through Trusted Execution and Semantic Middleware’, proposes a comprehensive, layered security architecture integrating Trusted Execution Environments, semantic middleware, and blockchain technologies to address these challenges. The framework achieves cross-layer security by establishing hardware-rooted trust, implementing zero-trust network principles, and leveraging semantic security mechanisms at the application level, while considering resource constraints and regulatory compliance. Will this integrated approach pave the way for more robust and resilient IoT deployments in increasingly complex environments?
The Expanding Threat Surface of Interconnected Devices
The exponential growth of interconnected devices, commonly known as the Internet of Things, has dramatically expanded the potential avenues for malicious attacks, far outpacing the capacity of conventional security measures. Each new device – from smart thermostats and refrigerators to industrial sensors and medical equipment – represents a potential entry point for cybercriminals. This isn’t simply a matter of increased numbers; the sheer diversity of these devices, often with limited built-in security features and lengthy update cycles, creates a fragmented and vulnerable ecosystem. Traditional security strategies, designed to protect a defined network perimeter, struggle to contain threats originating within the network from compromised IoT devices, necessitating a fundamental rethinking of how digital defenses are constructed and maintained. The resulting attack surface is unprecedented in its scale and complexity, demanding innovative approaches to threat detection and response.
Traditional network security strategies, built upon the concept of a fortified perimeter, are proving inadequate in the face of the expanding Internet of Things. These models presume that anything inside the network is trustworthy, a dangerous assumption when countless IoT devices – often with weak default security or limited update capabilities – are present. Once a compromised device breaches this perimeter, it can move laterally within the network, accessing sensitive data and critical systems undetected. This internal threat is exacerbated by the sheer volume of IoT devices, creating numerous potential entry points and overwhelming traditional monitoring capabilities. Consequently, organizations are finding it increasingly difficult to differentiate between legitimate traffic and malicious activity originating from within their own networks, rendering perimeter-based defenses largely ineffective against the evolving IoT threat landscape.
Modern data privacy regulations, such as the General Data Protection Regulation (GDPR) in Europe and the California Consumer Privacy Act (CCPA), significantly impact Internet of Things (IoT) deployments by mandating stringent data handling protocols. These laws aren’t merely about compliance; they necessitate a fundamental rethinking of how IoT devices collect, process, and store user data. Organizations are now legally obligated to minimize data collection, ensuring only necessary information is gathered and retained for specified, legitimate purposes. Furthermore, robust security measures are required to protect this data from unauthorized access, and individuals are granted rights to access, rectify, and erase their personal information. Failing to adhere to these regulations can result in substantial financial penalties and reputational damage, driving a shift towards privacy-by-design principles and proactive data governance within the expanding IoT ecosystem.
The escalating complexity of interconnected devices necessitates a departure from conventional security approaches, demanding a foundational shift towards zero-trust architectures. This paradigm assumes no implicit trust is granted to any device or user, regardless of network location, and continuously verifies every access request. Complementing this is the critical implementation of proactive threat intelligence – the continuous gathering, analysis, and dissemination of information about potential and emerging threats specifically targeting IoT ecosystems. Rather than reacting to breaches, this approach anticipates malicious activity by identifying vulnerabilities, tracking attacker tactics, and leveraging predictive analytics. Successfully integrating zero-trust principles with robust threat intelligence enables organizations to minimize the attack surface, rapidly detect anomalies, and dynamically adapt security measures – ultimately bolstering resilience against the ever-evolving threat landscape within the Internet of Things.
Hardware-Rooted Security: Establishing Trust at the Foundation
Trusted Execution Environments (TEEs) establish a secure, isolated operating system environment within the main processor. This isolation is achieved through hardware-based virtualization and memory separation, preventing unauthorized access from other software components, including the rich operating system and applications. TEEs are designed to protect sensitive data and operations – such as cryptographic key management, digital rights management, and secure boot processes – from software-based attacks. By executing critical tasks within this enclave, even a fully compromised operating system cannot directly access or manipulate the protected assets. The TEE typically has a smaller attack surface than a general-purpose operating system, enhancing overall system security.
ARM TrustZone establishes a foundational Trusted Execution Environment (TEE) by partitioning the ARM processor into a secure world and a normal world. This hardware-based isolation prevents unauthorized access to sensitive data and code, even if the normal operating system is compromised. While TrustZone provides core TEE functionality, designs like Fortress build upon this foundation by specifically enhancing the security of peripheral interfaces. Fortress achieves this through dedicated security monitors and secure boot mechanisms for peripherals, mitigating threats such as rogue devices or compromised DMA transfers. This peripheral-focused approach complements TrustZone’s CPU-centric security, creating a more robust and comprehensive TEE solution.
Hardware Security Modules (HSMs) integrated within a Trusted Execution Environment (TEE) provide a dedicated, tamper-resistant environment for managing cryptographic keys and performing sensitive cryptographic operations. These modules offload computationally intensive tasks – such as asymmetric encryption, digital signature generation, and key storage – from the main processor, enhancing both security and performance. By isolating key material and cryptographic processes within the HSM, the risk of compromise through software vulnerabilities or side-channel attacks is significantly reduced. Modern HSMs often include features like true random number generation and physical security mechanisms to further protect cryptographic assets, and can be implemented using dedicated hardware or as a secure enclave within a system-on-a-chip.
The increasing deployment of IoT devices with limited processing power and battery life necessitates the use of lightweight cryptographic algorithms within Trusted Execution Environments (TEEs). These algorithms minimize the computational burden and energy consumption associated with securing sensitive data and operations. Furthermore, the adoption of post-quantum cryptography within TEEs is crucial for future-proofing against potential attacks from quantum computers. It is important to note that TEE initialization itself introduces performance overhead; testing demonstrates an 8.2% energy overhead and a processing delay of 45 milliseconds during the boot sequence.
Semantic Security: A Shared Language for Trustworthy Data
Semantic security policies leverage ontologies – formal representations of knowledge – to establish a consistent and unambiguous interpretation of security rules. This approach addresses the challenges of interoperability in heterogeneous IoT environments by defining security concepts and relationships in a machine-readable format. Unlike traditional rule-based systems susceptible to inconsistencies due to varying interpretations, ontology-driven policies ensure that all devices, regardless of manufacturer or operating system, apply security protocols uniformly. The formalized definitions within the ontology explicitly state the meaning of security terms and the conditions for policy enforcement, minimizing ambiguity and enabling automated policy evaluation across diverse platforms and data formats.
The Canonical Ontology and Web Ontology Language (OWL) facilitate secure data exchange by establishing a shared, machine-readable vocabulary for describing data and security policies. OWL, built upon Resource Description Framework (RDF), allows for the formal definition of concepts, relationships, and constraints within a specific domain, ensuring consistent interpretation across heterogeneous systems. This standardization minimizes ambiguity and errors inherent in natural language-based security rules, enabling automated reasoning and validation of access control policies. The use of a canonical ontology ensures that data elements are uniquely identified and understood, reducing the risk of misinterpretation or unauthorized access during data transmission and storage, and supports interoperability between diverse IoT devices and platforms.
Semantic IoT middleware leverages Blockchain technology to establish secure data provenance and integrity by creating an immutable record of data transactions. Integration involves recording data origins, modifications, and access events on a distributed ledger. However, Blockchain operations introduce performance considerations; specifically, energy consumption increases by 15.3% due to the computational demands of consensus mechanisms, and transaction latency averages 320ms, impacting real-time data processing capabilities. These overheads necessitate careful system design and optimization to balance security requirements with performance constraints in IoT deployments.
AI-based threat intelligence systems utilize machine learning algorithms to identify deviations from established behavioral baselines, functioning as a proactive security measure. Enhancement through Federated Learning allows these systems to train on decentralized data sources – such as data from numerous IoT devices – without direct data exchange, preserving data privacy and reducing single points of failure. This distributed learning approach improves anomaly detection accuracy and broadens the scope of threat identification. Upon detecting anomalous activity, the system can automate pre-defined response actions, including isolating compromised devices, adjusting security policies, or alerting administrators, minimizing potential damage and response time.
Resilient IoT: Adapting to Inevitable Disruption
Resilience Engineering represents a paradigm shift in IoT security, moving beyond the limitations of purely preventative measures. Traditional approaches often focus on blocking all potential attacks, a strategy that proves increasingly untenable in the face of evolving threats and system complexity. Instead, resilience prioritizes the ability of an IoT system to continue functioning, potentially in a degraded but acceptable manner, even when under attack or facing adverse conditions. This involves designing systems that can absorb disruptions, adapt to changing circumstances, and rapidly recover from failures. Crucially, resilience acknowledges that compromise is inevitable, and focuses on minimizing the impact of successful attacks through techniques like redundancy, diversity, and self-healing mechanisms. By anticipating and preparing for failures, rather than solely attempting to prevent them, resilience engineering offers a more robust and sustainable security posture for the increasingly interconnected world of the Internet of Things.
The convergence of edge processing and Trusted Execution Environments (TEEs) represents a significant advancement in IoT security and performance. By shifting computational tasks from centralized cloud servers to devices nearer the data source – the ‘edge’ – latency is substantially reduced, enabling quicker response times critical for applications like autonomous vehicles and real-time monitoring. Simultaneously, TEEs create a secure enclave within the processor, isolating sensitive data and code from the broader operating system, thereby mitigating the risk of compromise even if other system components are breached. This localized processing, fortified by hardware-based security, not only minimizes data transmission – reducing bandwidth demands and potential interception – but also ensures the integrity and confidentiality of information at its origin, fostering a more resilient and trustworthy IoT ecosystem.
Implementing secure communication channels within a Trusted Execution Environment (TEE) necessitates a trade-off between heightened security and system performance. Recent studies demonstrate that establishing these secure connections introduces a measurable energy overhead of 6.5%, impacting battery life in resource-constrained IoT devices. Furthermore, the cryptographic processes involved incur a latency of 32 milliseconds, potentially affecting real-time applications requiring immediate data processing. This delay, while relatively short, becomes a critical consideration in time-sensitive scenarios like industrial control systems or autonomous vehicle operation, where even minor delays can have significant consequences. Optimizing these secure communication protocols within the TEE remains an ongoing area of research, aiming to minimize performance impacts while maintaining robust protection against evolving cyber threats.
The IoT Security Foundation (IoTSF) actively cultivates a more secure Internet of Things landscape through the development and dissemination of practical guidance. Recognizing the limitations of traditional perimeter-based security, the IoTSF champions the adoption of zero-trust architectures, where no device or user is inherently trusted, demanding continuous verification. Crucially, the foundation also supports the integration of Trusted Execution Environments (TEEs) as a key enabler for robust security at the hardware level. This work extends beyond theoretical frameworks; the IoTSF provides readily accessible best practices, resources, and support to manufacturers, developers, and users, fostering a collaborative approach to mitigating evolving IoT threats and building inherently resilient systems.
Towards a Secure and Trustworthy IoT Ecosystem
Data minimization and purpose limitation represent cornerstones of responsible data handling within the Internet of Things. These principles, increasingly codified in global regulatory frameworks like GDPR and CCPA, dictate that IoT devices should collect only the data absolutely necessary for specified, legitimate purposes. This approach drastically reduces the attack surface for potential breaches, limiting the scope of damage should a security incident occur. Beyond security, minimizing data collection enhances user privacy and builds trust, fostering wider adoption of IoT technologies. Implementing these principles requires careful consideration of data lifecycles, employing techniques like data anonymization, pseudonymization, and secure data storage to ensure compliance and ethical data practices throughout the entire IoT ecosystem.
Software-Defined Perimeter (SDP) offers a dynamic enhancement to zero-trust security models by shifting away from traditional, static network perimeters. Instead of granting network access based on location, SDP verifies user and device identity before establishing a secure connection to specific resources. This ‘black cloud’ approach effectively renders resources invisible to unauthorized entities, minimizing the attack surface and mitigating the risk of lateral movement within a network. By dynamically creating secure, isolated perimeters around each resource, SDP complements zero-trust’s principle of ‘never trust, always verify,’ offering granular access control and significantly reducing the potential for breaches in increasingly complex Internet of Things (IoT) ecosystems.
A comprehensive security framework, integrating robust hardware foundations with sophisticated data handling and resilient system design, demonstrably elevates IoT security posture. Recent evaluations reveal this holistic methodology attains 82% compliance with the IoTSF’s (IoT Security Foundation) stringent best practices – a substantial improvement over the 65% and 78% achieved by traditionally structured and cloud-focused architectures. This enhanced compliance suggests a significantly reduced vulnerability landscape, as the integrated approach proactively addresses security concerns across the entire IoT ecosystem, from device-level protection to data governance and operational continuity. The results underscore the efficacy of shifting from fragmented security measures to a unified, multi-layered defense capable of withstanding contemporary and emerging threats.
The dynamic nature of the Internet of Things demands perpetual refinement of security protocols and architectural designs. Threats to IoT devices and networks are not static; they constantly evolve in sophistication and scope, necessitating a proactive stance towards vulnerability mitigation. A truly trustworthy IoT ecosystem isn’t built on a fixed set of safeguards, but rather on a culture of continuous innovation and adaptation. This involves ongoing research into emerging threats, the development of novel security mechanisms – such as advanced encryption and behavioral analytics – and the agile implementation of updates and patches. Furthermore, fostering collaboration between stakeholders – device manufacturers, software developers, and cybersecurity experts – is crucial for rapidly identifying and addressing vulnerabilities before they can be exploited, ensuring the long-term resilience and reliability of interconnected devices and systems.
The pursuit of secure IoT systems, as detailed in this framework, mirrors a fundamental principle of elegant design. The architecture prioritizes minimizing complexity by integrating trusted execution environments, semantic middleware, and blockchain-removing potential attack vectors rather than adding layers of defense. This approach resonates with a sentiment expressed by Tim Bern-Lee: “The Web is more a social creation than a technical one.” The framework doesn’t merely propose technical solutions; it envisions a system where trust is inherently built into the fabric of interaction, streamlining security and fostering a more reliable connected world. It’s a testament to the idea that a successful system requires fewer instructions, not more, achieving security through inherent properties rather than imposed rules.
Future Directions
The presented architecture, while offering integration, does not eliminate inherent trade-offs. Semantic security, reliant on precise ontologies, faces the perpetual challenge of representing a world stubbornly resistant to categorization. Blockchain, lauded for immutability, introduces latency – a critical flaw in responsive edge computing scenarios. Further work must address these tensions, not by seeking resolution, but by quantifying the acceptable degree of imperfection.
Current threat models largely presume rational actors. A more fruitful, though unsettling, line of inquiry lies in anticipating irrationality – the deliberate introduction of chaos to exploit systemic vulnerabilities. The focus shifts from preventing intrusion to accepting its inevitability, and designing systems that minimize damage – a pragmatic embrace of failure.
Ultimately, the pursuit of absolute security is a logical fallacy. Clarity is the minimum viable kindness. The field progresses not through increasingly complex fortifications, but through increasingly accurate assessments of risk, and the elegant simplification of response. The next step is not more technology, but a disciplined subtraction of the unnecessary.
Original article: https://arxiv.org/pdf/2602.10762.pdf
Contact the author: https://www.linkedin.com/in/avetisyan/
See also:
- EUR USD PREDICTION
- Epic Games Store Free Games for November 6 Are Great for the Busy Holiday Season
- How to Unlock & Upgrade Hobbies in Heartopia
- Battlefield 6 Open Beta Anti-Cheat Has Weird Issue on PC
- Sony Shuts Down PlayStation Stars Loyalty Program
- The Mandalorian & Grogu Hits A Worrying Star Wars Snag Ahead Of Its Release
- ARC Raiders Player Loses 100k Worth of Items in the Worst Possible Way
- Unveiling the Eye Patch Pirate: Oda’s Big Reveal in One Piece’s Elbaf Arc!
- TRX PREDICTION. TRX cryptocurrency
- Best Ship Quest Order in Dragon Quest 2 Remake
2026-02-12 15:53