Author: Denis Avetisyan
A novel group key agreement protocol addresses the unique security challenges of resource-constrained cyber-physical systems relying on broadcast bus networks.
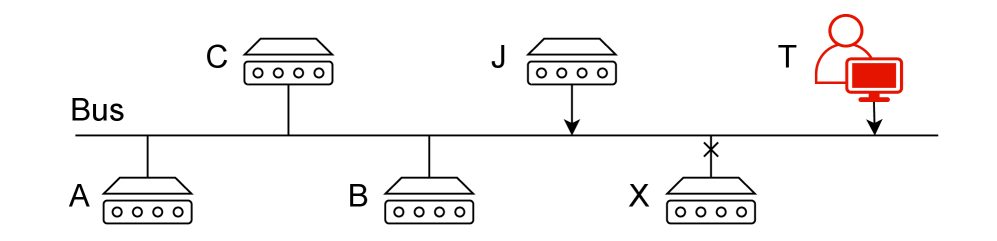
This review details GRACYBUS, a scalable and resilient protocol designed for secure group key agreement in cyber-physical systems, with considerations for future post-quantum cryptography.
While robust communication security is paramount in distributed cyber-physical systems, existing group key agreement protocols often prove ill-suited to the constraints of industrial bus topologies. This paper, ‘Secure Group Key Agreement on Cyber-Physical System Buses’, addresses this gap by presenting GRACYBUS, a novel protocol designed for resource-constrained networks, supporting dynamic membership and resilience against strong adversaries. GRACYBUS leverages a TreeKEM-based approach to establish authenticated, fully distributed keys suitable for broadcast, half-duplex bus systems, while paving the way for post-quantum cryptographic integration. Can this design provide a scalable and secure foundation for the next generation of interconnected industrial control systems?
The Fragility of Connection: CPS Security in a Networked Age
Contemporary Cyber-Physical Systems (CPS), encompassing networks like those utilizing Automotive Ethernet and PROFIBUS, frequently depend on security models developed for less interconnected eras. These traditional architectures often prioritize performance and compatibility over advanced threat mitigation, creating vulnerabilities exploitable by malicious actors. Specifically, many CPS bus systems employ static or infrequently rotated keys, and rely heavily on perimeter security-a defense easily bypassed once inside the network. This reliance on established, yet increasingly fragile, security paradigms leaves critical infrastructure susceptible to compromise, potentially impacting everything from automotive functions and industrial control systems to medical devices and smart grids. The inherent limitations of these older models necessitate a proactive shift towards more dynamic and robust security solutions capable of addressing the evolving threat landscape.
Conventional Cyber-Physical Systems (CPS) frequently employ centralized key management, where a single master key controls access for the entire network. While seemingly efficient, this approach introduces a critical vulnerability: compromise of the master key immediately grants an attacker control over all connected devices. This single point of failure stems from a lack of robust group key agreement protocols, which would allow devices to collaboratively establish and refresh encryption keys without relying on a central authority. Without such mechanisms, a successful attack doesn’t just breach one device, but the entire system, potentially disrupting critical infrastructure, compromising vehicle safety, or halting industrial processes. Consequently, the security of these networks remains fragile, demanding a shift toward distributed and resilient key management strategies to mitigate systemic risk.
The proliferation of interconnected Cyber-Physical Systems (CPS) necessitates a fundamental rethinking of network security. Historically, CPS relied on isolated architectures, but modern applications – from autonomous vehicles to smart grids – demand constant communication and data exchange. This increased connectivity dramatically expands the attack surface, rendering traditional security models inadequate. Current protocols struggle to scale effectively with the growing number of devices and the volume of data transmitted, creating vulnerabilities that malicious actors can exploit. A shift towards more resilient and scalable security protocols-those capable of dynamic key management, intrusion detection, and adaptive security policies-is no longer optional, but critical for ensuring the reliable and safe operation of these increasingly complex systems. The future of CPS security hinges on the development and implementation of these advanced, network-wide protections.
GRACYBUS: A System Designed for Distributed Trust
GRACYBUS is a group key agreement protocol developed to address the unique limitations of Cyber-Physical Systems (CPS) bus environments. Traditional key agreement methods often prove impractical for CPS due to constraints in bandwidth, processing power, and energy availability. GRACYBUS is specifically engineered to operate efficiently within these boundaries, prioritizing low communication overhead and minimal computational demands. It provides a mechanism for multiple nodes within a CPS network to securely establish a shared secret key, enabling secure communication and data exchange without relying on a central key distribution authority. This decentralized approach enhances the system’s robustness and scalability for use in resource-constrained CPS deployments.
GRACYBUS builds upon the foundational principles of the TreeKEM protocol to facilitate efficient and scalable group key distribution within networked systems. TreeKEM establishes a hierarchical key structure, and GRACYBUS leverages this existing framework by adapting its key exchange mechanisms for the specific requirements of Cyber-Physical Systems (CPS) bus architectures. This extension allows for the creation of a shared secret among multiple participants without requiring point-to-point key exchanges, reducing communication complexity. By utilizing the TreeKEM structure, GRACYBUS enables new members to join the group and receive the shared key with a logarithmic number of messages relative to the group size, enhancing scalability and minimizing latency for key updates and re-keys.
GRACYBUS utilizes a Binary Tree structure to manage group keys, fundamentally impacting communication efficiency and system robustness. Each node in the tree represents a key, and the tree’s hierarchical arrangement minimizes the number of key exchanges required for group operations. Specifically, key updates and re-keying operations only necessitate communication along the affected branch of the tree, rather than requiring broadcasts to all network participants. This localized approach directly reduces communication overhead, particularly within bandwidth-constrained CPS bus systems. Furthermore, the tree structure inherently provides resilience; a compromised node only impacts the subtree rooted at that node, limiting the scope of potential security breaches and enabling faster recovery through localized re-keying procedures.
GRACYBUS achieves a logarithmic time complexity of O(log\ n) for group key operations, specifically relating to key updates and re-keying events. This performance characteristic is directly attributable to the protocol’s utilization of a Binary Tree structure for key management; the computational cost scales with the height of this tree rather than the total number of nodes, n. Consequently, as the number of nodes in the Controlled Physical System (CPS) network increases, the operational overhead grows proportionally to the logarithm of that number, ensuring scalability for large-scale deployments where linear or higher-order complexities would become prohibitive. This logarithmic scaling minimizes communication latency and computational burden on individual nodes during group key agreement processes.
Validating Resilience: A Foundation of Modern Cryptography
GRACYBUS utilizes Advanced Encryption Standard (AES) with a 256-bit key size for symmetric encryption of data in transit and at rest. This algorithm is widely adopted and provides a high level of security against brute-force attacks. Secure Hash Algorithm 512 (SHA-512) is implemented for cryptographic hashing, generating a 512-bit hash value. SHA-512 is used for data integrity checks, password storage, and digital signatures, offering collision resistance and preventing unauthorized modification of data. These algorithms are implemented according to established cryptographic standards and best practices to ensure robust security within the GRACYBUS protocol.
GRACYBUS incorporates post-quantum cryptographic algorithms to mitigate the threat posed by future quantum computing capabilities. Specifically, the protocol utilizes CRYSTALS-Dilithium for digital signatures, a lattice-based signature scheme selected for its security and efficiency, and CRYSTALS-Kyber for key encapsulation, a lattice-based key-establishment mechanism. These algorithms are designed to resist attacks from both classical and quantum computers, providing a forward-secure communication channel and ensuring long-term data confidentiality and integrity even as computational power evolves. The integration of these post-quantum primitives prepares GRACYBUS for a transition to a post-quantum cryptographic landscape.
GRACYBUS utilizes the HMAC-based Key Derivation Function (HKDF) to generate cryptographic keys from a shared secret. HKDF accepts a keying material input and a salt, applying a hashing function – in this case, SHA-512 – to derive a pseudorandom key. This process ensures both strong key generation, resisting precomputation attacks, and unpredictability, preventing the derivation of related keys even with known inputs. The use of HKDF mitigates weaknesses present in simpler key derivation methods and facilitates the creation of multiple, independent keys for different protocol components from a single master secret, enhancing overall security.
Formal security analysis of the GRACYBUS protocol leverages the Dolev-Yao Model, a widely accepted computational model used to prove the security of cryptographic protocols. This model allows for the rigorous evaluation of protocol behavior by considering an attacker with arbitrary computational power who controls messages in transit. Through the application of the Dolev-Yao framework, the protocol’s resistance to various known attacks, including man-in-the-middle attacks, replay attacks, and impersonation attempts, has been mathematically validated. The analysis specifically focuses on demonstrating that an attacker, even with complete control over network communication, cannot forge messages or compromise the confidentiality and integrity of exchanged data, thus confirming the protocol’s robustness.
Beyond Protection: Architecting for the Inevitable Failure
The escalating connectivity of Cyber-Physical Systems (CPS) introduces vulnerabilities that threaten critical infrastructure and sensitive data; GRACYBUS addresses these concerns through a robust security framework. This isn’t simply a matter of adding a layer of protection, but fundamentally reshaping the security posture of CPS bus systems by establishing a secure communication channel. Through features like authenticated messaging and identity management, GRACYBUS actively mitigates risks associated with unauthorized access, data manipulation, and system compromise. Consequently, the implementation of GRACYBUS provides a demonstrable improvement in operational resilience, safeguarding vital processes and ensuring the continued, reliable function of increasingly interconnected industrial environments.
GRACYBUS establishes a robust security foundation by leveraging the well-established principles of an Industrial Public Key Infrastructure (PKI). This integration allows for the creation of a trusted framework wherein each node within the Control Plane System (CPS) possesses a unique digital identity, verifiable through a hierarchy of Certificate Authorities. By employing digital certificates, GRACYBUS ensures that all communications originate from authenticated sources, preventing unauthorized access and malicious manipulation. This system of identity management not only safeguards the integrity of data exchanged between nodes but also facilitates secure key distribution, enabling encrypted communication channels and bolstering the overall resilience of the CPS against cyber threats. The PKI-based authentication process provides a scalable and standardized approach to verifying the legitimacy of each device, essential for maintaining the reliability and safety of critical infrastructure.
The integrity of communication within critical systems is paramount, and Message Authentication Codes (MAC) serve as a crucial defense against malicious alterations and fabrication of data. These codes function by appending a short, fixed-size value – generated using a secret key and the message itself – to each transmission. Upon receipt, the system recalculates the MAC using the same key; any discrepancy between the received and recalculated MAC immediately indicates tampering or forgery, effectively invalidating the message. This cryptographic technique doesn’t guarantee confidentiality – messages aren’t encrypted – but it provides robust assurance that the information received is precisely what was sent, protecting against attacks where adversaries attempt to manipulate control signals or inject false data into the system. The implementation of MACs within CPS bus systems, therefore, constitutes a fundamental layer of security, preserving the reliability and trustworthiness of critical infrastructure.
GRACYBUS is architected for robust performance even within expansive Cyber-Physical Systems (CPS). Its efficiency stems from logarithmic scaling: both updating system configurations and removing nodes – critical operations for maintaining a dynamic network – require only O(log\ n) messages, where ‘n’ represents the total number of nodes. This contrasts sharply with systems requiring linear or greater complexity, which can become severely bottlenecked as the network grows. Furthermore, the storage demands for private keys – essential for secure communication – also scale at O(log\ n), minimizing the memory footprint on each node. This design choice ensures that GRACYBUS remains scalable and efficient, capable of securing large-scale CPS deployments without prohibitive computational or storage costs, paving the way for more resilient and interconnected critical infrastructure.
The pursuit of secure communication within cyber-physical systems, as detailed in this work with GRACYBUS, reveals a familiar tension. One strives for robust protocols, scalability, and even a future-proofed resistance to quantum threats, yet each added layer of complexity introduces new vulnerabilities. It echoes a sentiment expressed by Blaise Pascal: “The eloquence of youth is that it knows no limits.” This protocol, much like youthful ambition, attempts to encompass all possible defenses. However, the very act of anticipating every future failure-of optimizing for resilience-risks sacrificing the flexibility needed to adapt when unforeseen circumstances inevitably arise. The perfect architecture, a flawlessly secure system, remains a myth – a necessary fiction to justify the constant evolution and re-evaluation of these interconnected ecosystems.
The Turning of the Wheel
GRACYBUS, like all constructions, addresses a present need with promises made to the future. Every key established is a debt incurred, every broadcast a widening of the attack surface. The protocol’s efficiency, while laudable given the constraints of cyber-physical systems, merely delays the inevitable: the exhaustion of classical cryptographic assumptions. The move towards post-quantum considerations is not a fortification, but an acknowledgement of entropy-a system preparing to dismantle and rebuild upon its own foundations.
The true challenge lies not in designing more robust algorithms, but in accepting the inherent fragility of consensus. Control is an illusion that demands service level agreements. The focus will shift, inevitably, from securing the perimeter to cultivating internal resilience – systems that can degrade gracefully, reconfigure in response to compromise, and ultimately, fix themselves. Every dependency is a promise made to the past; the future belongs to those who minimize them.
This work represents a single rotation of the wheel. Further efforts should not concentrate solely on optimization, but on the choreography of failure. The next generation of protocols won’t be about preventing breaches, but about containing them – building ecosystems capable of absorbing disruption and continuing, diminished perhaps, but not destroyed. The system will always find a way.
Original article: https://arxiv.org/pdf/2601.21966.pdf
Contact the author: https://www.linkedin.com/in/avetisyan/
See also:
- Poppy Playtime Chapter 5: Engineering Workshop Locker Keypad Code Guide
- Jujutsu Kaisen Modulo Chapter 23 Preview: Yuji And Maru End Cursed Spirits
- God Of War: Sons Of Sparta – Interactive Map
- 8 One Piece Characters Who Deserved Better Endings
- Who Is the Information Broker in The Sims 4?
- Poppy Playtime 5: Battery Locations & Locker Code for Huggy Escape Room
- Mewgenics Tink Guide (All Upgrades and Rewards)
- Pressure Hand Locker Code in Poppy Playtime: Chapter 5
- Poppy Playtime Chapter 5: Emoji Keypad Code in Conditioning
- I Used Google Lens to Solve One of Dying Light: The Beast’s Puzzles, and It Worked
2026-01-31 09:26