Author: Denis Avetisyan
A new analysis reveals that cloning attacks pose a significant risk to applications leveraging Intel’s Software Guard Extensions, potentially compromising data confidentiality and integrity.
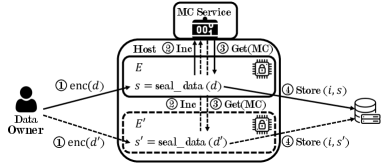
Approximately 20% of SGX applications remain vulnerable to cloning attacks despite existing rollback protection mechanisms, impacting data consistency and unlinkability.
While Trusted Execution Environments (TEEs) like Intel SGX offer promising confidentiality in cloud computing, their susceptibility to forking attacks remains a critical concern. This paper, ‘The Real Menace of Cloning Attacks on SGX Applications’, presents an extensive analysis of 72 SGX-based proposals, revealing that approximately 20% are vulnerable to cloning attacks-even those already protected against rollback. Our findings categorize these attacks into distinct types that compromise data consistency and unlinkability, demonstrating a significant gap in current SGX application security. Can we develop more robust defenses against cloning attacks to fully realize the security potential of TEEs?
The Allure and Illusion of Secure Enclaves
Contemporary applications are increasingly architected to leverage secure enclaves, with Intel Software Guard Extensions (SGX) being a prominent example, to fortify sensitive data and critical code segments. This shift towards enclave-based security addresses growing concerns regarding data breaches and malicious software by creating isolated execution environments, effectively shielding confidential computations from the compromised operating system and other potentially hostile software. Applications ranging from digital rights management and financial transactions to medical data processing and machine learning inference are adopting SGX to establish a hardware-rooted trust zone, ensuring the confidentiality and integrity of sensitive operations even in the face of system compromise. The appeal lies in SGX’s ability to protect data in use – a traditionally vulnerable point in the data lifecycle – by encrypting it within the enclave and limiting access to authorized code only.
Despite its promise of fortified security, Intel’s Software Guard Extensions (SGX) presents a unique attack surface that conventional security protocols struggle to address. The very isolation that defines SGX – creating protected enclaves within memory – inadvertently introduces vulnerabilities stemming from its complex interaction with the broader system. Sophisticated attacks don’t target the enclave’s code directly, but rather exploit weaknesses in how SGX manages these isolated environments, specifically in areas like memory encryption key derivation and enclave attestation. These bypass traditional defenses – firewalls, antivirus software – because the attacks operate outside the normal security perimeter, focusing instead on manipulating the SGX infrastructure itself. Consequently, researchers have demonstrated successful cloning and forking attacks, where an attacker can duplicate or split an enclave’s execution, potentially gaining access to sensitive data or manipulating its operations without triggering typical intrusion detection systems.
Sophisticated attacks targeting Intel SGX enclaves often bypass conventional security protocols by exploiting fundamental weaknesses in how the system manages and protects enclave code and data. Specifically, techniques like cloning and forking capitalize on vulnerabilities within SGX’s sealing mechanisms-the process of encrypting data for secure storage-and the overall enclave lifecycle management. Cloning attacks aim to duplicate an enclave’s state, while forking attempts to create multiple instances from a single enclave, potentially revealing sensitive information or compromising the enclave’s integrity. These exploits don’t target traditional operating system vulnerabilities; instead, they directly address the intricacies of SGX’s hardware and software interactions, requiring specialized countermeasures focused on strengthening sealing processes, enhancing enclave attestation, and improving the resilience of enclave management systems to prevent unauthorized duplication or manipulation.
The foundational promise of secure enclaves like Intel SGX – safeguarding sensitive data and critical code – hinges on the implementation of effective defenses against emerging attack vectors. While SGX establishes a protected execution environment, its inherent design can be subverted without stringent countermeasures, potentially rendering the isolation ineffective. Sophisticated attacks targeting the enclave’s sealing mechanisms and management protocols can compromise the integrity of the protected data, exposing it to malicious actors. Consequently, the potential gains in security offered by SGX are not automatic; they demand ongoing research and the deployment of robust mitigations to ensure that the enclave truly delivers on its promise of confidentiality and trust, preventing a false sense of security and the subsequent exposure of valuable information.
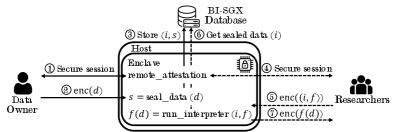
Mapping the Terrain of Attack
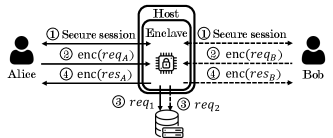
Cloning attacks in Intel SGX environments exploit the absence of robust control mechanisms over enclave instantiation. An adversary can repeatedly request the creation of new enclaves loaded with the same application binary, effectively duplicating the application’s execution context. This is possible because the SGX SDK does not inherently prevent the creation of multiple enclaves from a single binary image. While each enclave operates in a protected environment, the lack of attestation or verification of unique instantiation prevents the system from identifying and mitigating the proliferation of identical enclaves, enabling potential manipulation or data leakage across these cloned instances.
Forking attacks in Intel SGX environments occur when an attacker gains the ability to create multiple enclaves running the same application code, effectively partitioning clients and providing each with a potentially different operational context. This partitioning allows the attacker to present divergent views of data to different clients, leading to inconsistencies and enabling manipulation of information. The core mechanism relies on exploiting the lack of robust control over enclave instantiation, enabling the creation of unauthorized enclave instances. Successful forking can compromise data integrity by allowing an adversary to modify data presented to specific clients while maintaining a consistent, but false, view for others, or to create conflicting versions of the same data accessible to different users.
Rollback attacks target the sealing mechanism within Intel SGX enclaves, which is designed to protect data confidentiality and integrity. The sealing process creates encrypted data blobs linked to specific enclave measurements and a monotonically increasing nonce. Adversaries exploiting weaknesses in this process can potentially forge or manipulate the nonce, effectively requesting older, potentially compromised, sealed data. This is achieved by presenting a lower nonce value than expected, causing the enclave to decrypt and return a previous state of the data. Successful rollback attacks circumvent the intended protection against data tampering and allow adversaries to access or modify sensitive information from earlier points in time, even if the enclave has since been updated with security patches or new data.
An analysis of 72 applications utilizing Intel Software Guard Extensions (SGX) revealed that approximately 20% are susceptible to forking attacks enabled by cloning vulnerabilities. This indicates a substantial security risk within current SGX implementations, as cloning allows adversaries to create multiple enclave instances with identical binaries. A more focused analysis of database applications within this sample set showed a significantly higher vulnerability rate, with 64% found to be vulnerable to cloning attacks. This disproportionate impact on database applications suggests a critical need for enhanced security measures and specific mitigation strategies within this application category.
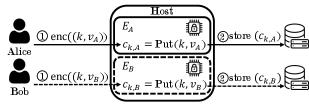
Countermeasures: Sculpting Resilience
Merkle Trees and Monotonic Counters provide mechanisms for verifying data freshness and preventing rollback attacks in secure enclaves. A Merkle Tree recursively hashes data, generating a root hash that represents the entire dataset’s integrity; any modification to the data results in a different root hash. Monotonic Counters, incremented with each update, ensure that operations are performed in the correct sequence and prevent replay attacks. Combining these techniques allows a verifier to confirm both the authenticity and temporal order of data, establishing a verifiable history and detecting any attempts to revert to a previous, potentially compromised, state. The root hash from the Merkle Tree and the value of the Monotonic Counter can be securely stored and used to validate the current data’s integrity and freshness against previously known good states.
CloneBuster mitigates cloning attacks in Intel SGX enclaves by establishing a cache covert channel. This channel operates by monitoring cache access patterns; legitimate enclave instances exhibit predictable behavior, while cloned instances, due to shared resources, introduce detectable anomalies. Specifically, CloneBuster utilizes a timing-based analysis of cache hits and misses to differentiate between authorized and unauthorized enclave replicas. Upon detection of a cloned instance, the system can trigger countermeasures, such as termination of the cloned enclave or revocation of its cryptographic keys, thereby preventing malicious exploitation of replicated enclave code and data.
SGX Proxies improve data privacy by enabling unlinkability, preventing an adversary from correlating enclave requests to a single client. However, this architecture introduces a potential vulnerability to forking attacks, where a malicious proxy duplicates requests to the enclave, potentially leading to denial of service or incorrect computations. Mitigating this requires careful design of the proxy to include unique request identifiers and replay protection mechanisms, such as sequence numbers or timestamps, to ensure each request is processed only once and originates from a legitimate client. Furthermore, the enclave itself must be designed to validate these identifiers and reject duplicate or out-of-order requests, preventing the proxy from successfully executing a forking attack.
Data encryption within an Intel SGX enclave provides confidentiality but is insufficient as a sole security measure. While encryption protects data at rest and in transit within the enclave’s memory, it does not prevent attacks targeting the enclave’s integrity or availability. Specifically, encryption does not defend against cloning attacks, where the enclave’s state is replicated, or manipulation attacks that alter data before or after encryption. Robust defenses require layering encryption with mechanisms such as attestation to verify enclave identity, integrity checks to detect tampering, and techniques like Merkle trees or clone detection systems to prevent rollback or unauthorized replication. Comprehensive security necessitates a defense-in-depth approach, acknowledging that encryption is a foundational element but must be combined with other protective measures to address the broader threat landscape.
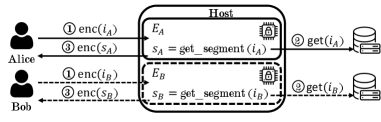
Towards a More Robust Paradigm
The implementation of robust defenses within Intel’s Software Guard Extensions (SGX) significantly bolsters the security of applications designed to operate within these protected enclaves. These defenses mitigate a spectrum of threats, ranging from side-channel attacks and memory corruption vulnerabilities to sophisticated code injection attempts. By hardening the perimeter around sensitive data and critical code segments, SGX-based applications become considerably more resistant to compromise, even in the presence of a compromised operating system or hypervisor. This enhanced security posture isn’t merely about patching individual flaws; it represents a fundamental shift toward a more resilient computing model, safeguarding valuable assets and ensuring the integrity of confidential operations across various sectors, including finance, healthcare, and cloud computing.
The bolstering of Intel’s Software Guard Extensions (SGX) security directly cultivates confidence in its potential as a cornerstone of confidential computing. This increased trust is not merely theoretical; it actively enables the development of previously untenable applications demanding absolute data privacy. Fields like secure healthcare data analytics, financial modeling with sensitive client information, and even privacy-focused machine learning are now realistically achievable due to SGX’s ability to create isolated execution environments. As vulnerabilities are addressed and defenses are strengthened, the platform moves beyond a promising technology towards a practical solution, paving the way for a new generation of applications where data confidentiality is paramount and innovation is no longer constrained by security concerns.
Addressing vulnerabilities in how enclaves are managed and data is handled is paramount to constructing genuinely resilient and trustworthy computing systems. Traditional security models often falter when facing sophisticated attacks targeting the management plane or exploiting weaknesses in data transfer protocols; therefore, meticulous attention to enclave lifecycle-from provisioning and initialization to secure deletion-is critical. Researchers are actively developing techniques to harden these processes, including robust access control mechanisms, enhanced memory protection, and rigorous validation of data integrity throughout the enclave’s operation. By proactively mitigating these risks, systems utilizing trusted execution environments can offer a significantly stronger defense against malicious actors, fostering a more secure and reliable foundation for sensitive applications and data processing.
The future of trusted execution environments hinges on persistent innovation in critical areas such as remote attestation and secure enclave provisioning. Ongoing research aims to refine attestation protocols, ensuring that enclaves are genuinely sourced and haven’t been tampered with prior to execution-a process crucial for establishing trust in remote computations. Simultaneously, advancements in secure enclave provisioning are streamlining the often-complex process of creating and initializing these secure containers, making them more accessible to developers and less prone to configuration errors. These combined efforts not only fortify the security foundations of platforms like SGX but also address usability concerns, paving the way for broader adoption and the realization of confidential computing’s full potential across diverse applications, from healthcare to finance.
The analysis reveals a predictable fragility within complex systems-specifically, the susceptibility of Intel SGX applications to cloning attacks. Approximately 20% demonstrate vulnerability, even with implemented rollback protection. This isn’t a design flaw, but rather an inherent characteristic of any system striving for absolute security within a chaotic environment. As Carl Friedrich Gauss observed, “If I have seen further it is by standing on the shoulders of giants.” The giants here are the accumulated complexities of hardware and software, and the ‘further’ we reach, the more acutely aware one becomes of the inherent limitations. The categorization of these attacks – impacting data consistency and unlinkability – merely formalizes the inevitable emergence of unforeseen interactions within a growing ecosystem. Stability, after all, is merely an illusion that caches well.
The Looming Shadow
The discovery that a fifth of ostensibly secure SGX applications remain vulnerable to cloning attacks isn’t a flaw in implementation, but a predictable consequence of belief in architectural salvation. Rollback protection, lauded as a defense, proves merely a delay of accounting. Each monotonic counter is, at its heart, a confession that absolute state is unattainable, a temporary reprieve before the inevitable drift into inconsistency. The categorization of these attacks-forking, cloning, and their subtle variations-feels less like a victory over chaos and more like taxonomy of decay.
Future work will undoubtedly focus on refining attestation and bolstering defenses against these specific vectors. Yet, this feels like rearranging deck chairs. The fundamental issue isn’t the how of the attack, but the inherent fragility of attempting to build trust on mutable state. Each additional layer of security adds a new surface for entropy to act upon, a new point of failure waiting to manifest.
The real challenge lies in accepting that secure enclaves aren’t islands of perfect integrity, but nodes in a distributed system of probabilistic guarantees. The pursuit of absolute confidentiality will, invariably, yield to the demands of availability and usability. The question isn’t how to prevent these attacks, but how to design systems that can gracefully absorb and recover from their inevitability.
Original article: https://arxiv.org/pdf/2601.09273.pdf
Contact the author: https://www.linkedin.com/in/avetisyan/
See also:
- Poppy Playtime Chapter 5: Engineering Workshop Locker Keypad Code Guide
- God Of War: Sons Of Sparta – Interactive Map
- Jujutsu Kaisen Modulo Chapter 23 Preview: Yuji And Maru End Cursed Spirits
- Poppy Playtime 5: Battery Locations & Locker Code for Huggy Escape Room
- Who Is the Information Broker in The Sims 4?
- Poppy Playtime Chapter 5: Emoji Keypad Code in Conditioning
- Someone Made a SNES-Like Version of Super Mario Bros. Wonder, and You Can Play it for Free
- Why Aave is Making Waves with $1B in Tokenized Assets – You Won’t Believe This!
- Pressure Hand Locker Code in Poppy Playtime: Chapter 5
- One Piece Chapter 1175 Preview, Release Date, And What To Expect
2026-01-15 18:01