Author: Denis Avetisyan
Researchers have developed a novel virtualization-based obfuscation framework that safeguards code and exception handling mechanisms against reverse engineering.
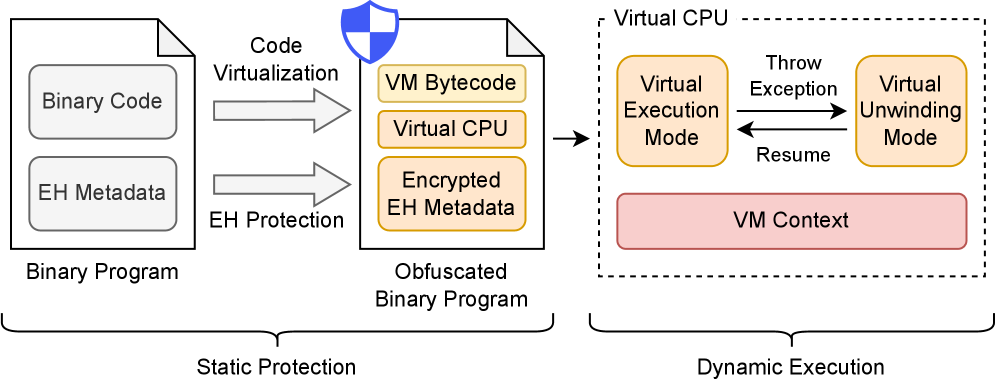
XuanJia maintains ABI compatibility while protecting binaries through metadata shadowing and advanced control-flow obfuscation.
While virtualization-based obfuscation is a common defense against reverse engineering, existing techniques often leave critical exception-handling metadata exposed. This paper introduces XuanJia: A Comprehensive Virtualization-Based Code Obfuscator for Binary Protection, a novel framework that comprehensively protects both code and exception semantics through ABI-compliant shadowing of exception metadata. By securely redirecting exception handling within a protected virtual machine, XuanJia eliminates static leakage without sacrificing runtime compatibility. Does this approach represent a significant step towards more robust and practical binary protection against increasingly sophisticated reverse engineering attacks?
Deconstructing Defenses: The Illusion of Binary Security
Historically, developers have relied on techniques like code obfuscation – deliberately scrambling the structure of compiled programs – to safeguard intellectual property and deter unauthorized modification. However, the efficacy of these binary protections is waning as reverse engineering tools become increasingly sophisticated. Modern disassemblers and decompilers, coupled with automated analysis frameworks, can now systematically unravel obfuscated code, revealing underlying algorithms and logic with relative ease. Attackers are no longer limited to manual inspection; they can deploy scripts and algorithms to automate the deobfuscation process, effectively bypassing traditional defenses and exposing the core functionality of a program. This shift necessitates a move beyond superficial protections towards more robust security measures that address the fundamental vulnerabilities within the code itself.
Modern reverse engineering relies heavily on tools capable of dissecting compiled code, effectively reconstructing the original source or mapping its execution flow. Static analysis tools achieve this by deconstructing the binary without actually running it, identifying functions, data structures, and potential vulnerabilities through pattern recognition and control flow analysis. Complementing this, dynamic analysis involves executing the code within a controlled environment – a debugger – to trace its behavior, observe variable values, and pinpoint sensitive operations. This combination allows skilled analysts to reveal the underlying algorithms and intellectual property embedded within the native code, even if the original source code remains unavailable, thereby compromising the confidentiality and integrity of the software.
The escalating arms race between software defenders and attackers increasingly favors the latter, as automated tools and advanced debugging skills erode the effectiveness of traditional binary protection methods. Where once code obfuscation and similar techniques presented a significant barrier to reverse engineering, modern attackers now routinely employ automated decompilers, dynamic analysis frameworks, and sophisticated debuggers to efficiently dissect and understand even heavily protected code. This shift means that defenses which previously slowed down attackers now merely add a layer of inconvenience, as automated processes can rapidly overcome obstacles and reveal sensitive algorithms or intellectual property. Consequently, a reliance on these conventional methods offers diminishing returns, demanding a move towards more robust and innovative security strategies that account for the growing capabilities of automated attacks.
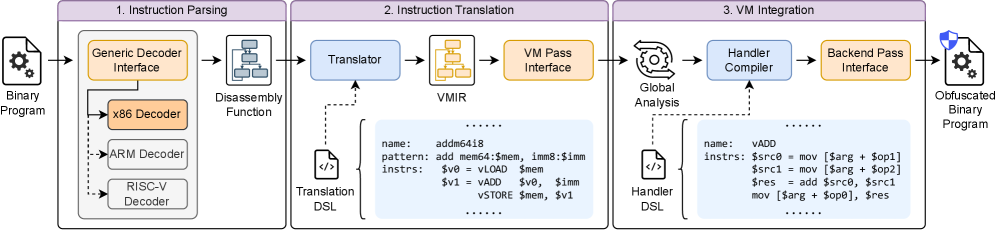
Transcending Native Code: The Allure of Virtualization
Virtualization obfuscation operates by converting application code from its native machine instruction set – typically x86, ARM, or similar – into a platform-independent bytecode representation. This bytecode is not directly executable by the processor; instead, it requires a virtual machine (VM) – a software emulation of a computer system – to interpret and execute the instructions. The VM acts as an intermediary, isolating the original code from direct analysis and hindering traditional reverse engineering techniques that rely on examining native instructions. This transformation effectively creates a customized instruction set architecture (ISA) understood only by the specific VM, adding a significant layer of complexity for potential attackers attempting to decompile or understand the application’s logic.
Instruction translation, a core component of virtualization obfuscation, involves converting native machine code – specific to a processor architecture like x86 or ARM – into bytecode designed for execution by a virtual machine. This transformation replaces direct processor instructions with an intermediate representation. The resulting bytecode is not directly executable by the host CPU, necessitating the VM interpreter. This process significantly increases the difficulty of static analysis, as reverse engineers must now analyze the translated bytecode rather than the original native code, and understand the VM’s specific instruction set and semantics. Furthermore, the translation introduces ambiguity; multiple native code sequences can translate to the same bytecode, and the translation process itself can be complex and non-deterministic, hindering straightforward reverse engineering attempts.
The Virtual Machine (VM) Interpreter functions as the runtime engine for the obfuscated bytecode, introducing a significant barrier to static and dynamic analysis. Rather than directly executing native machine code, the interpreter processes each bytecode instruction sequentially, performing the equivalent operations within the VM’s environment. This indirection prevents direct correlation between the bytecode and the underlying hardware instructions, complicating disassembly and debugging. Furthermore, the interpreter’s internal state and data structures are not directly visible to external analysis tools, requiring reverse engineers to understand the VM’s architecture and instruction set before meaningful analysis can occur. This abstraction layer substantially increases the effort and complexity required for reverse engineering, as tools designed for native code analysis are ineffective without adaptation.
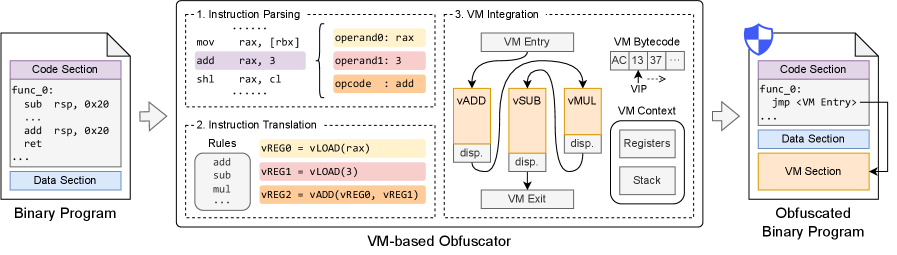
Unwinding the Truth: Shielding Exception Handling
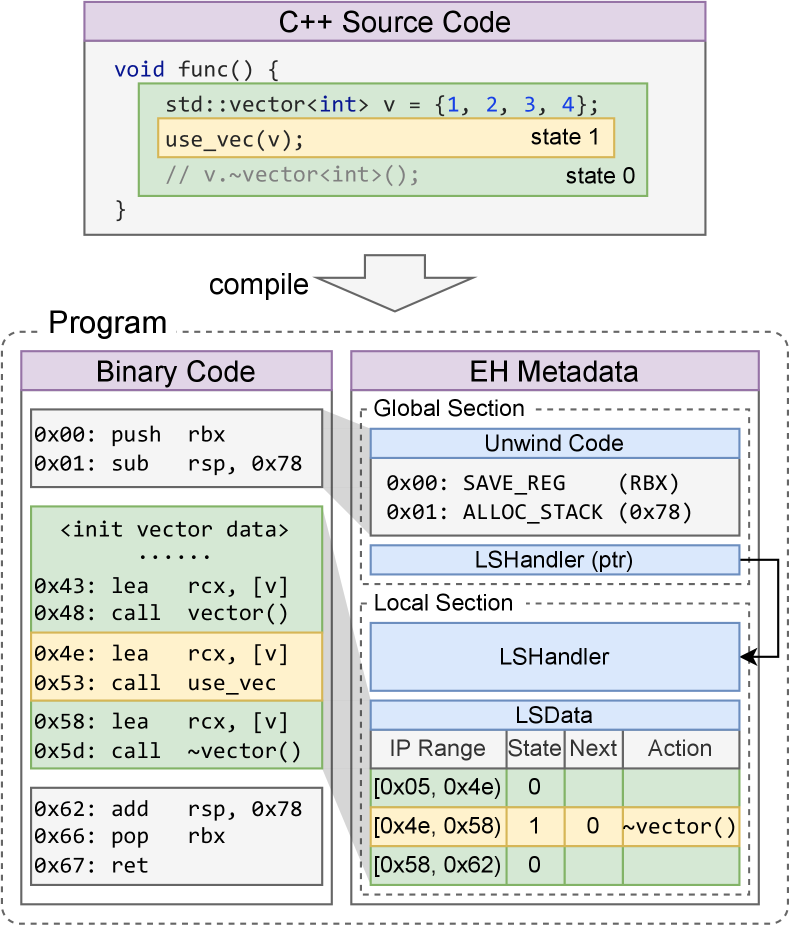
Exception handling (EH) is a fundamental component of robust software development, enabling programs to recover from runtime errors and maintain stability. However, the metadata associated with EH mechanisms-including unwind information, exception types, and handler locations-inherently exposes details about the program’s internal structure. This metadata is necessary for the operating system to correctly manage exceptions, but it also provides a potential target for reverse engineering. Analysis of EH metadata can reveal function boundaries, call relationships, and the overall organization of code, potentially aiding in the discovery of vulnerabilities or the reconstruction of algorithms. Consequently, protecting this metadata is a key consideration in software security.
ABI-Compliant Exception Handling (EH) Shadowing defends against reverse engineering by substituting the original EH metadata with a functionally equivalent ‘shadow’ section. This technique preserves binary compatibility, ensuring the program continues to operate correctly with existing exception handling mechanisms. The original metadata, which would typically reveal information about function boundaries and stack frame layouts, is replaced without altering the program’s behavior. The shadow section mirrors the functionality of the original, allowing the system to correctly locate and execute exception handlers while simultaneously obscuring the internal structure of the code from analysis.
Shadow Unwind Codes are integral to maintaining program stability during exception handling when employing ABI-compliant EH Shadowing. These codes dictate the process of stack unwinding – restoring the stack to a consistent state after an exception occurs – and ensure that destructors are called and resources are released correctly, preventing application crashes. The framework utilizes a diverse set of 1000 unique shadow unwind code sequences. This large number of variations significantly increases the difficulty for reverse engineers attempting to reconstruct the original exception handling logic, thereby enhancing obfuscation without compromising functional integrity.
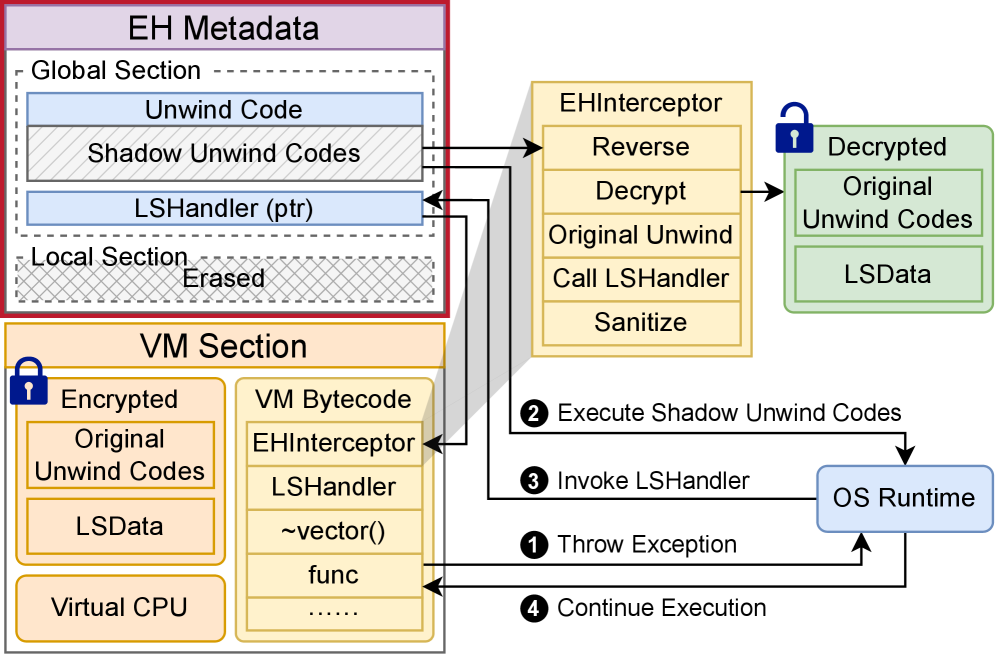
The Language of Deception: Tailoring Obfuscation to the Core
The virtual machine’s capacity to accurately manage exceptions hinges on its use of specialized components: `LSData` and `LSHandler`. `LSData` provides the VM with crucial language-specific information regarding data types, object layouts, and exception characteristics, effectively allowing it to ‘understand’ how exceptions manifest in different programming languages. Complementing this is the `LSHandler`, which acts as a dispatcher, directing exception handling procedures according to the rules defined by the `LSData`. This dynamic interplay ensures that exceptions originating from a virtualized application are not only detected but also processed correctly, even if the application’s exception handling mechanisms differ significantly from the host system’s native environment. Consequently, the framework avoids potentially catastrophic errors and maintains system stability by properly interpreting and responding to language-specific exception behaviors.
The framework’s exception handling relies on a coordinated effort between the Global Unwind Section and the Local Unwind Section to meticulously manage the process of stack unwinding and resource cleanup. The Global Unwind Section provides a comprehensive map of the program’s overall structure, enabling the system to identify critical cleanup points across function boundaries. Complementing this, the Local Unwind Section focuses on exception-specific details within individual functions, ensuring that all allocated resources-such as memory and file handles-are correctly released. This dual-layered approach guarantees a robust and reliable response to exceptions, preventing memory leaks and maintaining system stability even in the face of unexpected errors. By working in tandem, these sections create a safety net that ensures orderly program termination and prevents cascading failures.
The virtual machine’s security posture is significantly strengthened through the deliberate integration of language-specific components for exception handling. This framework doesn’t rely on generic approaches; instead, it employs LSData and LSHandler to accurately interpret and manage exceptions as they arise within the virtualized environment. While this meticulous approach yields a robust and reliable protection mechanism, it does introduce a trade-off: implementing this “EH Shadowing” technique currently results in an average file size overhead of 66.26%. This increase reflects the necessary inclusion of language-specific metadata and handling routines, demonstrating that a heightened level of security necessitates a corresponding increase in resource utilization.
XuanJia: Beyond Protection, A System of Controlled Complexity
XuanJia represents a novel approach to safeguarding software through a virtualization-based obfuscation framework. This system doesn’t simply scramble code; it constructs a virtual machine layer to execute the original binary, effectively concealing its underlying logic. Crucially, XuanJia extends this protection beyond typical code sections to encompass exception handling mechanisms – a frequently targeted area for reverse engineering. By safeguarding how the program responds to errors and unexpected events, XuanJia significantly raises the bar for attackers attempting to understand or manipulate the software’s behavior. This dual-layered defense – virtualized code execution and protected exception handling – creates a robust barrier against disassembly, debugging, and other reverse engineering techniques, making it substantially more difficult to extract the original source code or algorithm.
XuanJia employs a technique called handler diversification, a sophisticated method of shielding code logic from reverse engineers. Rather than relying on a single, predictable exception handler, the framework generates numerous, structurally unique handlers. This proliferation of handlers obscures the program’s control flow, as an attacker cannot reliably predict which handler will be invoked during an exception. Each handler is deliberately different, requiring significantly more effort to analyze and understand, and effectively disrupting attempts to reconstruct the original program logic. The increased complexity introduced by diversified handlers makes it substantially harder for malicious actors to pinpoint vulnerabilities or extract sensitive information from the protected binary.
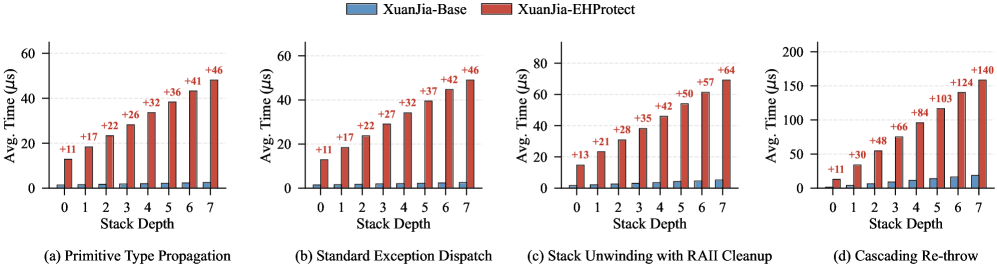
XuanJia presents a multifaceted approach to binary obfuscation, integrating virtualization techniques with robust exception handling and handler diversification to significantly impede reverse engineering efforts. This combined strategy creates a complex defensive layer, making it substantially more difficult for malicious actors to analyze and understand protected code. Importantly, XuanJia achieves this heightened security without imposing excessive performance penalties; benchmarks demonstrate a runtime overhead comparable to existing obfuscation solutions – ranging from 120x to 337x – while maintaining a relatively small increase in file size, typically between 2.1x and 11.2x. This balance between security and practicality positions XuanJia as a compelling option for developers seeking to safeguard intellectual property and enhance the resilience of their applications.
The creation of XuanJia embodies a spirit of deliberate disruption. It doesn’t simply accept the established boundaries of binary protection; instead, it actively challenges them by obscuring exception handling – a critical, often overlooked component. As Grace Hopper famously stated, “It’s easier to ask forgiveness than it is to get permission.” This framework operates on a similar principle. XuanJia intentionally complicates the reverse engineering process, forcing attackers to navigate a deliberately distorted landscape. By shadowing exception metadata while preserving ABI compatibility, it introduces a calculated impedance to analysis, effectively testing the limits of existing disassemblers and debuggers. The system’s resilience isn’t built on preventing access, but on making that access meaningfully more difficult, mirroring Hopper’s pragmatic approach to innovation.
Beyond the Veil
XuanJia’s approach to shadowing exception metadata presents a compelling, if predictable, escalation in the arms race between code protectors and reverse engineers. The framework effectively raises the cost of analysis, but the inherent limitations of any virtualization-based system remain. A determined analyst will inevitably probe the boundaries of the virtual machine, seeking leaks in the abstraction layer – not through brute force, but by exploiting inconsistencies between the virtualized and native execution environments. The true challenge, then, isn’t simply obfuscating the code, but making the cost of discerning that obfuscation greater than the value of the protected asset.
Future work should investigate dynamic, context-aware obfuscation techniques. Static virtualization, while effective, is ultimately a fixed target. Introducing runtime variability – altering the VM’s instruction set or memory layout based on environmental factors – could significantly increase the complexity of reverse engineering. Furthermore, exploring the interplay between virtualization and other obfuscation methods – control-flow flattening, instruction substitution, and even deliberately introduced vulnerabilities – might yield synergistic effects.
Ultimately, XuanJia, like all security measures, merely delays the inevitable. It’s a temporary reprieve, a beautifully constructed illusion. The interesting question isn’t whether it can be broken, but how – and what novel insights that process will reveal about the underlying architecture it sought to conceal. The system’s value lies not in its imperviousness, but in the intellectual friction it generates.
Original article: https://arxiv.org/pdf/2601.10261.pdf
Contact the author: https://www.linkedin.com/in/avetisyan/
See also:
- God Of War: Sons Of Sparta – Interactive Map
- Someone Made a SNES-Like Version of Super Mario Bros. Wonder, and You Can Play it for Free
- Epic Games Store Free Games for November 6 Are Great for the Busy Holiday Season
- How to Unlock & Upgrade Hobbies in Heartopia
- Sony Shuts Down PlayStation Stars Loyalty Program
- Battlefield 6 Open Beta Anti-Cheat Has Weird Issue on PC
- The Mandalorian & Grogu Hits A Worrying Star Wars Snag Ahead Of Its Release
- One Piece Chapter 1175 Preview, Release Date, And What To Expect
- Overwatch is Nerfing One of Its New Heroes From Reign of Talon Season 1
- Meet the Tarot Club’s Mightiest: Ranking Lord Of Mysteries’ Most Powerful Beyonders
2026-01-18 03:02