Author: Denis Avetisyan
Researchers have developed a novel cache architecture that adapts to security needs on the fly, offering strong defenses against increasingly sophisticated attacks.
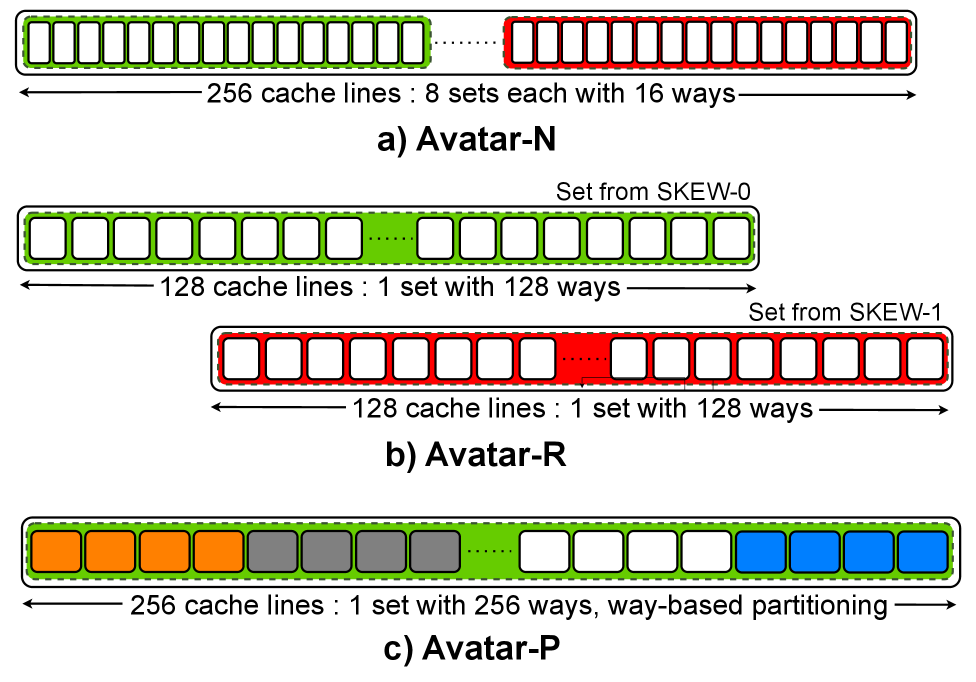
Avatar is a morphable LLC design that dynamically transitions between non-secure, randomized secure, and partitioned secure modes to minimize performance impact while maximizing protection.
Modern multi-core processors remain vulnerable to cross-core cache attacks despite decades of research into secure last-level cache (LLC) designs. This paper introduces ‘The Avatar Cache: Enabling On-Demand Security with Morphable Cache Architecture’, presenting a novel LLC that dynamically adapts between non-secure, randomized secure, and partitioned secure modes to mitigate both conflict- and occupancy-based attacks. Avatar achieves strong security guarantees – including a 10^{30}-year eviction rate in randomized mode – with minimal overhead, demonstrating less than 3% performance degradation and only 1.5% storage increase. Could this morphable approach finally bridge the gap between security and performance, paving the way for widespread adoption of secure LLCs in mainstream processors?
The Inherent Vulnerability of Shared Cache Resources
Modern computing depends critically on processor caches – small, fast memory stores that accelerate access to frequently used data. However, this performance enhancement introduces a significant security vulnerability. These caches are shared resources, meaning multiple processes or users can access them, creating opportunities for side-channel attacks. Rather than directly attacking encryption or authentication, these attacks exploit information leaked through subtle changes in cache behavior – things like access times or eviction patterns. An attacker can observe these patterns to infer sensitive data, such as cryptographic keys or private user information, without ever directly accessing the protected data itself. This presents a considerable challenge, as traditional security measures often incur substantial performance overhead, forcing designers to balance security and speed in increasingly complex ways.
Modern processors, while incredibly efficient, rely on caches – small, fast memory stores – that are susceptible to side-channel attacks. These attacks don’t target flaws in algorithms, but rather exploit variations in execution time caused by how data interacts with the cache. Conflict-based attacks observe which memory locations share a cache line; by monitoring access patterns, an attacker can deduce information about the data being processed. Occupancy-based attacks, conversely, analyze how full the cache is during computation, revealing details based on the timing of cache misses and evictions. Both techniques fundamentally leak information through observing the processor’s own internal behavior, making them particularly insidious as they bypass traditional security measures focused on data content itself.
Addressing the long-standing trade-off between cache security and performance, a novel cache architecture, termed Avatar, presents a robust defense against conflict-based side-channel attacks. Previous security implementations often incurred substantial performance penalties; however, Avatar achieves a demonstrably high security guarantee – a Successful Attack Extraction (SAE) frequency of only once in 1030 years – without significantly impacting operational speed. This breakthrough is achieved through a carefully engineered system that mitigates the information leakage inherent in shared cache resources, offering a substantial improvement in both security and efficiency for modern processors. The design effectively minimizes the attacker’s ability to correlate data access patterns with sensitive information stored within the cache, establishing a new benchmark for cache security.
Avatar LLC: Adaptable Security Through Morphable Caching
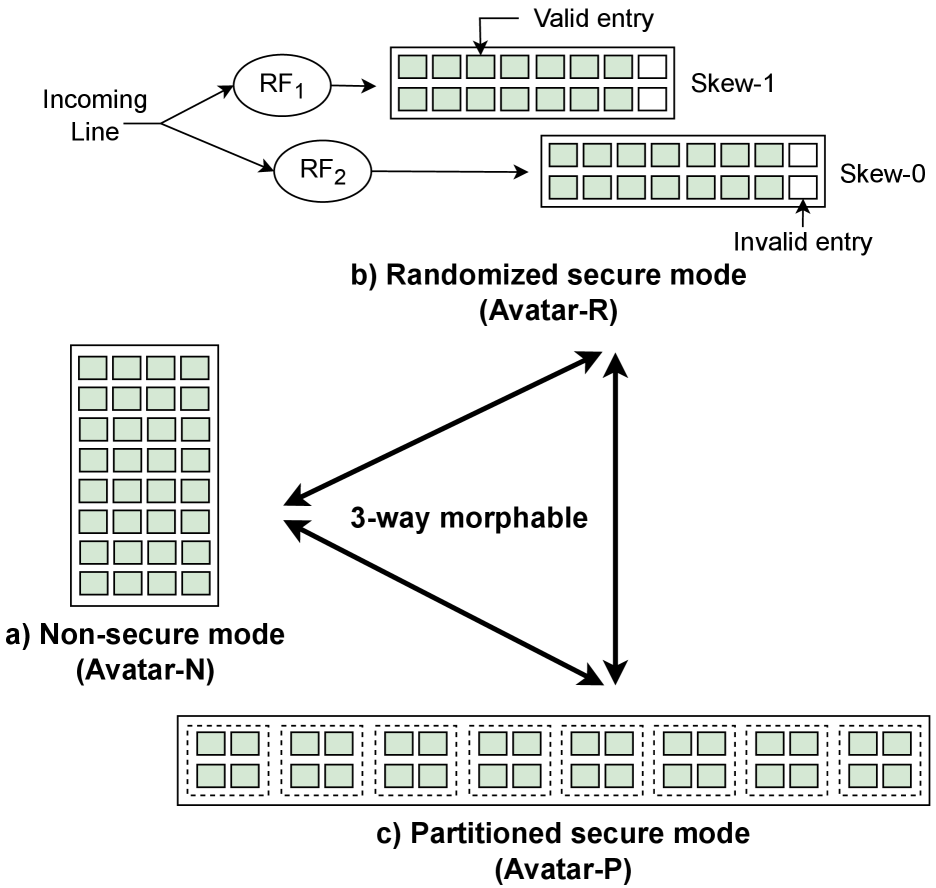
Avatar LLC implements a morphable Last-Level Cache (LLC) architecture with three operational modes to balance performance and security. The non-secure mode prioritizes speed with standard cache operation. Randomized secure mode introduces probabilistic data placement to hinder adversarial cache-based attacks. Finally, partitioned secure mode physically isolates cache lines, providing strong separation for sensitive data but potentially reducing capacity available to each application. This morphing capability allows the LLC to adapt to varying security requirements without substantial performance degradation.
Avatar LLC’s architecture is based on a set-associative cache organization, a design choice that balances performance and complexity. This structure divides the cache into sets, with each set containing multiple cache lines, or ways, allowing for parallel access to data. Data is stored in two primary components: Tag Stores and Data Stores. Tag Stores hold metadata about cached data, including the address tags used for hit/miss determination, while Data Stores contain the actual cached data itself. This separation allows for efficient lookup and retrieval; when a request arrives, the Tag Store is checked first to determine if the data is present, and if so, the corresponding data is then fetched from the Data Store. The set-associative organization, combined with dedicated Tag and Data Stores, minimizes conflict misses and provides fast access to frequently used data.
Avatar LLC facilitates a dynamic balance between performance and security through its selectable operating modes, allowing system resources to be allocated based on application-specific requirements. Performance testing, utilizing the SPEC CPU2017 and GAP benchmark suites, demonstrates that this adaptability incurs a minimal overhead of only 0.25% when compared to the non-secure operating mode, indicating a negligible impact on overall system throughput while providing enhanced security options.
Disrupting Attack Vectors: Randomized Security in Action
Avatar-R’s randomized secure mode mitigates cache conflicts by implementing a high-associativity cache design. Traditional caches typically have low associativity (e.g., 2-way or 4-way), leading to predictable placement of data and increasing vulnerability to attacks that exploit cache timing. High associativity-increasing the number of possible locations for each cache line-randomizes this placement. This makes it significantly more difficult for an attacker to reliably predict which cache line will hold a specific data element, thereby disrupting patterns used in side-channel attacks that rely on observing cache hits and misses. The increased number of possible locations effectively distributes the data, reducing the probability of conflict and improving security.
Avatar-R’s security approach draws heavily from the ‘Mirage’ system, specifically targeting the predictability of cache access patterns commonly exploited in side-channel attacks. By introducing randomization into cache set selection, Avatar-R prevents attackers from reliably correlating data access with specific cache lines. This disruption makes it significantly more difficult to construct successful side-channel attacks, as the attacker can no longer confidently predict where data will be located in the cache based on observed timing or power consumption. The effectiveness of this technique lies in obscuring the relationship between program execution and cache behavior, thereby increasing the attacker’s uncertainty and the complexity of mounting an effective attack.
Avatar-R utilizes the Bucket-and-Balls Model, a probabilistic analysis technique, to evaluate cache set contention and inform the randomization strategy. This model allows for the quantification of conflict probabilities within the cache hierarchy. Coupled with Global Random Replacement, where cache lines are evicted randomly regardless of access history, Avatar-R effectively disrupts predictable cache access patterns. Performance testing demonstrates a negligible overhead of only 0.25% when compared to a non-secure baseline, indicating a practical implementation without significant performance penalties.
Robust Isolation: Partitioned Security for Critical Data
Avatar-P establishes a robust security framework by strategically dividing the Last-Level Cache (LLC) into discrete, fixed partitions. Each of these partitions is specifically designated for a unique security domain, effectively creating isolated containers for sensitive data. This architectural approach ensures that data belonging to one domain remains entirely separate from others, preventing unauthorized access or interference. By physically segregating data within the cache hierarchy, Avatar-P minimizes the potential for cross-domain attacks and strengthens the overall confidentiality and integrity of the system. The rigid partitioning scheme forms the core of the security model, allowing for predictable and verifiable isolation between critical applications and sensitive data sets.
Static Partitioning and Secure Domain IDs (SDIDs) form the cornerstone of data isolation within the system. By pre-allocating fixed portions of the Last-Level Cache (LLC) to specific security domains, the architecture prevents unauthorized access and interference between different data sets. Each domain receives a unique SDID, which acts as a logical identifier and enables the hardware to enforce strict partitioning boundaries. This method ensures that data belonging to one domain remains entirely inaccessible to others, even in the event of malicious code execution or software vulnerabilities, thereby creating a highly secure environment for sensitive applications and critical data.
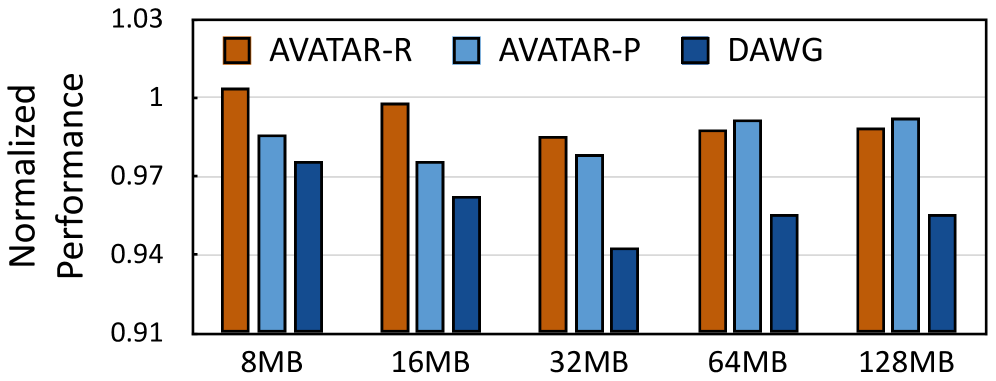
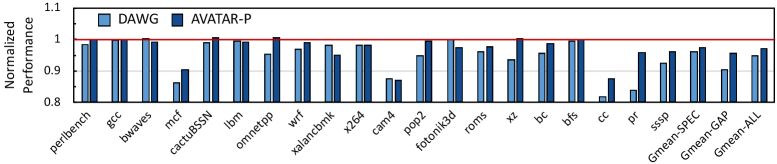
Avatar-P establishes a resilient defense against both conflict-based and occupancy-based attacks, crucial for safeguarding sensitive data within modern computing systems. By partitioning the Last-Level Cache (LLC), the system prevents malicious code from interfering with critical applications or accessing confidential information residing in other partitions. Importantly, this enhanced security is achieved with a minimal performance impact; evaluations demonstrate a mere 3% overhead compared to a non-secure baseline utilizing way-partitioned LLC. Furthermore, the system maintains modest increases in power consumption – 2.7% static overhead – and dynamic access energy, which increases by 11.11% compared to the baseline, demonstrating a practical balance between security and efficiency for demanding applications.
The Avatar cache architecture, with its dynamic shifts between security modes, embodies a dedication to provable correctness. It’s a system meticulously designed to eliminate ambiguity in security guarantees-a solution is either secure, or it is not. This pursuit of mathematical purity in hardware design resonates with a core principle: “Most good programmers do programming as an exercise in frustration.” Linus Torvalds’ observation speaks to the inherent challenge of achieving elegance and absolute certainty in complex systems. Avatar’s morphable nature, allowing it to adapt to threat landscapes, strives to minimize those frustrating ambiguities and achieve a demonstrably correct secure state, much like a well-proven algorithm.
What Lies Ahead?
The Avatar cache presents a notable attempt to reconcile performance with the ever-present threat of side-channel attacks. However, the architecture, while promising, implicitly assumes a certain threat model. The efficacy of dynamic mode switching rests on the precision with which an attack can be detected, not merely anticipated. The question remains: can any detection mechanism truly outpace the ingenuity of an attacker determined to extract information, or is this merely a shifting of the security perimeter?
Future work must address the limitations inherent in relying on randomization and partitioning alone. Formal verification of the mode-switching logic-a proof of its correctness and resistance to manipulation-is not simply desirable; it is essential. Without such a proof, the system remains vulnerable to subtle flaws, and the claim of “strong security guarantees” is, at best, an optimistic conjecture. The true metric of success will not be performance benchmarks, but the demonstrable impossibility of extracting secrets, regardless of computational resources.
Ultimately, the pursuit of cache security necessitates a more fundamental re-evaluation of how data is represented and accessed. Morphable architectures are a step in the right direction, but they treat the symptom, not the disease. The ideal solution lies not in masking vulnerabilities, but in eliminating them at the architectural level – a goal that demands a return to first principles and a rigorous mathematical foundation.
Original article: https://arxiv.org/pdf/2602.06433.pdf
Contact the author: https://www.linkedin.com/in/avetisyan/
See also:
- Epic Games Store Free Games for November 6 Are Great for the Busy Holiday Season
- EUR USD PREDICTION
- Battlefield 6 Open Beta Anti-Cheat Has Weird Issue on PC
- How to Unlock & Upgrade Hobbies in Heartopia
- Sony Shuts Down PlayStation Stars Loyalty Program
- The Mandalorian & Grogu Hits A Worrying Star Wars Snag Ahead Of Its Release
- Someone Made a SNES-Like Version of Super Mario Bros. Wonder, and You Can Play it for Free
- ARC Raiders Player Loses 100k Worth of Items in the Worst Possible Way
- Unveiling the Eye Patch Pirate: Oda’s Big Reveal in One Piece’s Elbaf Arc!
- God Of War: Sons Of Sparta – Interactive Map
2026-02-09 12:23