Author: Denis Avetisyan
A new analysis reveals widespread public key reuse across diverse cryptocurrencies, exposing vulnerabilities in privacy and enabling improved entity clustering.
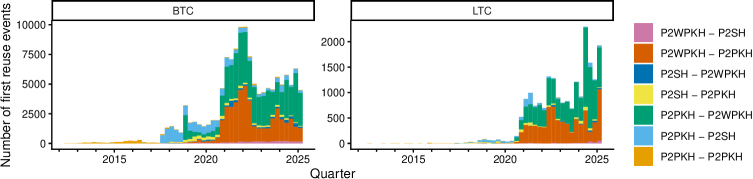
The study demonstrates significant cross-chain key reuse between UTXO and account-based cryptocurrencies, impacting privacy and traceability.
While cryptocurrency users are routinely warned against address reuse for privacy reasons, the extent of shared key usage across different blockchain networks remains largely unquantified. This paper, ‘Reuse of Public Keys Across UTXO and Account-Based Cryptocurrencies’, addresses this gap by demonstrating significant cross-chain key reuse between disparate systems like Bitcoin, Ethereum, and others. Our analysis reveals that cryptographic keys are extensively and actively shared, impacting user privacy and potentially enabling unintended linkages between identities. Could these findings necessitate a re-evaluation of current key management practices and privacy assumptions within the broader cryptocurrency ecosystem?
The Erosion of Anonymity: Key Reuse in a Decentralized World
Despite the robust cryptographic foundations of most cryptocurrencies, user behavior introduces a significant vulnerability: the inadvertent reuse of public keys across multiple platforms and transactions. This practice effectively erodes the privacy intended by these systems, as a single key can link seemingly disparate activities and expose financial connections. While public keys are designed to identify a user’s wallet without revealing their identity, consistent reuse transforms them into readily trackable identifiers, enabling malicious actors to profile users, correlate their transactions, and potentially target them for attacks. The underlying security protocols remain sound, but this human factor creates a pathway for sophisticated tracking and fund loss, effectively undermining the intended anonymity and security features of the cryptocurrency ecosystem.
The widespread practice of reusing cryptographic public keys across multiple cryptocurrency platforms presents a significant vulnerability, compromising user privacy and creating opportunities for advanced tracking and potential financial loss. A recent analysis uncovered a staggering 1,604,614 instances of key reuse, demonstrating the prevalence of this risky behavior. When a single key is used across multiple addresses or services, it allows malicious actors to correlate transactions and potentially de-anonymize users, revealing their holdings and transaction history. This interconnectedness effectively breaks the intended privacy safeguards of many cryptocurrencies and enables sophisticated surveillance, ultimately exposing individuals to targeted attacks and the risk of fund theft. The sheer scale of identified key reuse highlights an urgent need for improved user education and the development of tools to detect and mitigate this growing threat.
The architecture underlying a cryptocurrency significantly impacts the ease with which key reuse vulnerabilities can be detected and addressed. UTXO-based systems, like Bitcoin, present a challenge due to their privacy-focused design; transactions aren’t directly linked to specific addresses, obscuring patterns of reuse that might otherwise flag compromised keys. Conversely, account-based models, such as those used by Ethereum, maintain a clear association between transactions and accounts, simplifying the identification of reused keys but simultaneously increasing the potential for surveillance. This distinction necessitates tailored analytical approaches; while UTXO systems require sophisticated clustering techniques to reveal reuse, account-based systems benefit from direct monitoring of account activity. Effectively mitigating this risk, therefore, demands an understanding of these fundamental differences in transactional structure and the development of targeted security measures for each model.
Key Derivation and the Fragility of Unique Identities
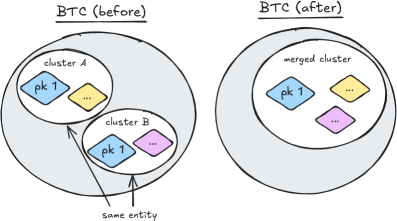
Hierarchical Deterministic (HD) wallets and deterministic key derivation are core technologies for generating and managing cryptographic keys, offering advantages in backup and recovery. However, improper implementation can lead to key reuse, compromising privacy and security. Deterministic key derivation relies on a seed value and a derivation path to generate a series of unique keys; if the same derivation path is used repeatedly, the same private key will be generated each time. This reuse negates the security benefits of unique key pairs and allows for transaction linking, potentially exposing user identities and financial activity. Careful implementation requires robust key management practices to ensure each transaction utilizes a unique, newly derived key.
The Unspent Transaction Output (UTXO) model necessitates clustering algorithms to link multiple transactions to a common entity, as individual transactions don’t inherently reveal ownership. The Multiple-Input Heuristic is a commonly employed technique for this purpose, grouping transactions sharing common inputs. However, the reuse of cryptographic keys significantly complicates this clustering process; when the same key is used across multiple, unrelated transactions, it creates false positives, incorrectly associating those transactions with a single entity and obscuring the true transactional graph. This key reuse introduces noise into the clustering data, reducing the accuracy of entity identification and potentially misrepresenting the flow of funds within the UTXO-based system.
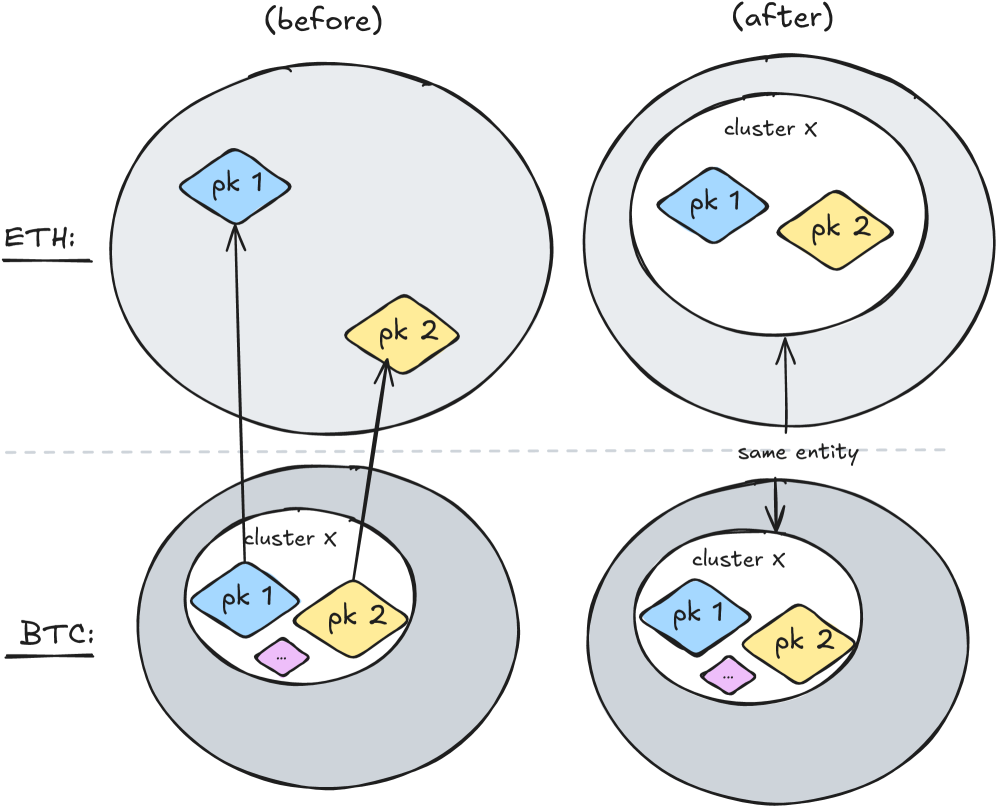
De-anonymizing transactions within account-based systems, such as those employed by Tornado Cash, necessitates detailed analysis of on-chain data to trace fund flows; however, the practice of key reuse significantly complicates this process. Our research identified a total of 831,056 keys that have been reused across both UTXO-based and account-based transaction models. This figure represents approximately 50% of all observed instances of key reuse, indicating a substantial overlap in address usage between different blockchain architectures and hindering efforts to accurately attribute transactions to unique entities.
Tracing the Threads: Cross-Chain Key Reuse Analysis
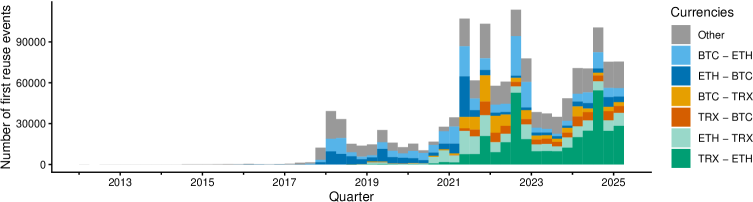
Cross-chain analysis utilizes specialized tools and techniques to identify instances where a single public key is used to authorize transactions on multiple, distinct blockchains. This process reveals connections between seemingly unrelated on-chain activities, as the same address controls funds or smart contract interactions across different ledger systems. The capability to detect public key reuse is crucial because it bypasses the inherent isolation between blockchains, allowing for the tracing of funds and potentially linking illicit activities or compromised accounts across multiple ecosystems. Identifying such reuse requires aggregating and correlating transaction data from various sources, employing sophisticated pattern recognition algorithms, and resolving discrepancies in address formats and data representations.
Cross-chain key reuse detection is a critical technique for establishing links between transactions occurring on different blockchains and identifying potential security vulnerabilities. Recent analysis has revealed 497,178 instances of a single public key being used across both the Bitcoin and Ethereum blockchains. This practice, while not inherently malicious, presents significant risks; if a private key associated with a reused public key is compromised on one chain, all funds controlled by that key on all connected chains are potentially at risk. The prevalence of this behavior highlights a substantial attack vector and underscores the importance of monitoring for and mitigating key reuse across multiple blockchain networks.
Cross-chain transaction analysis is increasingly complex due to the proliferation of blockchain bridges, such as the Avalanche Bridge. These bridges facilitate the transfer of assets between disparate blockchains but introduce new potential attack vectors. Specifically, vulnerabilities within the bridge’s smart contracts or consensus mechanisms can be exploited, allowing malicious actors to intercept or manipulate transactions. Analysis must therefore extend beyond on-chain data to include the specific architecture and security protocols of each bridge utilized, adding significant overhead to the investigative process and requiring specialized tooling to effectively trace fund flows across these interconnected systems.
The Architecture of Trust: Safeguarding Interoperability
The Avalanche Bridge, designed to connect disparate blockchain networks and enable the seamless transfer of assets, employs Intel Software Guard Extensions (SGX) as a crucial component for safeguarding sensitive transaction data. This technology creates a secure enclave within the processor, isolating critical operations from the potentially compromised operating system and other software. However, this reliance introduces a single point of failure; a successful exploit of the SGX enclave – through side-channel attacks, hardware vulnerabilities, or compromised code – could expose the private keys used to authorize cross-chain transactions. Consequently, the security of the entire bridge, and the assets it facilitates, is directly tied to the robustness of the SGX implementation and its ongoing protection against evolving threats, demanding continuous monitoring and proactive security measures.
The Segregated Witness (SegWit) upgrade fundamentally altered Bitcoin’s transaction structure, and its impact extends to bolstering the security of cross-chain analysis. Prior to SegWit, transaction malleability – the ability for transaction IDs to change before confirmation – complicated tracking funds across different blockchains. By separating the signature data from the core transaction data, SegWit created a more stable and predictable transaction ID. This stability is crucial for reliably linking transactions across chains, as analysts depend on consistent identifiers to trace the flow of funds. The upgrade doesn’t directly enhance cryptographic security, but by mitigating malleability, it provides a more robust foundation for accurate cross-chain tracking, allowing for more effective identification of potentially illicit activity and improved understanding of fund movements within the broader cryptocurrency ecosystem.
At the heart of cryptocurrency security lies the Elliptic Curve Digital Signature Algorithm (ECDSA), a cryptographic technique essential for verifying transactions and controlling asset ownership across all analyzed blockchains. Recent investigations leveraging this foundational algorithm have revealed a concerning trend: widespread key reuse. Analysis identified a staggering 1,429,008 instances of actively reused cryptographic keys, presenting a significant vulnerability for potential double-spending attacks and compromised privacy. Importantly, cross-chain key reuse analysis directly linked 203 of these compromised keys to the privacy-focused mixing service Tornado Cash, highlighting how seemingly anonymous transactions can be traced through patterns of key management and revealing potential connections to illicit activities. This underscores the critical need for improved key management practices and enhanced monitoring tools to mitigate risks within the cryptocurrency ecosystem.
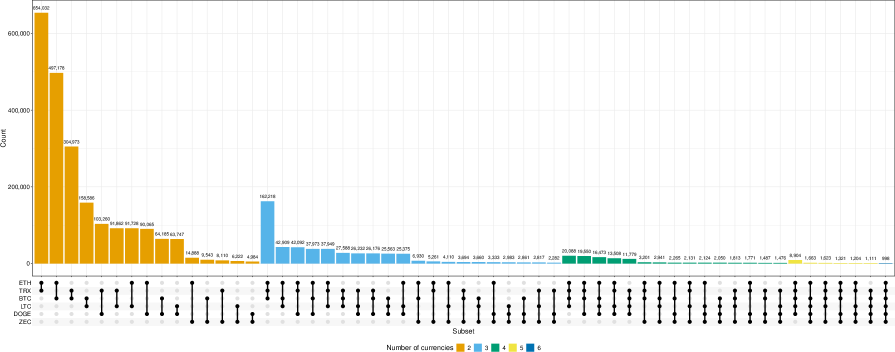
The study’s findings regarding widespread public key reuse across seemingly disparate cryptocurrencies highlight an inherent tension within system design. While efficiency encourages practices like key reuse, it simultaneously introduces vulnerabilities and erodes the intended privacy guarantees. As Vinton Cerf observed, “Any sufficiently advanced technology is indistinguishable from magic.” This ‘magic’ of interconnected systems, however, reveals a predictable pattern: simplification, in this case reusing keys for convenience, invariably carries a future cost. The paper demonstrates how this cost manifests as increased traceability and the potential for powerful entity clustering, effectively diminishing the anonymity these systems initially promised. It’s a reminder that technical debt isn’t simply about code; it’s the system’s memory, and in this instance, that memory is a shared public key.
What Lies Ahead?
The demonstrated prevalence of public key reuse across ostensibly disparate cryptocurrencies does not represent a flaw, but rather an inevitability. Systems, even those built on cryptographic foundations, do not escape the constraints of their components. The reuse observed is a symptom of finite address spaces and the human tendency toward simplification-a practical compromise enacted across networks. The observed clustering, while enabling entity identification, merely delays the inevitable erosion of financial privacy. It is not a breach, but a gradual unveiling.
Future work will likely focus on mitigating these effects-attempting to artificially extend the illusion of anonymity. However, such efforts are akin to rearranging deck chairs. The core issue isn’t technical; it’s systemic. Increased sophistication in key management will undoubtedly emerge, but these solutions will merely raise the cost-and therefore the selectivity-of surveillance. The pursuit of perfect privacy is a phantom; the goal, realistically, becomes increased resilience against observation.
Ultimately, this research highlights a fundamental truth: stability is often just a delayed manifestation of decay. The study of cryptocurrency isn’t simply about building secure systems, but about understanding how they age, and accepting that time, not malice, is the ultimate adversary. The question isn’t whether privacy will be compromised, but when, and what new forms of digital existence will emerge from the ruins.
Original article: https://arxiv.org/pdf/2601.19500.pdf
Contact the author: https://www.linkedin.com/in/avetisyan/
See also:
- Mewgenics Tink Guide (All Upgrades and Rewards)
- Top 8 UFC 5 Perks Every Fighter Should Use
- One Piece Chapter 1174 Preview: Luffy And Loki Vs Imu
- How to Play REANIMAL Co-Op With Friend’s Pass (Local & Online Crossplay)
- How to Discover the Identity of the Royal Robber in The Sims 4
- How to Unlock the Mines in Cookie Run: Kingdom
- Sega Declares $200 Million Write-Off
- Full Mewgenics Soundtrack (Complete Songs List)
- Starsand Island: Treasure Chest Map
- All 100 Substory Locations in Yakuza 0 Director’s Cut
2026-01-28 17:30