Author: Denis Avetisyan
As electric vertical takeoff and landing (eVTOL) aircraft prepare for takeoff, ensuring robust cybersecurity is paramount for safe and reliable urban air mobility.
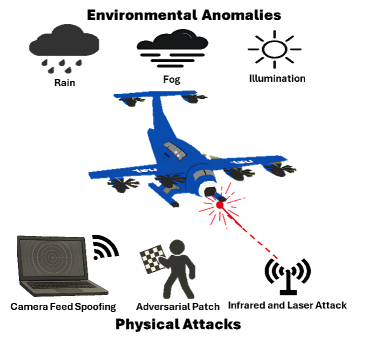
This review surveys the unique security challenges facing advanced air mobility platforms and details potential solutions for protecting critical systems from cyber threats.
While advancements in electric vertical takeoff and landing (eVTOL) aircraft promise a revolution in urban air mobility, ensuring their cybersecurity remains a critical, often overlooked challenge. This paper, ‘A Survey of Security Challenges and Solutions for Advanced Air Mobility and eVTOL Aircraft’, comprehensively examines potential vulnerabilities across AAM systems, drawing parallels with existing aviation and unmanned aerial system (UAS) threats. The survey identifies key attack vectors-including GPS interference, radio frequency misuse, and software exploits-and proposes mitigation strategies to safeguard system integrity, availability, and confidentiality. As AAM ecosystems mature, what novel defense mechanisms will be required to proactively address evolving cyber threats and maintain public trust in these increasingly autonomous platforms?
The Promise and Peril of Airborne Transit
Electric Vertical Takeoff and Landing (eVTOL) aircraft represent a potentially transformative shift in urban transportation paradigms. These aircraft, powered by electric motors and designed for vertical operation, promise to alleviate congestion and dramatically reduce commute times by bypassing ground-based infrastructure. Unlike traditional helicopters, eVTOLs aim for quieter operation and reduced emissions, contributing to more sustainable urban environments. Proponents envision a future where on-demand air travel becomes a reality, offering a swift and efficient alternative for both passengers and cargo within metropolitan areas. This new mode of transport could reshape city planning, enabling decentralized hubs and fostering economic growth by improving accessibility and connectivity, though realizing this vision requires addressing challenges related to infrastructure, regulation, and public acceptance.
The anticipated benefits of urban air mobility, reliant on electric vertical takeoff and landing aircraft, are increasingly intertwined with significant cybersecurity challenges. These advanced aerial systems depend heavily on the Global Navigation Satellite System (GNSS) for precise positioning and data links for crucial communications – systems inherently vulnerable to both unintentional interference and deliberate malicious attacks. Disruptions to GNSS signals, whether caused by atmospheric conditions, jamming devices, or spoofing attempts, can lead to navigational errors or complete loss of control. Compromised data links could enable unauthorized access to aircraft systems, potentially leading to data breaches, operational disruptions, or even safety-critical failures. Consequently, a proactive and robust cybersecurity framework is not merely a preventative measure, but an essential prerequisite for realizing the safe and reliable integration of urban air mobility into modern airspace.
Given the projected integration of electric Vertical Takeoff and Landing (eVTOL) aircraft into increasingly congested urban airspace, a robust cybersecurity framework is paramount. These systems, heavily reliant on satellite navigation and wireless communication for safe operation, present attractive targets for both unintentional interference and deliberate malicious attacks. Compromised positioning data or disrupted control signals could have catastrophic consequences, necessitating a shift from reactive security measures to a proactive approach. This includes rigorous vulnerability assessments throughout the entire lifecycle – from design and manufacturing to operation and maintenance – alongside the implementation of resilient communication protocols, intrusion detection systems, and robust authentication mechanisms. Prioritizing cybersecurity now is not merely a technical consideration, but a fundamental requirement for realizing the benefits of urban air mobility and ensuring public trust in this emerging technology.
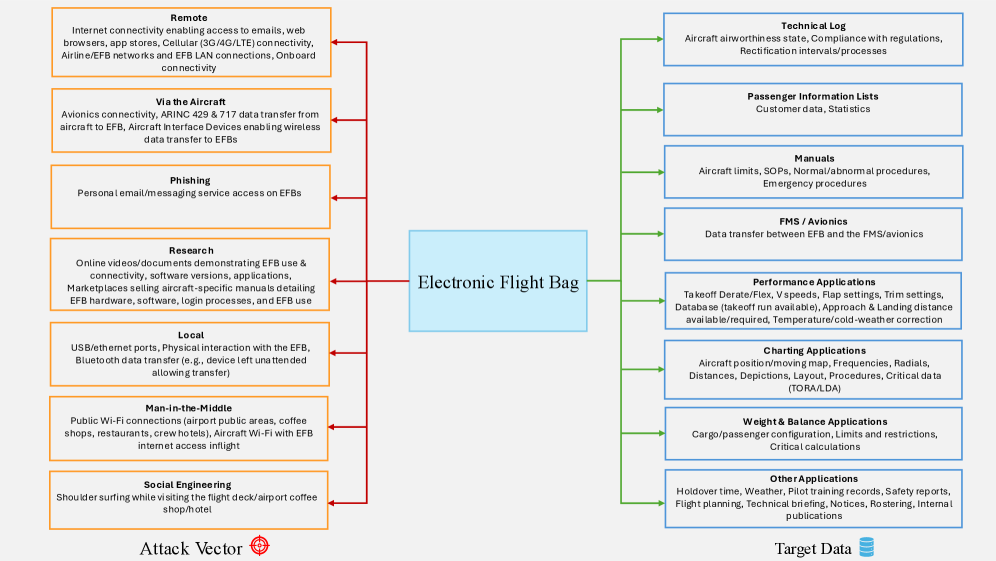
Securing the Skies: A Foundation of Digital Integrity
The operational safety of eVTOL aircraft is directly contingent upon comprehensive cybersecurity measures protecting all interconnected systems. These aircraft rely heavily on digital data for navigation, flight control, communication, and passenger safety services; compromise of this data could lead to system malfunctions, loss of control, or unauthorized access. Specifically, vulnerabilities in software, communication channels, and data storage present significant risks. A layered security approach, encompassing secure boot processes, robust authentication, data encryption both in transit and at rest, and continuous monitoring for anomalous activity, is essential to mitigate these threats and ensure the integrity and availability of critical flight data. Furthermore, the increasing connectivity of eVTOLs to ground infrastructure and cloud-based services expands the attack surface, necessitating proactive threat intelligence and incident response capabilities.
The operational safety of eVTOL aircraft is directly dependent on the secure functioning of core aviation systems, notably Flight Management Systems (FMS), Traffic Collision Avoidance Systems (TCAS), and Automatic Dependent Surveillance-Broadcast (ADS-B). Compromise of FMS could result in navigational errors or unintended flight paths. Exploitation of TCAS could lead to the suppression of critical warnings, increasing the risk of mid-air collisions. Manipulation of ADS-B data could generate false positional information, disrupting air traffic control and potentially creating hazardous situations. Consequently, these systems represent primary targets for malicious actors and require layered cybersecurity defenses to maintain the integrity and availability of the data they process and transmit.
Robust authentication and encryption protocols are foundational to securing eVTOL aircraft systems against unauthorized access and data tampering. These protocols establish verified identities and protect the confidentiality and integrity of sensitive data transmitted between aircraft components and ground-based infrastructure. Supplementing these protocols, Machine Learning-based Intrusion Detection Systems (NIDS) provide an additional layer of defense by actively monitoring critical communication channels. Recent evaluations of NIDS deployed to protect protocols like remote desktop protocol have yielded a true positive rate of 0.863, indicating effective threat detection, coupled with a remarkably low false positive rate of 0.0001, minimizing disruptive alerts and maintaining operational efficiency.
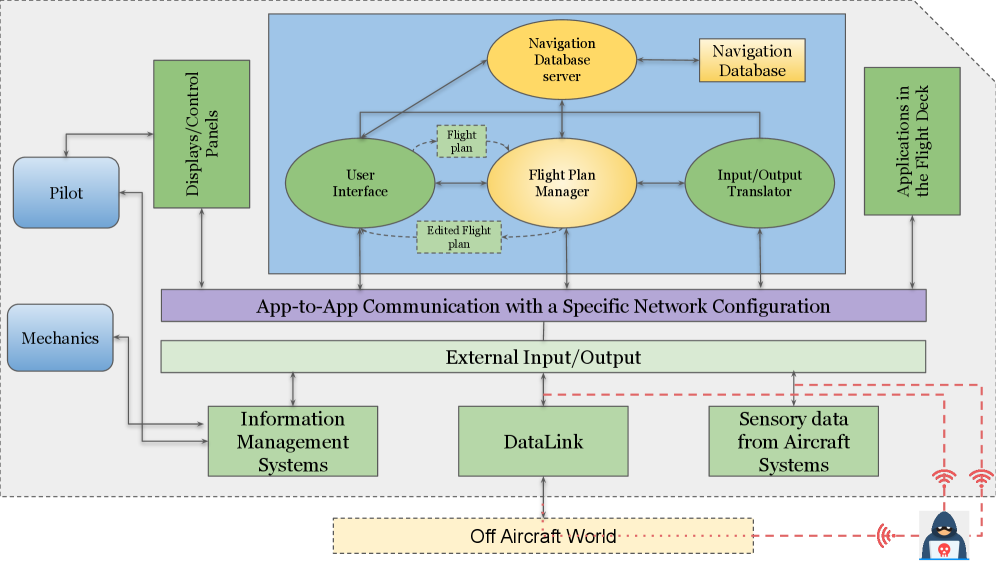
Resilience Through Layered Defenses
A layered defense strategy enhances system resilience by implementing redundancy and multi-sensor fusion. Redundancy involves duplicating critical components and data pathways, ensuring continued operation even if one element fails or is compromised. Multi-sensor fusion combines data from diverse sensor types – such as radar, lidar, cameras, and inertial measurement units – to create a more comprehensive and reliable understanding of the environment. This fusion process mitigates the limitations of individual sensors, improving accuracy and robustness against sensor failures, jamming, or spoofing attempts. By cross-validating data from multiple sources, the system can identify and reject erroneous or malicious information, maintaining operational integrity under adverse conditions. The combined effect of redundancy and fusion significantly reduces single points of failure and enhances the system’s ability to withstand both accidental failures and deliberate attacks.
Machine learning (ML) algorithms enhance cybersecurity by establishing behavioral baselines and identifying deviations indicative of malicious activity. These algorithms analyze network traffic, system logs, and user behavior to detect anomalies that traditional signature-based security systems may miss. Supervised learning techniques, trained on labeled datasets of normal and malicious activity, can classify threats with high accuracy. Unsupervised learning methods, such as clustering and anomaly detection, can identify previously unseen attack patterns without prior training data. Furthermore, reinforcement learning can be used to dynamically adapt security policies and responses to evolving threats, improving overall system resilience and proactively mitigating potential cyberattacks by learning from interactions with the system and potential adversaries.
Maintaining navigational integrity requires proactive mitigation of GNSS threats, including jamming and spoofing, as well as defenses against increasingly sophisticated adversarial attacks. Recent research demonstrates the vulnerability of object detection models to adversarial patches – subtly altered visual elements – which can reduce precision and accuracy by up to 48%. These attacks exploit weaknesses in machine learning algorithms, potentially causing critical failures in systems reliant on accurate object recognition. Therefore, robust defense mechanisms, including signal authentication, redundancy, and adversarial training of detection models, are essential to ensure reliable system operation in contested environments.
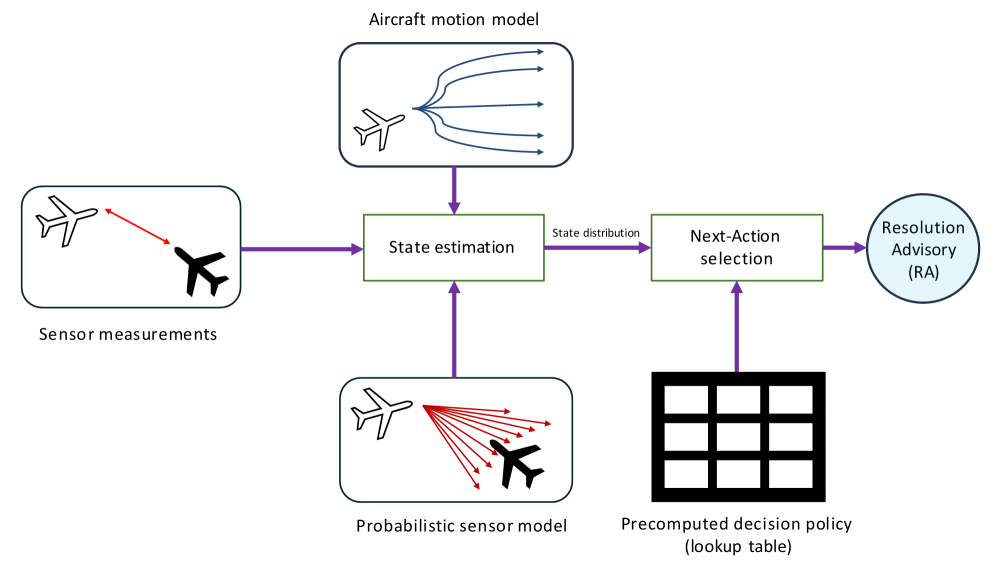
The Adaptive Skies: A Proactive Security Imperative
The advent of urban air mobility – a future filled with airborne vehicles transporting people and goods – necessitates a paradigm shift in cybersecurity, moving beyond reactive defenses to truly adaptive solutions. Unlike traditional aviation, which operates within highly controlled and predictable airspace, urban environments introduce a vastly expanded attack surface and a dynamic threat landscape. These airborne systems, reliant on GPS, wireless communication, and automated flight controls, are inherently vulnerable to a range of cyberattacks, from spoofing and jamming to malware and ransomware. Consequently, the security of these future skies depends not merely on preventing breaches, but on systems capable of anticipating potential threats, dynamically adjusting security protocols, and responding in real-time to emerging vulnerabilities – a proactive stance essential for maintaining public trust and ensuring the safe, reliable operation of urban air transport.
Maintaining secure urban air mobility demands a layered defense built on constant vigilance. Cybersecurity isn’t a one-time fix, but rather a continuous process of monitoring systems for anomalies, actively sharing threat intelligence across networks, and conducting proactive vulnerability assessments before exploits can emerge. This means employing real-time analytics to detect suspicious activity, collaborating with industry partners to disseminate information about emerging threats, and regularly simulating attacks to identify and patch weaknesses in hardware and software. Such a holistic approach moves beyond reactive damage control, establishing a resilient security posture capable of anticipating and mitigating risks in the dynamic airspace of the future, and ensuring the safety and reliability of increasingly connected aerial systems.
The advancement of secure urban air mobility necessitates a unified cybersecurity framework, achievable only through robust collaboration between industry, governmental bodies, and academic research institutions. Innovation in this rapidly evolving landscape demands the sharing of threat intelligence, best practices, and technological advancements – a process streamlined by open communication and standardized protocols. Government agencies can play a vital role in establishing clear regulatory guidelines and security benchmarks, while research institutions contribute cutting-edge detection and prevention technologies. Industry expertise, meanwhile, is crucial for practical implementation and real-world testing, creating a virtuous cycle of improvement and resilience. This collective effort isn’t simply about reacting to threats; it’s about proactively building a secure ecosystem that fosters public trust and enables the safe, reliable integration of airborne technologies into daily life.
The pursuit of secure Advanced Air Mobility (AAM) systems demands an uncompromising adherence to foundational principles. The article rightly emphasizes the critical need for robust cybersecurity measures across all eVTOL subsystems, a sentiment echoed by Linus Torvalds when he stated, “Most developers think that ‘good code’ means ‘clever code.’ I think good code means ‘correct code’”. The focus on data integrity within the Flight Management System (FMS), as detailed in the survey, is not simply a matter of functional reliability, but a logical necessity. Any deviation from provable correctness introduces unacceptable risk, transforming what should be a mathematically sound system into a fragile and potentially catastrophic one. Rigorous threat modeling and defense mechanisms are not optional; they are the formal definitions upon which a secure AAM future must be built.
What’s Next?
The presented survey, while detailing extant vulnerabilities within Advanced Air Mobility (AAM) and eVTOL systems, merely scratches the surface of a fundamentally intractable problem. The pursuit of ‘secure’ autonomous flight, predicated on ever-increasing computational complexity, ironically expands the attack surface proportionally. Defenses, at best, represent a shifting of risk, not its elimination. The true metric for evaluation should not be whether a system appears secure under contrived testing, but rather the provable bounds on its susceptibility to unforeseen exploits – a standard rarely, if ever, met in practice.
Future research must move beyond reactive threat modeling. A focus on formal verification of critical flight management system (FMS) components, employing mathematically rigorous methods, is paramount. The current reliance on empirical testing, akin to stress-testing a bridge with increasingly heavy loads until it fails, is intellectually unsatisfying and practically dangerous. Scalability remains a crucial, often overlooked aspect; defenses that perform adequately with a handful of aircraft will likely crumble under the demands of a densely populated urban airspace.
Ultimately, the quest for absolute security in these systems is a fallacy. The objective, therefore, should be a demonstrable understanding of residual risk and the development of systems that degrade gracefully, rather than catastrophically, in the face of inevitable compromise. The elegance of a solution, it bears repeating, is not measured in lines of code, but in the purity of its underlying mathematical foundation.
Original article: https://arxiv.org/pdf/2601.14415.pdf
Contact the author: https://www.linkedin.com/in/avetisyan/
See also:
- EUR USD PREDICTION
- Epic Games Store Free Games for November 6 Are Great for the Busy Holiday Season
- How to Unlock & Upgrade Hobbies in Heartopia
- Battlefield 6 Open Beta Anti-Cheat Has Weird Issue on PC
- Sony Shuts Down PlayStation Stars Loyalty Program
- TRX PREDICTION. TRX cryptocurrency
- The Mandalorian & Grogu Hits A Worrying Star Wars Snag Ahead Of Its Release
- Xbox Game Pass September Wave 1 Revealed
- INR RUB PREDICTION
- ARC Raiders Player Loses 100k Worth of Items in the Worst Possible Way
2026-01-23 04:20