Author: Denis Avetisyan
As decentralized systems mature, the need for mechanisms to address unforeseen vulnerabilities and critical events becomes paramount.

This review proposes a quantitative framework balancing rapid intervention with the preservation of trust and minimization of centralization in decentralized protocols.
Decentralized protocols promise immutable, rule-based execution, yet routinely embed mechanisms for intervention in the face of exploits and failures. This tension-between preserving trust and exercising discretion-is the focus of ‘Legitimate Overrides in Decentralized Protocols’, which proposes a quantitative framework mapping the design space of emergency architectures along dimensions of scope and authority. By formalizing the tradeoffs between centralization costs and containment speed as a stochastic cost-minimization problem, the authors demonstrate systematic relationships between intervention design, exploit losses-estimated at over $10$ billion between 2016-2026-and community sentiment. Can this approach move emergency governance beyond ideological debate and towards a more rigorous, engineering-driven approach to risk mitigation in decentralized systems?
The Immutable Paradox: Securing Blockchain Integrity
The very characteristic that defines blockchain technology – its immutability – creates a unique security challenge. While this permanence safeguards against tampering and fraud under normal circumstances, it simultaneously presents a paradox when vulnerabilities are discovered within smart contracts or the underlying code. Unlike traditional software where patches can be quickly deployed, flaws on a blockchain are essentially etched in stone. This necessitates the development of intervention mechanisms – often complex and controversial – that allow for mitigating damage or correcting errors after deployment, without completely compromising the integrity of the entire chain. These mechanisms range from carefully designed governance protocols allowing for code upgrades, to emergency halts and even, in extreme cases, hard forks – all representing deviations from the ideal of absolute immutability, yet crucial for protecting users and the network from potentially catastrophic exploits.
The expanding universe of Decentralized Finance (DeFi) and the burgeoning trend of tokenizing Real-World Assets (RWA) are dramatically increasing the stakes associated with blockchain vulnerabilities. While DeFi innovations unlock financial opportunities, they also introduce complex smart contracts that present novel attack vectors for malicious actors. Simultaneously, the practice of representing tangible assets – from commodities and real estate to intellectual property – as tokens on a blockchain means a successful exploit isn’t limited to the loss of cryptocurrency; it can now directly impact ownership and control of physical, real-world holdings. This convergence elevates the potential consequences of security breaches from primarily financial losses within the crypto ecosystem to systemic risks with broader economic implications, demanding a more robust and responsive approach to blockchain security than previously required.
Conventional cybersecurity strategies, designed for centralized systems, struggle to address the unique vulnerabilities present within decentralized blockchain networks. These networks face constantly evolving threats – from smart contract exploits to flash loan attacks – that outpace the development and deployment of traditional patching mechanisms. Consequently, a reactive security posture is insufficient; instead, robust emergency governance protocols are becoming essential. These protocols allow for swift, coordinated responses to critical incidents, potentially enabling mechanisms like pausing contracts, enacting circuit breakers, or initiating controlled rollbacks, all while minimizing disruption and protecting user funds in the face of increasingly sophisticated and impactful attacks.
A disproportionate concentration of damage characterizes blockchain security incidents; data indicates that a mere 20% of all addressable incidents account for approximately 80% of cumulative financial losses. This phenomenon, often referred to as ‘super-hacks’, suggests that a relatively small number of sophisticated attacks are responsible for the vast majority of exploited funds. Consequently, security efforts focused solely on mitigating the frequency of all incidents may be inefficient; instead, prioritizing defenses against these high-impact, ‘super-hack’ scenarios – those capable of causing catastrophic financial consequences – becomes paramount. Recognizing this skewed distribution of risk necessitates a shift towards proactive, targeted intervention strategies designed to prevent and contain the damage from these exceptionally damaging events.
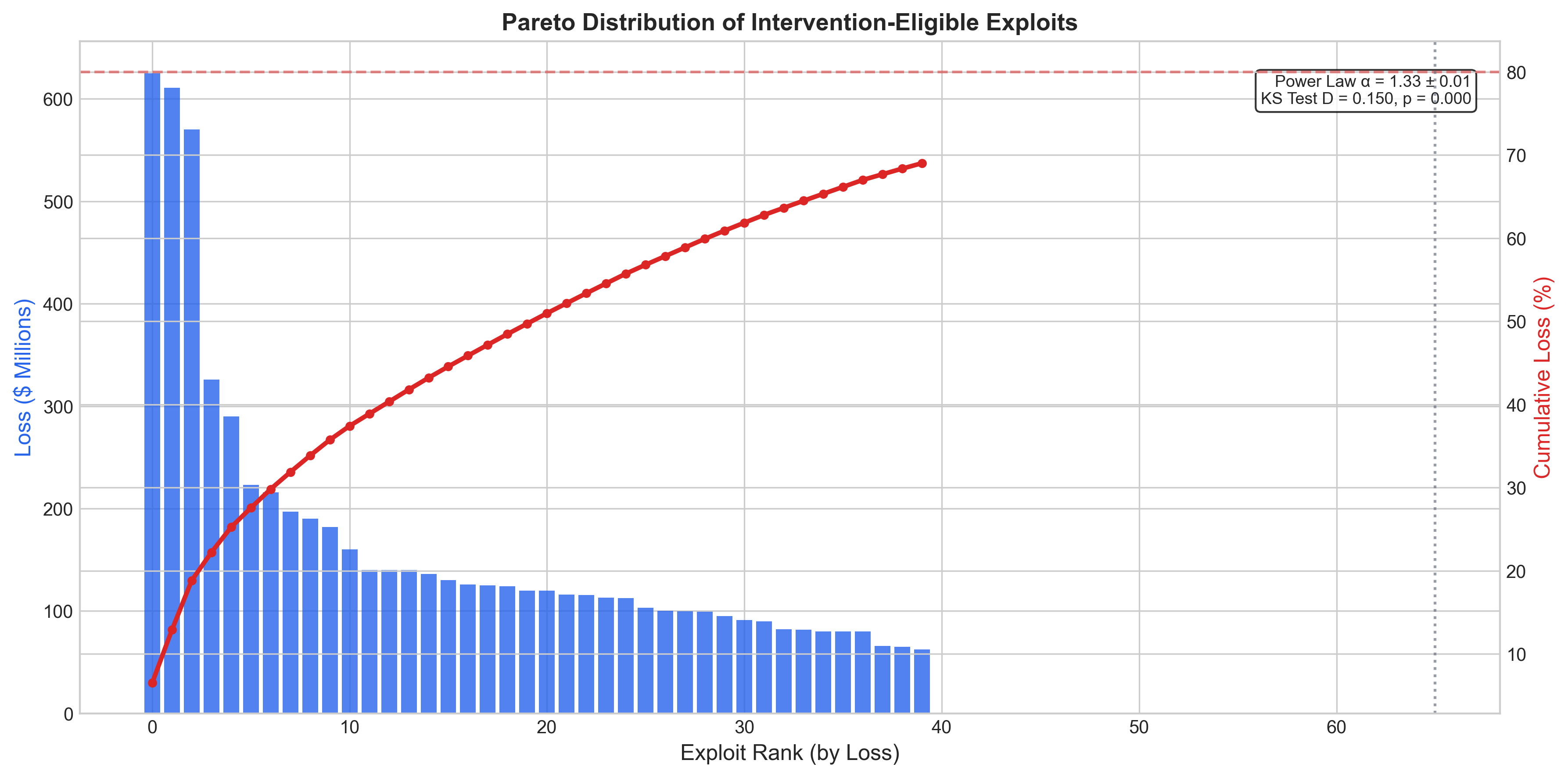
Defining the Boundaries of Responsible Intervention
Emergency governance frameworks are fundamentally defined by two key dimensions: intervention scope and authority. Intervention scope dictates the breadth of a response, ranging from network-wide actions affecting all participants, to account-level interventions targeting specific entities or assets. Authority, conversely, specifies the entity or process empowered to initiate an emergency response. These authorities can range from centralized bodies to decentralized signer sets or automated governance processes. The interplay between scope and authority determines the speed, flexibility, and decentralization characteristics of the emergency governance system, impacting its ability to effectively address critical situations while minimizing disruption or censorship.
Emergency governance authority can be implemented through three primary models, each with distinct characteristics. A ‘Governance Process’ relies on predefined rules and procedures, potentially slowing response times but offering transparency. Utilizing a ‘Signer Set’ involves a multi-signature scheme, enhancing security but requiring coordination among signers. Entrusting authority to a ‘Delegated Body’ enables rapid intervention by a specialized group, though this approach centralizes decision-making. The selection of an authority model involves balancing the need for speed and decentralization, and impacts the overall responsiveness and resilience of the governance system.
Intervention methodologies are differentiated by the breadth of their application and the actions they enable. ‘Network Scope Interventions’ affect the entire system, while ‘Account Scope Interventions’ target specific user accounts. These interventions utilize two primary mechanisms: a ‘Freeze Mechanism’ which restricts the movement of assets associated with an account, and account blacklisting, which prevents a specific account from interacting with the network. The selection of intervention scope and mechanism depends on the nature of the security threat and the desired level of disruption.
Analysis of intervention data indicates Delegated Body authority has demonstrably protected a significant volume of assets. Specifically, interventions authorized by Delegated Bodies have resulted in the safeguarding of $0.88 billion across all recorded cases. This figure represents 15.4% of the total value protected by all intervention types, establishing a quantifiable benefit and highlighting the effectiveness of this authority model in mitigating risk and securing assets within the network.
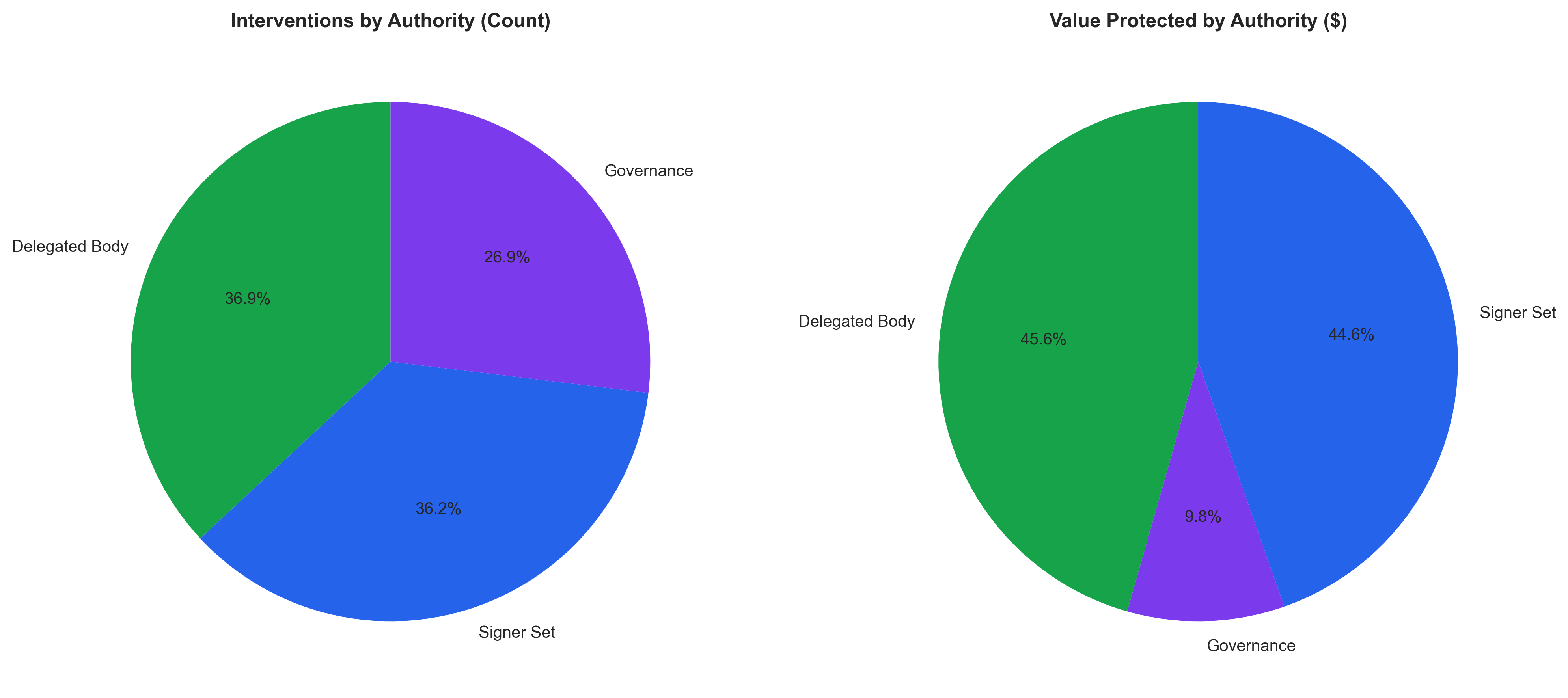
Optimizing Emergency Response Through Mathematical Precision
A Stochastic Optimization Model addresses emergency governance by mathematically minimizing the Expected\,Cost\,Function. This model utilizes probabilistic variables to represent uncertainties inherent in emergency events, such as incident probability and potential damage scales. By framing the problem as an optimization challenge, the model identifies strategies that balance the costs of preventative or reactive interventions with the costs associated with allowing an incident to escalate. The model’s objective is not to eliminate risk entirely, but to achieve the lowest overall expected cost, calculated as the sum of intervention costs multiplied by their probabilities, and the cost of damages multiplied by the probability of those damages occurring given a lack of intervention. This approach allows for a quantifiable comparison of different governance mechanisms and resource allocation strategies.
The stochastic optimization model incorporates probabilistic risk assessment by evaluating the likelihood of various exploit incidents occurring and quantifying the associated potential damage. This allows for a cost-benefit analysis that weighs the financial and logistical costs of proactive intervention – such as deploying security measures or initiating containment protocols – against the projected costs resulting from allowing an incident to unfold without response. The model calculates an ‘Expected Cost Function’ which represents the weighted average of these costs, factoring in both the probability and magnitude of potential outcomes, thereby identifying the intervention strategy that minimizes overall expected cost. This balancing act is crucial for efficient resource allocation in emergency governance.
The Culture Multiplier is a weighting factor integrated into the stochastic optimization model to reflect a community’s resistance to, or acceptance of, centralized intervention during emergency response. This multiplier scales the cost associated with deploying centralized authorities, acknowledging that interventions perceived as overly controlling can incur reputational or social costs. The model assigns a value to the Culture Multiplier based on pre-defined metrics representing community decentralization preferences; a higher value indicates greater resistance to centralized action, thereby increasing the cost of such interventions relative to localized, delegated responses. This allows the model to identify optimal strategies that balance effective incident containment with minimizing disruption to established community norms and governance structures.
Analysis using the stochastic optimization model indicates a 48.6% containment success rate when employing interventions managed by Delegated Bodies. This percentage represents the proportion of simulated exploit incidents successfully contained before significant damage occurred, based on model parameters reflecting probability of incident occurrence and potential damage levels. The 48.6% success rate is calculated across a comprehensive dataset of simulated scenarios, demonstrating a measurable effectiveness for this intervention strategy compared to alternative approaches modeled within the system. Further analysis indicates this success rate is sensitive to adjustments in the ‘Culture Multiplier’ and the cost-benefit thresholds within the ‘Expected Cost Function’.
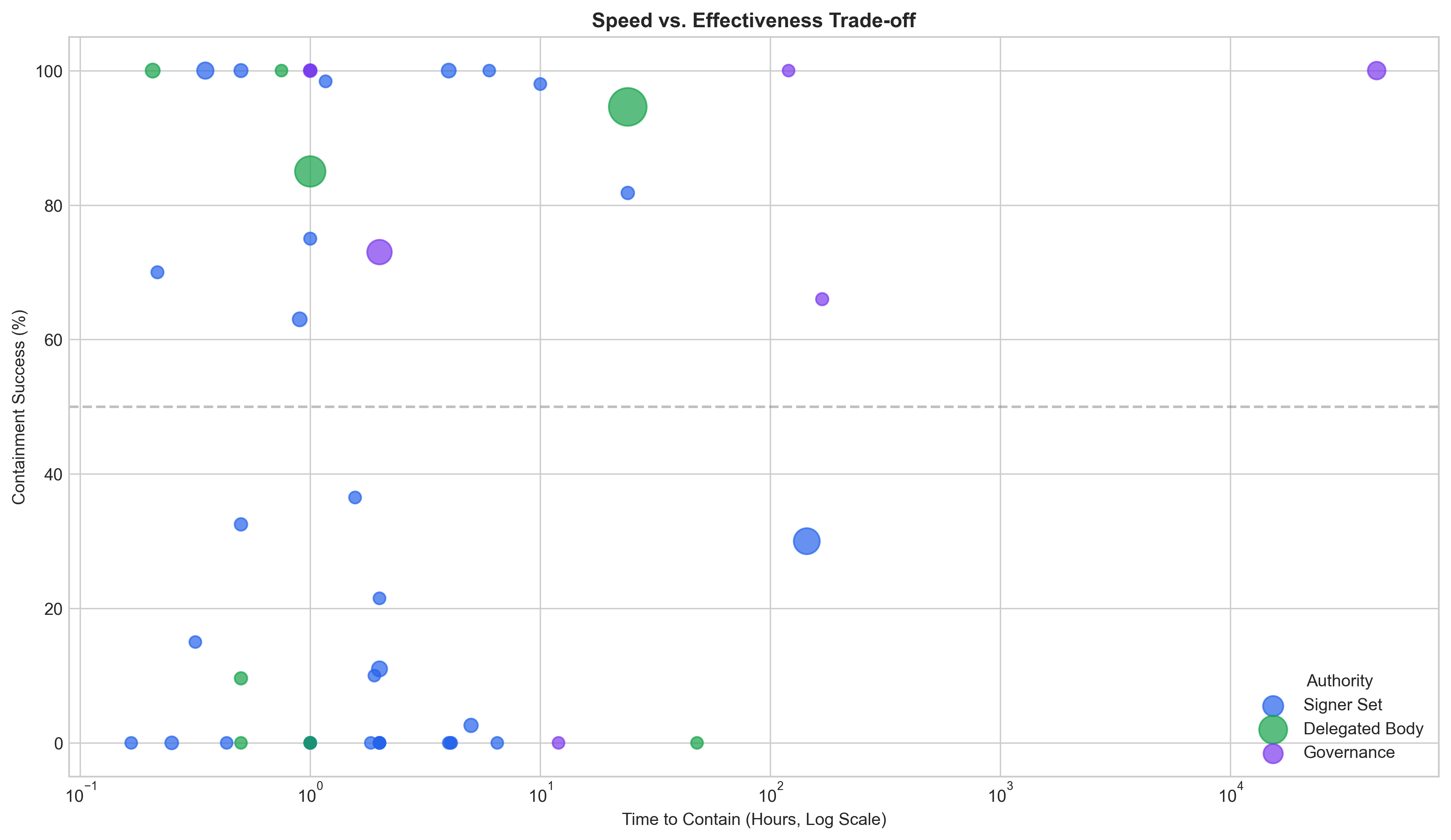
Extending Protection Across the Multi-Chain Future
As blockchain ecosystems mature and increasingly connect, the need for robust emergency governance extends beyond individual networks to encompass the entire multi-chain landscape. This demand for ‘Cross-Chain Coordination’ arises from the inherent risks of interoperability – vulnerabilities in one chain can propagate rapidly to others, necessitating a unified response. Effective governance, in this context, requires establishing standardized protocols for incident detection, information sharing, and coordinated mitigation strategies across disparate blockchain architectures. Without such coordination, a localized exploit could cascade into a systemic crisis, undermining trust and potentially causing significant financial loss. Therefore, proactive development of cross-chain governance frameworks is not simply a best practice, but a fundamental requirement for ensuring the long-term stability and security of the interconnected blockchain future.
As blockchain ecosystems proliferate, the ability to seamlessly share critical security information and orchestrate unified responses across disparate networks is paramount. Effective cross-chain coordination necessitates the development of standardized protocols for incident reporting, vulnerability disclosures, and intervention strategies. These protocols must facilitate rapid communication between security teams operating on different chains, enabling a collective and timely response to exploits or malicious activity. Without such interoperable systems, vulnerabilities on one network could easily cascade to others, amplifying potential damage and eroding trust in the broader multi-chain landscape. Establishing clear lines of communication and coordinated action is therefore not simply a matter of best practice, but a fundamental requirement for maintaining the integrity and resilience of the interconnected blockchain future.
Mitigating the risk of blockchain exploits increasingly relies on preventative strategies that address vulnerabilities before they can be actively exploited. Formal verification, a rigorous mathematical approach, allows developers to prove the correctness of smart contract code, significantly reducing the potential for logic errors. Complementing this, bug bounty programs incentivize ethical hackers to proactively identify and report security flaws in exchange for rewards. These programs create a ‘white hat’ testing environment, effectively crowdsourcing security audits and broadening the scope of vulnerability detection beyond internal teams. By prioritizing these proactive measures, blockchain projects can demonstrably lower the incidence of emergency interventions, fostering a more secure and reliable decentralized ecosystem and minimizing potential financial losses for users.
Analysis of on-chain governance interventions reveals a significant concentration of response activity within a designated group known as the Signer Set. This collective consistently handles 71.2% of all incident cases, establishing it as the primary actor in maintaining network security and stability. This high volume of intervention suggests the Signer Set isn’t merely reacting to rare, catastrophic failures, but is actively engaged in addressing a frequent stream of potential exploits and vulnerabilities. Consequently, the efficiency and reliability of this group are paramount; any disruption to its function would likely lead to a substantial increase in the severity and duration of security incidents across the blockchain ecosystem. The data underscores the importance of robust infrastructure and well-defined protocols to support the Signer Set’s ongoing and critical role.
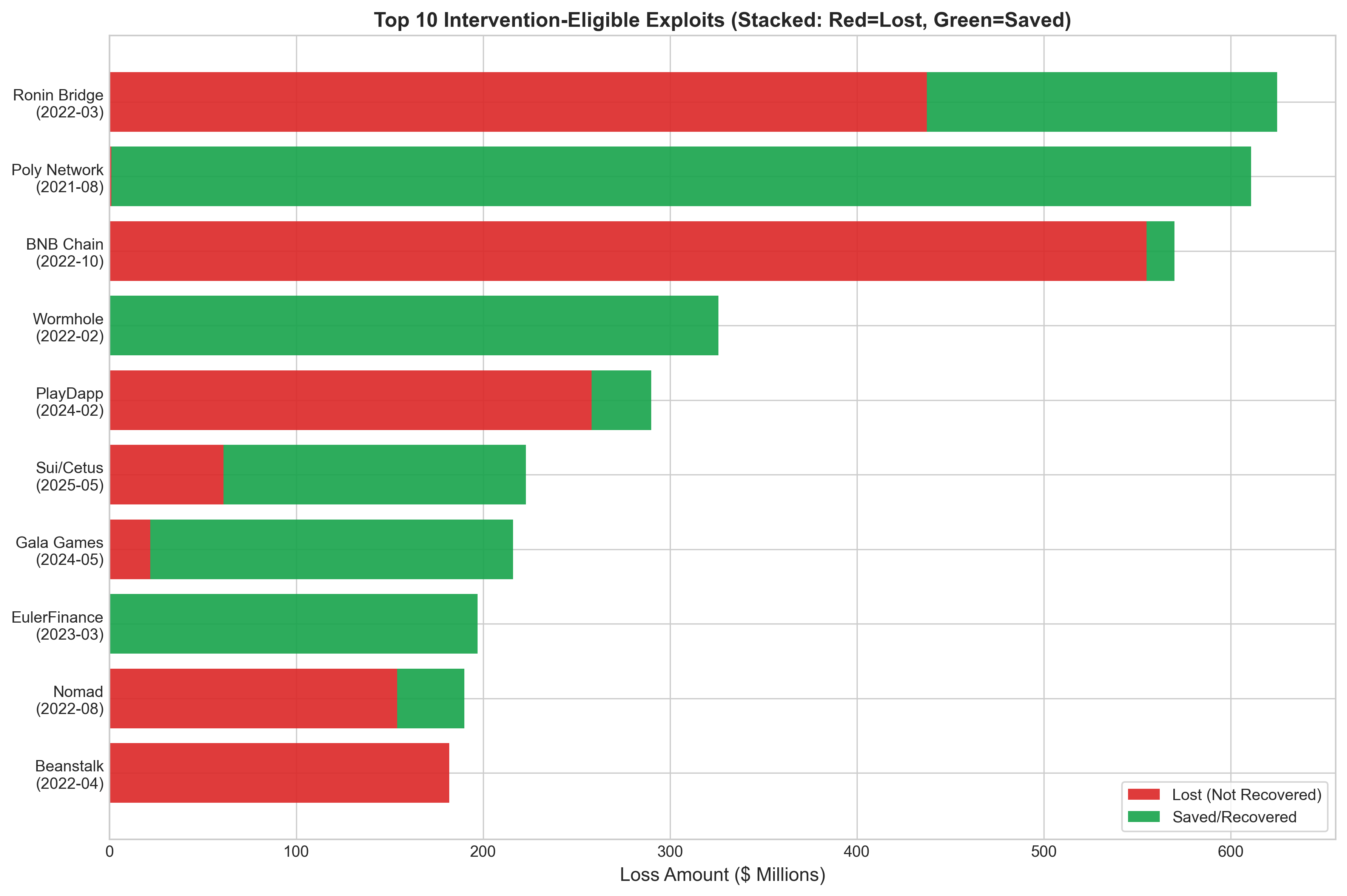
The pursuit of robust decentralized protocols often encounters the immutability paradox – a tension between steadfast security and necessary adaptation. This paper attempts to navigate this complexity by quantifying legitimate overrides, acknowledging that absolute rigidity can be as detrimental as unchecked authority. It’s a deliberate paring away of extraneous control, seeking the essential balance. As Henri Poincaré observed, “It is through science we get rid of many illusions.” This sentiment resonates deeply with the work; the proposed framework isn’t about introducing complexity, but about systematically removing the ambiguity surrounding emergency governance, thereby clarifying the boundaries of acceptable intervention and bolstering trust within the system.
What Remains?
The presented framework, while offering a quantitative approach to emergency governance, does not dissolve the fundamental tension inherent in decentralized systems. It clarifies how to override, but not when. The most pressing challenge lies not in modeling stochastic events, but in defining the boundaries of acceptable intervention. Any mechanism, however elegantly calibrated, remains vulnerable to subjective interpretation of ‘emergency’, and the inevitable abuse of authority – however limited in scope. Simplicity, not complexity, will reveal these weaknesses.
Future work should resist the temptation to build more elaborate models. Instead, focus should be directed toward minimizing the need for overrides. A truly robust protocol anticipates failure, rather than reacting to it. This necessitates a shift in design philosophy: prioritize inherent resilience over reactive mechanisms. The pursuit of perfect immutability is a fallacy; the goal should be sufficient flexibility without sacrificing core principles.
Ultimately, the field must acknowledge a difficult truth: decentralization is not a technological problem, but a social one. No amount of quantitative analysis can solve the problem of trust. The longevity of these protocols will depend not on the sophistication of their security mechanisms, but on the integrity of those who govern them – or, ideally, on the absence of governance altogether.
Original article: https://arxiv.org/pdf/2602.12260.pdf
Contact the author: https://www.linkedin.com/in/avetisyan/
See also:
- EUR USD PREDICTION
- Epic Games Store Free Games for November 6 Are Great for the Busy Holiday Season
- How to Unlock & Upgrade Hobbies in Heartopia
- Battlefield 6 Open Beta Anti-Cheat Has Weird Issue on PC
- Sony Shuts Down PlayStation Stars Loyalty Program
- TRX PREDICTION. TRX cryptocurrency
- The Mandalorian & Grogu Hits A Worrying Star Wars Snag Ahead Of Its Release
- Xbox Game Pass September Wave 1 Revealed
- Best Ship Quest Order in Dragon Quest 2 Remake
- INR RUB PREDICTION
2026-02-13 15:32