Author: Denis Avetisyan
Researchers have developed an automated system that uses artificial intelligence to dissect live blockchain attacks and recreate the exploits that made them possible.
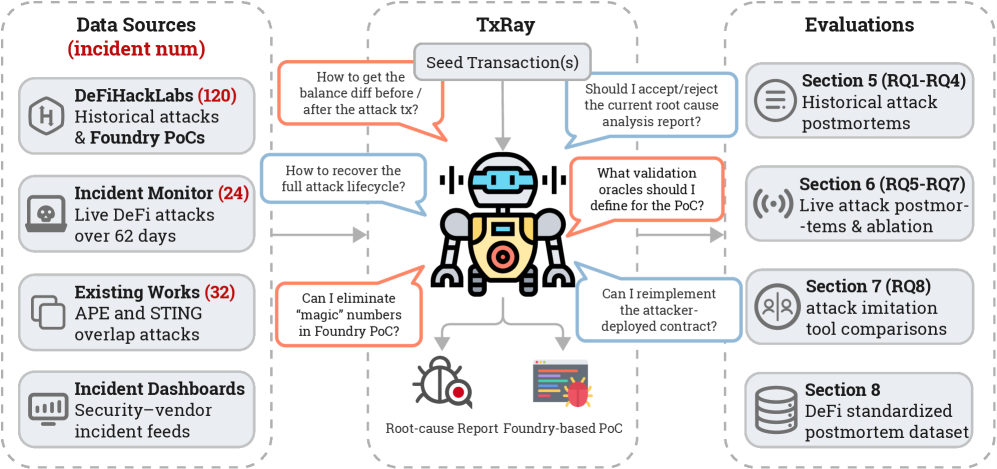
TxRay, an agentic system leveraging large language models, automates postmortem analysis of DeFi exploits, generates executable proof-of-concept attacks, and provides a standardized dataset for security research.
Despite the increasing transparency of blockchain technology, postmortem analysis of decentralized finance (DeFi) exploits remains a slow, manual process-often starting with minimal evidence. This paper introduces TxRay: Agentic Postmortem of Live Blockchain Attacks, a system leveraging large language model (LLM) agents to automatically reconstruct the lifecycle of “Anyone-Can-Take” (ACT) attacks and derive evidence-backed root causes. TxRay uniquely generates runnable, self-contained Proof-of-Concept (PoC) exploits, validated by self-checking oracles, achieving 92.11% end-to-end reproduction on 114 DeFi incidents and delivering validated root causes in under an hour. Could this approach fundamentally reshape incident response and proactive security research within the rapidly evolving DeFi landscape?
The Inevitable Surge of DeFi Exploits
Decentralized finance (DeFi) platforms, lauded for their potential to revolutionize financial systems, are simultaneously becoming prime targets for increasingly complex and damaging exploits. This surge in attacks isn’t simply a matter of quantity; the sophistication of these exploits is rapidly evolving, often leveraging novel smart contract vulnerabilities and intricate attack vectors. The financial stakes are substantial, with millions of dollars frequently lost in single incidents, and the reputational damage to affected projects can be crippling. Consequently, a swift and comprehensive understanding of these attacks is no longer a luxury, but a critical necessity for the continued viability and growth of the DeFi space. The innovative nature of these systems, while offering immense opportunity, inherently presents new attack surfaces that demand constant vigilance and proactive security measures.
Post-incident investigation within decentralized finance (DeFi) often relies on methods ill-equipped to handle the speed and intricacy of modern exploits. Traditional analysis typically involves manually sifting through blockchain transactions and smart contract code, a process that is both time-consuming and prone to human error. This reactive approach struggles to accurately piece together the sequence of events in complex attacks – such as those leveraging flash loans or multi-signature compromises – delaying the identification of vulnerabilities and hindering the development of effective preventative measures. The resulting lag between exploit detection and mitigation leaves DeFi protocols vulnerable to repeat offenses and erodes user trust, highlighting the urgent need for more efficient and automated analysis techniques.
Decentralized finance (DeFi) platforms generate an immense and constantly growing volume of on-chain data, creating a significant challenge for security analysts. Manual investigation of transactions and smart contract interactions is simply no longer practical, given the speed and complexity of modern exploits. To effectively identify and mitigate vulnerabilities, the field increasingly relies on automated tools capable of parsing and analyzing this data at scale. These intelligent systems employ techniques like anomaly detection, behavioral analysis, and symbolic execution to reconstruct attack vectors, pinpoint the root cause of exploits, and ultimately, prevent future incidents. The ability to rapidly process and interpret this flood of information is becoming essential for maintaining the integrity and security of the burgeoning DeFi landscape.
TxRay: An Agentic System for Postmortem Analysis
TxRay operates as an agentic system, meaning it utilizes multiple autonomous agents to perform complex tasks without direct human intervention. These agents are designed to ingest and process publicly available on-chain data – encompassing transaction histories, smart contract code, and token movements – to analyze potential DeFi exploits. The system doesn’t rely on pre-defined signatures or alerts; instead, agents dynamically explore the blockchain, identifying anomalous patterns and reconstructing the sequence of events that constitute an exploit. This reconstruction is achieved through automated analysis and simulation of transactions, allowing for a detailed understanding of the attack vector without requiring manual investigation of raw blockchain data.
The TxRay system employs an Incident Monitor that continuously scans blockchain data for anomalous transactions and patterns indicative of potential exploits. Upon detection of a suspicious event, TxRay automatically initiates a Proof-of-Concept (PoC) Generation process. This involves recreating the identified attack sequence within a secure, isolated environment-a forked Ethereum network-using the same transaction data and smart contract interactions. This controlled reproduction allows for detailed observation of the exploit’s execution path without risk to live funds or systems, forming the basis for subsequent root cause analysis and vulnerability assessment.
Root Cause Analysis within TxRay employs a multi-stage process to determine the precise vulnerabilities exploited during a DeFi incident. This begins with static analysis of the affected smart contract code, identifying potential weaknesses like integer overflows, reentrancy issues, or logic errors. Dynamic analysis then recreates the exploit in a controlled environment, tracing the execution flow and pinpointing the exact line(s) of code triggered by the malicious transaction(s). TxRay correlates on-chain data – including transaction hashes, contract interactions, and token transfers – with the code analysis to establish the causal chain of events. The system identifies not only the immediate vulnerability but also the underlying mechanisms – such as flawed access control or improper validation – that permitted the exploit to succeed, delivering a comprehensive report detailing the root cause and potential mitigation strategies.
Validating Exploit Reconstruction with Semantic Rigor
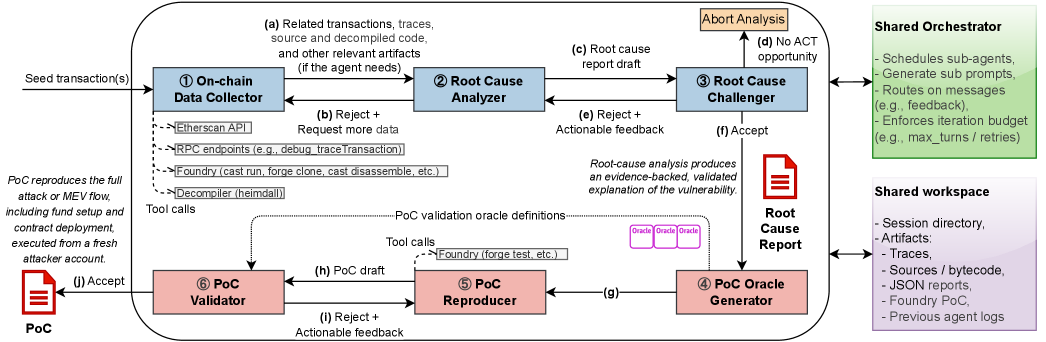
Oracle validation is a critical component in exploit reproduction, serving to confirm the functional correctness of a generated Proof-of-Concept (PoC). This process verifies that the PoC accurately mirrors the behavior of the original exploit, ensuring the reproduced vulnerability manifests as intended. Without validation, a PoC may superficially resemble an exploit but fail to reliably trigger the underlying vulnerability, leading to inaccurate analysis and potentially missed security flaws. The validation process confirms the PoC’s ability to successfully reproduce the exploit’s effects, establishing confidence in the analysis results and the identified vulnerability.
The validation of exploit reconstructions relies on a Semantic Oracle, which consists of a pre-defined set of constraints used to determine the expected behavior of a reproduced exploit. These constraints are not based on superficial observations, but rather on a formal definition of the vulnerability and its intended impact on the system. Specifically, the Semantic Oracle specifies acceptable outcomes – such as memory corruption at a defined address, control flow hijacking to a particular function, or unauthorized data access – and defines boundaries for acceptable execution paths. Any reproduction that violates these constraints is flagged as inaccurate, ensuring the generated Proof-of-Concept (PoC) faithfully reflects the underlying vulnerability.
TxRay utilizes semantic constraints to assess the validity of generated Proof-of-Concept (PoC) exploits. The system compares the behavior of the reconstructed exploit against these predefined constraints, which represent the expected outcome of a successful exploitation. Discrepancies between the observed behavior and the constraints trigger flags, indicating either an inaccurate PoC reconstruction or an incomplete representation of the exploit’s functionality. This constraint-based validation process is fundamental to ensuring the reliability of TxRay’s analysis, preventing the propagation of flawed or incomplete exploit data, and providing confidence in the accuracy of vulnerability assessments.
Uncovering the Deeper Implications of DeFi Vulnerabilities
A comprehensive root cause analysis, deeply informed by the intricacies of the Ethereum Virtual Machine (EVM) and a thorough understanding of Miner Extractable Value (MEV) dynamics, has pinpointed the specific vulnerabilities that enabled the recent exploit. This investigation reveals that the attacks weren’t simply a matter of coding errors, but rather exploited inherent properties within the EVM’s execution model, particularly as they relate to transaction ordering and gas price manipulation driven by MEV opportunities. By dissecting the exploit’s mechanics at this granular level, researchers have identified systemic weaknesses in how decentralized applications interact with the blockchain, showcasing that even seemingly secure contracts can be compromised when subjected to sophisticated MEV-driven attacks. This detailed examination underscores the necessity of building security measures that account for, and mitigate, these complex economic incentives within the Ethereum ecosystem.
Analysis of data from DeFiHackLabs is revealing crucial insights into the evolving landscape of blockchain exploits. This resource provides a unique opportunity to move beyond reactive security measures and proactively address vulnerabilities by identifying recurring patterns in attacker methodologies. Researchers are able to chart trends in exploit techniques – from common contract flaws to preferred attack vectors – allowing for the development of more targeted and effective security protocols. By understanding how attackers operate, the industry can anticipate future threats and build defenses that are specifically designed to mitigate them, ultimately fostering a more secure and resilient decentralized finance ecosystem. This data-driven approach promises a significant shift from simply responding to incidents, towards a future where vulnerabilities are predicted and prevented.
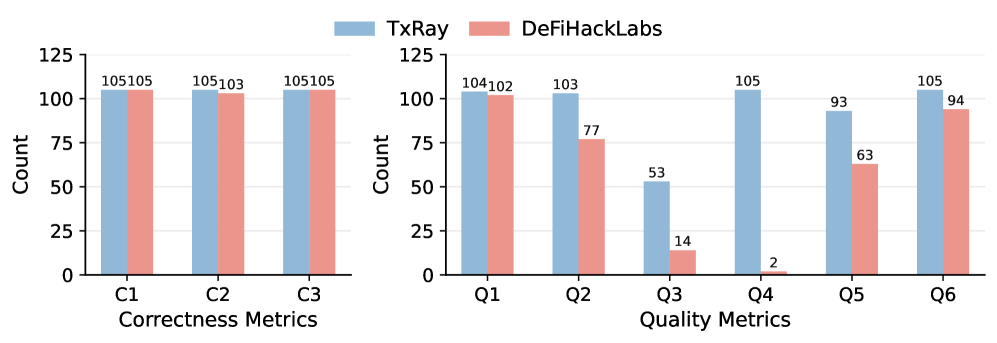
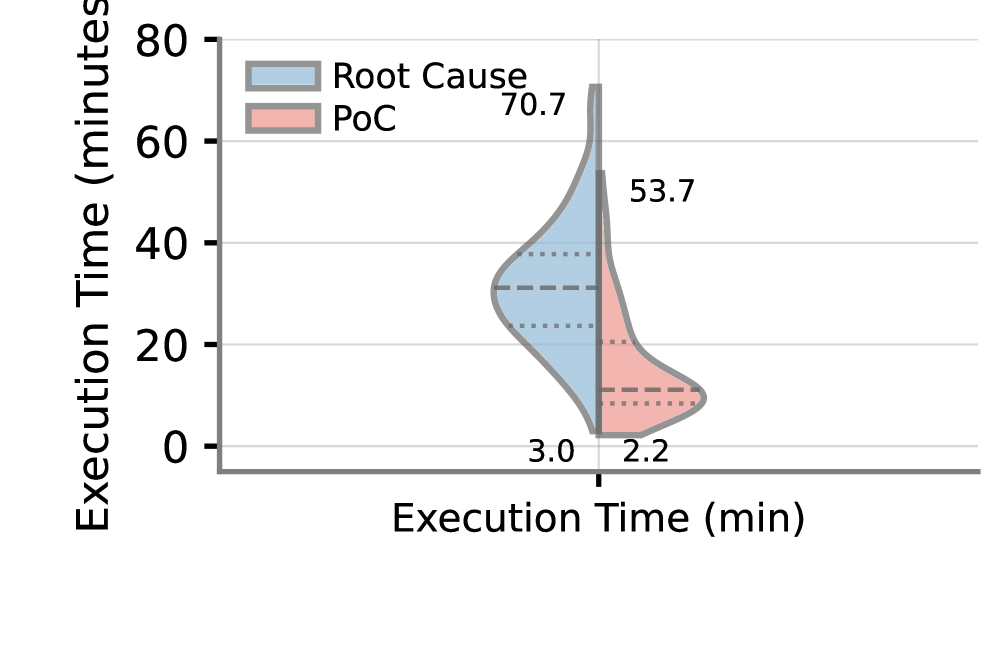
A novel automated system, TxRay, has demonstrated a substantial leap forward in the field of vulnerability analysis and post-incident reconstruction within decentralized finance. Evaluated against a dataset of 114 real-world incidents sourced from DeFiHackLabs, TxRay successfully reproduced exploit scenarios with a remarkable 92.11% success rate. This high degree of accuracy is further supported by a low miss rate of just 4.55% and a minimal misalignment rate of 3.67% when analyzing cases identified by the ACT (Attack Chain Tracing) framework. Importantly, TxRay doesn’t merely replicate exploits; it generates executable and self-contained Proofs-of-Concept (PoCs) with 100% correctness on 105 aligned incidents, and achieves this in a median time of 10.65 minutes – a significant improvement over existing methods, uncovering five additional exploitable opportunities in generalized attack imitation.
The automated vulnerability analysis system, TxRay, demonstrates a remarkable capacity for reconstructing and replicating DeFi exploits; when applied to 105 verified incidents, it successfully generated executable Proofs of Concept with complete accuracy. Crucially, TxRay produced self-contained PoCs, effectively isolating the vulnerability without including potentially misleading attacker-introduced code, in all but one instance. This reconstruction process is also notably efficient, with a median generation time of just 10.65 minutes. Beyond simply replicating known attacks, TxRay identifies an average of five additional exploitable opportunities compared to existing methods, suggesting a substantial improvement in generalized attack imitation and proactive security assessment.
The pursuit of absolute security in decentralized finance, as demonstrated by TxRay’s automated postmortem analysis, often proves illusory. The system, designed to dissect exploits and generate proof-of-concept attacks, reveals the inherent fragility woven into complex systems. It echoes Andrey Kolmogorov’s sentiment: “The most important thing in science is not knowing many scientific facts, but knowing how to do research.” TxRay isn’t a preventative measure, but a tool for understanding failure-a garden meticulously cultivated not to eliminate weeds, but to learn from their growth. The creation of a standardized dataset, a key component of this research, fosters a cycle of learning where each incident informs future resilience, recognizing that systems evolve and adapt, rather than achieving a state of perfect, static defense.
What Lies Ahead?
TxRay, as presented, does not solve the problem of DeFi exploits. It merely relocates the surface of attack. Automating postmortem analysis, while valuable, establishes a new equilibrium. The system will inevitably discover patterns that become targets themselves – the very logic of automated detection will be exploited. A system that never breaks is, after all, a dead system. The creation of a standardized dataset, intended to bolster research, is equally double-edged; it provides a richer training ground not only for defensive agents, but for those crafting more subtle and effective attacks.
The true limitation lies not in the technical capacity to generate PoCs, but in the fundamental asymmetry between attack and defense. Attack requires only a single novel vector; defense demands anticipating every possible permutation. Future work will not be measured by the sophistication of automated analysis, but by the acceptance of inherent fragility. Perhaps the focus should shift from preventing all exploits to minimizing blast radius, and building systems capable of graceful degradation – ecosystems, rather than fortresses.
Perfection, in this domain, leaves no room for people. The most promising avenues for research will likely lie not in ever-more-complex automation, but in tooling that amplifies human intuition and judgment. A system that requires no human oversight is not secure; it is simply awaiting its inevitable, and ultimately predictable, failure.
Original article: https://arxiv.org/pdf/2602.01317.pdf
Contact the author: https://www.linkedin.com/in/avetisyan/
See also:
- Solo Leveling: Ranking the 6 Most Powerful Characters in the Jeju Island Arc
- How to Unlock the Mines in Cookie Run: Kingdom
- Gold Rate Forecast
- Gears of War: E-Day Returning Weapon Wish List
- Bitcoin’s Big Oopsie: Is It Time to Panic Sell? 🚨💸
- How to Unlock & Visit Town Square in Cookie Run: Kingdom
- The Saddest Deaths In Demon Slayer
- How to Find & Evolve Cleffa in Pokemon Legends Z-A
- Most Underrated Loot Spots On Dam Battlegrounds In ARC Raiders
- Bitcoin Frenzy: The Presales That Will Make You Richer Than Your Ex’s New Partner! 💸
2026-02-04 04:21