Ah! Behold, dear friends, the Sui blockchain, now thrust beneath the magnifying glass of public opinion, for having lent its noble hand to the most curious of proposals: a recovery of 162 millions—yes, millions!—for the beleaguered Cetus Protocol. What a comedy of errors, what a ballet of digital ducats! 💸🤦♂️
Decentralization or Farce?
Cetus, ever the generous soul, waved a $6 million bounty before the hacker’s nose—an offer so modest it might have insulted even Harpagon’s thrift. The crowd jeered: “Six million? For a fortune so grand? Surely you jest!”
Yet, undeterred, Cetus presses for a protocol upgrade to return the frozen spoils—without so much as ruffling the historical feathers of the blockchain or rolling back a single transaction. A compromise, they say! But oh, what debates it has unleashed about the sanctity of decentralization. Is this not a stage where every actor improvises?
Meanwhile, the Sui Foundation, in a masterstroke of neutrality worthy of Orgon himself, has agreed to support an on-chain vote—while abstaining from the fray. “We shall watch,” they declare, “but not meddle.”
//beincrypto.com/wp-content/uploads/2025/05/image-226.png”/>
Sui’s Bounty: A Comedy of Errors
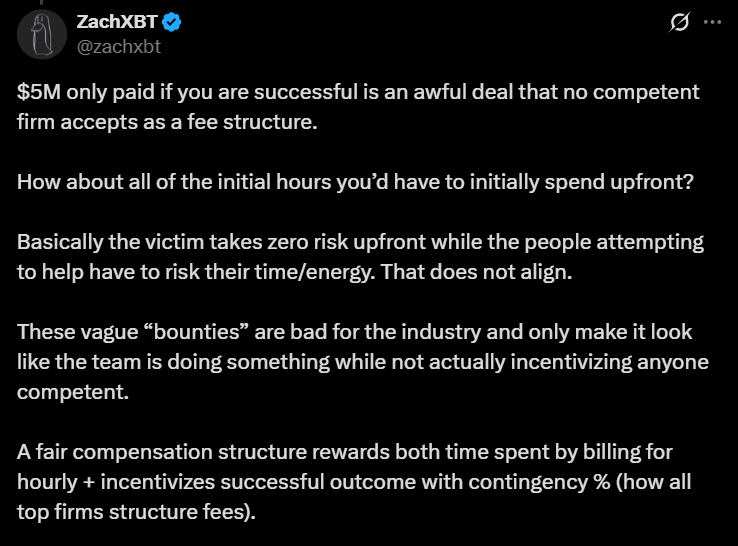
As if this were not enough, Sui’s own $5 million reward for information about the hacker has drawn more boos than bravos. “Vague!” cries ZachXBT, the on-chain sleuth. “Unhelpful! A reward that pays only upon success? Why not offer us magic beans while you’re at it?” 🫘😏
Yu Xian, co-founder of SlowMist and no stranger to intrigue, warns that unless the rogue returns the treasure or feels the heat of pursuit, investigators are doomed to chase shadows and phantoms across the digital stage.
He laments: “The cost of tracking such knavery is as uncertain as love itself—requiring alliances, negotiations, and endless reports. Without upfront coin or deep cooperation, our pursuit is but a farce.”
“The investment cost of tracking services is very uncertain, such as threat intelligence cooperation network resource coordination, stolen user communication, law enforcement communication, investigation and evidence collection, evidence fixation, negotiation promotion, analysis reports, etc. If there is no upfront cost or deep enough cooperation resources to guarantee, it is difficult to continue to advance,” Xian added.
Read More
- Delta Force: K437 Guide (Best Build & How to Unlock)
- Top 8 UFC 5 Perks Every Fighter Should Use
- USD ILS PREDICTION
- Slormancer Huntress: God-Tier Builds REVEALED!
- Tainted Grail: The Fall of Avalon – Everything You Need to Know
- AI16Z PREDICTION. AI16Z cryptocurrency
- Invincible’s Strongest Female Characters
- How to Unlock the Mines in Cookie Run: Kingdom
- REPO’s Cart Cannon: Prepare for Mayhem!
- Nine Sols: 6 Best Jin Farming Methods
2025-05-24 16:37